***H***ello people, got a good Saturday? Ready to open tons of bottles tomorrow? ***I***'m not...this year specially, i'm not ready. I will **return** on the street without any doubt, but this ~~the~~ another story.
So in our hands there's the **nightmare** of the **security cannibals**, the *fish* more difficult to take. There's OpenBSD. He (yes, it's a person, it's ***my best friend***) is a pure BSD 4.4 based Unix that never fail to his customer, respecting rules that, i'm my opinion, are fundamental blocks of great secures peaces of software:
Yes, the point three will open yours eyes i know, you will be accuse my to be insane....Well for sure... ***i'm totally insane*** but OpenBSD it's very clear and simple to manage. The secret it's to follow simple rules very easy to understand for the new and semi-new customer. OpenBSD don't use strange, absurd and long explication or vocabulary to explain the things. He will do it in simple way.
Remember, where you will find tons of code, many times there some *fantastic genius* that have done it to take you away from **the source code**. Adding complexity and time to understand basics procedure it's absolutely not a sign of great knowledge, it's a medieval procedure to maintain people away from the real purpose, that in this case will be obtain the keys to an extreme powerful, secure and clear Unix: OpenBSD.
I love Linux, but nowadays something, someone, or whatever the name you will use are totally destroy it. Millions of lines of code and complexity that have grow up a lot at low level code. For low class customer can use it with nice visual effects..
It's not difficult to understand, think about the new **systemd**, adopted for A LOT of great Linux distribution. Here are some links that will help you thing and OPEN your mind.
***T***or in computer science, that is what i'm speaking about with some Baroque embellishments, is the state of the art to theoretically preserve **privacy** of a Internet user. Remember very well, it was not designed to act like a **security** machine but like a **privacy** ensure. Is an open source software that enable anonymous communication in Internet. It can be stacked with other technologies, like vpn or i2p, to try conceal our real ip address and geo point of source.
***Th***or mythologically speaking, was son of Odin, dedicated to the protection of mankind and of the fortress of Asgard.
But..¿Was or is T**[h]**or really dedicated to the protection of the truth or does it complain also with other more obscures functions? A great question with a very difficult reply without a lot of sentiment and passion. I'm trying to do it better that i can but i really appreciate T**[h]**or. Really.
In real world, ou Jesus..real...in the binary system, Tor also open to the user, the man who navigate the Internet ocean, the access to the subterranean Internet, the (in)famous [#deepweb](https://steemit.com/trending/deepweb), or Deep Internet. And like all the things that we know, deep can be deeper and deeper and deeper and so on. Many people think that [#deepinternet](https://steemit.com/trending/deepinternet) is many times bigger than the Internet, is this true? Nobody, that i know ... ¿you know? know the answer. Like the deepest ocean in nature, i cannot explain to you what is the deepest Internet and who is the owner of that obscure site.
So it's normal that sometimes i was thinking about T[h]or more like Χάρων
Here you are some URI to try to do some light more on that themes:
But let's start together configuring those two fantastic open source project, and remember that Tor is not simple and easy like OpenBSD is.
Simply search and install tor and a good manager in nvcurse and gtk to admin it, we find in the classic port tree of OpenBSD:
```
$pkg_info -Q tor arm
$pkg_add -U tor arm
```
Arm is the the next Nyx.
We will use it like a foreground program, without launch it from rc. In this first and simple configuration it will act like a SOCKS proxy, configure only some kind of nation like good jump in our tor path to the Internet and little more.
We will use Arm with the same preinstaller `_tor` user that use OpenBSD package. So:
```
$doas chown -R _tor ~/.arm
$ doas cat > ~/.arm/.torrc <<EOF
DataDirectory /home/taglio/.arm/tor_data # location to store runtime data
Log notice file /home/taglio/.arm/tor_log # location to log notices, warnings, and errors
ControlPort 9051 # port controllers can connect to
CookieAuthentication 1 # method for controller authentication
ExitNodes {RO},{CH}
ExcludeNodes {AU},{CA},{US},{NZ},{UK}
EntryNodes {BE},{DE},{IT},{NL}
StrictNodes 1
SocksPort 9900
EOF
```
We're now interested in initialize arm configure and explain what the hell are those `{}`
https://en.wikipedia.org/wiki/UKUSA_Agreement
https://www.privacytools.io/#ukusa
Only the acronym is obscure yet. `UKUSA`
Read with your eyes what the hell is this democratic right abuse and masochism. Here up in those links.
