89 KiB
| published |
|---|
| false |
Explainer
Self Sovereign Identity
- What is Self Sovereign Identity 2021-10-13 Florian Strauf
The important thing in SSI is that instead of a stamp on the plastic card, the credential is signed cryptographically by the issuer, enabling anyone to verify who issued the credentials. This makes verification much easier than in the physical world.
- Decentralizing Identity - Taking Back Control 2021-10-13 Madigan Solutions
In a nutshell, Self-Sovereign Identity allows individuals to manage their own identities by moving physical credentials to digital devices. An individual will receive a credential from an issuer which will be stored in their digital wallet.
- 17 Things You Should Know About Self Sovereign Identity 2021-10-29 Colin Iles
lessons I took away from asking tech identity experts Andrew Baker (Head of EC2 Engineering at AWS), our mystery guest and Marius Mare, to why we need self-sovereign identity and why it has such profound implications.
- Is Self Sovereign Identity Going Exponential - With Andrew Baker and A Suprise Guest 2021-10-27 Colin Iles
despite the technological revolution we are living through, identity management is still as objectionable as ever, which is allowing criminals and companies (particularly the social media giants) to know more about you than can ever be justifiable.
In this discussion I ask Andrew Baker, AWS's Head of EC2 Engineering and a surprise guest, to share their views on whether Self Sovereign Identity management could be the solution and how likely it is
- Digital Identity: The Trending Tech Concept Changing How We Live 2021-10-15 Forbes
Identification is key to our success. It determines the jobs we get, the money we make, how we can manage our health, and more. The fact of the matter is that 3.4 billion people have access to legally recognized identification but still have difficulty using that identification online.
- Self-Sovereign Identity: a Primer 2021-08-03 Hartmut Obendorf
Digital trust is often centralised, with select, well-known entities providing an anchor of trust that is propagated to everyone else; you are using this mechanism as you read this paragraph, having accessed a https: URL to find this article on your trusted platform, Medium.
- Why self-sovereign identity matters 2020-04-29 GlobalID
your digital identity represents you as a unique real-life person in a secure digital format. In fact, we likely have many different virtual identities across a spectrum of platforms and services.
- The Principles of User Sovereignty 2020-07-31 UXDesign
“Our identities have no bodies, so, unlike you, we cannot obtain order by physical coercion. We believe that from ethics, enlightened self-interest, and the commonweal, our governance will emerge. Our identities may be distributed across many of your jurisdictions. The only law that all our constituent cultures would generally recognize is the Golden Rule. We hope we will be able to build our particular solutions on that basis. But we cannot accept the solutions you are attempting to impose.” — John Perry Barlow
- Distributed, Decentralized, Self-Sovereign Identity 2021-04-22 Condatis
With DID already being implemented, this new and exciting technology is due to shake up the digital identity space. We expect decentralized identity to continue making headway, with more and more sectors and businesses adopting the technology.
- Introduction to Self-Sovereign Identity 2021-03-28 Jakubkoci
In this article, I will do my best to explain self-sovereign identity from the end-user perspective, without any technicalities.
- Kaliya Young on Identikit with Michelle Dennedy 2021-08-25 IdentityWoman
our latest series examining the evolution of digital identity, and how self-sovereign identity, specifically, can advance a consent-based economy.
- Decentralized Identity Trilemma
There seems to exist a trilemma in decentralized identity analogous to @Zooko's triangle. None of the existing solutions are at the same time: 1) privacy-preserving, 2) Sybil-resistant 3) self-sovereign -[T]
- Self Sovereign Identity — explained 2020-11-11 Micha Roon
It would be great indeed if digital interactions became even more trustworthy without the need to present our data on a silver platter to large Internet corporations
- When a user holds his:her own credentials locally on the phone, it creates a three-sided market 2020-12-04 Lissi ID
which puts the holder of the credential in the position of a carrier between issuer and verifiers.
- The Mental Models of Identity Enabled by SSI 2020-12-03 Adrian Doerk The Models: Space Time • Presentation • Attribute • Relationship • Capability
- Why is SSI becoming a necessity and what potential it holds? 2020-11-12 ACEBlock
- Natural persons and legal entities interact in the digital world with the same freedom and capacities as in the offline world (e. g. signing, authorizing documents, validating signatures, communicating privately etc.)
- Data is stored privately on a user device and not replicated numerous times across the digital world.
In other words, when a user “shares” data, it shares only the access to his/her data. And, as easy as one can do that, they can also revoke it (unless they are legally bound to share it for a certain period).
- The Implications of Bring Your Own Identity Identity Defined Security Alliance 2020-12-03
My short stint as “Mark Jannell" taught me a lot of about trust and ease of use in a bring your own identity model. Trust, as always in security, is essential to this new class of relationships and must be established and then protected from abuse. Ease of use, it turns out, is a key factor in protecting that trust and promoting the adoption of good identity patterns. I’m sure that I could have learned these lessons in some other way, but I’ll never forget my half year answering to a pseudonym.
- Evolution of Self-Sovereign Identity (SSI) 2021-11-16 LionsGate
The public keys of the user and the third-party organization for verifying the digital signature are recorded in a distributed ledger, and the user of the identity information verifies the provided information using them. In this way, users can control their own identity information without relying on a specific central administrator.
- Self-Sovereign Identity Crisis 2021-11-23 Lionsgate
Through deceptive marketing practices the first-movers in the Digital ID market have done-away with the sovereignty. As a result a burgeoning new industry is experiencing a Self-Sovereign Identity Crisis.
- Trusted Third Parties vs Self-Sovereign Identity 2021-12-30 Affinidi
All of us have multiple identities at any point. We are sons, daughters, brothers, sisters, parents, partners, friends, colleagues, and more to different people.
- A Future Built on Decentralized Identity 2021-12-22 Bloom
Decentralized identity is an emerging concept becoming more popular for online consumers by eliminating the need to pass personal identifiable information (PII) to an ever-increasing number of companies. However, in practice, decentralized identity has only existed for a handful of years, and its potential is still being discovered. So how did we get here?
- SSI Essentials: Everything you need to know about Decentralized Identity 2021-11-29 Gataca
Solving the identity paradox: the tradeoff between privacy, security, & user experience
- Self-Sovereign Identities in Productive Systems - A Reality Check 2021-11-25 Frankfurt School Blockchain Center
- Which use cases does SSI have?
- What is the disruptive potential of SSI’s?
- Which risks does the adoption of SSI pose?
- What are the challenges and opportunities of SSI?
- Where do the limitations of SSI lie?
- How can SSI be incorporated into existing infrastructure?
- Which steps need to be taken for the proliferation of SSI?
- What is Self Sovereign Identity 2021-10-13 Florian Strauf
the digital representation of the identification process we know from the physical world. Things like showing our driver’s license to prove we are allowed to drive, or sending a bank statement to a real estate agent to prove our income and account balance.
- Self Sovereign Identity Explainer 2021-12-17 DIDAS Swiss (PDF
The Self Sovereign Identity Explainer (in German) is the basis for the future discussions and in-depth learning. It briefly introduces the development history of digital identity and roughly describes the different phases of identity in the Internet age.
- What Is Self-Sovereign Identity? 2020-04-28 Trinsic
Self-sovereign identity is the marriage of real identity with the digital world that will ultimately make people’s lives better.² It’s still in its infancy, and there is a long road ahead to truly make digital identity as legitimate and nuanced as a real-world identity.
