mirror of
https://github.com/Decentralized-ID/decentralized-id.github.io.git
synced 2024-12-26 23:59:36 -05:00
135 lines
18 KiB
Markdown
135 lines
18 KiB
Markdown
---
|
||
title: Personal Privacy and Self Sovereign Identity
|
||
description: A silent war is ongoing between users and companies over the control of data.
|
||
excerpt: >
|
||
But with challenges in the offing and platforms preparing to do battle, we must all support initiatives that support privacy and security, as well as the services that will bolster it. We must expect better and support the solutions that help us do better.
|
||
layout: single
|
||
toc: true
|
||
toc_sticky: false
|
||
permalink: /self-sovereign-identity/privacy/
|
||
canonical_url: 'https://decentralized-id.com/self-sovereign-identity/privacy/'
|
||
categories: ["About"]
|
||
tags: ["Privacy","Data Privacy"]
|
||
last_modified_at: 2023-06-29
|
||
---
|
||
|
||
## Explainer
|
||
* [What is Privacy?](https://www.windley.com/archives/2022/03/what_is_privacy.shtml) 2022-03 Phil Windley
|
||
> The International Association of Privacy Professionals (IAPP) [defines four classes of privacy](https://iapp.org/resources/glossary/):
|
||
> - Bodily Privacy—The protection of a person's physical being and any invasion thereof. This includes practices like genetic testing, drug testing, or body cavity searches.
|
||
> - Communications Privacy—The protection of the means of correspondence, including postal mail, telephone conversations, electronic mail, and other forms of communication.
|
||
> - Information Privacy—The claim of individuals, groups, or organizations to determine for themselves when, how, and to what extent information about them is communicated to others.
|
||
> - Territorial Privacy—Placing limitations on the ability of others to intrude into an individual's environment. Environment can be more than just the home, including workplaces, vehicles, and public spaces. Intrusions of territorial privacy can include video surveillance or ID checks.
|
||
* [Top 5 Must Read Articles on Data Privacy](https://academy.affinidi.com/top-5-must-read-articles-on-data-privacy-342e95c9dcfc) 2022-04-18 Affinidi
|
||
> To help you get a good grasp of the data privacy concepts and what it means for you, we have put together some relevant articles that make for an interesting read. These articles are sure to give you a whole new perspective of data privacy.
|
||
* [Privacy, Authenticity, and Confidentiality](https://www.windley.com/archives/2022/03/privacy_authenticity_and_confidentiality.shtml) 2022-03 Phil Windley
|
||
> Authenticity allows parties to a conversation to know to whom they are talking. Confidentiality ensures that the content of the conversation is protected from others. These three create a tradespace because you can't achieve all three at the same time.
|
||
* [Identity is evolving — but the battle for privacy has only just begun](https://blog.avast.com/identity-and-the-battle-for-privacy) 2022-03-10 Avast
|
||
> But with challenges in the offing and platforms preparing to do battle, we must all support initiatives that support privacy and security, as well as the services that will bolster it. We must expect better and support the solutions that help us do better. That’s the only way to create a future where privacy and security are at the core of our collective digital experiences.
|
||
* [The new age of privacy](https://werd.io/2021/the-new-age-of-privacy) 2021-01-06 Ben Werdmuller
|
||
> Privacy is a human right. Surveillance has a chilling effect on free speech and freedom of association, which we consider to be fundamental tenets of democracy. Sure, you can make a bunch of money by learning everything you can about an individual and selling access to their attention. But not everything that is profitable should be permissible.
|
||
* [How the cookie poisoned the Web](https://blogs.harvard.edu/doc/2021/05/14/poison/) 2021-05-14 Doc Searls
|
||
> Have you wondered why you have no more privacy on the Web than what other parties grant you ([which is none at all](https://www.linuxjournal.com/content/if-your-privacy-hands-others-alone-you-dont-have-any)), and that you can only opt in or out of choices that others provide—while the only controls you have over your privacy are to skulk around like a criminal (thank you, [Edward Snowden and Russell Brand](https://www.youtube.com/watch?v=2jxdwIkFdj8), for that analogy) or to stay offline completely?