So in `torrc` we can indicate to our Tor how to don't pass through one nation that remiss to *"The Fourteen Eyes"*.
I use to enter in this example Belgium or German or Italy or Holland, and after an unknown jump i will leave the Tor network passing or for Romania or for Swiss.
No only the correct launch for the same Tor and we can go to sleep :P
```
$doas -u _tor tor -f toorrc
$doas -u _tor arm
```
Explore the deepest that you can, but remember the more deep you arrive more pressure and less oxygen you will find.
# OpenBSD, Tor transparent local proxy.
## Background
------
**J**ust in the case that you've missed our last article we're speaking about *OpenBSD*, the most secure open source system operative in the world, and *Tor*, a free software for enabling anonymous communication.
In our [first post](https://steemit.com/openbsd/@npna/openbsd-tor-and-the-the-fourteen-eyes) we have done an introduction and a first configuration creating a tor service with only one local socks port opened for a static user configuration.
We've also introduced the concept of [FVEY](https://en.wikipedia.org/wiki/Five_Eyes) that we will continue to analyze as soon as possible.
What we don't touch last time is the important fact that this two fabulous softwares have got a strange difficult history of interoperability between them. OpenBSD is in ours life from middle of the nineteen and Tor, the onion router project, from September 2002.
But only with the birth of the [torbsd proyect](https://torbsd.github.io/) the configuration of the anonymizing daemon is something simple and easy as it have to be. We can study read and fork the work of the torbsd fellows at [github](https://github.com/torbsd/).
17.**GeoIPExcludeUnknown**: if it don't know where is the tor relay simply don't use it.
18.**SocksPort**: static port socks 4/5 listener (*will deepen later*).
19.**PathsNeededToBuildCircuits**: tor won’t build circuits until it has enough descriptors or microdescriptors to construct that fraction of possible paths.
Now we've to be sure that `dhclient`will not rewrite `/etc/resolv.conf`. In OpenBSD we've to add this to `/etc/dhcpclient.conf`:
OpenBSD was the first system operative to use one of the most powerful firewall, **pf**.
In others POST we will better analyze how to properly use this monster, but for now simply use this `pf.conf` to create a transparent firewall in an OpenBSD system newer than the 4.7 version.
We create another loopback interface in our system to play a little with internal routing:
match in all scrub (no-df random-id reassemble tcp)
antispoof for egress inet
block return log on egress all
pass in quick on lo1 inet proto tcp all flags S/SA modulate state rdr-to 127.0.0.1 port $trans_port
pass in quick on lo1 inet proto udp to port domain rdr-to 127.0.0.1 port domain
pass quick on { lo0 lo1 }
pass out quick inet proto tcp user _tor flags S/SA modulate state
pass out quick inet proto udp to port domain route-to lo1
pass out quick inet to $non_tor
pass out inet proto tcp all route-to lo1
EOF
```
Here you are some examples on how to use the pf firewall:
- pfctl -e (enable)
- pfctl -d (disable)
- pfctl -f /etc/pf.conf (load rules)
- pfctl -nf /etc/pf.conf (parse file, don't load)
- pfctl -sr (show current ruleset)
- pfctl -ss (show current state table)
- pfctl -si (show filter stats and counters)
- pftcl -sa (show all)
- pfctl -t table -T flush (flush table)
- pfctl -k 192.168.1.80 (kill connections for host 80)
- pfctl -t
-T expire 86400 -flush table (entries added in last 24 hours)
- add -vv to any for more info
## Start tor at boot
------
Last configuration is to activate tor at start.
*¿Will you use this daemon to protect your privacy or to access to the [#deepinternet](https://steemit.com/trending/deepinternet)?*
```
$ doas rcctl enable tor
$ doas reboot
```
**stay tuned for more OpenBSD, tor and deep Internet posts**, i love you.
# OpenBSD, Tor, 14 applications example. PART 1
## Fourteen application, the first three are browsers
------
First of all sorry for the delay, but i was busy with real life and i cannot go on with our series.
Let's start to analyze every step necessary to configure use of the TCP/IP socks sockets that we opened in our [last article](https://steemit.com/openbsd/@npna/openbsd-tor-and-the-streams-isolation).
