mirror of
https://github.com/pe3zx/my-infosec-awesome.git
synced 2024-06-27 14:12:12 +00:00
63 KiB
63 KiB
Articles
Cryptography
- A Readable Specification of TLS 1.3
- Encrypting for Apple's Secure Enclave
- hannob/tls-what-can-go-wrong - TLS - what can go wrong?
Digital Forensics and Incident Response
- A Newbie’s Guide to ESXi and VM Log Files
- certsocietegenerale/IRM - Incident Response Methodologies
- Cloud Forensics: Analyzing MEGASync
- Cloud Forensics: Google Drive
- Cloud Forensics: pCloud Drive
- Finding TikTok messages in iOS
- Forensic Analysis Of The μTorrent Peer-to-Peer Client In Windows
- "Gone In 10 Seconds" Snapchat Forensics
- How to Perform Hadoop Forensics
- Tool Analysis Result Sheet
Digital Forensics and Incident Response: Platform: Android
Digital Forensics and Incident Response: Platform: Unix/Linux
- Bruteforcing Linux Full Disk Encryption (LUKS) with hashcat - The Forensic way!
- Can an SSH session be taken from memory?
- Forensic Relevance of Vim Artifacts
- INTRO TO LINUX FORENSICS
- Linux Memory Forensics: Dissecting the User Space Process Heap
- KIT-CERT Checklist for Linux Forensics
Digital Forensics and Incident Response: Platform: IoT
Digital Forensics and Incident Response: Platform: MacOS/iOS
- A Few Interesting iOS Forensic Artefacts
- Apple File System Reference
- Apple Probably Knows What You Did Last Summer
- Detection of Backdating the System Clock in macOS
- Finding Slack app messages in iOS
- Getting saucy with APFS
- How to Acquire an iOS 11 Device Without the PIN/Passcode
- I Know What You Did Last Month: A New Artifact of Execution on macOS 10.13
- Inside iCloud Drive: Downloading
- Inside iCloud Drive: Pushed updates, that syncing feeling
- Inside iCloud Drive: uploading a file
- iOS 11: HEVC and HEIF (heic) files
- Knowledge is Power! Using the macOS/iOS knowledgeC.db Database to Determine Precise User and Application Usage
- mac4n6 - Presentations
- macOS Unified log: 1 why, what and how
- macOS Unified log: 2 content and extraction
- macOS Unified log: 3 finding your way
- Monkey takes a .heic
- Mounting an APFS image in Linux
- pstirparo/mac4n6 - Collection of forensics artifacs location for Mac OS X and iOS
- Reading Notes database on macOS
- Staring into the Spotlight
- The Hitchhiker’s Guide to macOS USB Forensics
- There’s Gold In Them There Blobs!
Digital Forensics and Incident Response: Platform: Windows
- (Am)cache still rules everything around me (part 2 of 1)
- Amcache and Shimcache in forensic analysis
- Carving EVTX
- Certificate Chain Cloning and Cloned Root Trust Attacks
- Detailed properties in the Office 365 audit log
- Detection and recovery of NSA’s covered up tracks
- Detecting DDE in MS Office documents with YARA rules
- Extracting Activity History from PowerShell Process Dumps
- Forensic Analysis of Systems that have Windows Subsystem for Linux Installed
- Getting to the Bottom of CVE-2018-0825 Heap Overflow Buffer
- How to Crack Passwords for Password Protected MS Office Documents
- HUNTING EVENT LOGGING COVERUP
- In-depth forensic analysis of Windows registry files
- Logging Keystrokes with Event Tracing for Windows (ETW)
- Looking at APT28 latest Talos Security write up and how YOU could catch this type of behavior
- MAC(b) times in Windows forensic analysis
- Malicious PowerShell in the Registry: Persistence
- Memory Acquisition and Virtual Secure Mode
- pwndizzle/CodeExecutionOnWindows - A list of ways to execute code on Windows using legitimate Windows tools
- RecentApps Registry Key
- RegRipper & keys parsed by plugins
- Tales of a Threat Hunter - Detecting Mimikatz & other Suspicious LSASS Access
- Volume Shadow Copies in forensic analysis
- Use Windows Event Forwarding to help with intrusion detection
- Windows, Now with built in anti forensics!
