mirror of
https://github.com/Decentralized-ID/decentralized-id.github.io.git
synced 2025-09-20 20:54:44 -04:00
topics category
This commit is contained in:
parent
5c0a89692b
commit
654be069ac
8 changed files with 255 additions and 417 deletions
|
|
@ -10,13 +10,11 @@ redirect_from:
|
|||
- /literature/self-sovereign-identity/
|
||||
- /self-sovereign-identity
|
||||
- /self-sovereign-identity/
|
||||
categories: ["Literature"]
|
||||
categories: ["Topics"]
|
||||
tags: ["Self Sovereign Identity","Laws of Identity","Literature","RWoT","IIW","Learning Machine","Sovrin Foundation","Evernym"]
|
||||
last_modified_at: 2023-06-22
|
||||
---
|
||||
|
||||
<center><img src="{{ site.baseurl }}/images/sovereign-id-wide.webp"/></center>
|
||||
|
||||
## About Self Sovereign Identity
|
||||
* [Video] [Exploring the Decentralized Web, Episode 4: Digital Identity](https://www.youtube.com/watch?v=jm8y56KMkIw) 2022-01-05 Filecoin Foundation
|
||||
> Episode 4 explores the relationship between authentication and authorization, the rise of single sign-on platforms, and the advantages of and use cases for self-sovereign identity. Guests include Brian Behlendorf, Rainey Reitman, Danny O'Brien, Sarah Friend, Wendy Hanamura, Andrew Hill, and Brad Kam.
|
||||
|
|
@ -100,6 +98,8 @@ last_modified_at: 2023-06-22
|
|||
> - [Part 4: Why every company is an identity company](https://medium.com/global-id/globalid-101-every-company-is-an-identity-company-a851beed999d) 2022-08-16
|
||||
* [Trusted Third Parties vs Self-Sovereign Identity](https://academy.affinidi.com/trusted-third-parties-vs-self-sovereign-identity-4e96de929b1b) 2021-12-30 Affinidi
|
||||
> All of us have [multiple identities](https://academy.affinidi.com/what-links-identity-and-vcs-together-across-applications-9523af3884a9) at any point. We are sons, daughters, brothers, sisters, parents, partners, friends, colleagues, and more to different people.
|
||||
* [Selective Disclosure: Share Just What You Want](https://academy.affinidi.com/selective-disclosure-share-what-you-want-8ae367655b7b) 2021-08-02 Affinidi
|
||||
> In the context of SSI, selective disclosure is best implemented through [verifiable credentials](https://academy.affinidi.com/what-are-verifiable-credentials-79f1846a7b9) where the user has separate credentials for each piece of information such as his/her date of birth, full name, vaccination details, address, passport number, etc.
|
||||
* [Self-Sovereign Identity: What You Can/Can’t Do With SSI?](https://academy.affinidi.com/self-sovereign-identity-what-you-can-cant-do-with-ssi-1284f7227b4e) 2021-06-24 Affinidi
|
||||
> it gives complete control and ownership of data to the individual entities as they can decide what data to share and with whom.
|
||||
>
|
||||
|
|
@ -138,7 +138,6 @@ The Models: Space Time • Presentation • Attribute • Relationship • Capab
|
|||
* [How Decentralized Identifiers Will Shape the Future of Identity](https://hackernoon.com/how-decentralized-identifiers-will-shape-the-future-of-identity-iam3w9g) 2020-11-09 HackerNoon
|
||||
> Hackers value personal information the most. 96% of hacking groups’ primary motive is intelligence gathering. Researchers at privacy website PrivacyAffairs.com found that you can obtain a person's full identity for the low price of $1,275.
|
||||
|
||||
|
||||
## Literature
|
||||
|
||||
* [WhitePaper] [Self Sovereign Identity](https://www.blockchainresearchinstitute.org/project/self-sovereign-identity) 2022-05-10 Phil Windley, Blockchain Research Institute
|
||||
|
|
|
|||
93
_posts/topics/2023-06-22-user-experience.md
Normal file
93
_posts/topics/2023-06-22-user-experience.md
Normal file
|
|
@ -0,0 +1,93 @@
|
|||
---
|
||||
title: User Experience and Self Sovereign Identity
|
||||
excerpt: >
|
||||
Lack of great user experiences is often raised as one of decentralized identity’s (and public blockchain’s) missing ingredients for ubiquitous adoption. However to arrive at usable experiences across the industry, we first need to reach consensus around basic user personas and mental models, then design and build interoperable system accordingly.
