mirror of
https://github.com/Decentralized-ID/decentralized-id.github.io.git
synced 2025-09-19 20:24:47 -04:00
toc: sticky False
This commit is contained in:
parent
663a4fdb97
commit
7b3c6c80b3
19 changed files with 35 additions and 22 deletions
|
|
@ -301,7 +301,7 @@ defaults:
|
|||
share: true
|
||||
related: true
|
||||
toc: true
|
||||
toc_sticky : true
|
||||
toc_sticky: false
|
||||
# _posts
|
||||
- scope:
|
||||
path: "_posts"
|
||||
|
|
@ -320,9 +320,9 @@ defaults:
|
|||
classes: wide
|
||||
related: true
|
||||
toc: true
|
||||
toc_label : "Contents"
|
||||
toc_icon : "link"
|
||||
toc_sticky : true
|
||||
toc_label: "Contents"
|
||||
toc_icon: "link"
|
||||
toc_sticky: false
|
||||
- scope:
|
||||
path: "_posts/companies"
|
||||
type: posts
|
||||
|
|
|
|||
|
|
@ -5,7 +5,7 @@ description: Self-Sovereign Identity for Humanitarian Interventions
|
|||
excerpt: >
|
||||
When forced to flee your home from one moment to the next, grabbing birth certificates, school diplomas, and other papers that prove you are who you say you are might not be the first thing that comes to mind. And without those credentials, everything is more difficult when it comes to starting a new life or picking up the pieces of an old one
|
||||
toc: true
|
||||
toc_sticky: true
|
||||
toc_sticky: false
|
||||
permalink: /application/humanitarian/
|
||||
redirect_from:
|
||||
- /organizations/humanitarian/
|
||||
|
|
|
|||
|
|
@ -5,7 +5,7 @@ description: The current model for connected things puts manufacturers in betwee
|
|||
excerpt: >
|
||||
Safety and security rests with all involved in authorizing updates, how and when they are applied as well as the right to repair when Things are no longer officially supported. Shared device lifecycle assurance is the basis for verifiable service histories of Things which give data provenance. When data can be proven to originate from reliable sources, its value increases while reducing the risk of using it. Enabling third parties to build value from data would unlock the true value of IoT which in turn could fund its upkeep. This talk will outline how identity and shared ledger technology have key roles to building Truth in Things for a sustainable IoT.
|
||||
toc: true
|
||||
toc_sticky: true
|
||||
toc_sticky: false
|
||||
permalink: /application/IOT/
|
||||
tags: ["IOT","Digital Twins","MOBI","ITN","European Commission","Peaq","Microsoft","LFPH","Sophie Project","Digital Twin Consortium","Venafi","Caution"]
|
||||
categories: ["Uses"]
|
||||
|
|
|
|||
|
|
@ -13,7 +13,7 @@ categories: ["Blockchain"]
|
|||
tags: ["NIST","Identiverse",Authenteq,Blockstack,Civic,Microsoft,Datum,ProCivis]
|
||||
last_modified_at: 2023-06-09
|
||||
toc: true
|
||||
toc_sticky: true
|
||||
toc_sticky: false
|
||||
---
|
||||
|
||||
## Literature
|
||||
|
|
|
|||
|
|
@ -10,7 +10,7 @@ categories: ["Decentralized Web"]
|
|||
tags: ["PICO","IOT"]
|
||||
last_modified_at: 2023-06-09
|
||||
toc: true
|
||||
toc_sticky: true
|
||||
toc_sticky: false
|
||||
---
|
||||
|
||||
## Explainer
|
||||
|
|
|
|||
|
|
@ -10,7 +10,7 @@ categories: ["Development"]
|
|||
tags: ["Biometrics"]
|
||||
last_modified_at: 2023-06-09
|
||||
toc: true
|
||||
toc_sticky: true
|
||||
toc_sticky: false
|
||||
---
|
||||
|
||||
## Explainer
|
||||
|
|
|
|||
|
|
@ -5,7 +5,7 @@ excerpt: >
|
|||
description: the mere fact of building such a verifiable and traceable architecture does not automatically translate into understandable communications
|
||||
layout: single
|
||||
toc: true
|
||||
toc_sticky: true
|
||||
toc_sticky: false
|
||||
permalink: /development/user-experience/
|
||||
canonical_url: 'https://decentralized-id.com/development/user-experience/'
|
||||
redirect_from:
|
||||
|
|
|
|||
|
|
@ -4,7 +4,7 @@ excerpt: >
|
|||
In chaotic systems such as those that the discipline of physics seeks to describe, there is also the concept of the “self-organizing principle,” which dictates a tendency for chaotic systems to organize themselves. While this might be a tendency in physics, organization usually needs a nudge in the right direction in the identity world.
|
||||
description: Authentication and authorization both fall under identity and access management (IAM) but serve different purposes.