- Windows Credentials: Attack + Mitigation + Defense
- Windows Drive Acquisition
- Windows event logs in forensic analysis
- Windows Privileged Access Reference
- Windows registry in forensic analysis
- Windows Security Identifiers (SIDs)
- Windows Subsystem for Linux and Forensic Analysi
- Windows Event Forwarding for Network Defense
- Word Forensic Analysis And Compound File Binary Format
Exploitation
Exploitation: Hardware-related Attacks
Exploitation: Platform: Android
- Android Bluetooth Vulnerabilities in the March 2018 Security Bulletin
- CVE-2017-13253: Buffer overflow in multiple Android DRM services
- Writing the worlds worst Android fuzzer, and then improving it
Exploitation: Platform: Linux
- 64-bit Linux Return-Oriented Programming
- Adapting the POC for CVE-2017-1000112 to Other Kernels
- Blocking double-free in Linux kernel
- Binary Exploitation ELI5– Part 1
- Binary Exploitation ELI5 — Part 2
- Binary Exploitation ELI5 — Part 3
- CVE-2016-2384: exploiting a double-free in the usb-midi linux kernel driver
- CVE-2017-2636: exploit the race condition in the n_hdlc Linux kernel driver bypassing SMEP
- CVE-2017-11176: A step-by-step Linux Kernel exploitation (part 1/4)
- CVE-2017-11176: A step-by-step Linux Kernel exploitation (part 2/4)
- CVE-2017-11176: A step-by-step Linux Kernel exploitation (part 3/4)
- CVE-2017-11176: A step-by-step Linux Kernel exploitation (part 4/4)
- Dirty COW and why lying is bad even if you are the Linux kernel
- Enumeration for Linux Privilege Escalation
- Escaping Docker container using waitid() – CVE-2017-5123
- Exploiting the Linux kernel via packet sockets
- Kernel Exploitation | Dereferencing a NULL pointer!
- Linux (x86) Exploit Development Series
- Linux Heap Exploitation Intro Series: The magicians cape – 1 Byte Overflow
- Linux Heap Exploitation Intro Series: Set you free() – part 1
- Linux Heap Exploitation Intro Series: Used and Abused – Use After Free
- Linux Kernel ROP - Ropping your way to # (Part 1)
- Linux Kernel ROP - Ropping your way to # (Part 2)
- Linux Kernel Vulnerability Can Lead to Privilege Escalation: Analyzing CVE-2017-1000112
- Linux System Call Table
- MMap Vulnerabilities – Linux Kernel
- r0hi7/BinExp - Linux Binary Exploitation
- Reversing DirtyC0W
- The Definitive Guide to Linux System Calls
- xairy/linux-kernel-exploitation
Exploitation: Platform: MacOS/iOS
- A Methodical Approach to Browser Exploitation
- An introduction to exploiting userspace race conditions on iOS
- Analysis: Inspecting Mach Messages in macOS Kernel-Mode Part I: Sniffing the sent Mach messages
- Analysis: Inspecting Mach Messages in macOS Kernel-Mode Part II: Sniffing the received Mach messages
- Covering Ian Beer's exploit techniques for getvolattrlist bug (iOS 11-11.3.1)
- Cracking the Walls of the Safari Sandbox - Fuzzing the macOS WindowServer for Exploitable Vulnerabilities
- Heapple Pie - The macOS/iOS default heap
- Kernel RCE caused by buffer overflow in Apple's ICMP packet-handling code (CVE-2018-4407)
- LightSpeed, a race for an iOS/MacOS sandbox escape
- The HIDeous parts of IOKit
- Timeless Debugging of Complex Software: Root Cause Analysis of a Non-Deterministic JavaScriptCore Bug
- Weaponization of a JavaScriptCore Vulnerability -Illustrating the Progression of Advanced Exploit Primitives In Practice
Exploitation: Platform: Windows
- 0patching the "Immortal" CVE-2017-7269
- 15 Ways to Bypass the PowerShell Execution Policy
- A Bug Has No Name: Multiple Heap Buffer Overflows In the Windows DNS Client
- A Deep Analysis of the Microsoft Outlook Vulnerability CVE-2018-8587