|
||||
description: the mere fact of building such a verifiable and traceable architecture does not automatically translate into understandable communications
|
||||
layout: single
|
||||
toc: true
|
||||
toc_sticky: true
|
||||
permalink: /topic/user-experience/
|
||||
canonical_url: 'https://decentralized-id.com/topic/user-experience/'
|
||||
redirect_from:
|
||||
- /literature/self-sovereign-identity/user-experience/
|
||||
- self-sovereign-identity/user-experience
|
||||
- self-sovereign-identity/user-experience/
|
||||
categories: ["Topics"]
|
||||
tags: ["User Experience"]
|
||||
last_modified_at: 2023-06-23
|
||||
published: true
|
||||
---
|
||||
|
||||
## General
|
||||
* [Identity and Consistent User Experience](https://www.windley.com/archives/2021/11/identity_and_consistent_user_experience.shtml) 2021-11 Phil Windley
|
||||
> There's a saying in security: "Don't roll your own crypto." I think we need a corollary in identity: "Don't roll your own interface." But how do we do that? And what should the interface be? One answer is to adopt the user experience people already understand from the physical world: connections and credentials.
|
||||
* [Fluid Multi-Pseudonymity](https://www.windley.com/archives/2021/09/fluid_multi-pseudonymity.shtml) 2021-09-07 Windley
|
||||
> Fluid multi-pseudonymity perfectly describes the way we live our lives and the reality that identity systems must realize if we are to live authentically in the digital sphere.‘
|
||||
* [Humanizing PoSSI- Human-centric structure of the Principles of SSI](https://iiw.idcommons.net/21M/_Humanizing_PoSSI-_Human-centric_structure_of_the_Principles_of_SSI) 2021-05-06 Line Kofoed
|
||||
> 1. [Line] Welcome and introductions; background information around how this topic is important to discuss
|
||||
> 2. Principles of SSI - [https://sovrin.org/principles-of-ssi/](https://sovrin.org/principles-of-ssi/)
|
||||
> 3. Sovrin Foundation is working on Sovrin Utility GF and the Sovrin Ecosystem GF
|
||||
> 4. Work on the SEGF led to reviewing how we define an ecosystem (see slide for definition) → identity ecosystem for identity services
|
||||
> 5. The approach to grouping the 12 principles are intended to enable better understanding as digital trust ecosystems grow
|
||||
> 6. Ecosystem of ecosystems will need a foundational set of values and principles and the PoSSI
|
||||
> 7. [Sterre] It is good to have the order the principles to help better understanding
|
||||
> 8. [Drummond] additional supplementary material to help laypersons understand the PoSSI better
|
||||
> 9. [Alex] is the original sequence/numbering sufficient and complete?
|
||||
> 10. [Chris] the grouping is more important for the SEGF
|
||||
> 11. [please join Sovrin meetings]
|
||||
* [Bringing User-Centricity to Decentralized Identity](https://www.youtube.com/watch?v=UnWsu1gCe9k) 2021-08-01 Nat Sakimura KuppingerCole
|
||||
> Raj Hegde sits with identity veteran, Nat Sakimura - Chairman of OpenID Foundation to understand how user-centric learnings from existing authentication protocols can be applied to future identity initiatives.
|
||||
* [How humans understand identity](https://medium.com/universal-identity/how-humans-understand-identity-367200ae9591) 2021-07-09 Universal Identity
|
||||
> Lack of great user experiences is often raised as one of decentralized identity’s (and public blockchain’s) missing ingredients for ubiquitous adoption. However to arrive at usable experiences across the industry, we first need to reach consensus around basic user personas and mental models, then design and build interoperable system accordingly.
|
||||
|
||||
## Relationships
|
||||
* [Are Transactional Relationships Enough?](https://www.windley.com/archives/2022/03/are_transactional_relationships_enough.shtml) 2022-03 Phil Windley
|
||||
> Our online relationships are almost all transactional. A purely transaction digital life can't feel as rich and satisfying as one based on interactional relationships. As more of our relationships are intermediated by technology, finding ways to support interactional relationships will allow us to live authentic digital lives.
|
||||
* [Backchannel: A relationship-based digital identity system](https://www.inkandswitch.com/backchannel/) 2021-09 Ink and Switch
|
||||
> Using Backchannel as a model example, we propose four design principles for trusted digital relationships. Then we used Backchannel to design and build three sample apps: chat, location sharing, and document preview. We also tested these designs with journalists, researchers, and designers. Based on this testing, we outline common user experience challenges and recommended solutions.
|
||||
* [Authentic Digital Relationships](https://www.windley.com/archives/2020/08/authentic_digital_relationships.shtml) 2020-08 Phil Windley
|
||||
> Self-sovereign identity (SSI) systems offers an alternative model that supports richer relationships. Rather than provisioning identifiers and accounts in an administrative system where the power imbalance assures that one party to the relationship can dictate the terms of the interaction, SSI is founded on peer relationships that are co-provisioned by the exchange of decentralized identifiers. This architecture implies that both parties will have tools that speak a common protocol.
|
||||
* [Relationships and Identity](https://www.windley.com/archives/2020/07/relationships_and_identity.shtml) 2020-07 Phil Windley
|
||||
> We build digital identity systems to create and manage relationships—not identities.
|
||||
|
||||
## Design
|
||||
* [More security does not have to mean less user-friendliness](https://background.tagesspiegel.de/cybersecurity/mehr-sicherheit-muss-nicht-weniger-nutzerfreundlichkeit-bedeuten) 2022-06-05 Martin Kuppinger, Tagesspiegel
|
||||
> The passwords that have been declared dead are far from dead. Nevertheless, the way in which users authenticate themselves is changing towards more security and convenience.