## Firefox
------
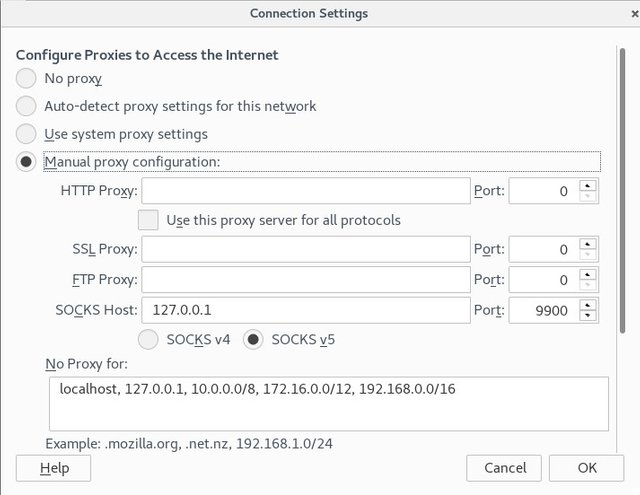
Like we can see in the image:
1. open `about:preferences#advanced`
2. click on `network` tab
3. click on `Settings`
4. check `Manual proxy configuration`
5. write on `SOCKS Host`the local ip `127.0.0.1` and `Port``9900`
6. write on `No proxy for``localhost, 127.0.0.1, 10.0.0.0/8, 172.16.0.0/12, 192.168.0.0/16` that are privates network as [RFC1918](https://tools.ietf.org/html/rfc1918).
## Chromium
------
As default chromium has no simple option to set a proxy server different from the system wide proxy. But we've done a little *hack*.
```
$ which chrome
/usr/local/bin/chrome
$ file /usr/local/bin/chrome
/usr/local/bin/chrome: Bourne shell script text executable
```
So here we can appreciate that chrome in our **OpenBSD workstation** is not an executable but is a shell script, here is a cat:
How you can see int last line of the script there is the real `exec`of the binary that in OpenBSD is located in `/usr/local/chrome/chrome` .
Simply *concat* in the same line of the var LANG the string `"--proxy-server="socks5://127.0.0.1:9901"`and close the sentence with a `"`that we've previously remove from the old sentence (the last one that you will find doing a `cat`). You can appreciate that for `chrome`we use socksv5 port `9901`.
## Tor browser
------
Tor browser is an open source fork of Firefox. It's maintained by the torproject folks. You can find the binaries [here](https://github.com/TheTorProject/gettorbrowser.git) in github. But remember that we're using OpenBSD and the Tor browser bundle is available in the ports tree. To download the binary for OpenBSD do:
```
$ doas pkg_add -U tor-browser
```
But `tor-browser`have got a `tor daemon` included that control via the `tor button` that we can launch via the onion icon on the left of the navigation bar. The first time that we execute this browser simply accept the default settings waiting to `connect`on the window that appear. But next:
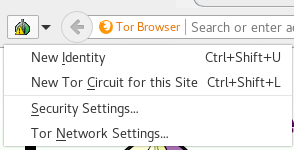
This is the first sub window if we click on the `onion button`. Let's assume that we will use `tor browser`with the most deep navigation in the web. So click on `security settings` and:
1. Check `This computer need to use a local proxy to access the Internet`
2. Select for `Proxy Type`the option `SOCKS 5`
3. Write in `Address``127.0.0.1` and in `Port``9902`
Now...there's some post on the web that does not recommend concatenate **Tor over Tor**, like [this](https://trac.torproject.org/projects/tor/wiki/doc/TorifyHOWTO#ToroverTor); but there is no exact explication so i really don't think so.
Remember that we have banned **ALL** the fourteens eyes country in our [last](https://steemit.com/openbsd/@npna/openbsd-tor-and-the-streams-isolation) configuration. I quoted the explication from [privacytools.io](https://www.privacytools.io/) :
> The UKUSA Agreement is an agreement between the United Kingdom, United
> States, Australia, Canada, and New Zealand to cooperatively collect,
> analyze, and share intelligence. Members of this group, known as the
> Five Eyes, focus on gathering and analyzing intelligence from
> different parts of the world. While Five Eyes countries have agreed to
> not spy on each other as adversaries, leaks by Snowden have revealed
> that some Five Eyes members monitor each other’s citizens and share
> intelligence to avoid breaking domestic laws that prohibit them from
> spying on their own citizens. The Five Eyes alliance also cooperates
> with groups of third party countries to share intelligence (forming
> the Nine Eyes and Fourteen Eyes), however Five Eyes and third party
> countries can and do spy on each other.