- A deeper look at ms11-058
- Abusing A Writable Windows Service
- Abusing Delay Load DLLs for Remote Code Injection
- Abusing GDI objects: Bitmap object’s size in the kernel pool
- An Analysis of Microsoft Edge Chakra JavascriptArray TypeId Handling Memory Corruption (CVE-2018-8467)
- An Analysis of the Use-After-Free Bug in the Microsoft Edge Chakra Engine (CVE-2018-0946)
- An Inside Look at CVE-2017-0199 – HTA and Scriptlet File Handler Vulnerability
- ANALYSIS OF A WIN32K NULL POINTER DEREFERENCE BY MATCHING THE MAY PATCH
- Analysis of CVE-2017-11882 Exploit in the Wild
- aPAColypse now: Exploiting Windows 10 in a Local Network with WPAD/PAC and JScript
- Arbitrary Code Guard vs. Kernel Code Injections
- Breaking backwards compatibility: a 5 year old bug deep within Windows
- Breaking out of Restricted Windows Environment
- Bypassing Microsoft's Patch for CVE-2017-0199
- C# Inject a Dll into a Process (w/ CreateRemoteThread)
- CVE-2018-8453 Win32k Elevation of Privilege Vulnerability Targeting the Middle East
- CVE-2018-8460: EXPOSING A DOUBLE FREE IN INTERNET EXPLORER FOR CODE EXECUTION
- DEFEATING DEVICE GUARD: A LOOK INTO CVE-2017-0007
- Delving deep into VBScript - Analysis of CVE-2018-8174 exploitation
- Detecting and mitigating elevation-of-privilege exploit for CVE-2017-0005
- Digging Into a Windows Kernel Privilege Escalation Vulnerability: CVE-2016-7255
- Disarming EMET 5.52: Controlling it all with a single write action
- Enumerating process, thread, and image load notification callback routines in Windows
- EternalBlue – Everything there is to know
- Exploiting a Windows 10 PagedPool off-by-one overflow (WCTF 2018)
- Exploit Kit Rendezvous and CVE-2017-0022
- Exploiting MS16-145: MS Edge TypedArray.sort Use-After-Free (CVE-2016-7288)
- Exploiting MS16-098 RGNOBJ Integer Overflow on Windows 8.1 x64 bit by abusing GDI objects
- Exploring Windows virtual memory management
- EXPLOITING WINDOWS’ IP ID RANDOMIZATION BUG TO LEAK KERNEL DATA AND MORE (CVE-2018-8493)
- From Out Of Memory to Remote Code Execution
- Getting Code Execution on Windows by Abusing Default Kernel Debugging Setting
- Hardening Windows 10 with zero-day exploit mitigations
- Introduction to IA-32e hardware paging
- Introduction to Windows shellcode development – Part 1
- Introduction to Windows shellcode development – Part 2
- Introduction to Windows shellcode development – Part 3
- Kernel Debugging 101 – Part1
- Kernel Debugging 101 – Part2
- Kernel Debugging 101 – Part3
- Kernel Exploitation Case Study - "Wild" Pool Overflow on Win10 x64 RS2 (CVE-2016-3309 Reloaded)
- Kernel Exploit Demo - Windows 10 privesc via WARBIRD
- Kernel Pool Overflow Exploitation In Real World – Windows 7
- Kernel Pool Overflow Exploitation In Real World – Windows 10
- Many Formulas, One Calc – Exploiting a New Office Equation Vulnerability
- Marshalling to SYSTEM - An analysis of CVE-2018-0824
- Microsoft Kills Potential Remote Code Execution Vulnerability in Office (CVE-2017-8630)
- MS17-010: EternalBlue’s Large Non-Paged Pool Overflow in SRV Driver
- MS OFFICE EXPLOIT ANALYSIS – CVE-2015-1641
- ON THE ROAD OF HIDING… PEB, PE FORMAT HANDLING AND DLL LOADING HOMEMADE APIS – PART 1
- ON THE ROAD OF HIDING… PEB, PE FORMAT HANDLING AND DLL LOADING HOMEMADE APIS – PART 2
- ON THE ROAD OF HIDING… PEB, PE FORMAT HANDLING AND DLL LOADING HOMEMADE APIS – PART 3
- ON THE ROAD OF HIDING… PEB, PE FORMAT HANDLING AND DLL LOADING HOMEMADE APIS – LAST PART
- Puppet Strings - Dirty Secret for Windows Ring 0 Code Execution