- Explaining SSI to C-suite executives, and anyone else for that matter – John Phillips 2020-02-18 SSIMeetup
John Phillips from 460degrees in Australia has been exploring with his team for more than two years for a way to describe Self-Sovereign Identity (SSI) that was easy to understand. We think he has found a good method to make SSI easy to understand for any C-suite executive and business people that goes beyond the technology.
- Self-Sovereign Identity: The Ultimate Beginners Guide! 2021-02-23 101 Blockchains
Apart from addressing the pitfalls in conventional identity management systems, SSI allows better functionalities for all users. With a wide range of benefits and the self-sovereign identity blockchain applications, it is important to take a step towards adopting SSI solutions.
- Understanding the SSI Identity Model with Verifiable Credentials 2021-11-13 Manning
Drummond Reed, an expert in Internet identity, security, privacy, and trust frameworks, explains the basic building blocks of SSI and how this new identity model fundamentally works.
- The 5P’s of a Self-Sovereign Identity 2019-06-05 Dr Mark van Rijmenam
A self-sovereign identity can be defined by the 5P’s as it is personal (it is about you), portable (meaning you can take your identity and data from one platform to another), private (you control your identity and data), persistent (it does not change without your consent) and protected (they cannot steal your identity).
- Digital identities – steps on the path to an ID ecosystem 2021-03-18 Bankenverband
This article is very very good in articulating the big picture of how SSI systems relative to older system and emerging fragmetned systems.
An answer to these challenges is an ecosystem in which digital identity data can be exchanged in a way that is secure, reliable, scalable and convenient. This will have a positive impact on the economic future of Germany and Europe while at the same time enhancing the private sphere of the individual.
- A beginner’s guide to self-sovereign identity (SSI) 2021-06-02 Domilabs
An issuer makes claims or assertions about a user. These claims are bundled together into verifiable credentials and given to the user, who stores them in their digital wallet. From there, they can decide which verifiers they want to present these credentials to.
- Self-Sovereign ID (SSI), The Unhackable Digital ID: What It Is and How It Works 2021-04 MemberPass
- The Siloed Model: The organization owns the member information, not the member.
- The Federated Model: The identity providers (IDP) owns the member data, not the member.
- The Best Model: SSI • The members own their own data!
- Karyl Fowler (Transmute) and Juan Caballero (DIF) present Intro to SSI at #IIW31 2020-10 Keryl Fowler, Juan Caballero Slides
Karyl and Juan revisited their slide deck from #IIW30 to give an overview of decentralized identity first as a "philosophy" at the confluence of ideological currents (Juan), and then as a set of specific emerging technologies which unlocks new mental models and business models that are still coming into focus sector by sector (Karyl). There follows a brief overview of educational resources, including some products of DIF's recent educational "content sprint," and a wide-ranging Q&A including podcast recommendations and how to navigate open standards for the first time. The slides are here, in downloadable and hyperlinked PDF form:
- [Podcast] Defining Self-Sovereign Identity with Kaliya Young 2021-06-02 Coding Over Cocktails
In this short preview, "Identity Woman" and digital identity advocate Kaliya Young tackles the issues around self-sovereign identity and how individuals are the rightful points of federation in sharing and controlling their online information.
- 19 FAQs on Verifiable Credentials and Self-Sovereign Identity 2021-05-31 Affinidi
This article has some FAQs on the basics of Verifiable Credentials (VCs) and Self-Sovereign Identity (SSI).
- Self-Sovereign Identity: What You Can/Can’t Do With SSI? 2021-06-24 Affinidi
it gives complete control and ownership of data to the individual entities as they can decide what data to share and with whom.
Beyond this encompassing vision, let’s drill down into the specifics to understand what you can and can’t do with SSI.
- A Digital Identity Revolution Tracey Follows
In order to better understand the benefits and drawbacks of such a verification system, we have to look at the future and work backward to make the right decisions today.
- The Basic Building Blocks of SSI 2020-07-29 Drummond Reed, Alex Preukschat Manning
In many cases these core concepts have been established for decades. What’s new is how they’re put together to create a new model for digital identity management. The purpose of this article is to quickly familiarize you with these seven basic building blocks from a conceptual and technical point-of-view.
- Verifiable credentials (aka digital credentials)
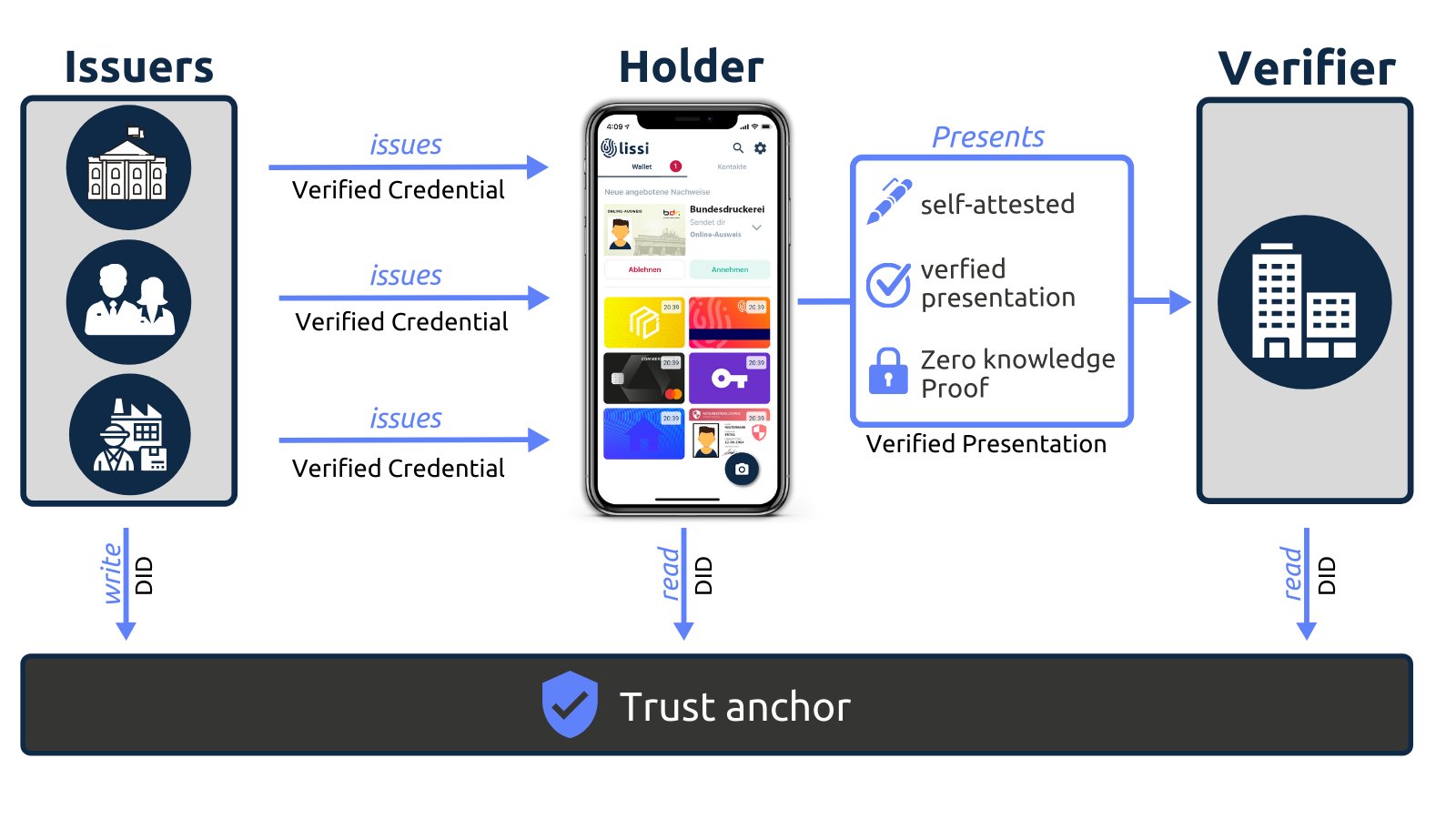
- Issuers, holders, and verifiers
- Digital wallets
- Digital agents and hubs
- Decentralized identifiers (DIDs)
- Blockchains
- Governance frameworks (aka trust frameworks)
- How to decentralize identity and empower individuals 2021-07-26 GlobalID
If the internet decentralized information and crypto decentralized money and payments, then verifiable credentials will decentralize identity. In this episode, we chat with Dev Bharel, the software architect leading the charge around verifiable credentials at GlobaliD.
