mirror of
https://github.com/Decentralized-ID/decentralized-id.github.io.git
synced 2025-12-18 01:44:39 -05:00
sort
This commit is contained in:
parent
edb1146d45
commit
61bf576b03
5 changed files with 18 additions and 186 deletions
|
|
@ -43,6 +43,8 @@ last_modified_at: 2023-06-17
|
||||||
> In a real world scenario we anticipate a software based wallet for Decentralized Identity of Things. That would allow automation of online stores to obtain verifiable credentials programmatically.
|
> In a real world scenario we anticipate a software based wallet for Decentralized Identity of Things. That would allow automation of online stores to obtain verifiable credentials programmatically.
|
||||||
* [DIDoT - DID of Things. Decentralized Identity of Things](https://devpost.com/software/did-of-things-didot-allergen-management-in-food-shopping) 2022-01-31 Devpost
|
* [DIDoT - DID of Things. Decentralized Identity of Things](https://devpost.com/software/did-of-things-didot-allergen-management-in-food-shopping) 2022-01-31 Devpost
|
||||||
> Allergen management in food shopping. Based on the concept of ‘things’ having verifiable credentials. [...] Our proposed solution requires a virtual wallet that can be orchestrated programmatically. We discussed how other self sovereign solutions have this capability and confirmed with the AAD Verifiable Credentials hackathon support team that this capability is not available.
|
> Allergen management in food shopping. Based on the concept of ‘things’ having verifiable credentials. [...] Our proposed solution requires a virtual wallet that can be orchestrated programmatically. We discussed how other self sovereign solutions have this capability and confirmed with the AAD Verifiable Credentials hackathon support team that this capability is not available.
|
||||||
|
* [students from @HU_Utrecht are using Aries Framework JavaScript for smart locks.](https://twitter.com/AnimoSolutions/status/1394895595236626433) 2021-05-19 Animo
|
||||||
|
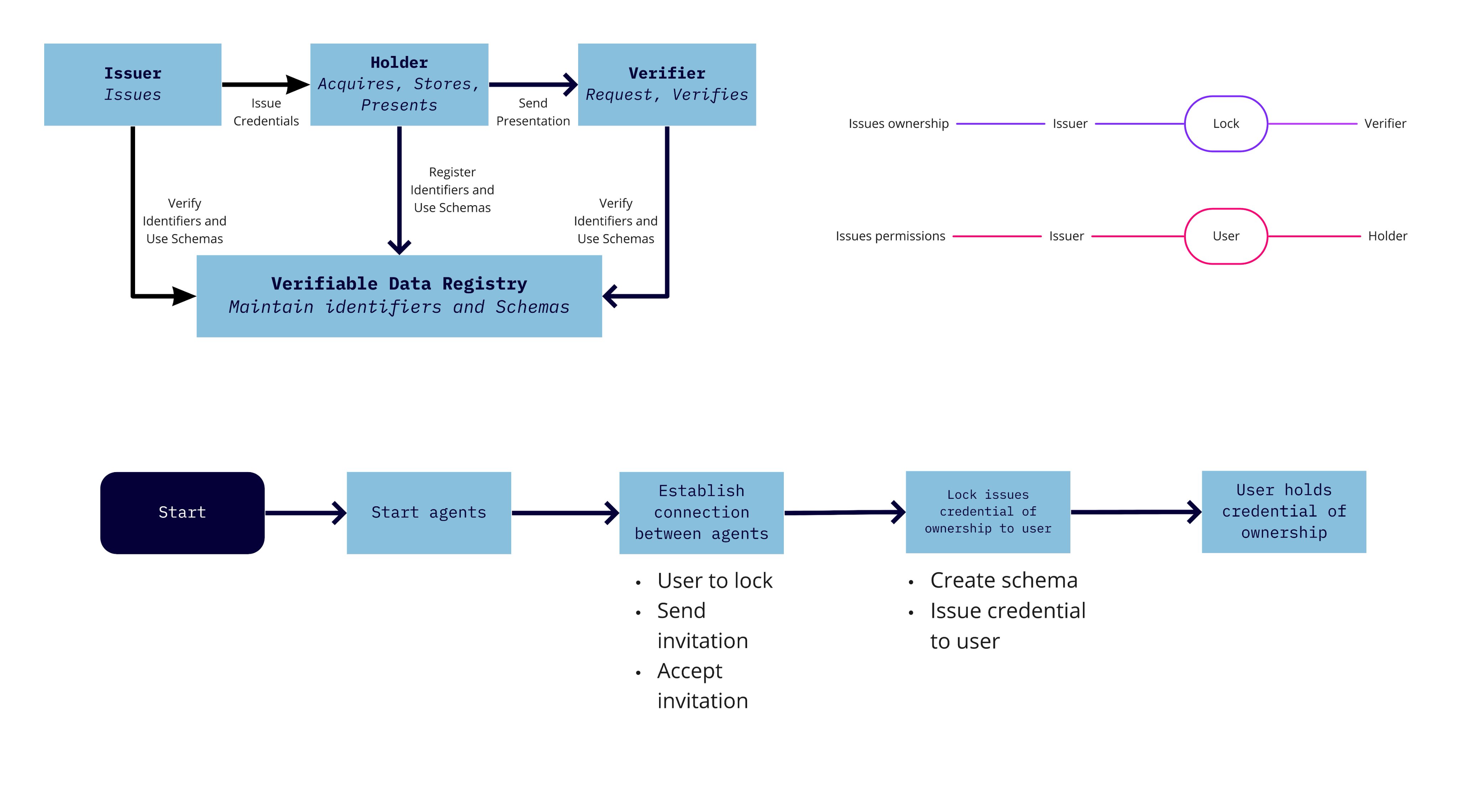
> 
|
||||||
|
|
||||||
## Devices
|
## Devices
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -13,6 +13,8 @@ last_modified_at: 2023-06-16
|
||||||
|
|
||||||
## Explainer
|
## Explainer
|
||||||
|
|
||||||
|
* [The Importance of Verifiable Credentials to Training Providers](https://uploads-ssl.webflow.com/6269810a06ae9fafd52556a3/629f94235eabc454ea48c117_The%20Importance%20of%20Verifiable%20Credentials%20for%20Training%20Providers.pdf?__hstc=100632769.d32f75d38c42eaa77409051b21d73653.1655033322879.1655033322879.1655033322879.1&__hssc=100632769.1.1655033322879&__hsfp=2803731784) 2022-06-03 Credivera
|
||||||
|
> like many other aspects of our daily lives, the digital transformation of education and training has added both convenience and challenges. Much like the shift to remote work, we can now learn from the comfort of our homes. Gone are the days of taking an in-person course where you receive your gold-sealed certificate upon completion of the last class, or walk across a stage to pick up your hard-earned degree.
|
||||||
* [Self-Sovereign Identity User Scenarios in the Educational Domain](https://er.educause.edu/articles/2022/4/self-sovereign-identity-user-scenarios-in-the-educational-domain) 2022-04-13 Gerd Kortemeyer Educause