- Reading Your Way Around UAC (Part 1)
- Reading Your Way Around UAC (Part 2)
- Reading Your Way Around UAC (Part 3)
- Reflective DLL Injection
- Rotten Potato – Privilege Escalation from Service Accounts to SYSTEM
- sam-b/windows_kernel_resources
- Sharks in the Pool :: Mixed Object Exploitation in the Windows Kernel Pool
- Starting with Windows Kernel Exploitation – part 1 – setting up the lab
- Starting with Windows Kernel Exploitation – part 2 – getting familiar with HackSys Extreme Vulnerable Driver
- Starting with Windows Kernel Exploitation – part 3 – stealing the Access Token
- Tales from the MSRC: from pixels to POC
- The Art of Becoming TrustedInstaller
- The lonely potato
- The Unpatched LSASS Remote Denial of Service (MS16-137)
- Using Binary Diffing to Discover Windows Kernel Memory Disclosure Bugs
- Windows 10 Creators Update 32-bit execution of ring-0 code from NULL page via NtQuerySystemInformation (class 185, Warbird functionality)
- Windows Exploit Development (primer) : Debugging Threads and Analyzing Memory
- Windows Exploit Development (primer II) : Corrupting Structured Exception Handling and Controlling Memory Pointers
- Windows Exploitation and AntiExploitation Evolution
- Windows Exploitation Tricks: Arbitrary Directory Creation to Arbitrary File Read
- Windows kernel pool spraying fun - Part 1 - Determine kernel object size
- Windows kernel pool spraying fun - Part 2 - More objects
- Windows kernel pool spraying fun - Part 3 - Let's make holes
- Windows kernel pool spraying fun - Part 4 - object & pool headers, kex & putting it all together
- Windows Kernel Exploitation Part 1
- Windows Kernel Exploitation Part 2
- Windows Kernel Exploitation Part 3
- Windows Kernel Exploitation Tutorial Part 1: Setting up the Environment
- Windows Kernel Exploitation Tutorial Part 2: Stack Overflow
- Windows Kernel Exploitation Tutorial Part 3: Arbitrary Memory Overwrite (Write-What-Where)
- Windows Kernel Exploitation Tutorial Part 4: Pool Feng-Shui –> Pool Overflow
- Windows Kernel Exploitation Tutorial Part 5: NULL Pointer Dereference
- Windows Kernel Exploitation Tutorial Part 6: Uninitialized Stack Variable
- Windows Kernel Exploitation Tutorial Part 7: Uninitialized Heap Variable
- Windows Kernel Exploitation Tutorial Part 8: Use After Free
- Windows Kernel Exploitation – Arbitrary Overwrite
- Windows Kernel Exploitation : This Time Font hunt you down in 4 bytes
- Windows Operating System Archaeology
- Zero Day Zen Garden: Windows Exploit Development - Part 0 [Dev Setup & Advice]
- Zero Day Zen Garden: Windows Exploit Development - Part 1 [Stack Buffer Overflow Intro]
- Zero Day Zen Garden: Windows Exploit Development - Part 2 [JMP to Locate Shellcode]
- Zero Day Zen Garden: Windows Exploit Development - Part 3 [Egghunter to Locate Shellcode]
Exploitation: Technique: Bypassing ASLR
Any related techniques for ASLR bypassing
- Bypass ASLR with partial EIP overwrite
- Bypassing ASLR – Part I
- Bypassing ASLR – Part II
- Bypassing ASLR – Part III
- Bypass ASLR+NX Part 1
- Bypass ASLR+NX Part 2
- Exploit Mitigation Techniques - Address Space Layout Randomization (ASLR)
- New bypass and protection techniques for ASLR on Linux
Exploitation: Technique: Format Strings
Exploitation: Technique: Heap Exploitation
- Heap Exploitation
- Heap Exploitation ~ Fastbin Attack
- Heap Exploitation ~ Abusing Use-After-Free
- Heap overflow using unlink
- Heap overflow using Malloc Maleficarum
- Heap Safari - Thread Local Caching
- shellphishi/how2heap
- X86 EXPLOITATION 101: HEAP OVERFLOWS… UNLINK ME, WOULD YOU PLEASE?