In the configuration of the `tor daemon`that came with `tor browser`we force tor to use the countries of the **nine eyes group** that will be the first three hops of ours jumps in the tor network. Doing so we will use **six** hops to navigate the Internet.
This are the files shipped with `tor launcher` (a sub packet of `tor browser`):
You find all the country codes **ISO 3166** in this [sheet](https://drive.google.com/open?id=1NBjLS5Mbf0jDYCdkJ_UHJXFeiPDyaUnaNecr9GkuP7w)
# Openbsd, Tor, Privoxy and the browsers.
## Privoxy, add a new friend to the battle.
So, we've got now three browsers using three differents socks port to access the Tor network, and the last of ours browsers building a special doble circuit in the tor network combining different countries (*this is not bad at all*). Remember, we were [here](https://steemit.com/openbsd/@npna/openbsd-tor-14-applications-example-part-1) .
But...the situation is so difficult...we've to protect us with more layers.
Let's introduce the layer 7 firewall **Privoxy**.
What is a layer 7 firewall? It's a firewall that work at the last layer of the ISO/OSI network stack, that in *no technical* user speaking is the URI, www.facebook.com, steemit.com/@npna ...
We've only a little problem respect to Tor with privoxy. To concatenate three privoxy ports to three Tor ports we've to launch three different privoxy instances. But with OpenBSD and to his clearness this is very simple.
Let's go **deep** in the configuration:
- cd to the privoxy configuration directory:
-`$ cd /etc/privoxy`
- copy default config file into three different:
-`$ doas cp config firefox && doas cp config chrome && doas cp config torbrowser`
- go to the OpenBSD rc.d directory:
-`$ cd /etc/rc.d`
- copy the default privoxy init script in three different:
-`$ doas cp privoxy privoxyfirefox && doas cp privoxy privoxychrome && doas cp privoxy privoxytorbrowser`
Ok all it's simple and without complications. Good, *i love OpenBSD*.
The privoxy main configuration file is full of options and you have to dedicate a couple of ours to understand all the voices, or to simply read it. For now we use this basic configuration (in ours next chapters probably we will do some changes to it). Let's see together the one that will be used in the firefox environment:
#client-specific-tag circumvent-blocks Overrule blocks but do not affect other actions
# disable-content-filters Disable content-filters but do not affect other actions
#
#
# client-tag-lifetime 180
# # IP address with a X-Forwarded-For header.
# trust-x-forwarded-for 1
```
Ok simply change `admin-address`and `hostname` with the yours.
Privoxy send in every configuration file the `http proxy port` to a distinct `socks port`.
To create the others two execute this command:
```
# sed s/privoxyfirefox/privoxychrome/g privoxyfirefox | sed s/9900/9901/g > privoxychrome
# sed s/privoxychrome/privoxytorbrowser/g privoxychrome | sed s/9901/9902/g > privoxytorbrowser
```
Now create the missing logs files with:
```
$ doas touch /var/log/privoxy/privoxyfirefox.log
$ doas touch /var/log/privoxy/privoxychrome.log
$ doas touch /var/log/privoxy/privoxytorbrowser.log
```
And enable all the three at boot:
```
$ doas rcctl enable privoxyfirefox
$ doas rcctl set privoxyfirefox user _privoxy
$ doas rcctl set privoxyfirefox flags /etc/privoxy/firefox
$ doas rcctl enable privoxychrome
$ doas rcctl set privoxychrome user _privoxy
$ doas rcctl set privoxychrome flags /etc/privoxy/chrome
$ doas rcctl enable privoxytorbrowser
$ doas rcctl set privoxytorbrowser user _privoxy
$ doas rcctl set privoxytorbrowser flags /etc/privoxy/torbrowser
```
At last start the three daemons:
```
$ doas rcctl start privoxyfirefox
$ doas rcctl start privoxychrome
$ doas rcctl start privoxytorbrowser
```
## Browsers configurations

Now we've got the correct setup of privoxy, but remember without any rule of layer 7 firewalling, that we will see in our next chapter.
We've to change the configuration of the three browsers to use privoxy and not directly the tor socks.
Ok, the cooking is started, but one last little `hack`to disturb our favorites *cannibals*. Let's eliminate the `HTTP header`**[Refer](https://en.wikipedia.org/wiki/HTTP_referer)**: