mirror of
https://github.com/Decentralized-ID/decentralized-id.github.io.git
synced 2025-02-14 06:11:45 -05:00
better organization \ names
This commit is contained in:
parent
daaeb78e38
commit
e06e3f9779
@ -1,5 +1,5 @@
|
||||
---
|
||||
title: IIW Session Topics (Unofficial)
|
||||
title: Session Topics from the Internet Identity Workshop since 2005
|
||||
layout: single
|
||||
description: Session topics from the Internet Identity Workshop over the past 15 years
|
||||
excerpt: "If you want to stay current in digital identity, keeping an eye on the session topics of the biannual internet identity workshop is a good place to start."
|
||||
|
||||
@ -15,7 +15,7 @@ redirect_from:
|
||||
header:
|
||||
image: /images/blockchange-identity-header.webp
|
||||
caption: "[On the Emergent Use of Distributed Ledger Technologies for Identity Management](https://blockchan.ge/blockchange-fieldreport.pdf)"
|
||||
categories: ["Regional"]
|
||||
categories: ["Government"]
|
||||
tags: ["Government","Global","Tokyo","China","Korea","Latin America","Japan","Africa"]
|
||||
last_modified_at: 2023-06-06
|
||||
toc: true
|
||||
|
||||
@ -6,7 +6,7 @@ excerpt: >
|
||||
There is a lot more work to be done and plenty of consultations to undertake, but we understand that as we increasingly rely on digital technology as part of our everyday lives, the government has a responsibility to ensure we can offer a digital ID system that is voluntary, efficient and meets people’s needs and most importantly offers the highest security for their personal information
|
||||
permalink : /government/australia/
|
||||
canonical_url: https://decentralized-id.com/government/australia/
|
||||
categories: ["Regional"]
|
||||
categories: ["Government"]
|
||||
tags: ["Australia","Australian Payments Network"]
|
||||
last_modified_at: 2023-06-07
|
||||
---
|
||||
|
||||
@ -6,7 +6,7 @@ excerpt: >
|
||||
Another functional question that needs to be resolved concerns how we communicate the value of data stewardship as an ideal, and relatedly the value of data itself. Given the unequal relationships between technology companies and people, the fact that data is a valuable resource that can be used for negotiation is still not necessarily understood.
|
||||
permalink : /government/india/
|
||||
canonical_url: https://decentralized-id.com/government/india/
|
||||
categories: ["Regional"]
|
||||
categories: ["Government"]
|
||||
tags: ["India","Aadhaar","Hyperledger","Orgbook"]
|
||||
toc: false
|
||||
last_modified_at: 2023-06-07
|
||||
|
||||
@ -6,7 +6,7 @@ excerpt: >
|
||||
Our government is embarking on a journey to create A Digital Strategy for Aotearoa that seeks to respond to the social, economic, education and cultural opportunities from digital technology, along with the risks that these technologies can bring.
|
||||
permalink : /government/new-zealand/
|
||||
canonical_url: https://decentralized-id.com/government/new-zealand/
|
||||
categories: ["Regional"]
|
||||
categories: ["Government"]
|
||||
tags: ["New Zealand","Aotearoa","DINZ","DISTF"]
|
||||
last_modified_at: 2023-06-07
|
||||
---
|
||||
|
||||
@ -6,7 +6,7 @@ excerpt: >
|
||||
permalink: /government/canada/pctf/
|
||||
canonical_url: https://decentralized-id.com/government/canada/pctf/
|
||||
tags: ["Trust Framework","Canada","Verifiable Credentials","DIACC","PCTF"]
|
||||
categories: ["Regional"]
|
||||
categories: ["Government"]
|
||||
header:
|
||||
image: /images/pan-canadian-trust-header.webp
|
||||
caption: "[PCTF Placemat](https://canada-ca.github.io/PCTF-CCP/docs/PCTF-Placemat.pdf)"
|
||||
|
||||
@ -6,7 +6,7 @@ excerpt: >
|
||||
"Digital technologies are transforming the way British Columbians live, work and play. To meet their changing expectations, government’s transformation is also underway. It’s about using modern tools and technologies to deliver the services people want and maximizing the power of data to improve the services people need."
|
||||
permalink: /government/canada/bcgov/
|
||||
redirect_from: /public-sector/canada/
|
||||
categories: ["Regional"]
|
||||
categories: ["Government"]
|
||||
tags: ["Trust Framework","Canada","Verifiable Organizations Network","Trinsic","IIW","DID","Aries","Verifiable Credentials","W3C","Trust over IP","Indy", "Real World","Orgbook"]
|
||||
header:
|
||||
image: /images/bcgov-header.webp
|
||||
|
||||
@ -6,7 +6,7 @@ excerpt: >
|
||||
permalink: /government/canada/
|
||||
redirect_from: /public-sector/canada/
|
||||
tags: ["Canada","Verifiable Credentials","DIACC","PCTF","Saskatchewan","Alberta","Ontario","UCVDCC","Real World"]
|
||||
categories: ["Regional"]
|
||||
categories: ["Government"]
|
||||
last_modified_at: 2023-06-10
|
||||
---
|
||||
|
||||
|
||||
@ -2,7 +2,7 @@
|
||||
date: 2019-03-01
|
||||
title: "General Data Protection Regulation (GDPR) of the European Union"
|
||||
toc: false
|
||||
categories: ["Regional"]
|
||||
categories: ["Government"]
|
||||
tags: ["GDPR","Europe","eIDAS","CCPA","eSSIF","eSSIF-Lab"]
|
||||
redirect_from:
|
||||
- public-sector/europe/GDPR/
|
||||
|
||||
@ -2,7 +2,7 @@
|
||||
date: 2020-01-06
|
||||
title: eIDAS - European Electronic Identification and Trust Services
|
||||
excerpt: This Regulation seeks to enhance trust in electronic transactions in the internal market by providing a common foundation for secure electronic interaction between citizens, businesses and public authorities, thereby increasing the effectiveness of public and private online services, electronic business and electronic commerce in the Union.
|
||||
categories: ["Regional"]
|
||||
categories: ["Government"]
|
||||
tags: ["eIDAS","Europe","EU","Trust Framework","EUDI Wallet","EUDI Framework","eIDAS2","eIDAS Bridge"]
|
||||
canonical_url: 'https://decentralized-id.com/government/europe/regulation/edias/'
|
||||
permalink: /government/europe/eu/eidas/
|
||||
|
||||
@ -5,7 +5,7 @@ description: A digital identity available to all Europeans, enabling access to d
|
||||
excerpt: By using the European Digital Identity, the user only has to select the necessary documents that are stored locally on his digital wallet to reply to the bank’s request. Then, verifiable digital documents are created and sent securely for verification to the bank, who can then continue with the application process.
|
||||
permalink: /government/europe/
|
||||
canonical_url: 'https://decentralized-id.com/government/europe/'
|
||||
categories: ["Regional"]
|
||||
categories: ["Government"]
|
||||
tags: ["Ethereum","uPort","Europe","EU","Zug","Finland","Spain","Netherlands","Germany","Catalonia","ESSIFlab","eIDAS","EBSI","Verifiable Credentials","W3C","IDUnion","Aries","Indy"]
|
||||
header:
|
||||
image: /images/european_union-header.webp
|
||||
|
||||
@ -7,7 +7,7 @@ excerpt: >
|
||||
layout: single
|
||||
permalink: government/europe/switzerland/zug/
|
||||
canonical_url: 'https://decentralized-id.com/government/europe/switzerland/zug/'
|
||||
categories: ["Regional"]
|
||||
categories: ["Government"]
|
||||
tags: ["Zug","Switzerland","DID","Aries","uPort","Crypto Valley Association","ProCivis","Europe","Ethereum","Consensys","Real World","Consensys"]
|
||||
header:
|
||||
image: /images/zug-header.webp
|
||||
|
||||
@ -4,7 +4,7 @@ description: a peer-to-peer network of interconnected nodes running a blockchain
|
||||
excerpt: >
|
||||
The European Blockchain Services Infrastructure aims to deliver EU-wide cross-border digital public services using blockchain technology. The EBSI will materialize as a network of distributed nodes across Europe (the blockchain), leveraging an increasing number of applications focused on specific use cases.
|
||||
layout: single
|
||||
categories: ["Regional"]
|
||||
categories: ["Government"]
|
||||
tags: ["Europe","EU","EBSI","ESSIF","GDPR","VIDChain","ValidatedID","Danube","Walt ID","Thales","CIMEA Naric","DXCTechnology","Identyum","Real World","Interop","Education"]
|
||||
canonical_url: 'https://decentralized-id.com/government/europe/eu/ebsi-essif/'
|
||||
redirect_from:
|
||||
|
||||
@ -6,7 +6,7 @@ excerpt: >
|
||||
The preliminary draft of the federal law declared the purpose of the E-ID to be to ensure "secure identification by means of E-ID among private individuals and with authorities". The protection of the personality and fundamental rights of individuals is to be provided by the following principles
|
||||
permalink : /government/europe/switzerland/
|
||||
canonical_url: https://decentralized-id.com/government/europe/switzerland/
|
||||
categories: ["Regional"]
|
||||
categories: ["Government"]
|
||||
tags: ["Europe","Switzerland"]
|
||||
last_modified_at: 2023-06-09
|
||||
---
|
||||
|
||||
@ -6,7 +6,7 @@ excerpt: >
|
||||
The government is committed to realising the benefits of digital identity, without creating ID cards. Earlier this year we published a draft of the UK digital identity and attributes trust framework. This document sets out what rules and standards are needed to protect people’s sensitive identity data when used digitally
|
||||
permalink : /government/europe/united-kingdom/
|
||||
canonical_url: https://decentralized-id.com/government/europe/united-kingdom/
|
||||
categories: ["Regional"]
|
||||
categories: ["Government"]
|
||||
tags: ["Europe","UK","NHS","Digital Staff Passport","Real World"]
|
||||
last_modified_at: 2023-06-09
|
||||
toc: false
|
||||
|
||||
@ -5,7 +5,7 @@ description:
|
||||
excerpt:
|
||||
permalink : /government/europe/eu/data-governance-act/
|
||||
canonical_url: https://decentralized-id.com/government/europe/eu/data-governance-act/
|
||||
categories: ["Regional"]
|
||||
categories: ["Government"]
|
||||
tags: ["Europe","Data Governance Act","EU"]
|
||||
last_modified_at: 2023-06-10
|
||||
published: false
|
||||
|
||||
@ -6,7 +6,7 @@ excerpt: >
|
||||
It would establish a task force to bring together key federal agencies with state and local government representatives to develop secure methods for government agencies to validate identity attributes to protect the privacy and security of individuals and support reliable, interoperable digital identity verification tools in the public and private sectors.
|
||||
permalink: /government/usa/
|
||||
canonical_url: 'https://decentralized-id.com/government/usa/'
|
||||
categories: ["Regional"]
|
||||
categories: ["Government"]
|
||||
tags: ["USA","New York","Austin","Illinois","Wyoming","Utah","FATF","IRS","FTC","Data Privacy","Web3","Digital Immigration Credentials","Verifiable Credentials","Real World"]
|
||||
last_modified_at: 2023-06-28
|
||||
---
|
||||
|
||||
@ -5,7 +5,7 @@ description: The United States Department Homeland Security has been the source
|
||||
excerpt: "The DHS Science and Technology Directorate (S&T) Silicon Valley Innovation Program (SVIP) is keeping pace with the innovation community to tackle the hardest problems faced by DHS and the Homeland Security Enterprise. SVIP expands DHS S&T’s reach to find new technologies that strengthen national security with the goal of reshaping how government, entrepreneurs, and industry work together to find cutting-edge solutions."
|
||||
permalink: /government/usa/dhs/
|
||||
canonical_url: 'https://decentralized-id.com/government/usa/dhs/'
|
||||
categories: ["Regional"]
|
||||
categories: ["Government"]
|
||||
tags: ["USA","DHS","Dignario","Indicio","Trinsic","Mavnet","SecureKey","Spherity","MATTR","Mesur","Stranger Labs","Verified.ME","SICPA","Learning Machine","Transmute","Danube Tech","Factom","Digital Bazaar","Evernym","Respect Network","Solarity","Narf","Celerity","Verifiable Credentials","W3C","Blockcerts","DKMS","USCIS"]
|
||||
layout: single
|
||||
last_modified_at: 2020-11-02
|
||||
|
||||
@ -9,7 +9,7 @@ excerpt: >
|
||||
- The right to opt-out of the sale of their personal information; and
|
||||
- The right to non-discrimination for exercising their CCPA rights.