- X86 EXPLOITATION 101: THIS IS THE FIRST WITCHY HOUSE
- X86 EXPLOITATION 101: “HOUSE OF MIND” – UNDEAD AND LOVING IT…
- X86 EXPLOITATION 101: “HOUSE OF FORCE” – JEDI OVERFLOW
- X86 EXPLOITATION 101: “HOUSE OF LORE” – PEOPLE AND TRADITIONS
- Understanding the Heap & Exploiting Heap Overflows
Exploitation: Technique: Integer Overflow
- Integer Overflow
- X86 EXPLOITATION 101: “INTEGER OVERFLOW” – ADDING ONE MORE… AAAAAAAAAAAND IT’S GONE
Exploitation: Technique: Return Oriented Programming
- A ROP Primer solution 64-bit style
- Blind Return Oriented Programming 102
- Interactive Beginner's Guide to ROP
- Intro to ROP: ROP Emporium — Split
- Introduction to Return Oriented Programming (ROP)
- Return-Oriented Programming (ROP) 101
- ROP Emporium
- ROP Primer
- ropchain
- Sigreturn Oriented Programming
Exploitation: Technique: return-to-libc
return-to-libc techniques
Exploitation: Technique: Shellcoding
- A Primer to Windows x64 shellcoding
- Shellcoding for Linux and Windows Tutorial
- SLAE: Bind TCP Shell – Assignment 1
- SLAE: Reverse TCP Shell – Assignment 2
- SLAE: Egg Hunter – Assignment 3
Exploitation: Technique: Stack Exploitation
- Buffer Overflow Explotation
- Classic Stack Based Buffer Overflow
- Exploiting 1-byte buffer overflows
- PLAYING WITH CANARIES
- Simple buffer overflow on a modern system
- [Stack Based Buffer Overflows on x64 (Windows)](Stack Based Buffer Overflows on x64 (Windows))
- Stack Clashing for Fun and Profit
- When is something overflowing
- X86 EXPLOITATION 101: WHEN THE STACK GETS OVER ITS HEAD
- X86 EXPLOITATION 101: BORN IN A SHELL
- X86 EXPLOITATION 101: “HOUSE OF SPIRIT” – FRIENDLY STACK OVERFLOW
- Your First Buffer Overflow
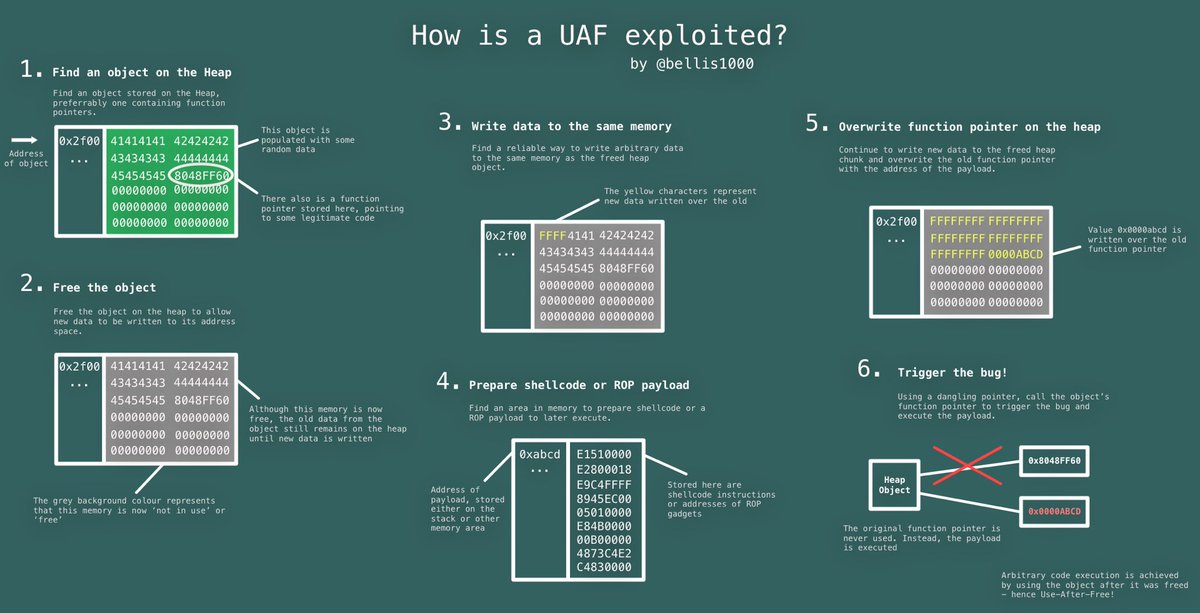
Exploitation: Technique Use-After-Free
Exploitation: Vulnerability: Speculative Side-Channel Attacks
- A Deep Dive Analysis of Microsoft’s Kernel Virtual Address Shadow Feature
- An accessible overview of Meltdown and Spectre, Part 1
- An accessible overview of Meltdown and Spectre, Part 2
- Explainer on #Spectre & #Meltdown
- KVA Shadow: Mitigating Meltdown on Windows
- Post-Spectre Threat Model Re-Think
- Reading privileged memory with a side-channel
- Total Meltdown?
Hardening
Malware Analysis
- A zebra in sheep’s clothing: How a Microsoft icon-display bug in Windows allows attackers to masquerade PE files with special icons
- Add-In Opportunities for Office Persistence
- Anti-debugging Techniques Cheat Sheet
- APT Groups and Operations