|
* [Self-Sovereign Identity User Scenarios in the Educational Domain](https://er.educause.edu/articles/2022/4/self-sovereign-identity-user-scenarios-in-the-educational-domain) 2022-04-13 Gerd Kortemeyer Educause
|
||||||
> Due to the high level of international mobility in the academic sector, insular solutions relying on only one national type of government-issued digital ID card will be insufficient; instead, the officials at the federation need to decide which digital ID cards are valid to uniquely associate an individual with private cryptographic keys, similar to the way passports are acknowledged internationally
|
> Due to the high level of international mobility in the academic sector, insular solutions relying on only one national type of government-issued digital ID card will be insufficient; instead, the officials at the federation need to decide which digital ID cards are valid to uniquely associate an individual with private cryptographic keys, similar to the way passports are acknowledged internationally
|
||||||
* [Digital Credentials – the new student experience](https://condatis.com/webinars/webinar/digital-credentials/) 2022-03-14 Condatis
|
* [Digital Credentials – the new student experience](https://condatis.com/webinars/webinar/digital-credentials/) 2022-03-14 Condatis
|
||||||
|
|
@ -47,6 +49,8 @@ last_modified_at: 2023-06-16
|
||||||
|
|
||||||
* [When Job Candidates Lie, New Tech From ZippedScript And LearnCard Will Help You Catch Them](https://www.forbes.com/sites/zengernews/2022/09/16/when-job-candidates-lie-new-tech-from-zippedscript-and-learncard-will-help-you-catch-them/?sh=731b54b63ed4) 2022-09-16 Forbes
|
* [When Job Candidates Lie, New Tech From ZippedScript And LearnCard Will Help You Catch Them](https://www.forbes.com/sites/zengernews/2022/09/16/when-job-candidates-lie-new-tech-from-zippedscript-and-learncard-will-help-you-catch-them/?sh=731b54b63ed4) 2022-09-16 Forbes
|
||||||
> “recently launched [LearnCard](http://www.learncard.com/), a digital wallet for education and employment programmable verifiable credentials”
|
> “recently launched [LearnCard](http://www.learncard.com/), a digital wallet for education and employment programmable verifiable credentials”
|
||||||
|
* [How to Prevent Fraud using #MARKs](https://dhiway.com/prevent-credential-fraud/) 2021-10-26 DHIWay
|
||||||
|
> Credential fraud has, unfortunately, become commonplace in today’s instant electronic age. Especially problematic in [higher education](https://dhiway.com/hashmarks-in-the-education-sector/), credential fraud has spiralled into a multi-billion-dollar industry
|
||||||
* [Redefining the Student Journey](https://www.youtube.com/watch?v=enqQ0FyLaBc) 2021-05-11 Condatis
|
* [Redefining the Student Journey](https://www.youtube.com/watch?v=enqQ0FyLaBc) 2021-05-11 Condatis
|
||||||
> Digital innovation has been front and centre in Higher Education since the pandemic. The challenges remain for universities supporting students now and for the future. With the help of Microsoft Azure AD Verifiable Credentials, universities can support student needs effective and innovative digital approach.
