Added pictures to the repository
BIN
attachment/wiki/split-ssh/adding-keys.png
Normal file
|
After Width: | Height: | Size: 44 KiB |
BIN
attachment/wiki/split-ssh/adding-new-entry.png
Normal file
|
After Width: | Height: | Size: 31 KiB |
BIN
attachment/wiki/split-ssh/check-integration-status.png
Normal file
|
After Width: | Height: | Size: 41 KiB |
BIN
attachment/wiki/split-ssh/client-creation.png
Normal file
|
After Width: | Height: | Size: 21 KiB |
BIN
attachment/wiki/split-ssh/create-database.png
Normal file
|
After Width: | Height: | Size: 34 KiB |
4
attachment/wiki/split-ssh/diagram.svg
Normal file
|
After Width: | Height: | Size: 240 KiB |
BIN
attachment/wiki/split-ssh/enable-ssh-agent-integration.png
Normal file
|
After Width: | Height: | Size: 40 KiB |
BIN
attachment/wiki/split-ssh/encryption-settings.png
Normal file
|
After Width: | Height: | Size: 40 KiB |
BIN
attachment/wiki/split-ssh/enter-passphrase.png
Normal file
|
After Width: | Height: | Size: 41 KiB |
BIN
attachment/wiki/split-ssh/naming-screen.png
Normal file
|
After Width: | Height: | Size: 52 KiB |
BIN
attachment/wiki/split-ssh/operation-execution.png
Normal file
|
After Width: | Height: | Size: 17 KiB |
BIN
attachment/wiki/split-ssh/password-screen.png
Normal file
|
After Width: | Height: | Size: 53 KiB |
BIN
attachment/wiki/split-ssh/select-private-key.png
Normal file
|
After Width: | Height: | Size: 71 KiB |
BIN
attachment/wiki/split-ssh/vault-adding-keepass.png
Normal file
|
After Width: | Height: | Size: 23 KiB |
BIN
attachment/wiki/split-ssh/vault-creation.png
Normal file
|
After Width: | Height: | Size: 20 KiB |
|
|
@ -6,7 +6,7 @@ This is done by using Qubes's [qrexec][qrexec] framework to connect a local SSH
|
|||
This way the compromise of the domain you use to connect to your remote server does not allow the attacker to automatically also steal all your keys.
|
||||
(We should make a rather obvious comment here that the so-often-used passphrases on private keys are pretty meaningless because the attacker can easily set up a simple backdoor which would wait until the user enters the passphrase and steal the key then.)
|
||||
|
||||

|
||||

|
||||
|
||||
## Security Benefits
|
||||
|
||||
|
|
@ -33,11 +33,11 @@ Skip the first step if you don't wish to create another vault.
|
|||
|
||||
1. Create a new vault AppVM (`vault`) based on your chosen template. Set networking to `(none)`.
|
||||
|
||||
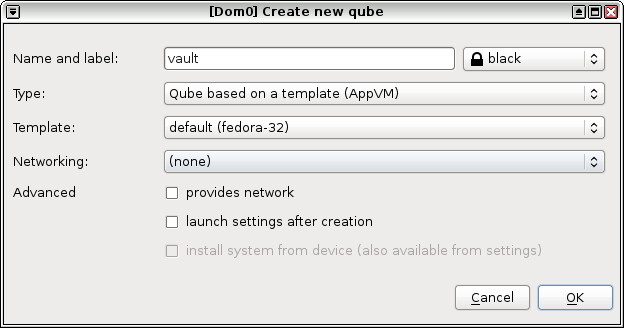
|
||||

|
||||
|
||||
2. Create a SSH Client AppVM (`ssh-client`). This VM will be used to make SSH connections to your remote machine.
|
||||
|
||||
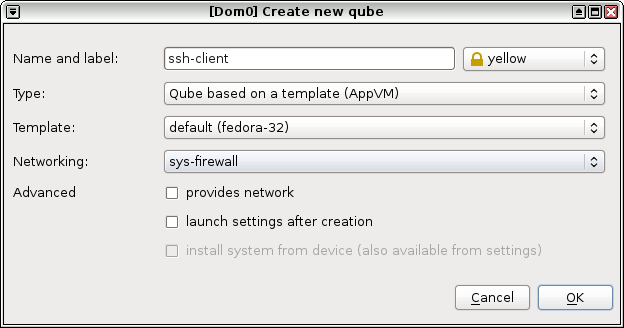
|
||||