- Self-Sovereign Identity: What’s the Big Deal? 2021-07-06 Affinidi, Hackernoon
Do you know where your digital credentials like your full name, date of birth, phone number, government ID, and other Personally Identifiable Information (PII) are stored online, and how they are used?
- The Role of Identity in Creating a Better Internet with Kaliya Young — Structure 3C 2021-11-21 CoHere
Kaliya talking with a colleague from way back Bill Johnston.
On this episode of the Cohere podcast, Kaliya joins Bill to discuss the history of online identity, what events led us to the consolidation of identity into a few centralized platforms, and what steps we need to take to recover and protect our online identities.
- Bright Story: Self Sovereign Identity 2019-05-05 Brightlands (EN)
the benefits (The good) of SSI are illustrated with a range of examples, comparing SSI-based business transactions to their current non-SSI-based equivalents and thus more cumbersome.
In addition, examples are given of the disadvantages (The bad); how SSI technology can be misused by unscrupulous organizations and how a combination of technology, knowledge and legislation could mitigate this risk.
Finally, we give examples of the harmful side (The ugly); how SSI technology can be used by criminals and what countermeasures are possible.
- How Verifiable Creds, Decentralized Identifiers and Blockchain Work Together for a Safer Internet 2021-08-22 Fluree, Hackernoon
Verifiable credentials, DIDs, and blockchain are evidence of what's to come: Web3, a more secure, widespread, machine-to-machine internet.
- Beyond basics: Expert Q&A about SSI with Dr. Milly Perry and Martin Schäffner 2021-06-01
In May, Dr. Milly Perry, blockchain expert and former research director at the Open University of Israel, had invited Martin Schäffner, the initiator of the SSI Working Group at the European Blockchain Association, to speak at a webinar of the Israeli Chamber of Information Technology (You can find the recording here). [...] Here is their exchange about Verifiable Credentials, biometrics, pitfalls and barriers, NFTs, the role of governments and the thing that could make SSI obsolete.
- Self-Sovereign Identity Allows YOU to Control Your Personal Data 2022-12-13 Imageware
SSI supports credential leveling, including:
- Authentication Assurance Levels (AAL) 1, 2 & 3
- Biometrics to protect your data
- Affirmation/Metadata SSI credentials can be used:
- In person or online
- For government, financial, or high trust applications (document verification markets)
- For asset ownership, decentralized finance (DeFi), and crypto markets
Security
- ID Verification Threats On the Horizon 2022-03-31 Liminal Podcasts
Cognito's CEO Alain Meier joins the State of Identity host Cameron D’Ambrosi to dive into why industries beyond financial services are now in the market for identity verification. They also unpack the impact of synthetic identity fraud across verticals, and how platforms find the balance when building their onboarding processes.
- How Decentralized Identifiers Will Shape the Future of Identity 2020-11-09 HackerNoon
Hackers value personal information the most. 96% of hacking groups’ primary motive is intelligence gathering. Researchers at privacy website PrivacyAffairs.com found that you can obtain a person's full identity for the low price of $1,275.
- Security, Silos, and Sovereignty 2021-03-12 Daniel Hardman
Why portable security is the sleeper — but killer — feature for SSI
what’s cool about DIDs (besides their self-service creation) is that their metadata is cryptographically verifiable. That means that anyone in the world can tell whether the metadata is legit, in the blink of an eye, just by asking software to check some math. And it also means that you can build a transport-independent, tamper-proof, encrypted communication channel with whoever controls a DID.
Cryptography
- Privacy-Preserving Authentication, Another Reason to Care about Zero-Knowledge Proofs —slideshare 2017-08-14 Clare Nelson
In the near future, privacy-preserving authentication methods will flood the market, and they will be based on Zero-Knowledge Proofs. IBM and Microsoft invested in these solutions many years ago.
- How to Explain Public-Key Cryptography and Digital Signatures to Anyone
Here’s an easy-to-understand analogy to help your non-technical friends and customers understand public keys and private keys, and how they relate to cryptography and digital signatures.
- Zero Knowledge Proofs 2021-11 Phil Windley
This problem was first explored by MIT researchers Shafi Goldwasser, Silvio Micali and Charles Rackoff in the 1980s as a way of combatting information leakage. The goal is to reduce the amount of extra information the verifier, Victor, can learn about the prover, Peggy.
System Architecture
- Good Welfare, Bad Platforms?: The Risks of Centralized Digital Identity Systems 2022-02-02 OpenID
As S. Shakthi and I noted in a recent research paper, digital identity systems are widely seen as datafiers by virtue of their core property of reducing the person to machine-readable data. A datafier is a system that performs the crucial operation of converting the physical into digital. A different, contrasting view is also emerging in research: digital identity systems are increasingly seen as platforms, i.e. “technological building blocks” on which different types of complements can be constructed.
- Identity management is key to increasing security, reducing fraud and developing a seamless customer experience 2022-01-07 Identity Praxis
- Identity management is an iterative process with three core elements – initial identification, authentication (re-identifying the individual) and verification (ensuring the individual is who they claim to be)
- Enterprises employ a vast array of technologies to execute these processes which are growing in scope and complexity
- Understanding why identity management is necessary to enterprises and how this creates opportunities for vendors
- Leveraging the Identity Metasystem 2021-12 Phil Windley
the metasystem guarantees the fidelity of the credential exchange. Credential fidelity comprises four important attributes. Credential exchange on the identity metasystem:
- Reveals the identifier of the issuer
- Ensures the credential was issued to the party presenting it
- Ensures the credential has not been tampered with
- Reveals whether or not the credential has been revoked
- Token-Based Identity 2021-10 Windley
Token-based identity systems move us from talking about who, to thinking about what, so that people can operationalize their digital lives. Token-based identity systems support complex online interactions that are flexible, ad hoc, and cross-domain.
- Your User is Your API 2021-05-17 Evernym
The customer becomes the integration point. The customer is the API. Rather than having one huge, expensive, and probably illegal data hub, every customer becomes a data hub in their own right. They provide the data needed, just-in-time, under their control.
- The Unbundling of Authentication vs Authorization - What You Need to Know 2021-09-08 Ping Identity
Authentication and authorization are both processes that fall under the category of identity and access management (IAM), but they serve different purposes.
- To Better Understand Digital Identity, Look to Physics 2021-05-17 Ping
In chaotic systems such as those that the discipline of physics seeks to describe, there is also the concept of the “self-organizing principle,” which dictates a tendency for chaotic systems to organize themselves. While this might be a tendency in physics, organization usually needs a nudge in the right direction in the identity world. Proper attention to requirements and a good change control process are a crucial part of the equation.
- The SSO Practitioner’s Introduction to Decentralized Identity
Written for IAM professionals familiar with federations.
In most self-sovereign and decentralized identity systems the trust model is fundamentally unidirectional, where a verifier will trust the issuer, but the issuer may have no knowledge of the verifier.
- The Architecture of Identity Systems 2020-09 Phil Windley
We can broadly classify identity systems into one of three types based on their architectures and primary root of trust:
- Administrative
- Algorithmic
- Autonomic
- Authentic Digital Relationships 2020-08 Phil Windley
Self-sovereign identity (SSI) systems offers an alternative model that supports richer relationships. Rather than provisioning identifiers and accounts in an administrative system where the power imbalance assures that one party to the relationship can dictate the terms of the interaction, SSI is founded on peer relationships that are co-provisioned by the exchange of decentralized identifiers. This architecture implies that both parties will have tools that speak a common protocol.
- Self-Sovereign vs Administrative Identity 2012-03-25 Doc Searls
The problem I’m trying to surface here is that we need full respect for self-sovereign identities, and identifiers, before we can solve the problem of highly fractured and incompatible administrative identifiers — a problem that has only become worse with the growth of the Web, where by design we are always the submissive and dependent party: calves to administrative cows.
- Fluid Multi-Pseudonymity 2021-09-07 Windley
Fluid multi-pseudonymity perfectly describes the way we live our lives and the reality that identity systems must realize if we are to live authentically in the digital sphere.‘
- What Is Zero Trust? Ping
- The network is always assumed to be hostile.
- External and internal threats exist on the network at all times.
- Network locality is not sufficient for deciding trust in a network.
- Every device, user and network flow is authenticated and authorized.
- Policies must be dynamic and calculated from as many sources of data as possible.
- What's the difference between identification, authentication and authorization? 2021-05-26 Adrian Doerk
- Identification: Who are you?
- Authentication: Is it you again?
- Authorization: What rights do I want to grant you?
Related
- Understanding Digital Credentials BCdiploma
We are freeing ourselves from the management of “data hash” which leads to a centralization or complexification of verification procedures. This makes our solution new compared to traditional blockchain applications on the market.
- DIGITAL SOVEREIGNTY 2021-05-05 Doc Searls, Aaron Newcomb FLOSS WEEKLY
Dr. Andre Kudra of esatus.com discusses SSI, or Self-Sovereign Identity. It's a hot and fast-moving topic with a growing base of hackers, companies, nonprofits, and whole states, provinces and countries. Aaron Newcomb and Doc Searls probe Andre for lots of great intelligence about how SSI puts individuals in full charge of how they present minimized ID credentials safely, and inside a whole new framework. They also talk with Andre about his involvement with the demoscene and retro computing, which are especially huge in Europe. It's a great discussion on this episode of FLOSS Weekly.
- An Introduction to Digital Trust 2021-09-06 Northern Block
what’s the purpose of SSI? It’s about enabling Digital Trust (which is quickly becoming an integral part of digital transformation for organizations).
- Badges and Credentials – A new currency for the digital world? 2021-11-12 Speexx Exchange
Listen to this episode for an entertaining deep dive into the topic of badges and credentials, as Donald Taylor sits down with Dr. Doug Belshaw to discuss the importance, various fields of application
Business
- New Indicio Executive Workshop Provides Essential Grounding in Digital Identity: The Business and Investor’s Guide to Self-Sovereign Identity 2021-12-14 Scott Harris
Participants will walk away with an essential understanding of how SSI works, the pain points it solves for, the risks it mitigates, the use cases currently in deployment, and the opportunities that are created by being able to build Trusted Data Ecosystems (TDEs).
- Who Controls Your Digital Identity? SAP 2021-02-18
SSI will have to be integrated with large existing business processes – and therefore enterprise systems such as ERPs, HCMs, or SCMs to name a few. If this integration results in SSI being as easy to use as clicking a button or selecting a menu item, it will lead to rapid uptake and acceptance.
Development
-
[resources] Getting Started with Self Sovereign Identity SSI 2021-03-29
The blog is my getting started with Self Sovereign identity. I plan to explore developing solutions using Self Sovereign Identities, the different services and evaluate some of the user cases in the next couple of blogs.
-
Bootstrapping a VDR-based Fully Decentralized Object (FDO)/Credential Platform: VON Example 2021-07-26 Hyperonomy
What are the common/known strategies for bootstrapping a VDR-based decentralized credential/object platform? …asked naively on purpose. Strategies for placing the first/initial DIDs in the VDR? …presumably purposed to be the initial Issuer(s) of verifiable
-
Challenges to Self-Sovereign Identity 2021-10-11 Damien Bod
I based my findings after implementing and testing solutions and wallets with the following SSI solution providers:
- Trinsic
- MATTR.global
- Evernym
- Azure Active Directory Verifiable Credentials
- Different Wallets like Lissi
-
#SSI gives its owner control over some aspects of identity, but not all 2021-12-14 Jolocom
Connections, relationships, and third-party issued credentials are not entirely self-sovereign, nor should they be. #JolocomAdvent #AdventCalendar
-
What are Verifiable Credentials? Why do they matter? 2022-01-10 Fluree
Authority Does Not Require Centralized Power
As mentioned in my previous article, the trouble with centralization is that data is stored in a database. Once breached, a database can yield a treasure chest of information to be sold on the dark web.
-
What Are Verifiable Credentials? And How Can They Build Digital Trust? 2022-02-01 Salesforce
Verifiable credentials and verifiable credential management technology offer a direct and secure channel between an organization and its stakeholders. Learn how they bring control over digital identity and build trust with organizations – from health credentials to college degrees.
-
The Decentralized Identity Schelling Point Sarah Baldeo
Back to the Schelling Point - communication requires a common language and understanding. As governments, banks, hospitals, etc. navigate how best to homogenize authenticating user identities in multiple contexts, solutions will depend on user adoption. Maximizing adoption requires avoiding a Schelling point by creating a shared, accessible, and evolving Decentralized Identity Lexicon.
-
Self-Sovereign Identity (SSI) Explained Animo
In this video, we explain how third parties get to see a lot of personal information about you that they don't really need. Whether it is your local supermarket or your new job, you're often sharing a lot of data when all they really need is a very simple yes or no answer.
-
Self Sovereign Identity Explainer DIDAS
With this presentation we start the Self-Sovereign Identity journey for all Swiss people.
We look forward to exploring further relevant topics with you in the near future!
-
Privacy, Authenticity, and Confidentiality Phil Windely
Authenticity allows parties to a conversation to know to whom they are talking. Confidentiality ensures that the content of the conversation is protected from others. These three create a tradespace because you can't achieve all three at the same time.
-
Verifiable Credentials explained Smart Degrees
Verifiable Credentials, its infrastructure (European Blockchain Services Infrastructure, EBSI), and the vast opportunities that it currently provides, through a user’s journey (“Eva’s trip”).
-
Impacts from a new reality drive the need for an enhanced digital identity framework Bank Automation News
Consumers will benefit in instances such as loan processing (with accompanying credit check verification) or when establishing a new bank account or a new internet contract (with identity and residency manual verification).
Service providers may benefit, as they will be able to minimize fraudulent account creation and simultaneously protect both parties from phishing attacks.
-
On the @IAlsoPodcast, partner Charlyn Ho discusses w/hosts @nicolekyle and @SophieWHolm #digitalidentity, how #blockchain empowers users to take control of their data, #privacy under #Web2 vs. #Web3, and more. Tune in 🎧: https://apple.co/3IvGVjr. #womenintech #ialsowantmoney
-
Blockchain for Decentralized Identity — Self-Sovereign Identity De-mystified Anita Rao
Web 3.0 presents a promise to address the above issues with Identity. The term Web 3.0 refers to a decentralized internet that uses crypto tokens. Decentralization is at the heart of Web 3.0 which has the potential to democratize technology and put the users in control of their data.