|
||||
layout: single
|
||||
toc: false
|
||||
toc: true
|
||||
permalink: /development/architecture/
|
||||
canonical_url: 'https://decentralized-id.com/development/architecture/'
|
||||
categories: ["Development"]
|
||||
|
|
@ -12,6 +12,7 @@ tags: ["Architecture"]
|
|||
last_modified_at: 2023-06-23
|
||||
---
|
||||
|
||||
## General
|
||||
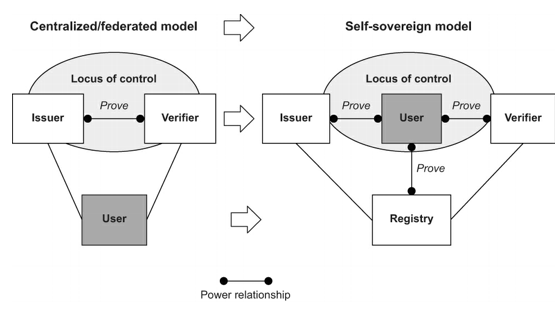
* [Centralized\Federated vs Self Sovereign](https://twitter.com/dominiumssi/status/1564188374529081345) 2022-08-29 dominiumssi
|
||||
> Anyone who wants to understand DID and Self Sovereign Identity should begin by understanding the graph below. We are shifting the power from the companies to the users. That's it in a nutshell.
|
||||
> 
|
||||
|
|
@ -65,3 +66,15 @@ last_modified_at: 2023-06-23
|
|||
> 3. Sybil-resistant — identity is subject to scarcity; i.e., creating more identifiers cannot be used to manipulate a system2.
|
||||
* [Self-Sovereign vs Administrative Identity](http://blogs.harvard.edu/vrm/2012/03/25/ssi/) 2012-03-25 Doc Searls
|
||||
> The problem I’m trying to surface here is that we need full respect for self-sovereign identities, and identifiers, before we can solve the problem of highly fractured and incompatible administrative identifiers — a problem that has only become worse with the growth of the Web, where by design we are always the submissive and dependent party: calves to administrative cows.
|
||||
|
||||
|
||||
## Decentralized Public Key Infrastructure DPKI
|
||||
* [Decentralized Public Key Infrastructure](https://github.com/WebOfTrustInfo/rebooting-the-web-of-trust/blob/master/final-documents/dpki.pdf) 2015-12-24 rwot1
|
||||
> Today’s Internet places control of online identities into the hands of third-parties. Email addresses, usernames, and website domains are borrowed or "rented" through DNS, X.509, and social networks. This results in severe usability and security challenges Internet-wide. This paper describes a possible alternate approach called decentralized public key infrastructure (DPKI), which returns control of online identities to the entities they belong to. By doing so, DPKI addresses many usability and security challenges that plague traditional public key infrastructure (PKI). DPKI has advantages at each stage of the PKI life cycle. It makes permissionless bootstrapping of online identities possible and provides for the simple creation of stronger SSL certificates. In usage, it can help “Johnny” to finally encrypt thanks to its relegation of public key management to secure decentralized datastores. Finally, it includes mechanisms to recover lost or compromised identifiers.
|
||||
|
||||
### Related
|
||||
* [SCPKI: A Smart Contract-based PKI and Identity System](http://www0.cs.ucl.ac.uk/staff/M.AlBassam/publications/scpki-bcc17.pdf)
|
||||
* [KeyChains: A Decentralized Public-Key Infrastructure](https://drum.lib.umd.edu/bitstream/handle/1903/3332/0.pdf?sequence=1&isAllowed=y)
|
||||
* [ClaimChain: Decentralized Public Key Infrastructure](https://www.researchgate.net/publication/318584251_ClaimChain_Decentralized_Public_Key_Infrastructure)
|
||||
* [A Decentralized Public Key Infrastructure with Identity Retention](https://eprint.iacr.org/2014/803.pdf)
|
||||
* [Privacy based decentralized Public Key Infrastructure (PKI) implementation using Smart contract in Blockchain](https://isrdc.iitb.ac.in/blockchain/workshops/2017-iitb/papers/paper-11%20-%20Decentralized%20PKI%20in%20blockchain%20and%20Smart%20contract.pdf)
|
||||
|
|
|
|||
|
|
@ -5,7 +5,7 @@ excerpt: >
|
|||
description: "concept of individual control over identity relevant private data"
|
||||
layout: single
|
||||
toc: true
|
||||
toc_sticky: true
|
||||
toc_sticky: false
|
||||
permalink: /development/ethics-rights-sovereignty/
|
||||
canonical_url: 'https://decentralized-id.com/development/ethics-rights-sovereignty/'
|
||||
categories: ["Development"]
|
||||
|
|
|
|||
|
|
@ -5,7 +5,7 @@ excerpt: >
|
|||
Self-Sovereign Identity not only presents an opportunity for businesses to build smarter, more secure, and more scalable relationships with customers; but it will enable them to completely rethink how they build trusted digital relationships from the ground up.