- baderj/domain_generation_algorithms - Some results of my DGA reversing efforts
- Borrowing Microsoft Code Signing Certificate
- Detecting Architecture in Windows
- DOSfuscation: Exploring the Depths Cmd.exe Obfuscation and Detection Techniques
- Fast Flux networks: What are they and how do they work?
- FIN7 Group Uses JavaScript and Stealer DLL Variant in New Attacks
- HIDING YOUR PROCESS FROM SYSINTERNALS
- High-reputation Redirectors and Domain Fronting
- How to become the best Malware Analyst E-V-E-R
- Hunting For In-Memory .NET Attacks
- Hunting Malware with Memory Analysis
- If memory doesn’t serve me right…
- MAEC - Malware Attribute Enumeration and Characterization | MAEC Project Documentation
- MikroTik Cryptojacking Campaigns
- PE File Infection Part I
- PE File Infection Part II
- So You Want To Be A Malware Analyst
- Running programs via Proxy & jumping on a EDR-bypass trampoline
- Running programs via Proxy & jumping on a EDR-bypass trampoline, Part 2
- Running programs via Proxy & jumping on a EDR-bypass trampoline, Part 3
- Running programs via Proxy & jumping on a EDR-bypass trampoline, Part 4
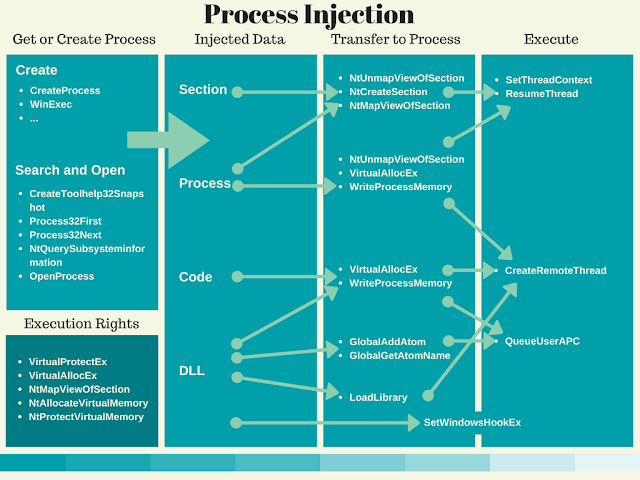
- Ten Process Injection Techniques: A Technical Survey Of Common And Trending Process Injection Techniques
- The Archaeologologogology #3 – Downloading stuff with cmdln32
- ThreatHuntingProject/ThreatHunting
- Tips for Reverse-Engineering Malicious Code
- Understanding Process Hollowing
- Use of DNS Tunneling for C&C Communications
- Attacks on point-of-sales systems
- Another Brick in the FrameworkPoS
- Backoff: New Point of Sale Malware
- Bingo, Amigo! Jackpotting: ATM malware from Latin America to the World
- Buy Candy, Lose Your Credit Card - Investigating PoS RAM Scraping Malware
- Follow The Money: Dissecting the Operations of the Cyber Crime Group FIN6
- New FrameworkPOS variant exfiltrates data via DNS requests
- PoS RAM Scraper Malware - Past, Present, and Future
- RawPOS Technical Brief
Mobile Security
- Four Ways to Bypass iOS SSL Verification and Certificate Pinning
- Mobile Application Hacking Diary Ep.1
- Mobile Application Hacking Diary Ep.2
- tanprathan/MobileApp-Pentest-Cheatsheet
Post Exploitation
Post Exploitation Platform: Linux
Post Exploitation Platform: Windows
- infosecn1nja/AD-Attack-Defense - Active Directory Security For Red & Blue Team
- Nested commands technique: chain multiple commands with
&,&&,|| - Abusing legitimate executables: using legitimate executables to execute intended commands e.g.