|
||||
|
||||
## Setting up SSH
|
||||
|
||||
|
|
@ -278,55 +278,55 @@ KeePassXC should be installed by default in both Fedora and Debian TemplateVMs.
|
|||
|
||||
1. Add KeepasXC to the Applications menu of the newly created AppVM for ease of access and launch it.
|
||||
|
||||
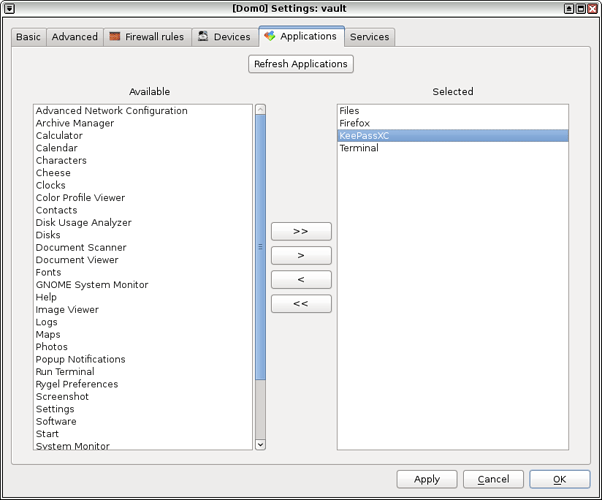
|
||||

|
||||
|
||||
**Note:** Since the vault VM has no internet connection, you can safely deny automatic updates if prompted.
|
||||
|
||||
2. Create a new database.
|
||||
|
||||
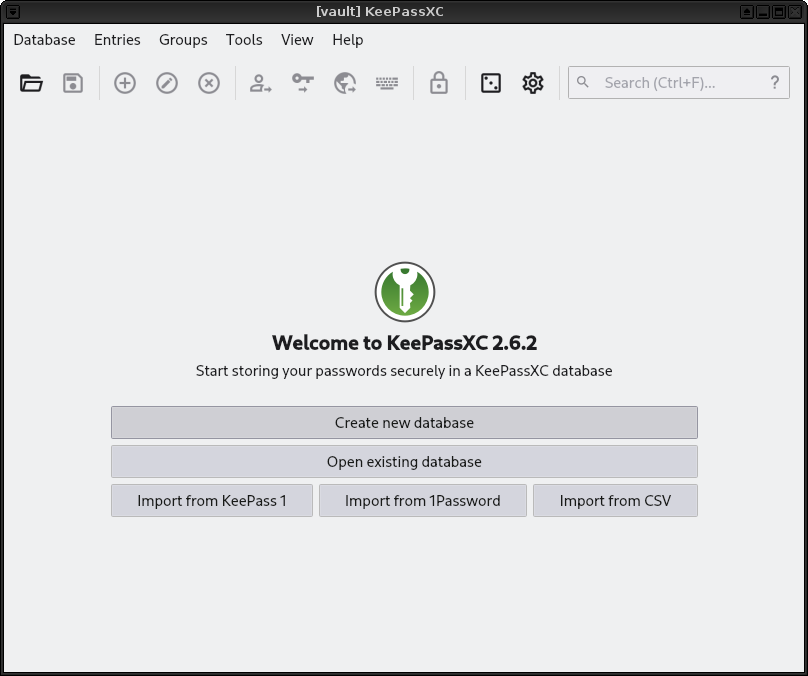
|
||||