|
||||
Businesses are required to give consumers certain notices explaining their privacy practices. The CCPA applies to many businesses, including data brokers.
|
||||
category: ["Regional"]
|
||||
category: ["Government"]
|
||||
tags: ["USA","CCPA","California","IAB","IAPP","CPRA","SMART Health Card","Covid 19","Trust Framework"]
|
||||
permalink: government/usa/california
|
||||
redirect_from:
|
||||
|
||||
@ -16,7 +16,7 @@ redirect_from:
|
||||
- hyperledger/hgf-2018/VerifiableOrganizationsNetwork-HGF/
|
||||
- government/canada/von/hgf-2018-presentation/
|
||||
permalink: /government/canada/bcgov/von/hgf-2018-production-government-deployment-hyperledger-indy/
|
||||
categories: ["Regional","History"]
|
||||
categories: ["Government","History"]
|
||||
tags: ["HGF 2018","Indy","Verifiable Organizations Network","Verifiable Credentials","Canada","BCGov","Hyperledger Forum","W3C","Transcript","Real World"]
|
||||
last_modified_at: 2019-07-11
|
||||
---
|
||||
|
||||
@ -6,7 +6,7 @@ excerpt: >
|
||||
The context of the eSSIF-Lab vision can be found in articles 8-10 of the European Convention on Human Rights (ECHR), that state the rights of individuals regarding their privacy, and their freedoms to collect, process, store, and express information in a self-sovereign fashion, i.e. in a way that they can decide for themselves.
|
||||
permalink: /government/europe/eu/essif-lab/
|
||||
canonical_url: 'https://decentralized-id.com/government/europe/eu/essif-lab/'
|
||||
categories: ["Regional","History"]
|
||||
categories: ["Government","History"]
|
||||
tags: ["eIDAS","GDPR","EBSI","EU","Europe","ESSIF","NGI","Interop"]
|
||||
last_modified_at: 2023-06-08
|
||||
---
|
||||
|
||||
55
_posts/organizations/2023-06-05-centre.md
Normal file
55
_posts/organizations/2023-06-05-centre.md
Normal file
@ -0,0 +1,55 @@
|
||||
---
|
||||
title:
|
||||
description:
|
||||
excerpt:
|
||||
layout: single
|
||||
permalink: organizations/centre/
|
||||
canonical_url: 'https://decentralized-id.com/organizations/centre/'
|
||||
categories: ["Organizations"]
|
||||
tags: ["Centre"]
|
||||
last_modified_at: 2023-06-16
|
||||
published: false
|
||||
---
|
||||
|
||||
# Centre - Verite
|
||||
|
||||
## Centre
|
||||
|
||||
* [Centre Consortium](https://www.centre.io/) - [GitHub](https://github.com/centrehq/verite)
|
||||
> Founded by Coinbase and Circle in 2018, the mission is to provide the governance and standards for the future digital financial ecosystem.
|
||||
>
|
||||
> We began by launching US Dollar Coin (USDC), a fiat-backed stablecoin and now the second largest stablecoin on the market. The standards we laid out for USDC provide a layer of trust and transparency so that users can operate with security and confidence as we enter a new world of digital payments.
|
||||
* [Welcome to Centre, Linda Jeng and Danielle Harold](https://www.centre.io/blog/welcome-to-centre-linda-jeng-and-danielle-harold)
|
||||
> “I am thrilled to welcome executives of this caliber to our team,” said David Puth, CEO of Centre. “Both Linda and Danielle bring an abundance of experience that will guide our organization as we create standards for the burgeoning blockchain space.”
|
||||
* [Ledger Joins Project Verite: a Decentralized Identity Coalition for Crypto Finance](https://www.ledger.com/ledger-joins-project-verite-a-decentralized-identity-coalition-for-crypto-finance) Ledger 2/22
|
||||
> We strongly believe that open standards are a key enabler for the development and scaling of new digital identity services around the globe. In this context, we are glad to be part of the Verite Distributed ID standards.” – Mung Ki Woo, VP Trust Services, Ledger
|
||||
|
||||
## Docs
|
||||
* [Verification Patterns, Part 1](https://docs.centre.io/blog/verification-patterns-1) Verite
|
||||
> Since verification is off-chain (and generally fast/inexpensive, depending on the provider), and since this avoids on-chain storage of potentially correlatable data, this is often the preferred solution.
|
||||
* [Introducing Verite](https://docs.centre.io/blog/introducing-verite) Justin Hunter, Pinata, Centre
|
||||
> But as the world shifts to an increasingly digital native format, and as people take more ownership over their identity, how can the issuance of, presentation of, and verification of credentials be managed?
|
||||
|
||||
### Verite
|
||||
* [Verite: A Technical Deep Dive with Kim Hamilton, Director of Identity & Standards](https://www.centre.io/blog/verite-a-technical-deep-dive-with-kim-hamilton-director-of-identity-standards) Centre
|
||||
> Verite is a decentralized identity framework demonstrating end-to-end, ecosystem-scale crypto and DeFi prototypes. With Verite, our focus is iteratively building open protocols rather than a product or a platform
|
||||
* [Introducing Verite](https://verite.id/blog/introducing-verite) Justin Hunter of Pinata
|
||||
> Currently available in TypeScript and [published through NPM](https://www.npmjs.com/package/verite), the Verite library seeks to make it easier to implement VCs in a variety of forms. The library is early and an additional goal of the library is to collect community feedback.
|
||||
* [Verite: Growing a Decentralized Identity Ecosystem](https://www.centre.io/blog/verite-growing-a-decentralized-identity-ecosystem) Centre Consortium
|
||||
> Developed last year and launched in Q1 of 2022, the [Verite standard](https://verite.id/verite) welcomes this flourishing of products and experiments with Verifiable Credentials and other privacy-preserving, data-minimizing patterns and principles.
|
||||
* [Circle and Industry Leaders Have Built the First Decentralized Identity Proof-of-Concept for Crypto Finance using Centre Verite Credentials](https://www.centre.io/blog/circle-and-industry-leaders-have-built-the-first-decentralized-identity-proof-of-concept-for-crypto-finance-using-centre-verite-credentials) Centre ([ANN-thread](https://twitter.com/circlepay/status/1575979855681753088)
|
||||
> Together with Archblock, the team behind the TrueFi protocol, MetaMask Institutional and Parallel Markets, Circle Internet Financial has built the first proof-of-concept for “know your business” (KYB) verification using [Verite](https://www.centre.io/verite/faq), Centre's set of open source protocols for decentralized digital identity credentials
|
||||
|
||||
## Policy
|
||||
* [Response to FinCEN RFI](https://www.centre.io/blog/centres-response-to-fincen-rfi) Centre
|
||||
> In this letter, we focus on two questions relevant to identifying Bank Secrecy Act (“BSA”) regulations and guidance that may be outdated, redundant, or do not promote a risk-based AML/CFT regulatory regime
|
||||
* [Centre’s Response to Australian Treasury](https://www.centre.io/blog/centres-response-to-australian-treasury) Centre
|
||||
> In this letter, we focus on a couple of issues that would be beneficial in expanding the Australian regulatory frameworks to include crypto assets. Furthermore, our comments pertain specifically to fiat-backed stablecoins, which are backed on a 1:1 basis by reserve assets, such as bank deposits and short-term government bonds.
|
||||
|
||||
## Development
|
||||
* [How To Create a Verifiable Credentials Registry Smart Contract in Solidity](https://docs.centre.io/blog/build-a-smart-contract-registry-solidity) Centre
|
||||
> When using the [smart contract pattern](https://docs.centre.io/verite/patterns/smart-contract-verite) for verifications, you can use any blockchain you would like. For the sake of this guide, we will focus on [Solidity](https://docs.soliditylang.org/en/v0.8.11/), which is the programming language for the Ethereum Virtual Machine.
|
||||
* [How To Use Verifiable Credentials And Verite To Build An Off-Chain NFT Allowlist](https://docs.centre.io/blog/NFT-allowlists-with-verifiable-credentials-and-verite) Justin Hunter, Pinata, Centre
|
||||
> if the signature is verified, we allow the minting to happen. When that's complete, we update the PREVIOUS_SIGNATURE variable. This is, as with many things in this demo, a simplified replay attack prevention model. This can and probably should be extended to support your own use cases.
|
||||
|
||||
|
||||
@ -1,9 +1,10 @@
|
||||
---
|
||||
date: 2019-03-11
|
||||
title: Identity Articles, Research and Literature
|
||||
title: "Research, Reports, and other Literature related to Self Sovereign Identity"
|
||||
layout: single
|
||||
description: A selection of DID related literature and top level resources for discovery of more.
|
||||
excerpt: A selection of DID related literature and top level resources for discovery of more.
|
||||
description: Verifiable credentials and digital wallets offer a convenient, secure, and privacy-oriented alternative to current physical and digital identity management systems.
|
||||
excerpt: >
|
||||
provides an overview of the SSI properties, focusing on an in-depth analysis, furthermore presenting a comprehensive collection of SSI properties that are important for the implementation of the SSI system.
|
||||
header:
|
||||
image: /images/literature-christian-wiediger-unsplash.webp
|
||||
categories: ["Resources"]
|
||||
@ -13,7 +14,7 @@ toc_sticky: false
|
||||
redirect_from:
|
||||
- literature
|
||||
- literature/
|
||||
permalink: resources/literature/
|
||||
permalink: /resources/literature/
|
||||
canonical_url: 'https://decentralized-id.com/resources/literature/'
|
||||
last_modified_at: 2023-06-19
|
||||
---
|
||||
|
||||
@ -1,5 +1,5 @@
|
||||
---
|
||||
title: "Resources and Introduction to Decentralized Identity"
|
||||
title: "Introduction to Decentralized Identity"
|
||||
description: Getting Started with Decentralized, Self Sovereign, Digital Identity
|
||||
excerpt: >
|
||||
The essence of Decentralized-ID is in creating open standards for a privacy preserving internet-wide identity layer — not owned by any one particular organization, but interoperable between all.
|
||||
@ -12,9 +12,9 @@ redirect_from:
|
||||
- /getting-started/
|
||||
- /resources/
|
||||
toc: true
|
||||
categories: ["Resources"]
|
||||
tags: ["101","Resources"]
|
||||
last_modified_at: 2023-06-29
|
||||
categories: ["About"]
|
||||
tags: ["101"]
|
||||
last_modified_at: 2023-07-01
|
||||
---
|
||||
|
||||
## Essence of Decentralized Identity
|
||||
@ -34,28 +34,29 @@ It's impossible to have a conversation about decentralized-id without discussing
|
||||
{: .notice--info}
|
||||
|
||||
## Getting Started with Decentralized, Self Sovereign, Digital Identity
|
||||
* [Unwrapping the Decentralised Identity Landscape](https://www.affinidi.com/post/unwrapping-the-decentralised-identity-landscape) 2022-07-08 Affinidi
|
||||
> This framework empowers individuals to own his or her data, decide where to store it, and choose to share some or all of it with others. Often, this decentralised identity is used to create verifiable and shareable data for securely accessing products and services.
|
||||
* [Decentralized identity: The Direct Presentation model](https://techcommunity.microsoft.com/t5/identity-standards-blog/decentralized-identity-the-direct-presentation-model/ba-p/3071981) 2022-02-02 Microsoft
|
||||
> The technical name for the model at work here is called the Direct Presentation model. A credential is issued, and then held for a long period of time with intermittent voluntary presentations to many different verifiers. To put that back into our example, my auto club issues me a card, which I hold in my wallet for years (maybe decades!), and I might choose to show that card to a garage when I need a tow, or possibly to a store to get a discount.
|
||||
> The technical name for the model at work here is called the Direct Presentation model. A credential is issued, and then held for a long period of time with intermittent voluntary presentations to many different verifiers.
|
||||
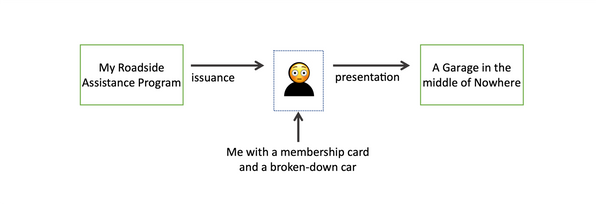
|
||||
* [New to the topic of self-sovereign identity?](https://threadreaderapp.com/thread/1405788127265005571.html) 2021-06-18 SSIAmbassador
|
||||
> No problem, there are several beginner #guides, which you can use to get familiar with the new standard for digital #identity.