Rundll32.exe:rundll32.exe shell32.dll,ShellExec_RunDLL notepad.exe- Program Compatibility Assistant (pcalua):
pcalua.exe -a calc.exe SyncAppvPublishingServer.vbsorSyncAppvPublishingServer.exe:SyncAppvPublishingServer.exe "n; Start-Process notepad.exe"
- Nested commands technique: chain multiple commands with
- Evading Microsoft’s AutoRuns
- Extension search order hijacking: Manipulate extension search order which
.COMhas been looked for first before.EXEby making the actual.EXEdisappeared and place dummy.COMwith the same name as.EXEon the same directory - PowerShell injection vulnerability: Use
SyncAppvPublishingServer.exeto execute powershell cmdlet e.g.SyncAppvPublishingServer.exe ".; Start-Process calc.exe
- Extension search order hijacking: Manipulate extension search order which
- Golden Ticket
- [paranoidninja/CarbonCopy](A tool which creates a spoofed certificate of any online website and signs an Executable for AV Evasion. Works for both Windows and Linux )
- Post Exploitation Using NetNTLM Downgrade Attacks
- Top Five Ways I Got Domain Admin on Your Internal Network before Lunch (2018 Edition)
DCShadow & DCSync
- ACTIVE DIRECTORY ATTACK - DCSHADOW
- DCShadow
- DCShadow - Minimal permissions, Active Directory Deception, Shadowception and more
- DCShadow: Attacking Active Directory with Rouge DCs
- DCShadow explained: A technical deep dive into the latest AD attack technique
Hot Potato
Post Exploitation Platform: Unix/Linux
Privacy
- Digital Privacy at the U.S. Border: Protecting the Data On Your Devices
- Protecting Your Source When Releasing Sensitive Documents
- Secure Journalism at Protests
- Security Education Companion
- Surveillance Self-Defense Checklist
- The Field Guide to Security Training in the Newsroom
- The Wired Guide to Digital Security
Reverse Engineering
- A Gentle Primer on Reverse Engineering
- A Guide to ARM64 / AArch64 Assembly on Linux with Shellcodes and Cryptography
- ELF hacking with Rekall
- FAQ: How to learn reverse-engineering?
- How to decompile any Python binary
- Reverse Engineering 101
Tutorials
Web Application Security
- 0xInfection/Awesome-WAF
- BugBountyProtips ~ Collection
- Gaining access for HTTPS certificate by abusing RFC2142.
- Using
admin@,administrator@,hostmaster@,postmaster@,webmaster@for email address
- Using
- [List of bug bounty writeups](List of bug bounty writeups)
- The 2018 Guide to Building Secure PHP Software
Web Application Security: Technique: CORS
Web Application Security: Technique: Cross-site Request Forgery
Web Application Security: Technique: Cross-site Scripting
Web Application Security: Technique: Serialization/Deserialization
- Understanding Java deserialization
- Why You Should Never Pass Untrusted Data to Unserialize When Writing PHP Code