|
||||
layout: single
|
||||
toc: true
|
||||
toc_sticky: true
|
||||
toc_sticky: false
|
||||
permalink: /development/business/
|
||||
canonical_url: 'https://decentralized-id.com/development/business/'
|
||||
categories: ["Development"]
|
||||
|
|
|
|||
|
|
@ -7,7 +7,7 @@ layout: single
|
|||
categories: ["Development"]
|
||||
tags: ["Wallets","User Experience"]
|
||||
toc: true
|
||||
toc_sticky: true
|
||||
toc_sticky: false
|
||||
permalink: /development/wallets/
|
||||
canonical_url: 'https://decentralized-id.com/development/wallets/'
|
||||
last_modified_at: 2023-07-01
|
||||
|
|
|
|||
|
|
@ -9,7 +9,7 @@ canonical_url: https://decentralized-id.com/government/india/
|
|||
categories: ["Government"]
|
||||
tags: ["India","Aadhaar","Hyperledger","Orgbook"]
|
||||
toc: true
|
||||
toc_sticky: true
|
||||
toc_sticky: false
|
||||
last_modified_at: 2023-06-07
|
||||
---
|
||||
|
||||
|
|
|
|||
|
|
@ -5,7 +5,7 @@ excerpt: >
|
|||
We should absolutely all be taking care of the data that belongs to us, our data that we create, that we have a right to be able to control and share exactly as we choose. But we should also bear in mind the power of that data to help each of us, every day, benefit from the good that can come when it is shared and used to create a better world for us all.
|
||||
layout: single
|
||||
toc: true
|
||||
toc_sticky: true
|
||||
toc_sticky: false
|
||||
permalink: /self-sovereign-identity/data-governance/
|
||||
canonical_url: 'https://decentralized-id.com/self-sovereign-identity/data-governance/'
|
||||
categories: ["About"]
|
||||
|
|
|
|||
|
|
@ -5,7 +5,7 @@ excerpt: >
|
|||
But with challenges in the offing and platforms preparing to do battle, we must all support initiatives that support privacy and security, as well as the services that will bolster it. We must expect better and support the solutions that help us do better.
|
||||
layout: single
|
||||
toc: true
|
||||
toc_sticky: true
|
||||
toc_sticky: false
|
||||
permalink: /self-sovereign-identity/privacy/
|
||||
canonical_url: 'https://decentralized-id.com/self-sovereign-identity/privacy/'
|
||||
categories: ["About"]
|
||||
|
|
|
|||
|
|
@ -6,7 +6,7 @@ excerpt: The Sovrin Foundation is a private-sector, international non-profit tha
|
|||
layout: single
|
||||
classes: ""
|
||||
toc: true
|
||||
toc_sticky: true
|
||||
toc_sticky: false
|
||||
header:
|
||||
image: "/images/sovrin-header.webp"
|
||||
og_image: /images/sovrin-foundation.webp
|
||||
|
|
|
|||
|
|
@ -5,7 +5,7 @@ title: MyData
|
|||
excerpt: >
|
||||
We are entrepreneurs, activists, academics, listed corporations, public agencies, and developers. For years, we’ve been using different words for what we do – MyData, Self Data, VRM (Vendor Relationship Management), Internet of Me, PIMS (Personal Information Management Services) etc, while sharing a common goal: to empower individuals with their personal data, thus helping them and their communities develop knowledge, make informed decisions, and interact more consciously and efficiently with each other as well as with organisations.
|
||||
toc: true
|
||||
toc_sticky: true
|
||||
toc_sticky: false
|
||||
categories: ["Organizations"]
|
||||
tags: ["MyData","eIDAS","GDPR","Meeco","JLinc","Verifiable Credentials","OAuth","AI","DKMS","Avast","MyDex","Cozy Cloud","Data Governance"]
|
||||
redirect_from: organizations/mydata
|
||||
|
|
|
|||
|
|
@ -8,7 +8,7 @@ excerpt: >
|
|||
These firms decided to pool their resources and create open-source blockchain technology that anyone could use. These far-sighted companies are helping blockchain to become a more popular and industry-standard technology.
|
||||
layout: single
|
||||
toc: true
|
||||
toc_sticky: true
|
||||
toc_sticky: false
|
||||
permalink: blockchain/hyperledger/
|
||||
redirect_from:
|
||||
- organizations/hyperledger/
|
||||
|
|
|
|||
|
|
@ -4,7 +4,7 @@ description: Linux Foundation Public Health's response to the Covid-19 pandemic
|
|||
excerpt: After initial success with deploying exposure notification apps, LFPH started to host CCI in December 2020 to advance the use of Verifiable Credentials (VCs) and data and technical interoperability of VCs in the public health realm, starting with vaccine credentials.
|
||||
layout: single
|
||||
toc: true
|
||||
toc_sticky: true
|
||||
toc_sticky: false
|
||||
permalink: application/covid-19/lfph_cci_good-health-pass/
|
||||
redirect_from:
|
||||
- organizations/covid-credentials-initiative/
|
||||
|
|
|
|||
|
|
@ -10,7 +10,7 @@ header:
|
|||
categories: ["Resources"]
|
||||
tags: ["Literature","Resources"]
|
||||
toc: true
|
||||
toc_sticky: true
|
||||
toc_sticky: false
|
||||
redirect_from:
|
||||
- literature
|
||||
- literature/
|
||||
|
|
|
|||
Loading…
Add table
Add a link
Reference in a new issue