|
||||
* [Video] [Understanding the SSI Identity Model with Verifiable Credentials](https://www.youtube.com/watch?v=TRuz39SEX7E) 2021-11-13 Manning
|
||||
> Drummond Reed, an expert in Internet identity, security, privacy, and trust frameworks, explains the basic building blocks of SSI and how this new identity model fundamentally works.
|
||||
* [Video] [Karyl Fowler (Transmute) and Juan Caballero (DIF) present Intro to SSI at #IIW31](https://www.youtube.com/watch?v=DaM0UtQTLCs) 2020-10 Keryl Fowler, Juan Caballero [Slides](https://drive.google.com/file/d/1_9jCcxgcCrL4Dfjvr4z7XSIwxfadjveR/view?usp=sharingQ)
|
||||
> Karyl and Juan revisited their slide deck from #IIW30 to give an overview of decentralized identity first as a "philosophy" at the confluence of ideological currents (Juan), and then as a set of specific emerging technologies which unlocks new mental models and business models that are still coming into focus sector by sector (Karyl). There follows a brief overview of educational resources, including some products of DIF's recent educational "content sprint," and a wide-ranging Q&A including podcast recommendations and how to navigate open standards for the first time. The slides are here, in downloadable and hyperlinked PDF form:
|
||||
> an overview of decentralized identity first as a "philosophy" at the confluence of ideological currents (Juan), and then as a set of specific emerging technologies which unlocks new mental models and business models that are still coming into focus sector by sector (Karyl). There follows a brief overview of educational resources, including some products of DIF's recent educational "content sprint," and a wide-ranging Q&A including podcast recommendations
|
||||
> 
|
||||
* [What Is Self-Sovereign Identity?](https://trinsic.id/what-is-self-sovereign-identity/) 2020-04-28 Trinsic
|
||||
> Self-sovereign identity is the marriage of real identity with the digital world that will ultimately make people’s lives better.² It’s still in its infancy, and there is a long road ahead to truly make digital identity as legitimate and nuanced as a real-world identity.
|
||||
* [Explaining SSI to C-suite executives, and anyone else for that matter – John Phillips](https://ssimeetup.org/explaining-ssi-c-suite-executives-anyone-else-john-phillips-webinar-48/) 2020-02-18 SSIMeetup
|
||||
> John Phillips from 460degrees in Australia has been exploring with his team for more than two years for a way to describe Self-Sovereign Identity (SSI) that was easy to understand. We think he has found a good method to make SSI easy to understand for any C-suite executive and business people that goes beyond the technology.
|
||||
> John will share the learnings he is gaining from University research, as well as the results of work in supporting capstone projects for higher education students, and how this has led us to a storytelling model to explain SSI.
|
||||
* [The Need for Good Digital ID is Universal](https://id2020.org/digital-identity) 2019-02-26 ID2020 Foundation
|
||||
> The ability to prove who you are is a fundamental and universal human right. Because we live in a digital era, we need a trusted and reliable way to do that both in the physical world and online.
|
||||
* [The Laws of Identity](http://www.windley.com/archives/2019/01/the_laws_of_identity.shtml) 2019-01 Phil Windley
|
||||
> The Internet was created without any way to identify the people who used it. The Internet was a network of machines. Consequently, all the identity in Internet protocols is designed to identify machines and services. People used the Internet through some institution (their company or university) and were part of that institution's administrative identity system. This can still be seen in the format of email addresses that identify both recipient and sender as someone@someplace. As the Internet grew to include people who weren't formally associated with an institution, every Web site and service created their own administrative identity domains. The result is the fractured plethora of identifiers, policies, and user experiences that constitute digital identity in 2019.
|
||||
> As the Internet grew to include people who weren't formally associated with an institution, every Web site and service created their own administrative identity domains. The result is the fractured plethora of identifiers, policies, and user experiences that constitute digital identity in 2019.
|
||||
* [The Inevitable Rise of Self-Sovereign Identity](https://sovrin.org/wp-content/uploads/2018/03/The-Inevitable-Rise-of-Self-Sovereign-Identity.pdf) 2018-03 Sovrin Foundation
|
||||
> This lack of secure, portable, user-controlled identity has some dire consequences. It means that a person’s identity and personal data only exists within the context of each specific website or application he or she uses. Stop using the site or application and the person’s digital existence is meaningless. And a user’s control over their identity and data must be exerted on a site-by-site, app-by-app basis.
|
||||
> This lack of secure, portable, user-controlled identity has some dire consequences. It means that a person’s identity and personal data only exists within the context of each specific website or application he or she uses.
|
||||
* [The Rising Tide of Decentralized Identity](https://medium.com/decentralized-identity/the-rising-tide-of-decentralized-identity-2e163e4ec663) 2017-10-11 Decentralized Identity Foundation
|
||||
> Creating a unified decentralized identity ecosystem requires addressing a set of fundamental user needs and technical challenges:
|
||||
> - Enabling registration of self-sovereign identifiers that no provider owns or controls.
|
||||
> - The ability to lookup and discover identifiers and data across decentralized systems.
|
||||
> - Providing a mechanism for users to securely store sensitive identity data, and enabling them to precisely control what is shared with others.
|
||||
@ -63,75 +64,58 @@ It's impossible to have a conversation about decentralized-id without discussing
|
||||
* [The Case for Decentralized Identity](https://www.windley.com/archives/2017/08/the_case_for_decentralized_identity.shtml) 2017-08 Phil Windley
|
||||
> We cannot decentralize many interesting systems without also decentralizing the identity systems upon which they rely. We're finally in a position to create truly decentralized systems for digital identity.
|
||||
* [The Path to Self-Sovereign Identity](https://github.com/ChristopherA/self-sovereign-identity/blob/master/ThePathToSelf-SovereignIdentity.md) 2017-03-01 Christopher Allen
|
||||
> Self-sovereign identity is the next step beyond user-centric identity and that means it begins at the same place: the user must be central to the administration of identity. That requires not just the interoperability of a user’s identity across multiple locations, with the user’s consent, but also true user control of that digital identity, creating user autonomy. To accomplish this, a self-sovereign identity must be transportable; it can’t be locked down to one site or locale.
|
||||
> That requires not just the interoperability of a user’s identity across multiple locations, with the user’s consent, but also true user control of that digital identity, creating user autonomy. To accomplish this, a self-sovereign identity must be transportable; it can’t be locked down to one site or locale.
|
||||
* [A Technology‐Free Definition of Self‐Sovereign Identity](https://raw.githubusercontent.com/jandrieu/rebooting-the-web-of-trust-fall2016/master/topics-and-advance-readings/a-technology-free-definition-of-self-sovereign-identity.pdf) 2016-10 Joe Andrieu RWoT3
|
||||
> Abstract The desire for increased control over our identity has catapulted the idea of “self‐sovereign identity” into the forefront of digital identity innovation, yet the term lacks a rigorous definition beyond specific technical implementations1. This paper explores what self‐sovereign identity means independent of technology: what people need from independent identity capabilities. I want to understand how such a system enables both individuals whose identities are in play (subjects), as well as those who use those “identities” to correlate interactions across contexts (observers). I start with grounding individual sovereignty in the Enlightenment and identity in its core function of correlation, then propose core characteristics of a self‐sovereign identity system. My eventual goal is to model the technology‐independent requirements of a self‐sovereign solution suitable for realizing UN Sustainable Development Goal 16.9: “Providing every last person on the planet with a legal identity by 2030.”
|
||||
> I want to understand how such a system enables both individuals whose identities are in play (subjects), as well as those who use those “identities” to correlate interactions across contexts (observers). I start with grounding individual sovereignty in the Enlightenment and identity in its core function of correlation, then propose core characteristics of a self‐sovereign identity system.
|
||||
|
||||
{% include video id="DaM0UtQTLCs" provider="youtube" %}
|
||||
|
||||
## Digital Identity 101
|
||||
If you're looking to freshen up on your digital identity fundamentals, the following resources will be a good place to start.
|
||||
## Frequently Asked Questions
|
||||
* [Knowledgebase] [DIF "Frequently Asked Questions"](https://identity.foundation/faq/) 2022-07-08
|
||||
> This is the Decentralized Identity Foundation’s general-purpose knowledgebase, which aims to help people at all levels of familiarity with our problem space quickly level-set and find the most useful links and ideas as they explore the space.
|
||||
* [19 FAQs on Verifiable Credentials and Self-Sovereign Identity](https://academy.affinidi.com/faqs-on-verifiable-credentials-and-self-sovereign-identity-3c3a505878bc) 2021-05-31 Affinidi
|
||||
> This article has some FAQs on the basics of Verifiable Credentials (VCs) and Self-Sovereign Identity (SSI).
|
||||
* [Answering Questions about Self-Sovereign Identity](https://www.windley.com/archives/2019/07/answering_questions_about_self-sovereign_identity.shtml) 2019-07 Phil Windley
|
||||
> Identity professionals continue to have questions about self-sovereign identity (SSI). In this post, I answer a few questions that Susan Morrow raised about the commercial viability, security, privacy, and desired user experience of SSI.
|
||||
|
||||
## Myth
|
||||
* [For traditional identity models, the biggest misconception is “strong passwords”](https://idramp.com/for-traditional-identity-models-the-biggest-misconception-is-strong-passwords/) 2022-07-20 IDRamp
|
||||
> One way to avoid password-related problems is to use decentralized identity management. This method is relatively new, so the best way to gain knowledge about it – contact the experts. For this reason, we are speaking with Mike Vesey, CEO of [IdRamp](https://idramp.com/).
|
||||
* [Myths about SSI](http://web.archive.org/web/20230209024203/https://jolocom.io/blog/myths-about-ssi/) 2022-05-25 Jolocom
|
||||
> The idea that as a user of SSI I have complete sovereignty over my digital identity is often misunderstood. At its core, SSI is about my digital identity being under my own control, so I can decide to whom I show my data, when, and for what.
|
||||
* [myths and facts. Is Self-Sovereign Identity Dangerous?](http://web.archive.org/web/20230209034007/https://jolocom.io/blog/mythen-und-fakten-ist-self-sovereign-identity-gefahrlich/) 2022-05-05 Jolocom (in german)
|
||||
> we examine more closely whether self-sovereign identity can increase or reduce risks for data misuse in certain cases.
|
||||
* [7 Myths of Self Sovereign Identity](https://medium.com/evernym/7-myths-of-self-sovereign-identity-67aea7416b1) 2018-10-31 Evernym
|
||||
> - Self-sovereign means self-attested.
|
||||
> - SSI attempts to reduce government’s power over an identity owner.
|
||||
> - SSI creates a national or “universal ID” credential.
|
||||
> - SSI gives absolute control over identity.
|
||||
> - There’s a “main” issuer of credentials.
|
||||
> - There’s a built-in method of authenticating.
|
||||
> - User-centric identity is the same as SSI.
|
||||
|
||||
## Digital Identity 101
|
||||
* [Understanding Online Identity](https://educatedguesswork.org/posts/understanding-identity/) 2022-06-02 EducatedGuessWork (broad contextualization)
|
||||
> As noted above, the ergonomics of having to make an account on every new system are fairly bad: it requires the user to have a large number of passwords, which is more opportunities to use a bad password or to lose your password and have to recover. There are some opportunities for improvement around the margin (e.g., WebAuthn instead of passwords for authentication), better form fill-in so users don't have to type their name over and over, etc, but at the end of the day, there's only so much you can do.
|
||||
* [Why do you care about identity?](https://wider.team/2022/01/18/phil-cares-about-identity/) 2022-01-18 Phil Wolff
|
||||
> I love that it’s more than a technical discussion. It’s laws. Sociology. Politics and civics. Commerce. Psychology. Ethics. History. Economy. All the humanities.
|
||||
>
|
||||
> Identity touches everything. It always will. Computation and communication continue their pervasion, and identity spreads with them.
|
||||
* [Difference Between Authentication and Authorization](https://www.beyondtrust.com/blog/entry/understanding-authentication-vs-authorization) 2020-10-19 Beyond Trust
|
||||
> What is the difference between authentication (authN) versus authorization (authZ)? While these two fundamental security terms are often confused with each other, the only real similarity is they both begin with the letter “A” and are linked by an account. In concept, one verifies the account (authentication) and the other sanctions (authorization) the account to perform a task. Because these terms are so fundamental, it’s crucial to understand the difference between them, and the implications for each when the concepts are blended
|
||||
> In concept, one verifies the account (authentication) and the other sanctions (authorization) the account to perform a task. Because these terms are so fundamental, it’s crucial to understand the difference between them, and the implications for each when the concepts are blended
|
||||
* [Guide to Digital Identity — Part 1](https://medium.com/@dip_ak/guide-to-digital-identity-part-1-4b7c8fe45ee1) 2020-04-08 Deepak Gupta
|
||||
> Are you curious about the Digital Identity Ecosystem? If you have been looking for a good, reliable and easy-to-understand source of information and haven’t had any luck, then this article is for you.