|
||||
* [How Might we Design Consent Experiences for Data Sharing?](https://www.youtube.com/watch?v=bGgV2Ffnczg) 2022-05-27 ToIP HXWG Arianna Rossi, Xengie Doan, Interdisciplinary Center for Security, Reliability and Trust (SnT) at the University of Luxembourg
|
||||
> The complex ecosystem where manifold transactions can be automatically enabled by smart contracts contributes, at least in principle, to establish greater transparency about data use towards the many parties involved. However, the mere fact of building such a verifiable and traceable architecture does not automatically translate into understandable communications, easily applicable instructions and smooth transactions for human beings.
|
||||
* [Tap and Prove](https://www.linkedin.com/pulse/tap-prove-stephen-wilson/) 2021-07-15 Stephen Wilson
|
||||
> We should be able to “tap and prove” any important fact and figures about ourselves – as easily as we tap and pay with a mobile phone at any one of 100s of millions of terminals globally.
|
||||
* [Disability-inclusive ID Systems](https://blogs.worldbank.org/voices/access-agency-and-empowerment-through-disability-inclusive-id-systems) 2020-12-09 World
|
||||
> Creating an inclusive ID system requires a comprehensive, whole-of-system approach to overcome barriers to ID enrollment and use for persons with disabilities.
|
||||
* [EPS for SSI (Self-Sovereign Identity)](https://medium.com/@kokumai/eps-for-ssi-self-sovereign-identity-8c742e2b1d02) 2020-08-15 Hitoshi Kokumai
|
||||
> you might be interested to hear that the core of EPS is designed to convert images to high-entropy codes, which work as very long passwords and also as the seeds of symmetric or asymmetric cryptographic keys.
|
||||
* [Falsehoods Programmers Believe About Names - With Examples](https://shinesolutions.com/2018/01/08/falsehoods-programmers-believe-about-names-with-examples/) 2018-01-08 Shine Solutions Group
|
||||
> In this post I’m going to list all 40 of Patrick’s original falsehoods, but give you an example (or two) drawn from my experiences working in this space. Ready? Let’s go!
|
||||
>
|
||||
> 1. People have exactly one canonical full name.
|
||||
> 2. People have exactly one full name which they go by.
|
||||
|
||||
## Trust
|
||||
* [An Introduction to Digital Trust](https://northernblock.io/verifiable-credentials/introduction-to-digital-trust/) 2021-09-06 Northern Block
|
||||
> what’s the purpose of SSI? It’s about enabling Digital Trust (which is quickly becoming an integral part of digital transformation for organizations).
|
||||
* [Will users and organizations have trust in keys roaming via the cloud?](https://www.kuppingercole.com/events/eic2022/blog/will-users-and-organizations-have-trust-in-keys-roaming-via-the-cloud) 2022-05-12 Kuppinger Cole EIC2022
|
||||
> the FIDO Alliance, a set of open, scalable, and interoperable specifications has been developed to replace passwords as a secure authentication method for online services. The alliance has also worked with companies such as [Microsoft](https://docs.microsoft.com/en-us/azure/active-directory/authentication/concept-authentication-passwordless), [Google](https://cloud.google.com/blog/products/identity-security/protect-gce-vms-with-managed-fido-security-keys), and [Apple](https://fidoalliance.org/expanded-support-for-fido-authentication-in-ios-and-macos/) to integrate and adopt FIDO standards across their operating systems.
|
||||
|
||||
## Consumer Research
|
||||
* [People Don’t Understand the Purpose of Privacy Policies and Terms of Service – New Research Published](https://me2ba.org/people-dont-understand-the-purpose-of-privacy-policies-and-terms-of-service-new-research-published/) Me2B Alliance ([Report](https://me2ba.org/spotlight-report-5-me2b-alliance-validation-testing-report-consumer-perception-of-legal-policies-in-digital-technology/)
|
||||
> - Consumers are aware that legal policies exist on connected technologies and that they should read them, but they continue to choose to largely ignore them.
|
||||
> - 55% of survey participants did not understand that a TOS/TOU agreement is a legal contract. This has significant implications because a key requirement for legally binding contracts is mutual assent, which means that both parties have a “meeting of the minds” and must understand they’re entering into a contract.
|
||||
> - None of the interview participants were aware of tools that explain or rate privacy policies and TOS/TOU documents, and half said that a score would not change their behavior.
|
||||
> - 66% of survey respondents believe that privacy policies protect the business, while 50% say they protect the consumer. It’s questionable that privacy policies protect either the individual or the business, as they are primarily legal notices, disclosures of how data is used by the technology and the companies behind it. Moreover, 39% of respondents erroneously thought that the privacy policy was a contract [between them and the company].