|
||
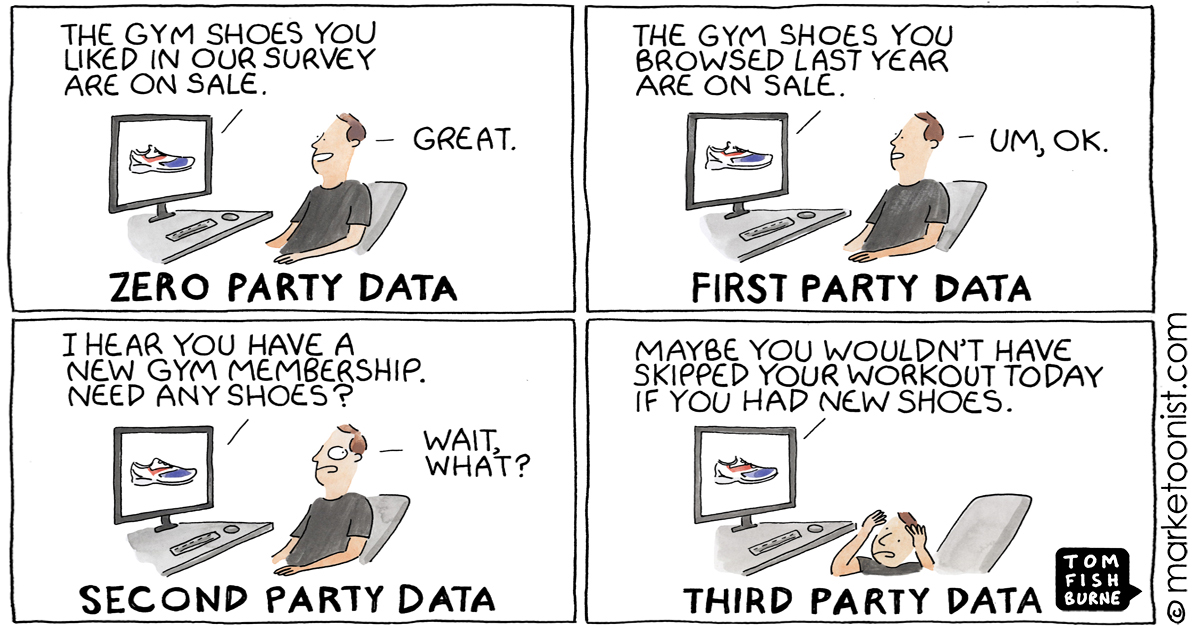
* [the personalization privacy paradox](https://marketoonist.com/2021/07/zeropartydata.html) 2021-05-25
|
||
> 
|
||
> “Zero party data is that which a customer intentionally and proactively shares with a brand. It can include preference center data, purchase intentions, personal context, and how the individual wants the brand to recognize her.”
|
||
|
||
## Self Sovereign Identity
|
||
|
||
* [Decentralized Digital Identity: Shaping the Future of Privacy](https://v3.opennodes.com/2021-06-24-08-33-27-decentralized-digital-identity-shaping-the-future-of-privacy) 2021-04-24 Open Nodes
|
||
> In May, [Tribe](http://www.tribex.co/) held a Clubhouse session with the Dutch Blockchain Coalition (DBC), in partnership with the Singapore Infocomm Media Development Authority (IMDA). Together with representatives from Affinidi, SITA, and Sphereon, the industry players shared their insights on how blockchain is being used to shape the future of privacy, and some practical applications of decentralized digital identity.
|
||
* [Self-Sovereign Identity - The Nash Equilibrium Point of the Personal Identity Information Game](https://www.thoughtworks.com/insights/blog/self-sovereign-identity-nash-equilibrium-point-personal-identity-information-game) 2021-05-07 ThoughtWorks
|
||
> "A silent war is ongoing between users and companies over the control of data."