|
||||
> Digital Identity is the new focus for many businesses, regulators and governments in a data-driven and hyper-connected world. The concept can be seen as an integration of two components — belongingness and separation.
|
||||
* [Member Presentations](https://idpro.org/educational-resources/) Identiverse 2019 [playlist](https://www.youtube.com/playlist?list=PLpKq7xRiIHaTDwAqpIU1UYpKZY03tfTMf)
|
||||
* [2019 - Introduction to Identity Part 1](https://www.youtube.com/watch?v=T5w1EXqMqR0&list=PLpKq7xRiIHaTDwAqpIU1UYpKZY03tfTMf) 2019-06-25 Identiverse
|
||||
> This workshop — provided by IDPro — will provide a comprehensive (and fun) introductory view of the identity world that will give participants a solid understanding of IAM’s foundations. Part 1 of this 2-part class begins with the basics like directories, identity proofing, provisioning, authentication (including multi-factor), authorization, as well as federation technologies like SAML, OAuth, and OpenID Connect. In Part 2, we build on those foundational technologies to explain PKI & digital certificates, privileged access management, identity for IoT, identity assurance, privacy issues, identity standards organizations, and even known attack vectors.
|
||||
* [2019 - Introduction to Identity Part 1](https://www.youtube.com/watch?v=T5w1EXqMqR0&list=PLpKq7xRiIHaTDwAqpIU1UYpKZY03tfTMf) 2019-06-25 Identiverse, IDPro
|
||||
> begins with the basics like directories, identity proofing, provisioning, authentication (including multi-factor), authorization, as well as federation technologies like SAML, OAuth, and OpenID Connect.
|
||||
* [Introduction to Identity Part 2](https://www.youtube.com/watch?v=zxKRUXmTLJs) 2019-06-25 Identiverse
|
||||
> we build on those foundational technologies to explain PKI & digital certificates, privileged access management, identity for IoT, identity assurance, privacy issues, identity standards organizations, and even known attack vectors.
|
||||
* [Modern Identity for Developers 101](https://www.youtube.com/watch?v=kWpqFWz_9II) 2019-06-25 Identiverse
|
||||
> Modern identity promises to solve some of the thorniest problems that historically plagued handling authentication and access control in applications. That sounds great in theory, but how do thinks really look like when the rubber hits the road – what does it take to incorporate modern identity in your applications development practice? Come to this session to learn the basis of modern identity development and be better equipped to understand and participate to the session in this year’s Identiverse development track.
|
||||
> Come to this session to learn the basis of modern identity development and be better equipped to understand and participate to the session in this year’s Identiverse development track.
|
||||
* [An Introduction to Mobile Identity](https://www.youtube.com/watch?v=25qiVyZEZOg&list=PLpKq7xRiIHaTDwAqpIU1UYpKZY03tfTMf&index=18) 2019-06-25 Identiverse
|
||||
* [What is Identity and Access Management and Why is it a Vital IT Security Layer?](https://www.beyondtrust.com/blog/entry/what-is-identity-and-access-management-and-why-is-it-a-vital-it-security-layer) 2018-11-29 Beyond Trust
|
||||
> Identity and Access Management (IAM), also called identity management, refers to the IT security discipline, framework, and solutions for managing digital identities. Identity management encompasses the provisioning and de-provisioning of identities, securing and authentication of identities, and the authorization to access resources and/or perform certain actions. While a person (user) has only one singular digital identity, they may have many different accounts representing them. Each account can have different access controls, both per resource and per context.
|
||||
> Identity and Access Management (IAM), also called identity management, refers to the IT security discipline, framework, and solutions for managing digital identities.
|
||||
* [What is Digital Identity?](https://medium.com/humanizing-the-singularity/what-is-digital-identity-c77983c03306) 2018-06-04 Humanizing the Internet
|
||||
> The Sapir–Whorf Hypothesis, also known as the principle of linguistic relativity, posits that language constructs our reality and worldview. While the hypothesis has been contested over the years, language is unarguably fundamental to the models of the world we build in our heads — and in our systems.
|
||||
> The Sapir–Whorf Hypothesis, also known as the principle of linguistic relativity, posits that language constructs our reality and worldview.
|
||||
|
||||

|
||||
|
||||
## Glossaries
|
||||
|
||||
* [Aries RFC 0006: SSI Notation](https://github.com/hyperledger/aries-rfcs/blob/main/concepts/0006-ssi-notation/README.md) 2019-06-20 Daniel Hardman Hyperledger Foundation
|
||||
> This RFC describes a simple, standard notation for various concepts related to decentralized and self-sovereign identity (SSI).
|
||||
* [IDCommongs - Lexicon](http://wiki.idcommons.org/Lexicon) 2014-08-18 IDCommons
|
||||
* [Identipedia](http://wiki.idcommons.org/Identipedia) 2008-01-22 IDCommons
|
||||
* [Systemic Elements](http://wiki.idcommons.org/Systemic_Elements) 2008-01-22 IDCommons
|
||||
|
||||
## Resources
|
||||
|
||||
* [Directory] [Global Verifiable Credential Adoption](https://trinsic.notion.site/trinsic/Global-Verifiable-Credential-Adoption-78c7e4c5f2a34a228a55d03db54ab399) 2023-07-05 Trinsic
|
||||
> 🔥 This is a community resource for tracking the adoption of verifiable credentials around the world. Please have a look around and join 10+ others who have contributed!
|
||||
* [Curated List] [animo/awesome-self-sovereign-identity/](https://github.com/animo/awesome-self-sovereign-identity) 2023-07-07 Animo
|
||||
> An awesome list of self-sovereign identity resources.
|
||||
* [Blog] [Phil Windley - Tags: identity](http://www.windley.com/tags/identity.shtml) 2023-06-26 [[Videos](https://vimeo.com/windley/videos)]
|
||||
> Phil Windley is a Senior Software Development Manager at AWS Identity. He is also the co-founder and organizer of the [Internet Identity Workshop](http://internetidentityworkshop.com/). [...] He was the Founding Chair of the Sovrin Foundation serving from 2016 to 2020, writes the popular Technometria blog, and is the author of the books [Learning Digital Identity](https://www.oreilly.com/library/view/learning-digital-identity/9781098117689/) (O'Reilly, Media 2023), [The Live Web](http://www.amazon.com/exec/obidos/ASIN/1133686680/windleyofente-20) (Course Technology, 2011), and [Digital Identity](http://www.amazon.com/exec/obidos/ASIN/0596008783/windleyofente-20) (O'Reilly Media, 2005). Phil has been a computer science professor at BYU and the University of Idaho, founder and CTO of several internet technology companies, and served as CIO for the State of Utah.
|
||||
* [Blog] [Identity Woman](https://identitywoman.net/) 2023-06-13
|
||||
> Kaliya Young (formerly Hamlin) is an expert in self-sovereign identity and identity on the blockchain. She is the co-author of a Comprehensive guide to Self-Sovereign Identity and is widely known as Identity Woman (its also the name of her blog and her twitter handle). She is committed her life to the development of an open standards based layer of the internet that empowers people.
|
||||
* [Publication] [SSI Meetup](http://ssimeetup.org/) 2023-06-20 [[Slides](https://www.slideshare.net/SSIMeetup/presentations/)] [[Videos](https://www.youtube.com/channel/UCSqSTlKdbbCM1muGOhDa3Og)]
|
||||
> To create Self-Sovereign Identity, knowledge tools and empower SSI evangelists around the world to set-up their own local communities without boundaries. The only focus is to make SSI happen with Blockchain & other technologies.
|
||||
* [Curated List] [karimStekelenburg/awesome-self-sovereign-identity](https://github.com/karimStekelenburg/awesome-self-sovereign-identity) 2023-06-07 Karim Stekelnburg
|
||||
> An awesome list of self-sovereign identity resources.
|
||||
* [Blog] [Identity Woman in Business](https://medium.com/@identitywoman-in-business) 2023-05-31
|
||||
> We provide consulting and advisory services to organizations across the world to help them succeed in adopting, developing and investing in Decentralized ID.
|
||||
* [Wiki] [IIW-Wiki](https://iiw.idcommons.net/Main_Page) 2023-01-05 IDCommons [[Past Workshop Proceedings](https://internetidentityworkshop.com/past-workshops/)]
|
||||
> The Internet Identity Workshop has been finding, probing and solving identity issues twice every year since 2005. We meet in the Computer History Museum in Mountain View, CA. Every IIW moves topics, code and projects downfield. Name an identity topic and it’s likely that more substantial discussion and work has been done at IIW than any other conference!
|
||||
* [Collection] [WebOfTrustInfo/self-sovereign-id/](https://github.com/WebOfTrustInfo/self-sovereign-identity) 2022-12-07 Rebooting Web of Trust
|
||||
> Articles and documents associated with designing and implementing identity technology using self-sovereign identity principles
|
||||
* [Course] [Getting Started with Self-Sovereign Identity](https://www.edx.org/course/getting-started-with-self-sovereign-identity) 2022-10-05 Kaliya & Lucy via Linux Foundation and EdX
|
||||
> Gain a solid foundation on self-sovereign identity (SSI) with a 360 degree overview of its evolutionary journey, key concepts, standards, technological building blocks, use cases, real-world examples and implementation considerations.
|
||||
* [Directory] [The open SSI / DID Directory](https://ssi-did-directory.gitbook.io/open-directory-for-all/) 2022-09-24 Open DID \ SSI Directory
|
||||
> Important: This directory is here for all of us to learn. You do not have to be technical to contribute, but we expect you to do your research before you contribute. We are blockchain agnostic.
|
||||
* [Knowledgebase] [DIF "Frequently Asked Questions"](https://identity.foundation/faq/) 2022-07-08
|
||||
> This is the Decentralized Identity Foundation’s general-purpose knowledgebase, which aims to help people at all levels of familiarity with our problem space quickly level-set and find the most useful links and ideas as they explore the space. It is structures as a (very exhaustive) list of questions and answers. Feel free to share “anchor links” to specific questions using the § symbol next to individual questions or section/sub-section headings.
|
||||
* [Curated List] [peacekeeper/blockchain-identity](https://github.com/peacekeeper/blockchain-identity) 2021-11-23 Markus Sabadello
|
||||
* [Book] [Self-Sovereign Identity : Decentralized digital identity and verifiable credentials](https://www.manning.com/books/self-sovereign-identity#toc) 2021-05 Manning
|
||||
> It combines a clear, jargon-free introduction to this blockchain-inspired paradigm shift with interesting essays written by its leading practitioners. Whether for property transfer, ebanking, frictionless travel, or personalized services, the SSI model for digital trust will reshape our collective future.
|
||||
* [Blog] [Identity Blog](https://identityblog.com) 2020-08-24 Kim Cameron
|
||||
> Many readers will already know that I retired from Microsoft after twenty years working as Chief Architect of Identity and other related roles. I had a great time there, and Microsoft adopted the Laws of Identity in 2005 at a time when most tech companies were still under dark influence of “Privacy is Dead”, building systems destined to crash at endless cost into a privacy-enabled future. Microsoft is a big complicated place, but Bill Gates and Satya Nadella were as passionate as me about moving Microsoft and the industry towards digital identity respectful of the rights of individuals and able to empower both individuals and organizations. I thank them and all my wonderful colleagues and friends for a really great ride.
|
||||
* [Wiki] [wiki.idcommons.net](http://wiki.idcommons.net/Main_Page) 2014-08-17 IIW IDCommons
|
||||
> We are a community of groups working on addressing the social, legal and technical issues that arise with the emerging, identity, data and social layer of the internet.
|
||||
|
||||
@ -1,46 +0,0 @@
|
||||
---
|
||||
title: SSI and Decentralized Identity Podcasts
|
||||
description: "exploring the ever-growing ecosystems around Self-Sovereign Identity, Decentralized Technologies and Digital Trust"
|
||||
excerpt: >
|
||||
Digital networks have centralized power over identities and information, creating problems for both markets and democracy. Does the solution require more shared agency over data? What might that look like? This panel discussion is structured around thought experiments to find solutions to this issue.