-
My first attempt at a business blockchain flowchart JonRamvi
Any feedback would be greatly appreciated. Thank you
- Volume 10, Issue 2 : Glossary of decentralized technosocial systems Internet Policy Review
Self-sovereign identity Definition <-its quite good
Self-sovereign identity (SSI) is rooted in the belief that individuals have the right to an identity independent of reliance on a third-party identity provider, such as the state or any other central authority. Its implementation requires the development of technical standards, as well as socio-political adaptations rooted in legal amendments in order to be successful.
-
SSI: self-sovereign identity explained Cheqd
Unlike the existing system, it’s a user-centric and user-controlled approach to exchanging authentic data in a much more secure way. Authentic data is information that’s source can be proven.
-
Passwordless Authentication – Everything You Need to Know
When it comes to authentication, passwords were once the safest and most used methods of authentication
-
Decentralized identities ≠ blockchain Jolocom
Decentralized digital identities are only possible due to cryptography. One of the cornerstones is asymmetric encryption. A key pair is generated using a cryptographic process. The pair consists of a public and a private key. As the names suggest, the private key must remain private and the public key can be shared.
-
Self-Sovereign Identity (SSI) Foam Figure Explainer v2 - this time with two cameras John Phillips
-
Three approaches to Self-Sovereign Identity based on blockchain
In this short article, we investigate three different approaches to how SSI concepts map on the blockchain infrastructure.
- [...]
The third approach is, in a way, derived from the previous one, and is the one pursued by uPort/Serto: the blockchain has one single registry that tracks down just the revocation of credentials,
-
The Buzz Behind Zero Trust State of Identity
The Zero Trust model is the belief that no one should be trusted from inside or outside your network, until their identity has been verified. Zero trust refers to the alignment of maturing identity practices, an established understanding of user behaviors, and the application of least-privilege access security policy decisions to trust boundOaries
-
8 Benefits of Multi-Factor Authentication (MFA) Ping
Multi-factor authentication takes it step further by requiring users to provide proof from two or more authentication factors (categories) before access is granted.
-
Challenges to Self Sovereign Identity Damien Bod 2021-10-11
The article goes through some of the challenges we face when using or implementing identity, authentication and authorization solutions using self sovereign identity. I based my findings after implementing and testing solutions and wallets with the following SSI solution providers: Trinsic MATTR.global Evernym Azure Active Directory Verifiable Credentials Different Wallets like Lissi SSI
-
Our Ultimate Guide to Authentication: Types, Mechanisms, Forms, Protocols and More Ping Identity
When organizations employ authentication factors and protocols in a well-thought-out manner, users can still have excellent experiences while security administrators and auditors know operations are being executed securely. As we have seen, there are a number of ways to provide these services in any organization.
-
ID Token and Access Token: What Is the Difference?
"Let’s use a token to secure this API call. Should I use the ID token or the access token? 🤔 The ID token looks nicer to me. After all, if I know who the user is, I can make better authorization decisions, right?"
-
Self-Sovereign Identity Foundations, Applications, and Potentials of Portable Digital Identities
Fraunhofer Institute for Applied Information Technology FIT, Project Group Business & Information Systems Engineering
-
What is the Trust Triangle? Affinidi
The relationship between the issuers, holders, and verifiers is called the trust triangle simply because you need an element of trust among these entities for them to work together.
-
Do You Need Blockchain for Enabling SSI? Affinidi
We hope this will get you thinking about enabling SSI using an option that best suits your application or business requirement.
-
Identities Evolve: Why Federated Identity is Easier Said than Done SSRN
This paper shows that federated identity is really a radical and deeply problematic departure from the way we do routine business. Federation undoes and complicates long standing business arrangements, exposing customers and service providers alike to new risks that existing contracts are unable to deal with. Identity federations tend to overlook that identities are proxies for relationships we have in different contexts. Business relationships don’t easily “interoperate."
-
Verifiable credentials are key to the future of online privacy Helpnet 2021-07-26
they offer a few advantages that we don’t get with paper records. Whereas a physical document (let’s say, a vaccine card) can be forged and passed off as authentic, the security mechanisms behind a verifiable credential means that it can never be tampered with and that anyone shown the credential will be able to immediately verify who issued it and to whom it was issued. 2021-06-08
-
Selective Disclosure: Share Just What You Want Affinidi
In the context of SSI, selective disclosure is best implemented through verifiable credentials where the user has separate credentials for each piece of information such as his/her date of birth, full name, vaccination details, address, passport number, etc.
-
IDENTOS prepares customers for verifiable credentials Identos
Rather than trying to paste everything and everyone together, the path forward to help build trusted ecosystems relies on interoperability and leveraging existing assets while positioning the user in a disintermediated model of control and agency — possible with FPX and verifiable credentials.
Sebastian Gebski's Reviews > Self-Sovereign Identity: Decentralized Digital Identity and Verifiable Credentials by Alex Preukschat, Drummond Reed
highly recommended. I strongly believe that the concept of SSI will be extremely important in the future - that's actually one of the few implementations on the blockchain that make a lot of sense.
-
Techno-Feudalism Is Taking Over
Meanwhile, digital platforms have replaced markets as the locus of private wealth extraction. For the first time in history, almost everyone produces for free the capital stock of large corporations. That is what it means to upload stuff on Facebook or move around while linked to Google Maps…. But while capitalism may end with a whimper, the bang may soon follow. If those on the receiving end of techno-feudal exploitation and mind-numbing inequality find a collective voice, it is bound to be very loud.
-
The Working Principles of 2FA (2-Factor Authentication) Software Auth0
There’s a lot of “magic” happening under the hood of how software 2FA works. Today, we’re going to peel back the curtains and see how it works, how the codes are generated, what it protects and doesn’t protect from.
-
Blockchain, The Missing Piece In Self-Sovereign Digital Identity Modex Tech Modex, one of the earliest players in the blockchain market, has utilized its trademark Blockchain Database (BCDB) solution to develop PatientDataChain, a working proof of concept that utilizes the unique characteristics of blockchain to create a patient-centric ecosystem that gives patients control and ownership of their medical records and identity.
-
What Is Authentication? 1Kosmos
Authentication is the process of proving that a user is who they claim to be to access system resources or features. Typically, this calls for some type of proof, whether that is a physical piece of information, a secret piece of information or some other immutable form of evidence.
-
Self-Sovereign Identity: What You Can/Can’t Do With SSI? Affinidi
-
DID 101: A Brief Introduction to What Makes Ontology Special
-
New to the topic of self-sovereign identity? SSIAmbassador
No problem, there are several beginner #guides, which you can use to get familiar with the new standard for digital #identity.
-
What Are Self-Sovereign Identities (SSI)? Europechain
In this context, ‘self-sovereignty’ refers to the ability of the individual or the organization in control of the identity to share it and present it to other agencies with no intermediaries.
-
Digital signatures, a fast track to digital transformation in the real estate sector
The implementation of the electronic signature was a major development in the development in management.
99% of our documents are digitally signed digitally and we have eliminated many face-to-face meetings.