|
||
> 1. Privacy or convenience is a question
|
||
> 2. SSI is the answer to this question
|
||
* [Verifiable credentials are key to the future of online privacy](https://www.helpnetsecurity.com/2021/07/26/verifiable-credentials/) 2021-07-26 Helpnet
|
||
> they offer a few advantages that we don’t get with paper records. Whereas a physical document (let’s say, a [vaccine card](https://www.helpnetsecurity.com/2021/06/15/vaccine-passports/)) can be forged and [passed off as authentic](https://www.npr.org/2021/06/08/1004264531/fake-covid-vaccine-cards-keep-getting-sold-online-using-one-is-a-crime?t=1626423870877), the [security mechanisms](https://www.evernym.com/blog/the-three-pillars-of-self-sovereign-identity/) behind a verifiable credential means that it can never be tampered with and that anyone shown the credential will be able to immediately verify who issued it and to whom it was issued. 2021-06-08
|
||
* [Self Sovereign e-ID Schemes & Privacy Challenges](https://www.youtube.com/watch?v=1vgNzSDn554) 2021-12-13 Crypto Valley Conference 2021
|
||
> Kurt Nielsen & Nagib Aouini from Partisia Blockchain
|
||
* [Identity and Privacy: Past, Present, and Digital](https://www.slideshare.net/SSIMeetup/identity-and-privacy-past-present-and-digital-brenda-k-leong) 2018-09-21 Brenda K. Leong SSI Meetup
|
||
> Underlying this conversation is the concept of privacy. Is it a fundamental right? What does it mean? Who gets to decide which conveniences are worth the tradeoffs they require? Are the protections for personal data offered by policy and law sufficient, or should technical and security protections be required? Are some systems simply too high-risk to implement regardless of perceived benefits? To answer those questions, it’s important to understand the technologies at work – biometrics such as fingerprints and facial recognition offer greater reliability, security and certainty, but raise fears of “permanent” breach if the personal data is compromised. These systems offer accessibility at scale that can be updated throughout a lifetime in a way that password-based accounts cannot equal. But fair access to all, protections of personal data, and most importantly, legal, policy, and technical protections against discrimination and abuse are critical to ensuring these and related technologies are not simply used to restrict personal freedom, or target groups and other populations. Brenda covers how these and other aspects of the modern concept of “digital identity” are being approached in different ways, and what some of the benefits and risks are for the future.
|
||
* [Zero-Knowledge Proofs: Privacy-Preserving Digital Identity](https://www.slideshare.net/SSIMeetup/zeroknowledge-proofs-privacypreserving-digital-identity-with-clare-nelson) 2018-10-12 Clare Nelson SSI Meetup
|
||
> Clare will explain why ZKPs are so powerful, and why they are building blocks for a range of applications including privacy-preserving cryptocurrency such as Zcash, Ethereum, Artificial Intelligence, and older versions of Trusted Platform Modules (TPMs). The presentation includes many backup slides for future learning and researching, including four slides of references.
|
||
|
||
## Policy
|
||
* [UNDP LEGAL IDENTITY AGENDA ONLINE FORUM: PRIVATE SECTOR ENGAGEMENT ROUNDTABLES: DATA PROTECTION AND PRIVACY](https://unstats.un.org/LEGAL-IDENTITY-AGENDA/MEETINGS/2021/UNLIA-FUTURETECH/DOCS/REPORT2.PDF) 2022-07-13 UNStats
|
||
> A second Private Sector Engagement Roundtable was held on February 10, 2022 building on the first roundtable held in May 2021. The forum drew 74 virtual participants. Hosted by the UN Legal Identity Agenda (LIA) Task Force1, the roundtable with members of UN entities and the private technology sector addressed, core questions about data protection and privacy, as well as policy issues concerning legal identity systems.
|
||
* [Letter to Attorney General Becerra Re: FinCen Proposed Rule Privacy concerns](https://blockadvocacy.medium.com/letter-to-attorney-general-becerra-re-fincen-proposed-rule-privacy-concerns-d6706694b8a9) 2021-02-23 Ally Medina BlockAdvocacy
|
||
> Our concerns with the consumer privacy implications of this proposed rule are twofold:
|
||
>
|
||
> First, the proposed rule’s requirement that MSB’s collect identifying information associated with wallet addresses will create reporting that extends well beyond the intent of the rule or the transaction.
|
||
|
||
## Business
|
||
* [The business of Privacy is Booming](https://www.axios.com/2021/11/09/privacy-business-booming-protonmail-you-search) 2021-11-09
|
||
> Investors and consumers show growing enthusiasm for privacy-focused alternatives to Google and Facebook amid renewed scrutiny over the real cost of their "free" services.