|
||||
layout: single
|
||||
permalink: resources/podcasts/
|
||||
toc: true
|
||||
redirect_from:
|
||||
- media/
|
||||
- podcasts/
|
||||
canonical_url: 'https://decentralized-id.com/resources/podcasts/'
|
||||
categories: ["Resources"]
|
||||
tags: ["Resources"]
|
||||
last_modified_at: 2023-06-29
|
||||
---
|
||||
|
||||
## Current
|
||||
* [RadicalxChange (RxC) is a global movement for next-generation political economies.](https://radicalxchange-s.simplecast.com/) RxC Glen Weyl
|
||||
> Digital networks have centralized power over identities and information, creating problems for both markets and democracy. Does the solution require more shared agency over data? What might that look like? This panel discussion is structured around thought experiments to find solutions to this issue.
|
||||
* [The SSI Orbit Podcast](https://podcasts.apple.com/ca/podcast/ssi-orbit-podcast-self-sovereign-identity-decentralized/id1552622325) Northern Block Mathieu Glaude
|
||||
* [Let’s Talk About Digital Identity (LTADI)](https://www.ubisecure.com/lets-talk-about-digital-identity-podcast/) Ubisecure
|
||||
* [MyData Podcast](https://mydata.org/podcast/)
|
||||
* [Next Level Supply Chain Podcast with GS1](https://next-level-supply-chain-with-gs1us.podcastpage.io/)
|
||||
* [The Week in Identity](https://podcasters.spotify.com/pod/show/the-cyber-hut/) The CyberHut
|
||||
* [Digital Identity and Self Sovereignty](https://www.traceyfollows.com/tag/podcast/) Tracey Follows
|
||||
* [ID Talk](https://findbiometrics.com/topics/id-talk-podcast/) FindBiometrics
|
||||
|
||||
## Archive
|
||||
* [Identity, Unlocked](http://identityunlocked.auth0.com/) Auth0
|
||||
* [Identity Masters Podcast](https://open.spotify.com/show/0NmFDoGu9zq3r1nmgjwkhQ) Authenteq
|
||||
* [Definitely Identity](https://podcasts.apple.com/ca/podcast/definitely-identity/id1496565155) Tim Bouma
|
||||
* [The Digital Identity Transformation](https://idramp.com/the-digital-identity-transformation-podcast/) IDRamp
|
||||
* [Federal Blockchain News](https://www.spreaker.com/show/federal-blockchain-news) - (covers work with DHS and other govt agencies)
|
||||
* [Identity North Podcast](https://podcasts.apple.com/ca/podcast/identity-north-podcast/id1450122415) Identity North
|
||||
* [Privacy, Surveillance and Anonymity](https://open.spotify.com/show/0lkmZrdHMIJrkIEqT13SJQ) Kaliya 'Identity Woman' Young and Seth Goldstein
|
||||
|
||||
## Posts
|
||||
|
||||
* [My podcasts of choice](https://blogs.harvard.edu/doc/2021/05/04/podcasts/) 2021-05-04 Doc Searls
|
||||
* [Listening to identity podcasts is our 2021 new year’s resolution](https://www.ubisecure.com/education/why-listen-to-identity-podcasts/)
|
||||
> A gem we must have missed last month from Ubisecure, lists the identity podcasts that should be on our list.
|
||||
> - [Let’s Talk About Digital Identity (LTADI)](https://www.ubisecure.com/lets-talk-about-digital-identity-podcast/) – Ubisecure
|
||||
> - [Definitely Identity](https://podcasts.apple.com/ca/podcast/definitely-identity/id1496565155) – Tim Bouma
|
||||
> - [ID Talk](https://findbiometrics.com/topics/id-talk-podcast/) – FindBiometrics and, as you’d expect, focused on the biometrics space
|
||||
> - [State of Identity](https://oneworldidentity.com/podcast-main/) – OWI
|
||||
89
_posts/resources/2021-04-17-resources.md
Normal file
89
_posts/resources/2021-04-17-resources.md
Normal file
@ -0,0 +1,89 @@
|
||||
---
|
||||
title: "Directories, Courses, Curated Lists, Blogs, Podcasts and other Resources on Decentralized Identity"
|
||||
description: "exploring the ever-growing ecosystems around Self-Sovereign Identity, Decentralized Technologies and Digital Trust"
|
||||
excerpt: >
|
||||
Digital networks have centralized power over identities and information, creating problems for both markets and democracy. Does the solution require more shared agency over data? What might that look like? This panel discussion is structured around thought experiments to find solutions to this issue.
|
||||
layout: single
|
||||
permalink: resources/
|
||||
toc: true
|
||||
redirect_from:
|
||||
- media/
|
||||
- podcasts/
|
||||
canonical_url: 'https://decentralized-id.com/resources/'
|
||||
categories: ["Resources"]
|
||||
tags: ["Resources"]
|
||||
last_modified_at: 2023-07-30
|
||||
---
|
||||
|
||||
## General
|
||||
|
||||
* [Directory] [Global Verifiable Credential Adoption](https://trinsic.notion.site/trinsic/Global-Verifiable-Credential-Adoption-78c7e4c5f2a34a228a55d03db54ab399) 2023-07-05 Trinsic
|
||||
> 🔥 This is a community resource for tracking the adoption of verifiable credentials around the world. Please have a look around and join 10+ others who have contributed!
|
||||
* [Curated List] [animo/awesome-self-sovereign-identity/](https://github.com/animo/awesome-self-sovereign-identity) 2023-07-07 Animo
|
||||
> An awesome list of self-sovereign identity resources.
|
||||
* [Publication] [SSI Meetup](http://ssimeetup.org/) 2023-06-20 [[Slides](https://www.slideshare.net/SSIMeetup/presentations/)] [[Videos](https://www.youtube.com/channel/UCSqSTlKdbbCM1muGOhDa3Og)]
|
||||
> To create Self-Sovereign Identity, knowledge tools and empower SSI evangelists around the world to set-up their own local communities without boundaries. The only focus is to make SSI happen with Blockchain & other technologies.
|
||||
* [Curated List] [karimStekelenburg/awesome-self-sovereign-identity](https://github.com/karimStekelenburg/awesome-self-sovereign-identity) 2023-06-07 Karim Stekelnburg
|
||||
> An awesome list of self-sovereign identity resources.
|
||||
* [Wiki] [IIW-Wiki](https://iiw.idcommons.net/Main_Page) 2023-01-05 IDCommons [[Past Workshop Proceedings](https://internetidentityworkshop.com/past-workshops/)]
|
||||
> The Internet Identity Workshop has been finding, probing and solving identity issues twice every year since 2005. We meet in the Computer History Museum in Mountain View, CA. Every IIW moves topics, code and projects downfield. Name an identity topic and it’s likely that more substantial discussion and work has been done at IIW than any other conference!
|
||||
* [Collection] [WebOfTrustInfo/self-sovereign-id/](https://github.com/WebOfTrustInfo/self-sovereign-identity) 2022-12-07 Rebooting Web of Trust
|
||||
> Articles and documents associated with designing and implementing identity technology using self-sovereign identity principles
|
||||
* [Course] [Getting Started with Self-Sovereign Identity](https://www.edx.org/course/getting-started-with-self-sovereign-identity) 2022-10-05 Kaliya & Lucy via Linux Foundation and EdX
|
||||
> Gain a solid foundation on self-sovereign identity (SSI) with a 360 degree overview of its evolutionary journey, key concepts, standards, technological building blocks, use cases, real-world examples and implementation considerations.
|
||||
* [Directory] [The open SSI / DID Directory](https://ssi-did-directory.gitbook.io/open-directory-for-all/) 2022-09-24 Open DID \ SSI Directory
|
||||
> Important: This directory is here for all of us to learn. You do not have to be technical to contribute, but we expect you to do your research before you contribute. We are blockchain agnostic.
|
||||
* [Curated List] [peacekeeper/blockchain-identity](https://github.com/peacekeeper/blockchain-identity) 2021-11-23 Markus Sabadello
|
||||
* [Book] [Self-Sovereign Identity : Decentralized digital identity and verifiable credentials](https://www.manning.com/books/self-sovereign-identity#toc) 2021-05 Manning
|
||||
> It combines a clear, jargon-free introduction to this blockchain-inspired paradigm shift with interesting essays written by its leading practitioners. Whether for property transfer, ebanking, frictionless travel, or personalized services, the SSI model for digital trust will reshape our collective future.
|
||||
* [Wiki] [wiki.idcommons.net](http://wiki.idcommons.net/Main_Page) 2014-08-17 IIW IDCommons
|
||||
> We are a community of groups working on addressing the social, legal and technical issues that arise with the emerging, identity, data and social layer of the internet.
|
||||
|
||||
## Blogs
|
||||
|
||||
* [Phil Windley - Tags: identity](http://www.windley.com/tags/identity.shtml) 2023-06-26 [[Videos](https://vimeo.com/windley/videos)]
|
||||
> Phil Windley is a Senior Software Development Manager at AWS Identity. He is also the co-founder and organizer of the [Internet Identity Workshop](http://internetidentityworkshop.com/). [...] He was the Founding Chair of the Sovrin Foundation serving from 2016 to 2020, writes the popular Technometria blog, and is the author of the books [Learning Digital Identity](https://www.oreilly.com/library/view/learning-digital-identity/9781098117689/) (O'Reilly, Media 2023), [The Live Web](http://www.amazon.com/exec/obidos/ASIN/1133686680/windleyofente-20) (Course Technology, 2011), and [Digital Identity](http://www.amazon.com/exec/obidos/ASIN/0596008783/windleyofente-20) (O'Reilly Media, 2005). Phil has been a computer science professor at BYU and the University of Idaho, founder and CTO of several internet technology companies, and served as CIO for the State of Utah.
|
||||
* [Identity Woman](https://identitywoman.net/) 2023-06-13
|
||||
> Kaliya Young (formerly Hamlin) is an expert in self-sovereign identity and identity on the blockchain. She is the co-author of a Comprehensive guide to Self-Sovereign Identity and is widely known as Identity Woman (its also the name of her blog and her twitter handle). She is committed her life to the development of an open standards based layer of the internet that empowers people.
|
||||
* [Identity Woman in Business](https://medium.com/@identitywoman-in-business) 2023-05-31
|
||||
> We provide consulting and advisory services to organizations across the world to help them succeed in adopting, developing and investing in Decentralized ID.
|
||||
* [Identity Blog](https://identityblog.com) 2020-08-24 Kim Cameron
|
||||
> Many readers will already know that I retired from Microsoft after twenty years working as Chief Architect of Identity and other related roles. I had a great time there, and Microsoft adopted the Laws of Identity in 2005 at a time when most tech companies were still under dark influence of “Privacy is Dead”, building systems destined to crash at endless cost into a privacy-enabled future.
|
||||
|
||||
## Glossaries
|
||||
|
||||
* [Aries RFC 0006: SSI Notation](https://github.com/hyperledger/aries-rfcs/blob/main/concepts/0006-ssi-notation/README.md) 2019-06-20 Daniel Hardman Hyperledger Foundation
|
||||
> This RFC describes a simple, standard notation for various concepts related to decentralized and self-sovereign identity (SSI).
|
||||
* [IDCommongs - Lexicon](http://wiki.idcommons.org/Lexicon) 2014-08-18 IDCommons
|
||||
* [Identipedia](http://wiki.idcommons.org/Identipedia) 2008-01-22 IDCommons
|
||||
* [Systemic Elements](http://wiki.idcommons.org/Systemic_Elements) 2008-01-22 IDCommons
|
||||
|
||||
## Podcasts
|
||||
* [RadicalxChange (RxC) is a global movement for next-generation political economies.](https://radicalxchange-s.simplecast.com/) RxC Glen Weyl
|
||||
> Digital networks have centralized power over identities and information, creating problems for both markets and democracy. Does the solution require more shared agency over data? What might that look like? This panel discussion is structured around thought experiments to find solutions to this issue.
|
||||
* [The SSI Orbit Podcast](https://podcasts.apple.com/ca/podcast/ssi-orbit-podcast-self-sovereign-identity-decentralized/id1552622325) Northern Block Mathieu Glaude
|
||||
* [Let’s Talk About Digital Identity (LTADI)](https://www.ubisecure.com/lets-talk-about-digital-identity-podcast/) Ubisecure
|
||||
* [MyData Podcast](https://mydata.org/podcast/)
|
||||
* [Next Level Supply Chain Podcast with GS1](https://next-level-supply-chain-with-gs1us.podcastpage.io/)
|
||||
* [The Week in Identity](https://podcasters.spotify.com/pod/show/the-cyber-hut/) The CyberHut
|
||||
* [Digital Identity and Self Sovereignty](https://www.traceyfollows.com/tag/podcast/) Tracey Follows
|
||||
* [ID Talk](https://findbiometrics.com/topics/id-talk-podcast/) FindBiometrics
|
||||
|
||||
### Archive
|
||||
* [Identity, Unlocked](http://identityunlocked.auth0.com/) Auth0
|
||||
* [Identity Masters Podcast](https://open.spotify.com/show/0NmFDoGu9zq3r1nmgjwkhQ) Authenteq
|
||||
* [Definitely Identity](https://podcasts.apple.com/ca/podcast/definitely-identity/id1496565155) Tim Bouma
|
||||
* [The Digital Identity Transformation](https://idramp.com/the-digital-identity-transformation-podcast/) IDRamp
|
||||
* [Federal Blockchain News](https://www.spreaker.com/show/federal-blockchain-news) - (covers work with DHS and other govt agencies)
|
||||
* [Identity North Podcast](https://podcasts.apple.com/ca/podcast/identity-north-podcast/id1450122415) Identity North
|
||||
* [Privacy, Surveillance and Anonymity](https://open.spotify.com/show/0lkmZrdHMIJrkIEqT13SJQ) Kaliya 'Identity Woman' Young and Seth Goldstein
|
||||
|
||||
### Posts
|
||||
|
||||
* [My podcasts of choice](https://blogs.harvard.edu/doc/2021/05/04/podcasts/) 2021-05-04 Doc Searls
|
||||
* [Listening to identity podcasts is our 2021 new year’s resolution](https://www.ubisecure.com/education/why-listen-to-identity-podcasts/)
|
||||
> A gem we must have missed last month from Ubisecure, lists the identity podcasts that should be on our list.
|
||||
> - [Let’s Talk About Digital Identity (LTADI)](https://www.ubisecure.com/lets-talk-about-digital-identity-podcast/) – Ubisecure
|
||||
> - [Definitely Identity](https://podcasts.apple.com/ca/podcast/definitely-identity/id1496565155) – Tim Bouma
|
||||
> - [ID Talk](https://findbiometrics.com/topics/id-talk-podcast/) – FindBiometrics and, as you’d expect, focused on the biometrics space
|
||||
> - [State of Identity](https://oneworldidentity.com/podcast-main/) – OWI
|
||||
@ -17,6 +17,8 @@
|
||||
|
||||
* [Drilling Down on what Open Source is](https://medium.com/decentralized-identity/drilling-down-open-source-f50d1a4f2a76) DIF
|
||||
> The ostensibly binary distinction between “open” and “closed” software gets bandied about in many contexts, often in a dangerously simplified form, as though there were only two, mutually-exclusive options.
|
||||
* [Crossfunctionality](https://docs.centre.io/blog/crossfunctionationality) 2022-08-13 Centre
|
||||
> I have developed a pet peeve for "technosolutionism": the notion that a sufficiently innovative technology can solve a social problem, or a business problem, without complex and nuanced changes to social and business practice.
|
||||
* [Three Scenarios for Rolling Back Surveillance Capitalism](https://reb00ted.org/tech/20201009-three-scenarios-rolling-back-surveillance-captialism/) by Johannes Ernst
|
||||
> Scenario 1: Regulation Bites. Scenario 2: A Global Disinvestment Campaign Leads to a Vibrant Good Technology Market. Scenario 3: Frustrated Users and Open-Source Developers Start Cooperating for Mutual Benefit
|
||||
- [Drilling down: Open Source](https://medium.com/decentralized-identity/drilling-down-open-source-f50d1a4f2a76) - A crash-course in the complex world of variously-open software licensing
|
||||
|
||||
@ -1,38 +0,0 @@
|
||||
---
|
||||
published: false
|
||||
---
|
||||
|
||||
# Explainer
|
||||
|
||||
## Frequently Asked Questions
|
||||
|
||||
* [Answering Questions about Self-Sovereign Identity](https://www.windley.com/archives/2019/07/answering_questions_about_self-sovereign_identity.shtml) 2019-07 Phil Windley
|
||||
> Identity professionals continue to have questions about self-sovereign identity (SSI). In this post, I answer a few questions that Susan Morrow raised about the commercial viability, security, privacy, and desired user experience of SSI.
|
||||
* [19 FAQs on Verifiable Credentials and Self-Sovereign Identity](https://academy.affinidi.com/faqs-on-verifiable-credentials-and-self-sovereign-identity-3c3a505878bc) 2021-05-31 Affinidi
|
||||
> This article has some FAQs on the basics of Verifiable Credentials (VCs) and Self-Sovereign Identity (SSI).
|
||||
|
||||
## Myth
|
||||
|
||||
* [Myths about SSI](http://web.archive.org/web/20230209024203/https://jolocom.io/blog/myths-about-ssi/) 2022-05-25 Jolocom
|
||||
> The idea that as a user of SSI I have complete sovereignty over my digital identity is often misunderstood. At its core, SSI is about my digital identity being under my own control, so I can decide to whom I show my data, when, and for what.
|
||||
* [myths and facts. Is Self-Sovereign Identity Dangerous?](http://web.archive.org/web/20230209034007/https://jolocom.io/blog/mythen-und-fakten-ist-self-sovereign-identity-gefahrlich/) 2022-05-05 Jolocom (in german)
|
||||
> we examine more closely whether self-sovereign identity can increase or reduce risks for data misuse in certain cases.
|
||||
* [For traditional identity models, the biggest misconception is “strong passwords”](https://idramp.com/for-traditional-identity-models-the-biggest-misconception-is-strong-passwords/) 2022-07-20 IDRamp
|
||||
> One way to avoid password-related problems is to use decentralized identity management. This method is relatively new, so the best way to gain knowledge about it – contact the experts. For this reason, we are speaking with Mike Vesey, CEO of [IdRamp](https://idramp.com/).
|
||||
* [7 Myths of Self Sovereign Identity](https://medium.com/evernym/7-myths-of-self-sovereign-identity-67aea7416b1) 2018-10-31 Evernym
|
||||
> - Self-sovereign means self-attested.
|
||||
> - SSI attempts to reduce government’s power over an identity owner.
|
||||
> - SSI creates a national or “universal ID” credential.
|
||||
> - SSI gives absolute control over identity.
|
||||
> - There’s a “main” issuer of credentials.
|
||||
> - There’s a built-in method of authenticating.
|
||||
> - User-centric identity is the same as SSI.
|
||||
|
||||
## Big Picture
|
||||
|
||||
* [Crossfunctionality](https://docs.centre.io/blog/crossfunctionationality) 2022-08-13 Centre
|
||||
> I have developed a pet peeve for "technosolutionism": the notion that a sufficiently innovative technology can solve a social problem, or a business problem, without complex and nuanced changes to social and business practice.
|
||||
* [Unwrapping the Decentralised Identity Landscape](https://www.affinidi.com/post/unwrapping-the-decentralised-identity-landscape) 2022-07-08 Affinidi
|
||||
> Decentralised identity, an emerging trust framework for digital identity, strives to give data ownership and control back to the user. This framework empowers individuals to own his or her data, decide where to store it, and choose to share some or all of it with others. Often, this decentralised identity is used to create verifiable and shareable data for securely accessing products and services.
|
||||
* [Understanding Online Identity](https://educatedguesswork.org/posts/understanding-identity/) 2022-06-02 EducatedGuessWork (broad contextualization)
|
||||
> As noted above, the ergonomics of having to make an account on every new system are fairly bad: it requires the user to have a large number of passwords, which is more opportunities to use a bad password or to lose your password and have to recover. There are some opportunities for improvement around the margin (e.g., WebAuthn instead of passwords for authentication), better form fill-in so users don't have to type their name over and over, etc, but at the end of the day, there's only so much you can do.
|
||||
@ -1,9 +1,17 @@
|
||||
---
|
||||
title: "Governance: Trust Frameworks, Trust Registries, and Machine Readable Governance in Self Sovereign Identity"
|
||||
description:
|
||||
excerpt: >
|
||||
|
||||
layout: single
|
||||
categories: ["Development"]
|
||||
tags: ["Governance","Trust Frameworks","Trust Registries","Machine Readable Governance"]
|
||||
permalink: /development/governance-trust-frameworks-registries/
|
||||
canonical_url: "https://decentralzed-id.com/development/governance-trust-frameworks-registries/"
|
||||
published: false
|
||||
last_modified_at: 2023-07-01
|
||||
---
|
||||
|
||||
# Governance
|
||||
|
||||
* [https://disco.coop/](https://disco.coop/)
|
||||
|
||||
* [https://en.wikipedia.org/wiki/Rochdale_Principles](https://en.wikipedia.org/wiki/Rochdale_Principles)
|
||||
@ -43,3 +51,95 @@ Working through this now: more of a playbook [https://elements.disco.coop/](http
|
||||
<iframe src="//www.slideshare.net/slideshow/embed_code/key/49oAhEWXzJXXi1" width="595" height="485" frameborder="0" marginwidth="0" marginheight="0" scrolling="no" style="border:1px solid #CCC; border-width:1px; margin-bottom:5px; max-width: 100%;" allowfullscreen> </iframe>
|
||||
|
||||
[Decentralized governance for SSI and Blockchains with Lawrence Lundy-Bryan](https://www.slideshare.net/SSIMeetup/decentralized-governance-for-ssi-and-blockchains-with-lawrence-lundybryan)
|
||||
|
||||
## Contents
|
||||
|
||||
* 800-63-3
|
||||
|
||||
* DIACC
|
||||
|
||||
## Links
|
||||
|
||||
* [Digital Identity and Attributes Trust Framework](https://stateofidentity.libsyn.com/digital-identity-and-attributes-trust-framework) State of Identity
|
||||
> Do you trust technology and government to protect your data? On this week's State of Identity podcast, host, Cameron D'Ambrosi is joined by Gareth Narinesingh, Head of Digital Identity at HooYu to discuss the bridge between payments and identity wallets, the UK's next big push in adopting shared identity standards, and the foundation of decentralized identity verification across Web3 applications and the metaverse.
|
||||
|
||||
* [The Ukrainian War, PKI, and Censorship](https://www.windley.com/archives/2022/03/the_ukrainian_war_pki_and_censorship.shtml) Phil Windley
|
||||
> PKI has created a global trust framework for the web. But the war in Ukraine has shone a light on its weaknesses. Hierarchies are not good architectures for building robust, trustworthy, and stable digital systems.
|
||||
|
||||
* [Digital Caribou looks at the future trends impacting Digital Identity](https://medium.com/caribou-digital/diagnostic-trends-shaping-the-future-of-digital-identification-181724c40068) Caribou Digital
|
||||
> 1. The state of the art in digital identification are trust frameworks that accommodate diverse technologies, systems and stakeholders\n > 2. Risks remain even within the most rigorous trust framework:\n > 3. Achieving inclusion requires addressing both technical and political dimensions\n > 4. Trust frameworks are complicated so getting governance right requires an ecosystems approach\n > 5. Building the future of digital identification means reckoning with an analogue past
|
||||
|
||||
* [Trust Frameworks](https://medium.com/mattr-global/learn-concepts-trust-frameworks-ad96a4427991) Mattr Global
|
||||
> Trust frameworks are a foundational component of the web of trust. A trust framework is a common set of best practice standards-based rules that ensure minimum requirements are met for security, privacy, identification management and interoperability through accreditation and governance. These operating rules provide a common framework for ecosystem participants, increasing trust between them.
|
||||
|
||||
* [The trust infrastructure of self-sovereign identity ecosystems](https://ssi-ambassador.medium.com/the-trust-infrastructure-of-self-sovereign-identity-ecosystems-551f46ed9e2c) SSI Ambassador
|
||||
> The trust infrastructure is concerned with the question of how and why the presented information can be trusted. It defines the rules for all stakeholders and enables legally binding relationships with the combination of governance frameworks, which are built on top of trust frameworks.\n > \n > includes a section on the core components of identity architecture that includes a graphic [based on a post by Phil Windley](https://www.windley.com/archives/2020/09/the_architecture_of_identity_systems.shtml)
|
||||
|
||||
* [Battle of the Trust Frameworks with Tim Bouma & Darrell O’Donnell](https://northernblock.io/battle-of-the-trust-frameworks-with-tim-bouma-darrell-odonnell) Northern Block
|
||||
> 1. Levels of Assurance (LOA): an introduction to LOAs as they relate to Digital Identity and why they’re an important part of the recipe in achieving digital trust. Tim and Darrell give us some practical examples of LOAs.
|
||||
> 2. The Concept of Trust: how do we define trust at a high-level and how do we differentiate between technical and human trust? How can we build trust with credential issuers but also with credential holders?
|
||||
> 3. The World of Trust Frameworks: what are trust frameworks and what are different types of frameworks being deployed in both the public and private sectors? How are organizations trying to monetize trust frameworks? What’s going right, and what’s going wrong with the way trust frameworks are being implemented?
|
||||
> 4. The Importance of Open Source for Trust Creation: why is open source important for achieving digital sovereignty? Is open source the only way to improve transparency, flexibility and accountability?
|
||||
|
||||
* [Good Health Pass Ecosystem Trust Architecture: DIDs and X.509 Trust Registries with Ecosystem Governance Frameworks](https://iiw.idcommons.net/23F/_Good_Health_Pass_Ecosystem_Trust_Architecture:_DIDs_and_X.509_Trust_Registries_with_Ecosystem_Governance_Frameworks) Drummond Reed, Scott Perry, Darrell O’Donnell IIW
|
||||
> Governance, Trust Registry, Ecosystem, Transitive Trust, Architecture
|
||||
- [GHP Ecosystem Trust Architecture PDF](https://drive.google.com/file/d/1Hgh5JvrM7aUCmg5q6KIXzvpVIcgfhTjr/view?usp=sharing)
|
||||
- [Good Health Pass Collaborative Principles Paper](https://www.goodhealthpass.org/wp-content/uploads/2021/02/Good-Health-Pass-Collaborative-Principles-Paper.pdf)
|
||||
- [GHPC Interoperability Blueprint Outline v2](https://www.goodhealthpass.org/wp-content/uploads/2021/03/GHPC-Interoperability-Blueprint-Outline-v2.pdf)
|
||||
|
||||
|
||||
* [Towards a Better Digital Identity Trust Framework in Aotearoa](https://digitalidentity.nz/2022/09/21/towards-a-better-digital-identity-trust-framework-in-aotearoa/) Digital Identity NZ
|
||||
> It’s a great pleasure to share with you DINZ Reflections Report, a seminal piece of work that DINZ’s Digital Identity Trust Framework working group has developed over several months.
|
||||
|
||||
* [Trust Frameworks? Standards Matter](https://medium.com/@trbouma/trust-frameworks-standards-matter-47c946992f44) Tim Bouma
|
||||
> He points at the NIST documents about it [Developing Trust Frameworks to Support Identity Federations](https://nvlpubs.nist.gov/nistpubs/ir/2018/NIST.IR.8149.pdf) published in 2018. He also points at the Canadian government’s definition of standards.\n“a document that provides a set of agreed-upon rules, guidelines or characteristics for activities or their results. Standards establish accepted practices, technical requirements, and terminologies for diverse fields.” He goes on to highlight a lot of the work being done in Canada and where it all sits relative to being a standard - “In closing, there are lots of trust frameworks being developed today. But to be truly trusted, a trust framework needs to either apply existing standards or become a standard itself.”
|
||||
|
||||
* [Pan-Canadian Trust Framework (PCTF) – Overview](https://northernblock.io/pan-canadian-trust-framework/) Northern Block
|
||||
> Right now, we are alpha testing the framework with different kinds of actors, both public and private, and with assessors. Through this process, we’re going to learn what may need to change, and what may not need to change. We’re going to get real knowledge there. I will say that what we’re seeing already, is that DIACC and our priorities are really driven by members.
|
||||
|
||||
* [Trinsic Basics: What Is a Trust Registry?](https://trinsic.id/trinsic-basics-what-is-a-trust-registry/) Trinsic
|
||||
> Trust registries also need to be interoperable. The [Trust Over IP Foundation](https://www.trustoverip.org/) has a [specification](https://github.com/trustoverip/tswg-trust-registry-tf) for an interoperable trust registry, and ours is the first implementation of this spec. Because of this, Trinsic’s Trust Registry Service is architected so that one ecosystem could reference or incorporate a trust registry from a separate ecosystem if needed.
|
||||
|
||||
## Trust Registries
|
||||
|
||||
* [Managing Trust and Reputation via Trust Registries](https://www.continuumloop.com/managing-trust-and-reputation-via-trust-registries/) Continuum Loop
|
||||
|
||||
The concept behind a Trust Registry is that a Wallet needs to know which decentralized identifiers (DIDs) to “trust” as a source of truth. At many levels, this “trust” translates to “authority” – knowing that somebody, centralized or decentralized, is responsible for maintaining a list of trusted DIDs.
|
||||
|
||||
* [OIX White Paper: Trust Frameworks for Identity Systems](https://www.oixnet.org/news-whitepaper/) OIX
|
||||
|
||||
* [Bottom-up Trust Registry in Self Sovereign Identity](https://arxiv.org/abs/2208.04624v1) Kai Jun Eer, Jesus Diaz, Markulf Kohlweiss Arxiv
|
||||
> we propose a trust registry design that handles the aspect of human trust in self sovereign identity. We also introduce an incentivisation mechanism for the trust registry in order to motivate each stakeholder to participate actively and honestly.
|
||||
* [A novel approach to establish trust in verifiable credential issuers in Self-sovereign identity ecosystems using TRAIN](https://dl.gi.de/handle/20.500.12116/38702) 2022-07-07 Isaac Johnson Jeyakumar, David Chadwick; Michael Kubach Open Identity Summit
|
||||
> This paper illustrates how TRAIN (Trust mAnagement INfrastructure), an approach based on established components like ETSI trust lists and the Domain Name System (DNS), can be used as a trust registry component to provide a holistic approach for trust management in SSI ecosystems. TRAIN facilitates individual trust decisions through the discovery of trust lists in SSI ecosystems, along with published credential schemas, so that verifiers can perform informed trust decisions about issued credentials.
|
||||
* [Trust Registries in the Real World](https://www.continuumloop.com/trust-registries-in-the-real-world/) Continuum Loop
|
||||
> Trust Registries allow us to know that the various shared credentials (e.g. proof of insurance) are accurate. A Homeowner can ask their Digital Wallet to verify an insurance Credential that the Contractor is honest.
|
||||
|
||||
* [Trust Registries Tweetstorm](https://www.continuumloop.com/trust-registries-tweetstorm/) 2022-09-14 Continuum Loop
|
||||
> We want to start a conversation on Trust Registries and get people thinking about how Trust Registries will help answer the hard questions an ecosystem needs to create a whole experience [[tweetstorm](https://threadreaderapp.com/thread/1569093372920614914.html)]
|
||||
* [Podcast] [Are Trust Registries Vital to the Success of Decentralized Identity?](https://northernblock.io/are-trust-registries-vital-to-the-success-of-decentralized-identity-with-darrell-odonnell/) 2022-09-30 Darrell O’Donnell Northern Block
|
||||
> - What are the differences between Verifiable Data Registries and Trust Registries?
|
||||
> - How can Trust Registries help establish the Authenticity of Data?
|
||||
> - Does placing too much Governance at the Verifiable Data Registry layer cause scaling issues?
|
||||
> - Why DNS can become an elegant Root of Trust solution to validate the authenticity of Credential Issuers.
|
||||
> - Who in the Trust Triangle benefits the most from Trust Registries
|
||||
* [Solving Governance in SSI Ecosystems with Trust Registries.](https://www.youtube.com/watch?v=5zZKIwesSl8) 2022-10-04 Trust over IP Foundation
|
||||
> Learn the what and the why behind trust registries. In addition to discussing how trust registries solve governance in verifiable credential ecosystems, Tomislav demos the very first implementation of ToIP’s trust registry specification.
|
||||
* [Trust Registries Webinar](https://www.continuumloop.com/trust-registries-webinar/) 2021-09-21 Continuum Loop
|
||||
> - “I don’t trust organizations and corporations” – where we point out the “decentralize the world” approach goes to far.
|
||||
> - Phoning home – (hint: no it doesn’t need to phone home)
|
||||
> - Where are Holders Authorized? (hint: [Knowing if you can trust Bubba’s Wallet](https://www.continuumloop.com/bubbas-wallet/) may be more important…)
|
||||
> - Canadian Digitial Identities are emerging – can startups leverage this?
|
||||
> - Explain the Role of Government in ecosystems.
|
||||
> - “Can a third party discover who I trust from a trust registry?”
|
||||
> - How will interoperability work between trust registries?
|
||||
* [Decentralized Ecosystem Governance: Better, More Effective, and More Robust than Trust Registries](https://indicio.tech/decentralized-ecosystem-governance-better-more-effective-and-more-robust-than-trust-registries/) 2022-09-12 Indicio
|
||||
> Decentralized Ecosystem Governance makes verifying data an easy-to-play game of red light/green light. And, importantly, it decentralizes governance to the appropriate authorities.
|
||||
* [Trust Registry or Machine-Readable Governance?](https://indicio.tech/trust-registry-or-machine-readable-governance/) 2021-09-28 Indicio
|
||||
> Machine-readable governance is composed of elements that help to establish trust and enable interoperability: trusted participants, schemas (templates for structuring information in a credential), and rules and flows for presenting credentials and verifying them. Machine-readable governance can be hierarchical. Once a governance system is published, other organizations can adopt and then amend or extend the provided system.
|
||||
|
||||
* [Trust Frameworks and SSI: An Interview with CULedger on the Credit Union MyCUID Trust Framework](http://ssimeetup.org/trust-frameworks-ssi-interview-culedger-credit-union-mycuid-trust-framework-drummond-reed-webinar-9/) [Slideshare](https://www.slideshare.net/SSIMeetup/trust-frameworks-and-ssi-an-interview-with-culedger-on-the-credit-union-mycuid-trust-framework)
|
||||
> In this webinar, Evernym Chief Trust Officer Drummond Reed, chair of the Sovrin Foundation Trust Framework Working Group, will explain what a trust framework is and why they are are essential to SSI. Then he will interview executives of CULedger, the credit union blockchain consortia, about the MyCUID Trust Framework—the first global trust framework for proving membership in a credit union.
|
||||
* [Is the Self-Sovereign digital identity the future digital business registry?](https://blogs.worldbank.org/psd/self-sovereign-digital-identity-future-digital-business-registry) 2021-12-17 GORAN VRANIC, ANDREJA MARUSIC; WorldBank
|
||||
> This rapid digitalization of the private sector exposed a challenge in the business registration paradigm. To use private digital platforms for e-Logistics or e-Commerce, SMEs have to register and confirm their identity with these platforms, despite already being identified in the government business registry.
|
||||
> 
|
||||
|
||||
@ -1,110 +0,0 @@
|
||||
---
|
||||
published: false
|
||||
---
|
||||
|
||||
# Trust Frameworks
|
||||
|
||||
## Contents
|
||||
|
||||
* 800-63-3
|
||||
|
||||
* DIACC
|
||||
|
||||
## Links
|
||||
|
||||
* [Digital Identity and Attributes Trust Framework](https://stateofidentity.libsyn.com/digital-identity-and-attributes-trust-framework) State of Identity
|
||||
> Do you trust technology and government to protect your data? On this week's State of Identity podcast, host, Cameron D'Ambrosi is joined by Gareth Narinesingh, Head of Digital Identity at HooYu to discuss the bridge between payments and identity wallets, the UK's next big push in adopting shared identity standards, and the foundation of decentralized identity verification across Web3 applications and the metaverse.
|
||||
|
||||
* [The Ukrainian War, PKI, and Censorship](https://www.windley.com/archives/2022/03/the_ukrainian_war_pki_and_censorship.shtml) Phil Windley
|
||||
> PKI has created a global trust framework for the web. But the war in Ukraine has shone a light on its weaknesses. Hierarchies are not good architectures for building robust, trustworthy, and stable digital systems.
|
||||
|
||||
* [Digital Caribou looks at the future trends impacting Digital Identity](https://medium.com/caribou-digital/diagnostic-trends-shaping-the-future-of-digital-identification-181724c40068) Caribou Digital
|
||||
> 1. The state of the art in digital identification are trust frameworks that accommodate diverse technologies, systems and stakeholders\n > 2. Risks remain even within the most rigorous trust framework:\n > 3. Achieving inclusion requires addressing both technical and political dimensions\n > 4. Trust frameworks are complicated so getting governance right requires an ecosystems approach\n > 5. Building the future of digital identification means reckoning with an analogue past
|
||||
|
||||
* [Trust Frameworks](https://medium.com/mattr-global/learn-concepts-trust-frameworks-ad96a4427991) Mattr Global
|
||||
> Trust frameworks are a foundational component of the web of trust. A trust framework is a common set of best practice standards-based rules that ensure minimum requirements are met for security, privacy, identification management and interoperability through accreditation and governance. These operating rules provide a common framework for ecosystem participants, increasing trust between them.
