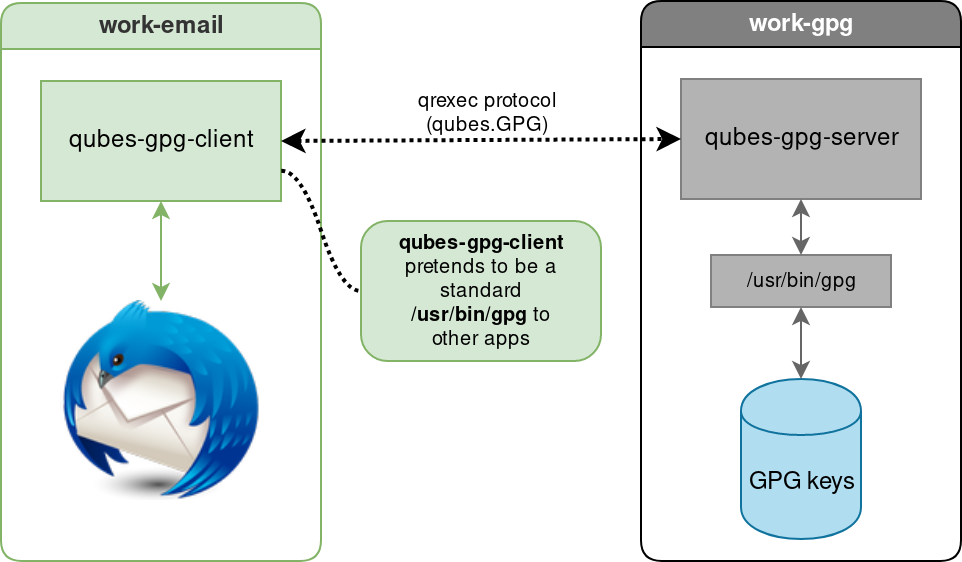
Split GPG is a software alternative to keeping your main keypair on a separate device. Instead of using a physical USB drive, Split GPG utilizes non-networked qubes to store the keys. For more in-depth explanation, [refer to the official docs](https://www.qubes-os.org/doc/split-gpg/).
### Simple diagram of Split GPG
Subkeys are essentially children keys of the main keypair. The advantage is they can be revoked independently without needing to revoke your main. The drawback is you can have many subkeys for signing, but only 1 for encrypting. [See the Debian wiki on subkeys, especially the Caveats section](https://wiki.debian.org/Subkeys)
## How to setup Split GPG with subkeys
### Prerequisites
1. Follow the official Split GPG documentation on setting up Split GPG first: https://www.qubes-os.org/doc/split-gpg/#configuring-split-gpg
#### One possible key distribution
| Key type | VM location | Note |
|:----------|:-------------|:------------------ |
| sec | vault | Main secret key. Should be tarballed and stored, not actively on the keychain |
| pub | vault | Main public key. Can be used or not. However, if you sign with a subkey (ssb) it cannot be verifid with the main public key. If you don't use it, may as well keep it in the vault. |
| ssb | gpg | Secret subkey. Only accessed with Split GPG commands where needed. `gpg` VM is not connected to the internet. |
| sub | personal | Public subkey. Can be freely distributed |
<sup>[Setup without subkeys](https://www.qubes-os.org/doc/split-gpg/#setup-description)</sup>
The main key is still in the keyring. Export its subkeys in a temp file, delete the main key from the keyring, then import the subkeys. Be sure to delete `subkeys` after importing.