|
||
* [The Rising Consumer Demand for Data Privacy and Autonomy](https://medium.com/sequoia-capital/the-rising-consumer-demand-for-data-privacy-and-autonomy-b8254bf3368e) 2021-11-19 Sequoia
|
||
> Increased supply of user-friendly private tech and increased demand for privacy have converged, creating a moment of unprecedented opportunity for founders with a vision for privacy-first online experiences.
|
||
|
||
## Development
|
||
* [Why Privacy by (Re)Design Better Defines Responsibility for Privacy](https://anonyome.com/2021/09/why-privacy-by-redesign-better-defines-responsibility-for-privacy/) 2021-09 Anonyome
|
||
> Where privacy by design puts the onus on app developers to be proactive about data privacy, privacy by (re)design redesigns the “app ecosystem to address data sharing”, spreading the burden.
|
||
* [Can Consent Ever Play a Valuable Role in Consumer Privacy?](https://anonyome.com/2021/08/can-consent-ever-play-a-valuable-role-in-consumer-privacy/) 2021-08 Anonyme
|
||
> Can we rely on ‘informed consent’ if the informed part is largely missing?\
|
||
> Consent doesn’t scale well from the consumer’s perspective.
|
||
* [Reciprocal Negotiated Accountability](https://www.windley.com/archives/2021/06/reciprocal_negotiated_accountability.shtml) 2021-06-21 Phil Windley
|
||
> The self-sovereign internet underscores a tension between those who desire perfect oversight of society and those who desire perfect privacy. In this post, I explore a method for conditional legibility of private communications.
|
||
* [Agency By Design (Privacy is not Enough)](https://iiw.idcommons.net/20B/_Agency_By_Design_(Privacy_is_not_Enough)) 2021-05-06 Adrian Gropper
|
||
> I’m not a fan of Privacy by Design.\
|
||
> In the industry are only concerned about compliance, very rarely talk about Human Agency\
|
||
> Privacy by Default is the opposite in some sense to privacy by design\
|
||
> The problem is that It conflict with community in many cases. (e.g. social credit score)\
|
||
> Cultural differences (EU accepts better centralization than US)\
|
||
> Delegation and agency are one the same thing\
|
||
> Agency is a much bigger thing and delegation is a mechanism that supports it\
|
||
> I want my fiduciaries to know as much as possible of me (e.g. my doctor, my lawyer) \
|
||
> Model Agency as hierarchy and delegation is the mean to have it.
|
||
* [Understand the ORGANS Framework Before Building Privacy-Preserving Apps](https://academy.affinidi.com/understand-the-organs-framework-before-building-privacy-preserving-apps-cfc00e00a90c) 2022-08-23 Affinidi
|
||
> - O -> Open Standards
|
||
> - R -> Revocable by individuals
|
||
> - G -> Granular
|
||
> - A -> Auditable
|
||
> - N -> Notice to all parties involved
|
||
> - S -> Secure
|
||
* [Data Privacy: does anyone care?](https://blog.meeco.me/data-privacy-does-anyone-care/) 2021-09-15 Meeco
|
||
> The compelling data and research suggest that my original question now needs to be reframed. People most certainly do care about their data privacy. The question now is: how are organisations going to bridge this data privacy chasm?
|
||
* [Provisional Authenticity and Functional Privacy](https://www.windley.com/archives/2022/03/provisional_authenticity_and_functional_privacy.shtml) 2022-03 Phil Windley
|
||
> Provisional authenticity and confidentiality can help us manage the trade offs between privacy and authenticity to support online accountability along with functional privacy.
|
||
|
||
## Application
|
||
* [Use Sudo Platform’ Decentralized Identity Capabilities to Rapidly Deliver Customer Privacy Solutions](https://anonyome.com/2022/04/how-your-business-can-rapidly-deliver-customer-privacy-solutions-with-the-sudo-platform-a-5-part-series%ef%bf%bc/) 2022-04 Anonyme
|
||
> In this 5-part series, we’ll look at how enterprises can rapidly deliver customer privacy solutions with the Sudo Platform digital identities and decentralized identity capabilities.
|
||
* [Revoke](https://revoke.com/personal/how-it-works/)
|
||
> Revoke allows you to send requests to retrieve and/or delete your data.
|
||
> - Each company has 30 days to respond under the GDPR.
|
||
> - Revoke gives you full visibility and control of what to do with that information.