|
||||
|
||||
* [The trust infrastructure of self-sovereign identity ecosystems](https://ssi-ambassador.medium.com/the-trust-infrastructure-of-self-sovereign-identity-ecosystems-551f46ed9e2c) SSI Ambassador
|
||||
> The trust infrastructure is concerned with the question of how and why the presented information can be trusted. It defines the rules for all stakeholders and enables legally binding relationships with the combination of governance frameworks, which are built on top of trust frameworks.\n > \n > includes a section on the core components of identity architecture that includes a graphic [based on a post by Phil Windley](https://www.windley.com/archives/2020/09/the_architecture_of_identity_systems.shtml)
|
||||
|
||||
* [Battle of the Trust Frameworks with Tim Bouma & Darrell O’Donnell](https://northernblock.io/battle-of-the-trust-frameworks-with-tim-bouma-darrell-odonnell) Northern Block
|
||||
> 1. Levels of Assurance (LOA): an introduction to LOAs as they relate to Digital Identity and why they’re an important part of the recipe in achieving digital trust. Tim and Darrell give us some practical examples of LOAs.
|
||||
> 2. The Concept of Trust: how do we define trust at a high-level and how do we differentiate between technical and human trust? How can we build trust with credential issuers but also with credential holders?
|
||||
> 3. The World of Trust Frameworks: what are trust frameworks and what are different types of frameworks being deployed in both the public and private sectors? How are organizations trying to monetize trust frameworks? What’s going right, and what’s going wrong with the way trust frameworks are being implemented?
|
||||
> 4. The Importance of Open Source for Trust Creation: why is open source important for achieving digital sovereignty? Is open source the only way to improve transparency, flexibility and accountability?
|
||||
|
||||
* [Good Health Pass Ecosystem Trust Architecture: DIDs and X.509 Trust Registries with Ecosystem Governance Frameworks](https://iiw.idcommons.net/23F/_Good_Health_Pass_Ecosystem_Trust_Architecture:_DIDs_and_X.509_Trust_Registries_with_Ecosystem_Governance_Frameworks) Drummond Reed, Scott Perry, Darrell O’Donnell IIW
|
||||
> Governance, Trust Registry, Ecosystem, Transitive Trust, Architecture
|
||||
- [GHP Ecosystem Trust Architecture PDF](https://drive.google.com/file/d/1Hgh5JvrM7aUCmg5q6KIXzvpVIcgfhTjr/view?usp=sharing)
|
||||
- [Good Health Pass Collaborative Principles Paper](https://www.goodhealthpass.org/wp-content/uploads/2021/02/Good-Health-Pass-Collaborative-Principles-Paper.pdf)
|
||||
- [GHPC Interoperability Blueprint Outline v2](https://www.goodhealthpass.org/wp-content/uploads/2021/03/GHPC-Interoperability-Blueprint-Outline-v2.pdf)
|
||||
|
||||
|
||||
* [Towards a Better Digital Identity Trust Framework in Aotearoa](https://digitalidentity.nz/2022/09/21/towards-a-better-digital-identity-trust-framework-in-aotearoa/) Digital Identity NZ
|
||||
> It’s a great pleasure to share with you DINZ Reflections Report, a seminal piece of work that DINZ’s Digital Identity Trust Framework working group has developed over several months.
|
||||
|
||||
* [Trust Frameworks? Standards Matter](https://medium.com/@trbouma/trust-frameworks-standards-matter-47c946992f44) Tim Bouma
|
||||
> He points at the NIST documents about it [Developing Trust Frameworks to Support Identity Federations](https://nvlpubs.nist.gov/nistpubs/ir/2018/NIST.IR.8149.pdf) published in 2018. He also points at the Canadian government’s definition of standards.\n“a document that provides a set of agreed-upon rules, guidelines or characteristics for activities or their results. Standards establish accepted practices, technical requirements, and terminologies for diverse fields.” He goes on to highlight a lot of the work being done in Canada and where it all sits relative to being a standard - “In closing, there are lots of trust frameworks being developed today. But to be truly trusted, a trust framework needs to either apply existing standards or become a standard itself.”
|
||||
|
||||
* [Pan-Canadian Trust Framework (PCTF) – Overview](https://northernblock.io/pan-canadian-trust-framework/) Northern Block
|
||||
> Right now, we are alpha testing the framework with different kinds of actors, both public and private, and with assessors. Through this process, we’re going to learn what may need to change, and what may not need to change. We’re going to get real knowledge there. I will say that what we’re seeing already, is that DIACC and our priorities are really driven by members.
|
||||
|
||||
* [Trinsic Basics: What Is a Trust Registry?](https://trinsic.id/trinsic-basics-what-is-a-trust-registry/) Trinsic
|
||||
> Trust registries also need to be interoperable. The [Trust Over IP Foundation](https://www.trustoverip.org/) has a [specification](https://github.com/trustoverip/tswg-trust-registry-tf) for an interoperable trust registry, and ours is the first implementation of this spec. Because of this, Trinsic’s Trust Registry Service is architected so that one ecosystem could reference or incorporate a trust registry from a separate ecosystem if needed.
|
||||
|
||||
## Trust Registries
|
||||
|
||||
* [Managing Trust and Reputation via Trust Registries](https://www.continuumloop.com/managing-trust-and-reputation-via-trust-registries/) Continuum Loop
|
||||
|
||||
The concept behind a Trust Registry is that a Wallet needs to know which decentralized identifiers (DIDs) to “trust” as a source of truth. At many levels, this “trust” translates to “authority” – knowing that somebody, centralized or decentralized, is responsible for maintaining a list of trusted DIDs.
|
||||
|
||||
* [OIX White Paper: Trust Frameworks for Identity Systems](https://www.oixnet.org/news-whitepaper/) OIX
|
||||
|
||||
* [Bottom-up Trust Registry in Self Sovereign Identity](https://arxiv.org/abs/2208.04624v1) Kai Jun Eer, Jesus Diaz, Markulf Kohlweiss Arxiv
|
||||
> we propose a trust registry design that handles the aspect of human trust in self sovereign identity. We also introduce an incentivisation mechanism for the trust registry in order to motivate each stakeholder to participate actively and honestly.
|
||||
* [A novel approach to establish trust in verifiable credential issuers in Self-sovereign identity ecosystems using TRAIN](https://dl.gi.de/handle/20.500.12116/38702) 2022-07-07 Isaac Johnson Jeyakumar, David Chadwick; Michael Kubach Open Identity Summit
|
||||
> This paper illustrates how TRAIN (Trust mAnagement INfrastructure), an approach based on established components like ETSI trust lists and the Domain Name System (DNS), can be used as a trust registry component to provide a holistic approach for trust management in SSI ecosystems. TRAIN facilitates individual trust decisions through the discovery of trust lists in SSI ecosystems, along with published credential schemas, so that verifiers can perform informed trust decisions about issued credentials.
|
||||
* [Trust Registries in the Real World](https://www.continuumloop.com/trust-registries-in-the-real-world/) Continuum Loop
|
||||
> Trust Registries allow us to know that the various shared credentials (e.g. proof of insurance) are accurate. A Homeowner can ask their Digital Wallet to verify an insurance Credential that the Contractor is honest.
|
||||
|
||||
* [Trust Registries Tweetstorm](https://www.continuumloop.com/trust-registries-tweetstorm/) Continuum Loop
|
||||
> We want to start a conversation on Trust Registries and get people thinking about how Trust Registries will help answer the hard questions an ecosystem needs to create a whole experience [[tweetstorm](https://threadreaderapp.com/thread/1569093372920614914.html)]
|
||||
* [Podcast] [Are Trust Registries Vital to the Success of Decentralized Identity?](https://northernblock.io/are-trust-registries-vital-to-the-success-of-decentralized-identity-with-darrell-odonnell/) Northern Block, with Darrell O’Donnell
|
||||
> - What are the differences between Verifiable Data Registries and Trust Registries?
|
||||
> - How can Trust Registries help establish the Authenticity of Data?
|
||||
> - Does placing too much Governance at the Verifiable Data Registry layer cause scaling issues?
|
||||
> - Why DNS can become an elegant Root of Trust solution to validate the authenticity of Credential Issuers.
|
||||
> - Who in the Trust Triangle benefits the most from Trust Registries
|
||||
* [Solving Governance in SSI Ecosystems with Trust Registries.](https://www.youtube.com/watch?v=5zZKIwesSl8) Trust over IP Foundation
|
||||
> Learn the what and the why behind trust registries. In addition to discussing how trust registries solve governance in verifiable credential ecosystems, Tomislav demos the very first implementation of ToIP’s trust registry specification.
|
||||
* [Trust Registries Webinar](https://www.continuumloop.com/trust-registries-webinar/) Continuum Loop
|
||||
|
||||
Questions started at about [46:30] – though some questions came earlier. We covered:
|
||||
|
||||
- “I don’t trust organizations and corporations” – where we point out the “decentralize the world” approach goes to far.
|
||||
- Phoning home – (hint: no it doesn’t need to phone home)
|
||||
- Where are Holders Authorized? (hint: [Knowing if you can trust Bubba’s Wallet](https://www.continuumloop.com/bubbas-wallet/) may be more important…)
|
||||
- Canadian Digitial Identities are emerging – can startups leverage this?
|
||||
- Explain the Role of Government in ecosystems.
|
||||
- “Can a third party discover who I trust from a trust registry?”
|
||||
- How will interoperability work between trust registries?
|
||||
* [Decentralized Ecosystem Governance: Better, More Effective, and More Robust than Trust Registries](https://indicio.tech/decentralized-ecosystem-governance-better-more-effective-and-more-robust-than-trust-registries/) 2022-09-12 Indicio
|
||||
> Decentralized Ecosystem Governance makes verifying data an easy-to-play game of red light/green light. And, importantly, it decentralizes governance to the appropriate authorities.
|
||||
* [Trust Registry or Machine-Readable Governance?](https://indicio.tech/trust-registry-or-machine-readable-governance/) Indicio
|
||||
> Machine-readable governance is composed of elements that help to establish trust and enable interoperability: trusted participants, schemas (templates for structuring information in a credential), and rules and flows for presenting credentials and verifying them. Machine-readable governance can be hierarchical. Once a governance system is published, other organizations can adopt and then amend or extend the provided system.
|
||||
<iframe src="//www.slideshare.net/slideshow/embed_code/key/hwUlr34zkyfGvm" width="595" height="485" frameborder="0" marginwidth="0" marginheight="0" scrolling="no" style="border:1px solid #CCC; border-width:1px; margin-bottom:5px; max-width: 100%;" allowfullscreen> </iframe>
|
||||
|
||||
[Overview of the Proposed PanCanadian Trust Framework for SSI - Tim Bouma](https://www.slideshare.net/SSIMeetup/overview-of-the-proposed-pancanadian-trust-framework-for-ssi-tim-bouma)
|
||||
|
||||
|
||||
### CULedger and MyCUID
|
||||
|
||||
<iframe src="//www.slideshare.net/slideshow/embed_code/key/3ypv0M4BJA8pPs" width="595" height="485" frameborder="0" marginwidth="0" marginheight="0" scrolling="no" style="border:1px solid #CCC; border-width:1px; margin-bottom:5px; max-width: 100%;" allowfullscreen> </iframe>
|
||||
|
||||
[Trust Frameworks and SSI: An Interview with CULedger on the Credit Union MyCUID Trust Framework](https://www.slideshare.net/SSIMeetup/trust-frameworks-and-ssi-an-interview-with-culedger-on-the-credit-union-mycuid-trust-framework)
|
||||
|
||||
|
||||
|
||||
* [Is the Self-Sovereign digital identity the future digital business registry?](https://blogs.worldbank.org/psd/self-sovereign-digital-identity-future-digital-business-registry) 2021-12-17 GORAN VRANIC, ANDREJA MARUSIC; WorldBank
|
||||
> This rapid digitalization of the private sector exposed a challenge in the business registration paradigm. To use private digital platforms for e-Logistics or e-Commerce, SMEs have to register and confirm their identity with these platforms, despite already being identified in the government business registry.
|
||||
> 
|
||||
Loading…
x
Reference in New Issue
Block a user