|
||||
|
||||
### Location Tracking
|
||||
* [Most People Feel Negatively About Location Tracking in Websites and Apps](https://me2ba.org/most-people-feel-negatively-about-location-tracking/) 2021-11-16 Me2Ba
|
||||
> The Spotlight Report, “[Consumer Sensitivity to Location Tracking by Websites and Mobile Apps](https://me2ba.org/spotlight-report-3-me2b-alliance-validation-research-consumer-sensitivity-to-location-tracking-by-websites-and-mobile-apps/)”, was developed to validate the Location Commitment scoring criteria in the [Me2B Alliance Validation Research: Consumer Sensitivity to Location Tracking by Websites and Mobile Apps](https://me2ba.org/spotlight-report-3-me2b-alliance-validation-research-consumer-sensitivity-to-location-tracking-by-websites-and-mobile-apps/)
|
||||
* [What is Respectful Use of Location Information? New Me2BA Reearch](https://me2ba.org/what-is-respectful-use-of-location-information-new-me2ba-research-published/) 2021-11-22 Me2B
|
||||
> As we’ve been performing independent product audits over the past year and a half, we received some push-back on our passing criteria related to the automatic translation of IP address to geographic location. Vendors felt that automatically calculating the user’s geographical location was, in fact, a benefit. However, in our specification, that behavior will receive a failing score. At an impasse, we decided to conduct some validation testing with Me-s.
|
||||
* [“Spotlight Report #3: Consumer Sensitivity to Location Tracking by Websites and Mobile Apps”](https://me2ba.org/spotlight-report-3-me2b-alliance-validation-research-consumer-sensitivity-to-location-tracking-by-websites-and-mobile-apps/) 2021-11-16 Me2B
|
||||
> This research quantifies and qualifies public opinion of location tracking in a variety of different contexts within web and mobile technology.
|
||||
* [Do Consumers Even Want Personalized Ads?](https://anonyome.com/2021/06/do-consumers-even-want-personalized-ads/) 2021-06 Anonyme
|
||||
> The [YouGov](https://www.globalwitness.org/en/blog/do-people-really-want-personalised-ads-online/) poll of consumers in France and Germany we mentioned earlier says it’s the [behind the scenes](https://mysudo.com/2021/02/beware-the-dark-patterns-trying-to-steal-your-data/) or back door nature of personalization that gives people the creeps.
|
||||
* [Only 5% Of US Consumers Want To Be Tracked For Ads](https://anonyome.com/2021/05/only-5-of-us-consumers-want-to-be-tracked-for-ads/) 2021-05 Anonyme
|
||||
> That means 95% of US consumers are saying ‘no way’ to cross-app tracking with Apple’s new [App Tracking Transparency](https://anonyome.com/2021/05/apples-new-att-and-why-facebook-is-hitting-back-hard/) (ATT) feature.
|
||||
58
_posts/topics/2023-06-23-architecture.md
Normal file
58
_posts/topics/2023-06-23-architecture.md
Normal file
|
|
@ -0,0 +1,58 @@
|
|||
---
|
||||
title: System Architecture and Self Sovereign Identity
|
||||
excerpt: >
|
||||
In chaotic systems such as those that the discipline of physics seeks to describe, there is also the concept of the “self-organizing principle,” which dictates a tendency for chaotic systems to organize themselves. While this might be a tendency in physics, organization usually needs a nudge in the right direction in the identity world.
|
||||
description: Authentication and authorization both fall under identity and access management (IAM) but serve different purposes.
|
||||
layout: single
|
||||
toc: false
|
||||
permalink: /topic/architecture/
|
||||
canonical_url: 'https://decentralized-id.com/topic/architecture/'
|
||||
categories: ["Topics"]
|
||||
tags: ["Architecture"]
|
||||
last_modified_at: 2023-06-23
|
||||
---
|
||||
|
||||
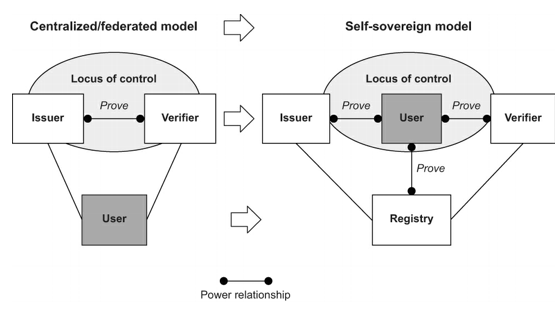
* [Centralized\Federated vs Self Sovereign](https://twitter.com/dominiumssi/status/1564188374529081345) 2022-08-29 dominiumssi
|
||||
> Anyone who wants to understand DID and Self Sovereign Identity should begin by understanding the graph below. We are shifting the power from the companies to the users. That's it in a nutshell.
|
||||
> 
|
||||
* [Good Welfare, Bad Platforms?: The Risks of Centralized Digital Identity Systems](https://points.datasociety.net/good-welfare-bad-platforms-d65b412d962e) 2022-02-02 OpenID
|
||||
> As S. Shakthi and I noted in a recent [research paper](https://journals.openedition.org/samaj/6279), digital identity systems are widely seen as datafiers by virtue of their core property of reducing the person to machine-readable data. A datafier is a system that performs the crucial operation of converting the physical into digital. A different, contrasting view is also emerging in research: digital identity systems are increasingly seen as platforms, i.e. “technological building blocks” on which different types of complements can be constructed.