|
||
> - Easy to use app helps you discover who hold yours personal information.
|
||
* [Exposed documents reveal how the powerful clean up their digital past using a reputation laundering firm](https://restofworld.org/2022/documents-reputation-laundering-firm-eliminalia/) 2022-02 Rest of World
|
||
> Reputation firms like Eliminalia use legal threats and copyright notices to have material taken down around the world.
|
||
>
|
||
> From the we can’t talk about ourselves without ®’s camp
|
||
|
||
## Privacy Violations
|
||
* [Businesses need to ‘mind the trust gap’ so users don’t need to sacrifice privacy, MEF Global Consumer Trust Survey finds](https://blog.digi.me/2021/05/20/businesses-need-to-mind-the-trust-gap-so-users-dont-need-to-sacrifice-privacy-mef-global-consumer-trust-survey-finds/) 2021-05-20 Digi.me
|
||
> - Users sacrifice privacy and security for access to valued services
|
||
> - Smartphone users begin to sense improvement in the mobile environment
|
||
> - More and more users take protective steps, but remain exposed to harm
|
||
> - Protective actions do not necessarily drive confidence
|
||
> - Cost, knowledge and perceived complexity are key barriers
|
||
> - Transparency and control are key values for users
|
||
* [Privacy Harms](https://teachprivacy.com/privacy-harms/) 2021-02-09 Daniel Solove Teach Privacy
|
||
> This article makes two central contributions. The first is the construction of a road map for courts to understand harm so that privacy violations can be tackled and remedied in a meaningful way.
|
||
* [John Oliver on Surveillance Capitalism](https://www.windley.com/archives/2022/04/john_oliver_on_surveillance_capitalism.shtml) 2022-04 Phil Windley
|
||
> In researching this story, we realized that there is any number of perfectly legal bits of f—kery that we could engage in. We could, for example, use data brokers to go phishing for members of congress, by creating a demographic group consisting of men, age 45 and up, in a 5-mile radius of the U.S. Capitol, who had previously visited sites regarding or searched for terms including divorce, massage, hair loss and mid-life crisis.
|
||
* [Google Sued for Misleading Users Over Location Data Privacy](https://anonyome.com/2022/03/google-sued-for-misleading-users-over-location-data-privacy/) 2022-03 Anonyme
|
||
> “Google falsely led consumers to believe that changing their account and device settings would allow customers to protect their privacy and control what personal data the company could access. The truth is that contrary to Google’s representations it continues to systematically surveil customers and profit from customer data.”
|
||
* [Report] [Me2BA Product Testing Spotlight Report Published: Data Sharing in Primary & Secondary School Mobile Apps](https://me2ba.org/me2ba-product-testing-spotlight-report-published-data-sharing-in-primary-secondary-school-mobile-apps-2/) 2021-05-04 Me2Ba
|
||
> 60% of School Apps are Sending Student Data to Potentially High-risk Third Parties Without Knowledge or Consent According to New Research from Me2B Alliance
|
||
* [Someone could be tracking you through your headphones](https://nrkbeta.no/2021/09/02/someone-could-be-tracking-you-through-your-headphones/) 2021-09-02 NRK Beta
|
||
> - At least 9149 products with Bluetooth transmitters were uniquely recognized at least 24 hours apart.
|
||
> - At least 129 headphones could be tracked in the dataset for longer than 24 hours.
|
||
> - Popular headphones models from Bose, Bang & Olufsen, Jabra, Sennheiser and JBL can be tracked over longer periods of time.
|
||
* [Links Between Privacy and Disinformation: Julia Angwin](https://anonyome.com/2021/07/the-links-between-privacy-and-disinformation-julia-angwin/) 2021-07
|
||
> Privacy, as we know, is a complex topic. When it converges with technology, it becomes more complicated. One aspect of this complexity is where privacy fits in with disinformation—false or misleading information spread intentionally to confuse or manipulate people.
|
||
* [Literature] [Privacy Risks With Opioid Recovery Apps](https://www.expressvpn.com/digital-security-lab/opioid-telehealth-research) 2021-07-07 ExpressVPN
|
||
> Perhaps the most alarming revelation from our study of ten opioid addiction treatment and recovery apps is the consistent access of unique identifiers, given the sensitivity of privacy around health and substance use issues.
|