|
||||
|
||||
3. Enter a name for your database and continue.
|
||||
|
||||
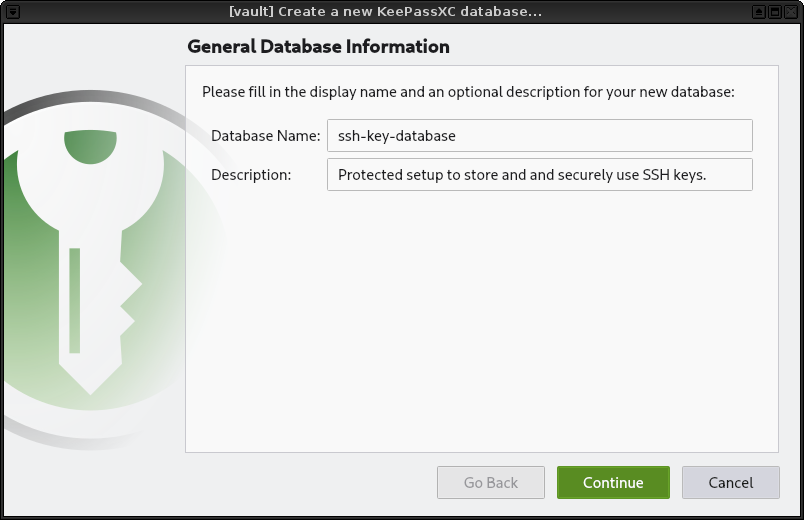
|
||||

|
||||
|
||||
4. Adjust the encryption settings.
|
||||
Check the [KeePassXC User Guide][KeePassXC User Guide] for more information about these settings.
|
||||
|
||||
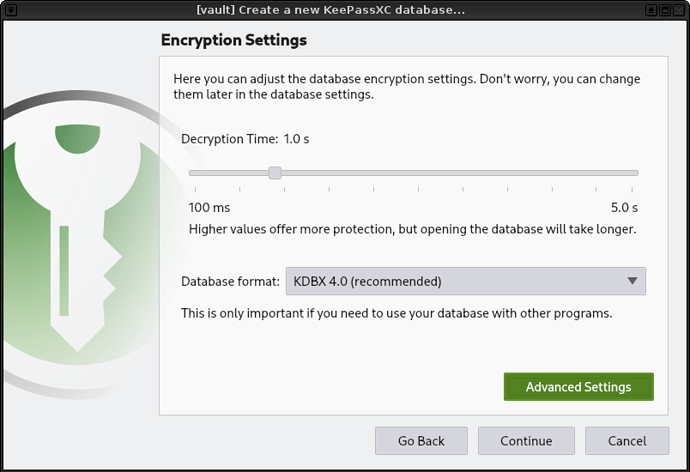
|
||||

|
||||
|
||||
5. Enter a password for your database. Take your time make a secure but also rememberable password. ([hint][Hint])
|
||||
|
||||
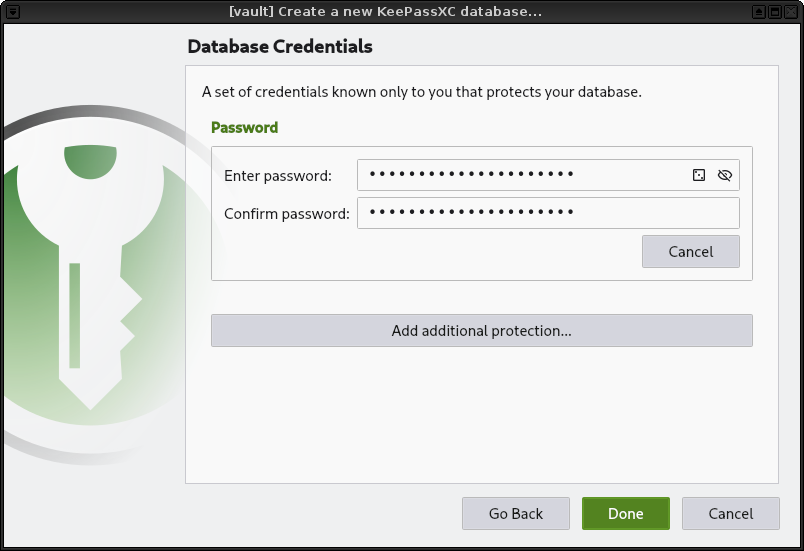
|
||||