|
||||
* [Leveraging the Identity Metasystem](https://www.windley.com/archives/2021/12/leveraging_the_identity_metasystem.shtml) 2021-12 Phil Windley
|
||||
> the [metasystem guarantees the fidelity of the credential exchange](https://www.windley.com/archives/2021/06/ssi_interaction_patterns.shtml). Credential fidelity comprises four important attributes. Credential exchange on the identity metasystem:
|
||||
>
|
||||
> 1. Reveals the identifier of the issuer
|
||||
> 2. Ensures the credential was issued to the party presenting it
|
||||
> 3. Ensures the credential has not been tampered with
|
||||
> 4. Reveals whether or not the credential has been revoked
|
||||
* [Token-Based Identity](https://www.windley.com/archives/2021/10/token-based_identity.shtml) 2021-10 Phil Windley
|
||||
> Token-based identity systems move us from talking about who, to thinking about what, so that people can operationalize their digital lives. Token-based identity systems support complex online interactions that are flexible, ad hoc, and cross-domain.
|
||||
* [Your User is Your API](https://www.evernym.com/blog/your-user-is-your-api/) 2021-05-17 Evernym
|
||||
> The customer becomes the integration point. The customer is the API. Rather than having one huge, expensive, and probably illegal data hub, every customer becomes a data hub in their own right. They provide the data needed, just-in-time, under their control.
|
||||
* [The Unbundling of Authentication vs Authorization - What You Need to Know](https://www.pingidentity.com/en/company/blog/posts/2021/authentication-vs-authorization.html) 2021-09-08 Ping Identity
|
||||
> Authentication and authorization are both processes that fall under the category of [identity and access management (IAM)](https://www.pingidentity.com/en/company/blog/posts/2017/what-is-identity-and-access-management-iam.html), but they serve different purposes.
|
||||
* [The Buzz Behind Zero Trust](https://stateofidentity.libsyn.com/zero-trust-architecture) 2021-10-21 State of Identity
|
||||
> The Zero Trust model is the belief that no one should be trusted from inside or outside your network, until their identity has been verified. Zero trust refers to the alignment of maturing identity practices, an established understanding of user behaviors, and the application of least-privilege access security policy decisions to trust boundOaries
|
||||
* [What Is Zero Trust?](https://www.pingidentity.com/en/company/blog/posts/2021/what-is-zero-trust.html) 2021 Ping
|
||||
> 1. The network is always assumed to be hostile.
|
||||
> 2. External and internal threats exist on the network at all times.
|
||||
> 3. Network locality is not sufficient for deciding trust in a network.
|
||||
> 4. Every device, user and network flow is authenticated and authorized.
|
||||
> 5. Policies must be dynamic and calculated from as many sources of data as possible.
|
||||
* [Compare and Contrast — Federated Identity vs Self-sovereign Identity](https://academy.affinidi.com/compare-and-contrast-federated-identity-vs-self-sovereign-identity-227a85cbab18) 2021-04-26 Affinidi
|
||||
> The next step was a federated form of identity where third parties issued digital identity credentials using which users could log into other websites or services. Typically, these were your Google and Facebook logins. In the process, these third parties that issued federated identities became the middlemen.
|
||||
* [The SSO Practitioner’s Introduction to Decentralized Identity](https://www.pingidentity.com/en/resources/blog/post/sso-practitioners-introduction-decentralized-identity.html) 2020-10-13
|
||||
*Written for IAM professionals familiar with federations.*
|
||||
> In most self-sovereign and decentralized identity systems the trust model is fundamentally unidirectional, where a verifier will trust the issuer, but the issuer may have no knowledge of the verifier.
|
||||
* [The Architecture of Identity Systems](https://www.windley.com/archives/2020/09/the_architecture_of_identity_systems.shtml) 2020-09 Phil Windley
|
||||
> We can broadly classify identity systems into one of three types based on their architectures and primary root of trust:
|
||||
> - Administrative
|
||||
> - Algorithmic
|
||||
> - Autonomic
|
||||
* [Never mind who I am, ask me about my credentials](https://www.linkedin.com/pulse/never-mind-who-i-am-ask-me-my-credentials-john-phillips/) 2020-02-09 John Phillips
|
||||
> Many (most) identity systems make a fundamental assumption that is built into their very architecture. This assumption creates three significant problems: privacy erosion; toxic data stores; and poor security.
|
||||
* [Decentralized Identity Trilemma](https://maciek.blog/p/dit) 2018-08-13 Maciek Laskus
|
||||
> 1. Self-sovereignty — anybody can create and control as many identities1 as they wish without 3rd party involvement.
|
||||
> 2. Privacy-preserving — one can acquire and utilize an identifier without revealing their ‘real name’ or other personality identifying information.
|
||||
> 3. Sybil-resistant — identity is subject to scarcity; i.e., creating more identifiers cannot be used to manipulate a system2.
|
||||
* [Self-Sovereign vs Administrative Identity](http://blogs.harvard.edu/vrm/2012/03/25/ssi/) 2012-03-25 Doc Searls
|
||||
> The problem I’m trying to surface here is that we need full respect for self-sovereign identities, and identifiers, before we can solve the problem of highly fractured and incompatible administrative identifiers — a problem that has only become worse with the growth of the Web, where by design we are always the submissive and dependent party: calves to administrative cows.
|
||||
81
_posts/topics/2023-06-23-ethics-rights-sovereignty.md
Normal file
81
_posts/topics/2023-06-23-ethics-rights-sovereignty.md
Normal file
|
|
@ -0,0 +1,81 @@
|
|||
---
|
||||
title: "Ethics, Human Rights, Sovereignty and Self Sovereign Identity"
|
||||
excerpt: >
|
||||
In a world that is becoming more digital, it is relevant to find some guidelines for organizations to design digital identity more ethically. A universal identity system on the internet is still missing and there are no clear standards for organizations to design digital identity.
|
||||
description: "concept of individual control over identity relevant private data"
|
||||
layout: single
|
||||
toc: true
|
||||
toc_sticky: true
|
||||
permalink: /topic/ethics-rights-sovereignty/
|
||||
canonical_url: 'https://decentralized-id.com/topic/ethics-rights-sovereignty/'
|
||||
categories: ["Topics"]
|
||||
tags: ["Ethics","Human Rights","Sovereignty"]
|
||||
last_modified_at: 2023-06-23
|
||||
---
|
||||
|
||||
## Ethics
|
||||
* [Pro-social behaviours](https://en.wikipedia.org/wiki/Prosocial_behavior) 2023-06-14 Wikipedia
|
||||
> those intended to benefit others, or society as a whole — for example, helping, sharing, donating, co-operating, and volunteering. Within a community, they’re the behaviours that make it an attractive space to belong to, and which encourage its growth and/or development. It’s a central part of the value cycles that underpin the Communities of Practice model.
|
||||
* [Radical generosity](https://provocations.darkmatterlabs.org/radical-generosity-8063d9edc3aa) 2022-08-31 Dark Matter
|
||||
> Could we establish an alternative market economy, one that is structured around a distinct set of principles centred on care, trust, generosity, the importance of collective intelligence and deep sets of relationships; what would fall away and what would remain in place?
|
||||
* [Measuring the Ethical Behavior of Technology](https://me2ba.org/measuring-the-ethical-behavior-of-technology/) 2021-08-12 Me2bAlliance
|
||||
> This session will share the results and learnings of the creation and development of an ethical “yardstick” for respectful technology, including its application to websites and mobile apps. The speakers will also explore learnings from everyday people in the validation research around the certification mark as well as share recommendations for tech makers.
|
||||
* [Me2B Alliance Safe & Respectful Technology Specification](https://me2ba.org/flash-guide-2-what-is-the-me2b-respectful-tech-specification/) 2021-07-21 Me2B
|
||||
> The specification, produced by the Me2B Alliance’s Respectful Tech Spec Working Group, is designed to provide a standard for measuring safe and ethical behavior in connected technology.
|
||||
* [literature] [Ethical Design of Digital Identity Environmental Implications from the Self-Sovereign Identity Movement](https://theses.ubn.ru.nl/items/5afb03ab-7a90-4303-909b-4934295859f8) 2021-06 Sanne Glastra
|
||||
> In a world that is becoming more digital, it is relevant to find some guidelines for organizations to design digital identity more ethically. A universal identity system on the internet is still missing and there are no clear standards for organizations to design digital identity. With this research, knowledge and insights have been obtained to advance organizations to design digital identity more ethically. A contribution has been made by proposing the conditions to enable improvements for a more ethical design.
|
||||
* [Sovereignty, privacy, and ethics in blockchain‑based identity management systems](https://link.springer.com/content/pdf/10.1007/s10676-020-09563-x.pdf) 2020-11-30 Georgy Ishmaev
|
||||
> It is argued that ‘self-sovereignty’ in this context can be understood as the concept of individual control over identity relevant private data, capacity to choose where such data is stored, and the ability to provide it to those who need to validate it.
|
||||
* [NO NEED FOR SUPERHUMANS!: A practical guide to ethics in socio-technical systems design](https://trustoverip.org/blog/2022/03/18/no-need-for-superhumans/) TOIP 2022-03-18
|
||||
> Of course we are not as Albert Camus once said, ‘wild beasts loosed upon this world’, all of us have a moral compass and a sense of what is right and wrong, no-one intends for their product or service to cause harm. Neither are we superhuman, able to always understand the perspectives of all stakeholders or foresee the consequences of every cool feature or elegant line of code, nor indeed can we forecast how our products and services will be used for good or ill. Lisa called on all of us to remember that “technology is not a product, but a system”, and gave us practical steps to help us tap into our innate moral compass and design for those systems with the human experience and human flourishing at its heart.
|
||||
- summary and video [on our Wiki](https://wiki.trustoverip.org/display/HOME/1.+Dear+Human%2C+The+Future+Needs+You.++Practical+Ethics+with+Digital+Sociologist%2C+Lisa+Talia-Moretti) or [YouTube](https://www.youtube.com/watch?v=Xmnnj82wpTM&t=20s
|
||||
- Lisa’s Ted Talk, [Technology is not a product, it’s system](https://www.ted.com/talks/lisa_talia_moretti_technology_is_not_a_product_it_s_a_system)
|
||||
- [HXWG Expert Series Summary](https://wiki.trustoverip.org/display/HOME/Expert+Series) including video of Lisa’s talk
|
||||
- [A SocioTechnical Process for Researchers, Designers and Creators](https://bit.ly/sociotechprocess)
|
||||
- The [responsible tech guide](https://atih.responsibletechguide.com/introduction) is full of useful links and insights
|
||||
- [Ethics for Designers also has practical tools](https://www.ethicsfordesigners.com/tools)
|
||||
* [FRIDA’S principles to guide data and technology](https://youngfeministfund.org/wp-content/uploads/2020/07/FRIDAS-TECH-AND-DATA-PRINCIPLES.pdf) 2020-07 Young Feminist Fund
|
||||
> The tech we use should be responsive to and responisble with the climate, environment crises of our time. Frida advocates for the use and creation of volence-free technologies putting first the care of our territories and bodies
|
||||
* [FRIDA Happiness Manifesto](https://youngfeministfund.org/wp-content/uploads/2019/06/Happiness-Manifestx-web.pdf) Young Feminist Fund
|
||||
* [We Should Embrace the Ethical Implementation of Digital Identity](https://www.continuumloop.com/embrace-the-ethical-implementation-of-digital-identity/) 2022-03-22 Continuum Loop
|
||||
> Maybe it’s because of the nature of my job in decentralized identity consulting, but lately, I’ve been seeing a lot of conspiracy theories on social media about Self-Sovereign Identity (SSI). People criticize the way it’s being implemented and warn about the negative consequences it will have. It’s almost as if people don’t realize that organizations are already monitoring and influencing us and that Google and social media algorithms have been instrumental in this.
|
||||
|
||||
## Sovereignty
|
||||
|
||||
* [The railroad of (no) choice](https://www.mydigitalfootprint.com/2021/07/the-railroad-of-no-choice.html) 2021-07 MyDigitalFootprint
|
||||
> - to force something to be officially approved or accepted without much discussion or thought.
|
||||
> - to force someone into doing something quickly, usually without enough information.
|
||||
* [A Deep-Dive on Digital Self-Determination](https://medium.com/berkman-klein-center/a-deep-dive-on-digital-self-determination-368c48d87705) 2021-05-26 Berkman Klein
|
||||
> Questions of control over personal data were a cross-cutting theme throughout a [Research Sprint](https://cyber.harvard.edu/story/2021-03/research-sprint-examines-digital-self-determination-increasingly-interconnected-world) co-hosted by the [Berkman Klein Center for Internet & Society](http://cyber.harvard.edu) and [Digital Asia Hub](https://www.digitalasiahub.org/). The Sprint also examined other important dimensions of self-determination in the digitally networked world, for instance, self-expression and participation in civic life and the digital economy, or relationship-building and well-being, to name just a few application areas.
|
||||
* [DIGITAL SOVEREIGNTY](https://twit.tv/shows/floss-weekly/episodes/628) 2021-05-05 Doc Searls, Aaron Newcomb FLOSS WEEKLY
|
||||
> Dr. Andre Kudra of esatus.com discusses SSI, or Self-Sovereign Identity. It's a hot and fast-moving topic with a growing base of hackers, companies, nonprofits, and whole states, provinces and countries. Aaron Newcomb and Doc Searls probe Andre for lots of great intelligence about how SSI puts individuals in full charge of how they present minimized ID credentials safely, and inside a whole new framework. They also talk with Andre about his involvement with the demoscene and retro computing, which are especially huge in Europe. It's a great discussion on this episode of FLOSS Weekly.
|
||||
* [The principles of user sovereignty](https://uxdesign.cc/the-principles-of-user-sovereignty-515ac83401f6?sk=d37a69c8efc8a48cdd4a23d0518ba8d0) 2020-07-31 UX Design
|
||||
> The earliest discussion of the phrase I could find is a [blog post](https://blog.lizardwrangler.com/2011/08/04/extending-our-reach-many-layers-of-user-sovereignty/) from August 4th, 2011 by the “Chief Lizard Wrangler” herself, [Mitchell Baker](https://en.wikipedia.org/wiki/Mitchell_Baker) the CEO of Mozilla. In it she prophetically describes user sovereignty as the consequence of new “engines” that are “…open, open-source, interoperable, public-benefit, standards-based, platforms…” She also makes the critical link between the philosophy of openness and standards-based interoperability with that of identity management and personal data dominion.
|
||||
* [Identity and Digital Self-Sovereignty](https://medium.com/learning-machine-blog/identity-and-digital-self-sovereignty-1f3faab7d9e3) 2016-09-19 Natalie Smolenski
|
||||
> Web-based applications increasingly form the infrastructure of modern life. They are the seas, roads, buildings, schools, and libraries within which we travel, socialize, learn, and express ourselves. They store data that is integral to our social and legal identities. Without them, a person is consigned to something like social death — not too different from the situation of a passenger of a ship on the High Seas.
|
||||
|
||||
## Human Rights
|
||||
|
||||
* [If Tech Fails to Design for the Most Vulnerable, It Fails Us All: Building around the so-called typical user is a dangerous mistake](https://www.wired.com/story/technology-design-marginalized-communities/) 2022-05-15 Wired
|
||||
> WHAT DO RUSSIAN protesters have in common with Twitter users freaked out about Elon Musk reading their DMs and people worried about the criminalization of abortion? It would serve them all to be protected by a more robust set of design practices from companies developing technologies.
|
||||
* [Tech Tools for Human Rights Documentation](https://documentation-tools.theengineroom.org/) 2022-04-06 The Engine Room
|
||||
> Insights from research & practical guidance for civil society documenters of human rights violations
|
||||
* [Human Rights Documentation](https://documentation-tools.theengineroom.org/findings-documentation/) The Engine Room
|
||||
> For this research, The Engine Room and HURIDOCS conducted a combined total of 36 one-on-one interviews with civil society documenters of human rights abuses and direct support organisations. Our findings are supplemented by insights from interviews with eight tool developers working in the human rights documentation space.
|
||||
* [Tool Development](https://documentation-tools.theengineroom.org/findings-tool-dev/) The Engine Room
|
||||
> For this research, The Engine Room conducted eight interviews with tool developers, and carried out independent research into relevant tools.
|
||||
* [Transitional Justice](https://documentation-tools.theengineroom.org/findings-transitional-justice/) Tech tools from a transitional justice perspective
|
||||
> For this research, PILPG conducted interviews with 15 transitional justice experts and held three focus groups.
|
||||
* [TAKEAWAYS FROM OUR COMMUNITY CALL ON INTERSECTIONS BETWEEN DATA & DIGITAL RIGHTS AND SOCIAL JUSTICE](https://www.theengineroom.org/takeaways-from-our-community-call-on-intersections-between-data-digital-rights-and-social-justice/) 2022-03-21 The Engine Room
|
||||
> On February 15, we held a community call to discuss our newly-published [research findings](https://www.theengineroom.org/new-research-community-call-intersectional-approaches-to-data-and-digital-rights-advocacy/) on intersectional collaboration between social justice communities and data and digital rights (DDR) communities. We were joined by speakers Temi Lasade-Anderson from Alaase Lab, Luã Cruz from IDEC, Patronella Nqaba from Atlantic Fellows for Racial Equity and Paromita Shah from Just Futures Law.
|
||||
* [Human rights perspective on W3C and IETF protocol interaction](https://lists.w3.org/Archives/Public/public-credentials/2022Jan/0014.html) 2022-01-05 Adrian Gropper
|
||||
> The Ford Foundation paper attached provides the references. However, this thread should not be about governance philosophy but rather a focus on human rights as a design principle as we all work on protocols that will drive adoption of W3C VCs and DIDs at Internet scale.
|
||||
* [Redecentralize Digest — August 2021](https://redecentralize.org/redigest/2021/08/) 2021-08
|
||||
> Decisions made by engineers in internet standards bodies (such as IETF and W3C) have a large influence on internet technology, which in turn influences people’s lives — people whose needs may or may not have been taken into account. In the report [Human Rights Are Not a Bug](https://www.fordfoundation.org/work/learning/research-reports/human-rights-are-not-a-bug-upgrading-governance-for-an-equitable-internet/) (see also its launch event), Niels ten Oever asks “how internet governance processes could be updated to deeply embed the public interest in governance decisions and in decision-making culture”.
|
||||
* [Internet Governance - UDDI - Universal Declaration of Digital Identity](https://iiw.idcommons.net/10I/_Internet_Governance_-_UDDI_-_Universal_Declaration_of_Digital_Identity) 2021-05-06 Jeff Aresty, Kristina Yasuda IIW, IDCommons
|
||||
> Reaffirming the human rights and fundamental freedoms enshrined in the Universal Declaration of Human Rights and relevant international human rights agreements such as the UN GP on BHR and Constitutional Rights;
|
||||
>
|
||||
> Reaffirming the relevance of international human rights standards in the digital environment and the need to explore and expand new human rights guarantees for the future;
|
||||
* [Universal Declaration of Digital Rights](https://docs.google.com/document/d/1y9C-5TPYmRruRQqJq39-HePk3ypWLDpSAEVzuonOH2Q/edit) 2020-10-21 Johannes Ernst
|
||||
> all states should recognise and promote universal respect for and observance of both fundamental human and digital rights in physical domain and the digital spaces environment and ensure that these rights are upheld as core elements of a free, open and representative society
|
||||
|
||||
Loading…
Add table
Add a link
Reference in a new issue