-
7 Benefits Of Using Digital Identities Europechain
Mobile First • Establish Framework of Trust • Smart City Access • Digital Economy • Financial and Social Inclusion • Enhanced Portability
-
Comparing X.509 Certificates with SSI Windley
X.509 certificates have been around for 40 years and have proven to be a trustworthy means of exchanging data. So, what are the differences between X.509 ceritificates and SSI? And what are the advantages of each?
-
Sovrin’s 12 Principles of Self-Sovereign Identity
Representation • Interoperability • Decentralization • Control & Agency • Participation • Equity and Inclusion • Usability, Accessibility, and Consistency • Portability • Security • Verifiability and Authenticity • Privacy and Minimal Disclosure • Transparency
-
Let’s throw a widely accepted definition out there. According to Wikipedia, ‘A digital identity is information on an entity used by computer systems to represent an external agent. That agent may be a person, organization, application, or device.’
-
Part 2: How DIDs Can Enable True Customer Centricity
By using Decentralized Identifiers (DIDs) – creating a unique identifier for each and every different relationship – customers can seamlessly set up a new, highly secure, two-way channel with the business
-
Part 3: Digital Wallets and Digital Agents: Putting the Individual in Control Evernym
Fittingly, some define wrath as “when anger is directed against an innocent person, and when it is unduly strong or long-lasting.” That feels right if you consider the real-life impacts of disabling someone’s digital identity without notice.
-
Part 4: Getting on the Right Data Diet with Verifiable Credentials
Apparently gluttony means “overconsumption to the point of waste.” Sadly that feels apt when it comes to customer data APIs.
-
Part 5: How Zero-Knowledge Proofs (ZKPs) Enable Smarter Customer Insights, With Less Liability
Put simply, most organizations are unthinkingly collecting more data from customers, without understanding the true impact: the real costs to themselves, and to customers.
* 6: Breaking Down Silos with Open Ecosystems and True Data Portability
Every company providing a new digital identity solution believes that all the other digital identity options are not good enough, not secure enough, not fast enough. They believe they can do better.
Yet collaboration will be critical to making digital identity work properly at scale.
-
Part 7: Envy Counting The Cost of Data Collection, And A New Paradigm Of ‘Identity Holder Present’
It all feels like data envy to me. Aristotle described envy as the pain at the sight of another’s good fortune, stirred by “those who have what we ought to have.” Precisely.
-
Seven Ways Self-Sovereign Identity Can Enable True Digital Transformation: A CODA
“Self-Sovereign Identity not only presents an opportunity for businesses to build smarter, more secure, and more scalable relationships with customers; but it will enable them to completely rethink how they build trusted digital relationships from the ground up.”
We expect Digital Transformation to be a more prevalent talking point around digital identity. FOMO can go a long way, to sell SII, for Goverments and Corporations striving to not be left behind in the digital age. This is excellent work, with lots of references, by Dr. Nuttawut Kongsuwan (Finema & QTFT), and Rachata Tosirisuk (Thailand Internet Exchange, Finema & QTFT).
- The Verifiable Credential’s Model
At the core of every self-sovereign identity (SSI) use case is what we call the verifiable credentials model. This simple yet effective model helps conceptualize how verifiable credentials are exchanged between people and organizations.
New major white paper by Phil Windley with the Blockchain Research Institute
the relationship view of identity, the nature of authentic digital relationships, the trust bases of identity systems, and the architecture of the identity metasystem, including decentralized identifier communication and the self-sovereign Internet. He then explores how to operationalize digital relationships and the potential of generative identities (e.g., verifiable credentials) and credential exchange. He concludes with a deep dive into self-sovereign identities in production: the UK National Health Service staff passport, Bonifii’s MemberPass for credit unions, the International Air Transport Association Travel Pass, and others.
-
The Era of Self-Sovereign Identity ChakRay
Similar actions conducted in person do not represent the same amount of risk. For example, if someone asks you to verify your identity, we show our ID or driver’s license, and when you pay at the store, you provide your bank card. In this way, the control and the ownership of the data stays with you.
-
Blockchain Self-Sovereign Identity: True Control Of Your Identity Komodo Platform
The adoption of verifiable credentials is another fundamental part of the SSI concept. Verifiable credentials use a digital signature for identity claims by combining public-key hashing cryptography and privacy-protection techniques to convert credentials like ID cards to digital versions.
-
[Video] Exploring the Decentralized Web, Episode 4: Digital Identity Filecoin Foundation
Episode 4 explores the relationship between authentication and authorization, the rise of single sign-on platforms, and the advantages of and use cases for self-sovereign identity. Guests include Brian Behlendorf, Rainey Reitman, Danny O'Brien, Sarah Friend, Wendy Hanamura, Andrew Hill, and Brad Kam.
(the) Use Case
How does this change the world of cybersecurity protection? Typically, bad actors approach cybersecurity attacks by developing solutions that exploit the attack vectors of their target victims.
There are 4 attack vector categories to self-sovereign identity that map directly to each element: Issuer, Holder, Trust Registry and Verifier.
Identity Proofing
- SSI & Proof of Reputation Catalyst Swarm
Join Frank Albanese (Snapbrillia), Lance Byrd (RootsID), Nick Mason (ProofSpace), Niels Kijf (Design Academy), Patrick Suzzi (F8 OSDE), Juan Sierra (HERG), Zoéys Welt, Brian Harper, Ashton Engberg, Ninh Tran (Snapbrillia) and many others as the community discusses the different what is SSI & Proof of Reputation and why it matters.
Presentation: https://bit.ly/3OmuIRx
-
Advocating for learner-centric badge systems We Are Open Coop
how do we advocate for learner-centric badge systems? This is the piece that we’ve been thinking about the past couple of weeks.
-
Crafting a “no-bs” SSI platform Aditya Santhanarn
Let’s look at a few pointers that I believe make it hard for the web3 protocols to work for businesses and users in general
-
Digital Wallet Systems: What is true decentralization ? Thrivacy
True decentralization in the digital world means that once verified, your PII is on your phone and under your control. The data doesn’t live anywhere else.
-
Self-Sovereign Identity (SSI) & Atala PRISM with Allison Fromm Cardano Catalyst Women
-
0:02:58 What is Identity?
-
0:04:14 Problems with Digital Identity
-
0:08:38 Solution: Self-Sovereign Identity (SSI)
-
0:15:55 Getting Started with SSI: A Catalyst Proposal
-
0:20:11 Conclusion
-
0:22:20 Core team
-
0:24:05 Questions
-
Unwrapping the Decentralised Identity Landscape Affinidi Podcast: Digital Identity and Self Sovereignty Kaliya Young & Lucy Yang -Future of You
- The tools Kaliya and Lucy are developing to enable self-sovereign identities
- Whether anonymity or pseudonymity is feasible while maintaining accountability
- Wallet Wars: how might wallets evolve and consolidate across the public and private sector
-
Decentralization is the Future of Digitization Jolocom
Digital identity data is introduced as having a positive impact on Germany’s future as well as Europe’s. Following, benefits of a decentralized identity based on a fully open infrastructure are given.
-
What Will We Learn from the Market Failure of Digital Identity? Identiverse
We have a widely accepted Standard Model of Identity, or architecture, in which Subjects, Identity Providers and Relying Parties (aka Holders, Issuers and Verifiers) hold, present, exchange, use and/or consume digital identities.
-
The World’s First Verifiable Credentials Steve Wilson
Commonly associated with blockchain and the Self-Sovereign Identity movement, Verifiable Credentials are in fact an old idea. It is instructive to break down their essential properties and examine the pioneering examples.
-
myths and facts. Is Self-Sovereign Identity Dangerous? Jolocom (in german)
we examine more closely whether self-sovereign identity can increase or reduce risks for data misuse in certain cases.
-
Digital Identity Conspiracies ContinuumLoop
The only ones who will benefit from your digital ID are the Issuer (who gave you the credential), holder (you) and verifier (who you’re sharing it with).
-
Compare and Contrast — Federated Identity vs Self-sovereign Identity Affinidi
-
What is Self-Sovereign Identity? Tangle Labs
-
Digital sovereignty: Reclaiming your private data in Web3 Cointelegraph
this is a collaborative effort — one bigger than a single individual or organization — and the whole Web3 space should work together.
-
SteveWilson Considering SSI critics
I reckon most cases of over-identification stem either from bad habits (e.g. RPs gathering circumstantial AuthN signals) or from Surveillance Capitalism. Either way, better deals for users will come from better design, not by weaponising Digital Identity (SSI, DIDs).
-
Understanding Verifiable Credentials Credivera
The value of verifiable credentials and the critical role they will play to our future digital identities is undeniable. As we enter a new era of online representation, trust in the internet will need to be vigorously robust.
-
More security does not have to mean less user-friendliness Martin Kuppinger, Tagesspiegel
The passwords that have been declared dead are far from dead. Nevertheless, the way in which users authenticate themselves is changing towards more security and convenience.
-
Never mind who I am, ask me about my credentials John Phillips
Many (most) identity systems make a fundamental assumption that is built into their very architecture. This assumption creates three significant problems: privacy erosion; toxic data stores; and poor security.
-
Digital Identity Convenience Christine Martin, Continuum Loop
You will take back control of your identity and hold it. Not Facebook, not Google, and you will decide what credentials to share on a need-to-know basis. We don’t have to be scared of the shift; we have to ensure the architecture is built ethically for all
-
Understanding Verifiable Credentials by Credivera
The value of verifiable credentials and the critical role they will play to our future digital identities is undeniable. As we enter a new era of online representation, trust in the internet will need to be vigorously robust.
-
Rewiring the Internet with Self-Sovereign Identities.
In “Self-Sovereign Identity,” Johannes Sedlmeir makes a clear distinction between two concepts too often mixed: “identity” and “identifiers”. What we are experiencing in today’s Web are some external organizations identifying us as citizens, community members, customers, etc. But this isn’t our “identity.” Those are identifiers.
-
Digital Identities and Verifiable Credentials Johannes Sedlmeir • Reilly Smethurst • Alexander Rieger • Gilbert Fridgen Published October 2021
-
Myths about SSI Jolocom
The idea that as a user of SSI I have complete sovereignty over my digital identity is often misunderstood. At its core, SSI is about my digital identity being under my own control, so I can decide to whom I show my data, when, and for what.
-
Getting Data Security Right Alan Michel
data security is about system-wide design, where many different elements need to fit together to create a working whole.
-
What is Self-Sovereign Identity (SSI) with PeterMcCormack @justinrezvani (short clip)
-
Understanding Online Identity EducatedGuessWork (broad contextualization)
-
ISO/TR 23249:2022 – Overview of existing DLT systems for identity management ISO
- The 5P’s of a Self-Sovereign Identity
- Can Self-Sovereign Identity (SSI) fit within the GDPR? : a Conceptual Data Protection Analysis (Part II)
- Can Self-Sovereign Identity (SSI) fit within the GDPR?: a Conceptual Data Protection Analysis (Part I)
- Why Self-Sovereign Identity is a Game Changer for Government-Resident Interactions
- New Encyclopedia entry Self-Sovereign Identity (SSI)
-
What are the main contributions of the Self-Sovereign Identity?
Identity represents a great asset. But we do not have control of this asset, as it is in the hands of organizations, governments, institutions, etc. These entities know everything about us from all this data.
-
The Future of Self-Sovereign Identity (SSI) Evernym
Drummond Reed and Alex Preukschat, co-authors of Manning Publication's new book 'Self-Sovereign Identity,' for a conversation on the book's development and recent release and what the future holds for SSI as a technology, architecture, and movement.
-
The Evolution of Digital Identity Tomas Hahn
How is it possible that the Internet has spread and developed to such an extent, while the unambiguous digital identification is not yet feasible?
-
What Does Self-Sovereign Identity Mean For My Business? Continuum Loop
- What will happen if I don’t jump on this train?
- What would it mean if I didn’t have to own my customer’s digital identity but establish a deep digital relationship with them instead?
- Do I have the capacity to learn about this? If not, who do you trust to figure it out – both on the business and technical sides.
- What changes when digital identity becomes a revenue driver and asset for your business? (hint: top and bottom line)
- Which of my competitors is probably already doing this?
-
Simple Definitions for Complex Terms in Decentralized Identity
-
What is Self-Sovereign Identity? TangleLabs
-
How Do Verifiable Credentials and Decentralized Identities Work?
Decentralized identity (DID) is a way for users to own their identity, using specific credentials to verify their identity to applications. These credentials, called Verifiable Credentials, enable you to do this. Verifiable Credentials are identity attestations that come from a trusted issuer, like proof of a workplace, student IDs, or official memberships.
-
SSI 101: Online identity and the history of identifiers Hypersign
This series is intended to be a basic, easy-to-understand introduction to SSI, but for a much deeper dive, check out Hypersign Labs — our technical blog. Here’s a good place to start on SSI:
-
Digital Identity: Past; Present; Future Hypersign
As a result of limited and known users there was no layer of identity and authentication in the design of internet framework. With the invention of the World Wide Web (WWW), the users made it a common platform for data sciences. Various sectors of society like health and finance have started using the internet for their services.
-
In-depth introduction to Self Sovereign Identity (SSI) Hypersign
-
What Is Self-Sovereign Identity? Trinsic
Eventually, SSI will give people a super simple way to do the following and more:
- Protect sensitive identity information like SSN and birthdates to reduce the likelihood and impact of identity theft
- Securely prove your identity or things about yourself in a way that institutions can trust
- Maintain privacy and reduce the ability for corporations or nefarious actors to track you without your consent
- Conveniently get access to services you need without usernames and passwords
-
Crossfunctionality Centre
I have developed a pet peeve for "technosolutionism": the notion that a sufficiently innovative technology can solve a social problem, or a business problem, without complex and nuanced changes to social and business practice.
-
What does ‘open’ mean to you? WeAreOpenCoop
Even with a little bit of input and discussion, you can see the shift to words such as ‘inclusivity’ and phrases such as ‘being more accessible’ or ‘getting everyone involved’.
-
The Self-Sovereign Identity (SSI) Basics Santanderigo
The very center of the digital identity is your documents: from your National ID or Passport to your degrees, mobile phone number, bank account number, or your medical records. Anything that is intrinsically bound to you is your data and therefore your identity. While talking about SSI these are called Verifiable Credentials (VC).
-
What is decentralized identity? In CSO
The DID model allows you to establish a relationship between your private key (your blockchain wallet) and your citizenship. The issuing authority signs off on the truth of your claim and, thereafter, third parties can check your public key to see that the holder of the private key is in fact a British citizen.
-
How Self-Sovereign Identity Works with Trinsic's Riley Hughes Georgian
-
What is identity?
-
The different ways Trinsic can be used by developers.
-
Ways to disrupt or democratize the current model of identity.
-
Decentralized identity and its many use cases.
-
The continued need for anonymity in a digital identity world.
-
How identity will evolve with web 3 and the metaverse.
- The Use of Self-Sovereign Identity With Zero-Knowledge Proof (ZKP) Data Driven Investor
- Decentralization of Identity Exstalis
- What is decentralized identity? CSO Online
-
The Journey of Decentralized Identity: Where It’s Been and Where It’s Going Trinsic
Our goal has been to completely abstract away the complexity of the ever-changing landscape so organizations can focus on the important stuff—what product to build, and how to take it to market. Teams shouldn’t have to “pick winners” and wager what to build on. Their products should be interoperable with multiple ecosystems. That’s what Trinsic is providing, out-of-the-box.
-
Self Sovereign Identity- Internet’s Missing Identity Layer 2022-02-02 Identrix
When the Internet was built, it was done so in a way that you would not know who you were connecting to. To get rid of this loophole, the TCP/IP protocol was introduced, which gives us the address of the computer we are connecting to, but nothing about the person, organisation or thing we are communicating with! We can see how that be potentially dangerous for any online user, making your devices highly susceptible not only to hacking but also to identity theft.
-
Can Decentralized Identity Give You Greater Control of Your Online Identity?
- Decentralized identifiers - Self-Sovereign Identity livebook Manning
- Worried About Digital Identity? - Continuum Loop Inc. Christine Martin
- SSI (Self-Sovereign Identity): The Most Important Acronym You've Probably Never Heard Of A glimpse of VR & AR
-
For traditional identity models, the biggest misconception is “strong passwords”
One way to avoid password-related problems is to use decentralized identity management. This method is relatively new, so the best way to gain knowledge about it – contact the experts. For this reason, we are speaking with Mike Vesey, CEO of IdRamp.
-
Introducing the Auth0 Research Program auth0
give direct input towards our product improvements and be the first choice for research recruiting opportunities.
-
Use the Okta CLI to Build Secure Python Apps Okta 2022-07-27
- Teach you how to create your first application
- Learn about authentication and authorization credentials
- Set up hosted authentication with Okta and try it out
- Stoic Sovereign Identity (SSI) Simone Ravaioli
-
Drawbacks of Traditional Identifiers and An Introduction to WEB3 Hypersign
-
Digital Identity: Past; Present; Future Hypersign
-
In-depth introduction to Self Sovereign Identity (SSI) Hypersign
-
GlobaliD 101: ID wallets GlobalID
-
Future with Decentralized Identity SparkPlusTech
-
The changing landscape of digital identity by Tata Consultancy Services
-
Future with Decentralized Identity SparkPlusTech
-
The changing landscape of digital identity by Tata Consultancy Services
-
GlobaliD 101: ID wallets GlobalID
-
Identity Insights - Basics of Verifiable Credentials Indicio, Youtube
What are verifiable credentials? In this episode we are joined by Indicio software engineer Char Howland for an introduction to what this technology is and what it can do.
-
Decentralized identity: What it is, why it matters SC Magazine
-
Levels of information architecture reb00ted
So I propose this outermost framework to help us think about how to interact with shared information environments
-
Self-sovereign identity: an ecosystem of digital identities Ergon
Even though some questions are still unanswered, self-sovereign identities will unlock enormous economic value. If you want to get some initial experience with SSI you can try the available open-source technologies. A successful proof of concept will enable companies to see the possibilities of the new technology and harness this potential more effectively.
-
What is decentralized identity in blockchain? Cointelegraph
-
Are Self-Sovereign Identities on blockchain technology the future? Kook Content 2022-09-01
-
Self-sovereign identity: an ecosystem of digital identities Ergon
-
The Top Five Misconceptions around Self-Sovereign Identity (SSI)
We all have a cybersecurity problem, and SSI represents the most current thinking to address it. For that reason, we believe that SSI is not just another technology.
-
Part 1: What a smart and humanistic approach to digital identity would like
-
Part 2: The Trust Triangle — the system of issuers, holders, and verifiers that illustrates how identity works (and how it’s broken, today)
-
Part 3: Why the ID Wallet is the first step toward achieving a new vision for digital identity
-
Part 4: Why every company is an identity company
-
[...]
There is a real opportunity to combine technology that is being developed with the concept of BYO Identity that will create a new identity framework where you own and control your data.
-
Centralized\Federated vs Self Sovereign dominiumssi
-
Self-sovereign identity: an ecosystem of digital identities Ergon
-
Trust Registries in the Real World Continuum Loop
Trust Registries allow us to know that the various shared credentials (e.g. proof of insurance) are accurate. A Homeowner can ask their Digital Wallet to verify an insurance Credential that the Contractor is honest.
-
Many articles are being written about SSI, not all so excellent John Philip
Most are probably not "written" in the normally understood sense of the word (auto-scraping and ctrl-c and ctrl-v isn't writing). Many are probably not written by a person at all.
-
Centralized\Federated vs Self Sovereign dominiumssi
There is a real opportunity to combine technology that is being developed with the concept of BYO Identity that will create a new identity framework where you own and control your data.
-
Part 1: What a smart and humanistic approach to digital identity would like
-
Part 2: The Trust Triangle — the system of issuers, holders, and verifiers that illustrates how identity works (and how it’s broken, today)
-
Part 3: Why the ID Wallet is the first step toward achieving a new vision for digital identity
-
Part 4: Why every company is an identity company
-
TOWARDS A USER-CENTRIC DIGITAL IDENTITY SYSTEM Irish Tech News
-
Debunking Common Misconceptions About Passwordless Authentication auth0
-
From DID to DeFi and EVM Metadium
-
A Beginners Guide to Decentralized Identifiers (DIDs) Veramo
-
10 Resources for beginners in Decentralized Identity (DID) Veramo
-
Self-Sovereign Identity: Taking Control Over Your Digital Identity Forbes 2022-09-26
The two main ingredients of SSI are verifiable credentials (VCs) and decentralized identifiers (DIDs).
-
According to W3: "Verifiable credentials represent statements made by an issuer in a tamper-evident and privacy-respecting manner."
-
Self-Sovereign Identity, Zero-Knowledge Proofs & the Future of Data Blockchain Australia
No other additional information is needed to complete this data exchange. So how do you know that the information being provided is authentic? The identity ‘proof’ uses a cryptographic hash function that confirms beyond any doubt that the identity claim is accurate.
-
The Importance of Self-Sovereign Identity Blockchain Solutions Zaisan
The public keys, as the name implies are there to view anytime and are used for exchanging information and can be revoked, however, the private key is for the account holder himself, be that an issuer, a verifier, or a subject. It is only through a private key that one can pass on his credentials using his DID to an issuer who then validates the credentials and sends them to the verifier using his DID.
-
WHAT’S DECENTRALIZED IDENTITY? NFTNewsToday 2022-10-06
issuers or verifiers can only access the information shared by the DID holder. This information exchange can occur through various technologies, like NFC, QR, or Bluetooth. Zero-knowledge proofs are applied to restrict full information access. 2022-09-15
-
GlobaliD 101: Device-based identity
That way, your sensitive personal data is stored locally on your own device rather than hosted on some company’s server that becomes a target for hackers.
-
tldr
:: DID is just an URI
:: VC is a cryptographically verifiable credential using DID\ :: SSI is a self-sovereign and privacy-preserving identity :: Non-human (Machines, Bots, Goods, anything) also able to have DID, VC, and SSIs -
Decentralized Systems of Identity and Owning Your Own Data Coindesk
On this episode of “Money Reimagined,” hosts Michael Casey and Sheila Warren are together again but this time, at Converge22 by Circle. They discuss the challenges of identity and verification in the U.S. and in other countries with Daniel Buchner, head of decentralized identity at Block; and Chi Nnadi, the co-founder and CEO at Mara.
-
Introduction to Decentralized Identity IOTA Wiki