|
||||
|
||||
6. Add a new entry.
|
||||
|
||||
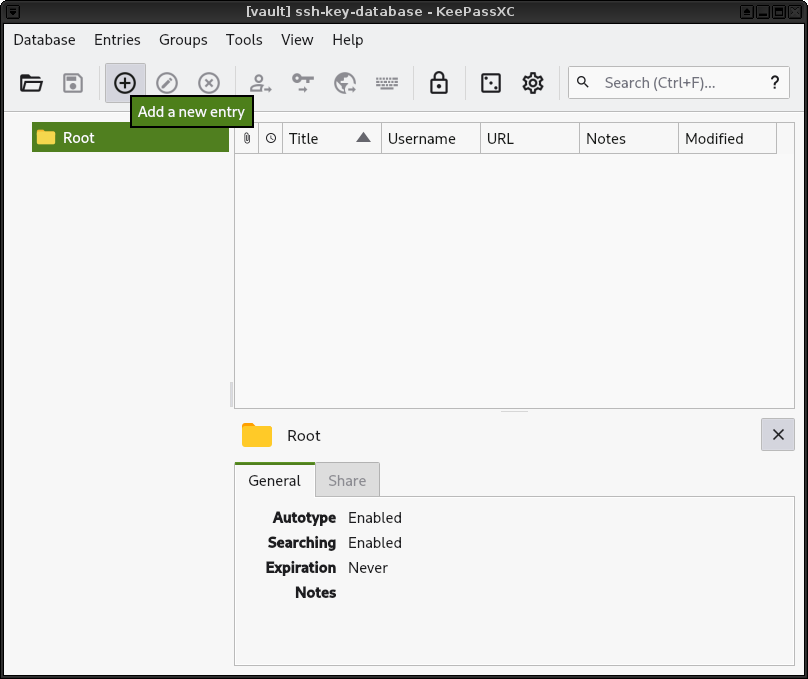
|
||||

|
||||
|
||||
7. Set password to your SSH key passphrase.
|
||||
|
||||
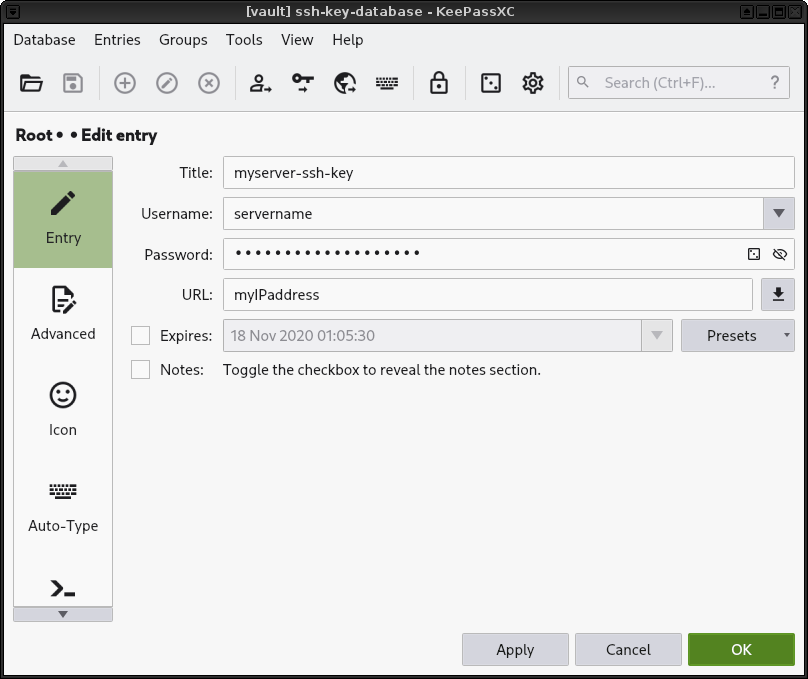
|
||||

|
||||
|
||||
8. Go into the Advanced section and add your keys.
|
||||
|
||||
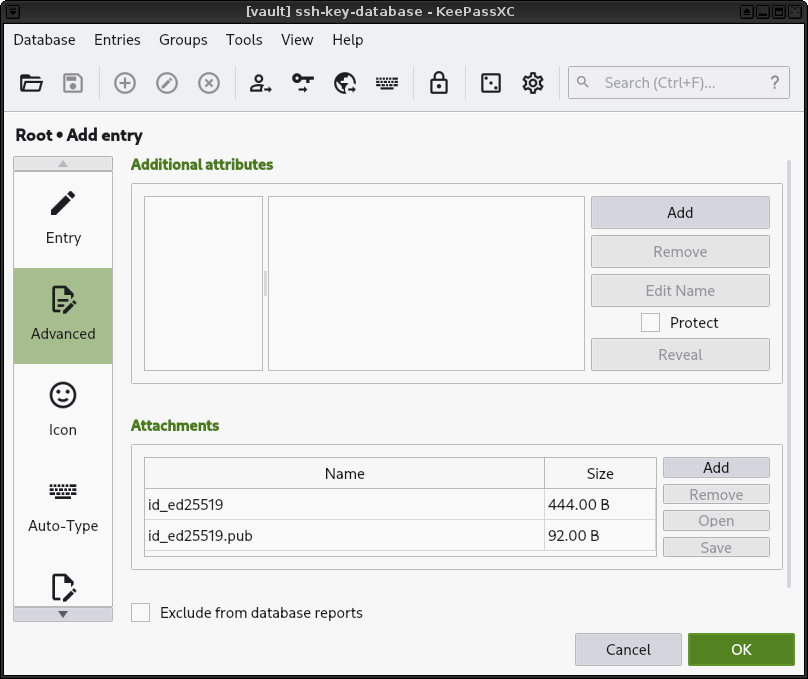
|
||||

|
||||
|
||||
**Note:** Technically, you only need to add the private key (`id_25519`) for the following steps to work. If you add the public key here, too, you can later on backup your kdbx file and have everything in one place. You can even delete your keys (`id_25519` and `id_25519.pub`) from your file system if you like.
|
||||
|
||||
9. Enable "SSH Agent Integration" within the Application Settings.
|
||||
|
||||
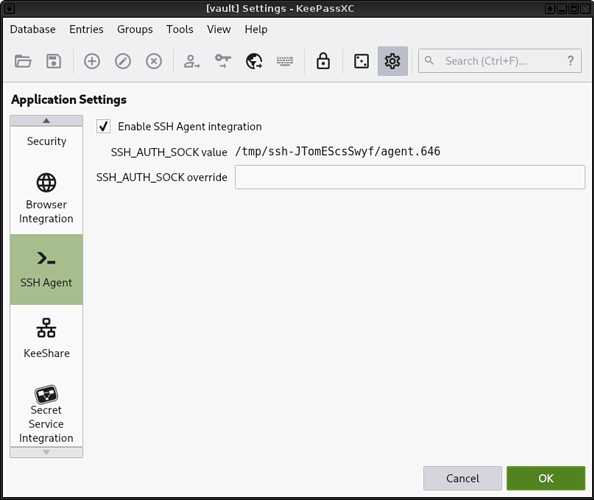
|
||||

|
||||
|
||||
10. Restart KeePassXC
|
||||
|
||||
11. Check the SSH Agent Integration status.
|
||||
|
||||
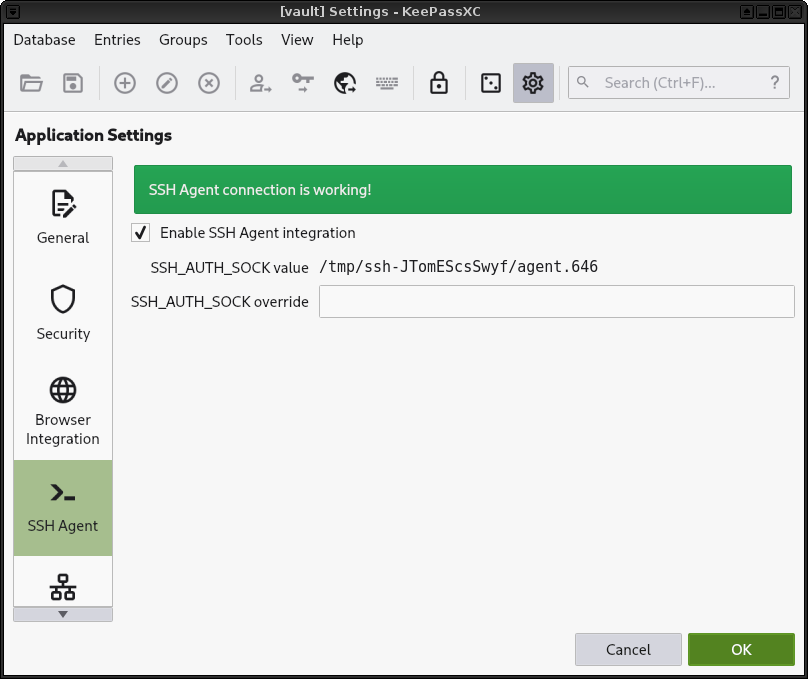
|
||||

|
||||
|
||||
12. Open the entry you created and select your private key in the "SSH Agent" section.
|
||||
Don't forget to also check the first two options.
|
||||
|
||||
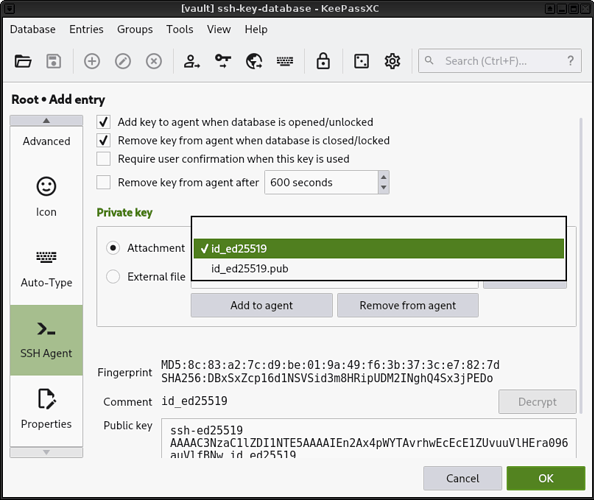
|
||||

|
||||
|
||||
#### Testing the KeePassXC Setup
|
||||
|
||||
|
|
@ -358,7 +358,7 @@ If it is, restart your vault VM and do not enter your password when it asks you
|
|||
|
||||
3. Allow operation execution. (If you don't see the below prompt, check your VM interconnection setup.)
|
||||
|
||||
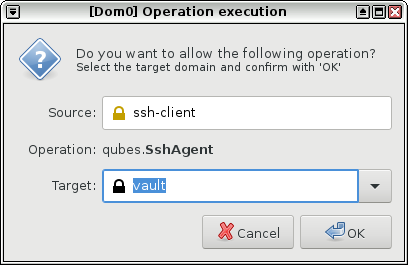
|
||||

|
||||
|
||||
It should return `The agent has no identities.`.
|
||||
|
||||
|
|
@ -391,7 +391,7 @@ Using split ssh in QubesOS 4.0 (Kushal Das) https://kushaldas.in/posts/using-spl
|
|||
Using Split-SSH in Qubes 4 (Denis Zanin) https://deniszanin.com/using-split-ssh-gpg-in-qubes-os/ <br/>
|
||||
R.I.S.K.S. https://19hundreds.github.io/risks-workflow/ssh-split-setup <br/>
|
||||
|
||||
Contributor(s): @shaaati, @invalid-error, @deeplow, @santorihelix
|
||||
Contributor(s): @shaaati, @invalid-error, @deeplow, @ephemer4l
|
||||
|
||||
[CreateBackup]:https://www.qubes-os.org/doc/backup-restore/#creating-a-backup
|
||||
[qrexec]: https://www.qubes-os.org/doc/qrexec/
|
||||
|
|
|
|||