|
> Digital innovation has been front and centre in Higher Education since the pandemic. The challenges remain for universities supporting students now and for the future. With the help of Microsoft Azure AD Verifiable Credentials, universities can support student needs effective and innovative digital approach.
|
||||||
* [Open Badges] [Blockchain and the future of Education](https://wellthatsinteresting.tech/blockchain-and-the-future-of-education/) 2020-08-10 WellThatsInteresting.tech
|
* [Open Badges] [Blockchain and the future of Education](https://wellthatsinteresting.tech/blockchain-and-the-future-of-education/) 2020-08-10 WellThatsInteresting.tech
|
||||||
|
|
|
||||||
|
|
@ -3,12 +3,16 @@ published: false
|
||||||
---
|
---
|
||||||
|
|
||||||
# Explainer
|
# Explainer
|
||||||
|
* [ID Verification Threats On the Horizon](https://stateofidentity.libsyn.com/id-verification-threats-on-the-horizon) 2022-03-31 Liminal Podcasts
|
||||||
|
> Cognito's CEO Alain Meier joins the State of Identity host Cameron D’Ambrosi to dive into why industries beyond financial services are now in the market for identity verification. They also unpack the impact of synthetic identity fraud across verticals, and how platforms find the balance when building their onboarding processes.
|
||||||
* [It’s time for digital self-sovereign identity](https://gcn.com/emerging-tech/2022/08/its-time-digital-self-sovereign-identity/375285/) GCN
|
* [It’s time for digital self-sovereign identity](https://gcn.com/emerging-tech/2022/08/its-time-digital-self-sovereign-identity/375285/) GCN
|
||||||
> the implementation of granular security measures to protect that data creates trusted networks between governments and the citizens they serve. Everyone wins.
|
> the implementation of granular security measures to protect that data creates trusted networks between governments and the citizens they serve. Everyone wins.
|
||||||
|
* [Digital Identity Isn’t Only For People](https://www.forbes.com/sites/davidbirch/2020/12/22/digital-identity-isnt-only-for-people/) 2020-12-22 David Birch, Forbes
|
||||||
* [Kaliya Young on Identikit with Michelle Dennedy](https://identitywoman.net/podcast-identikit-with-michelle-dennedy/)
|
> fintechs and regtechs looking for opportunities in the digital identity space should cast their ideas net pretty wide. Digital identities are not only for people and the future desperately needs digital identities for pretty much everything to underpin recognition, relationships and reputation (the 3Rs of the online economy).
|
||||||
|
* [Impacts from a new reality drive the need for an enhanced digital identity framework](https://bankautomationnews.com/allposts/risk-security/impacts-from-a-new-reality-drive-the-need-for-an-enhanced-digital-identity-framework/) 2022-02-28 Bank Automation News
|
||||||
our latest series examining the evolution of digital identity, and how self-sovereign identity, specifically, can advance a consent-based economy.
|
> While US-based entities are adhering to an enhanced regulatory framework, these mandates are particularly applicable in Europe, where there is necessary compliance with enacted standards (such as the General Data Protection Regulation—commonly known as GDPR—and the Payment Service Providers Directive 2—referred to as PSD2. A clear need for a true and persistent digital identity as a solution to the ancillary—and sometimes unforeseen—challenges that have arisen.
|
||||||
|
* [Kaliya Young on Identikit with Michelle Dennedy](https://identitywoman.net/podcast-identikit-with-michelle-dennedy/) IdentityWoman
|
||||||
|
> our latest series examining the evolution of digital identity, and how self-sovereign identity, specifically, can advance a consent-based economy.
|
||||||
* [The Architecture of Identity Systems](https://www.windley.com/archives/2020/09/the_architecture_of_identity_systems.shtml) by Phil Windley
|
* [The Architecture of Identity Systems](https://www.windley.com/archives/2020/09/the_architecture_of_identity_systems.shtml) by Phil Windley
|
||||||
> I recently read a paper from Sam Smith, [Key Event Receipt Infrastructure](https://arxiv.org/abs/1907.02143), that provided inspiration for a way to think about and classify identity systems. In particular his terminology was helpful to me. This blog post uses terminology and ideas from Sam's paper to classify and analyze three different identity system architectures. I hope it provides a useful model for thinking about identity online.
|
> I recently read a paper from Sam Smith, [Key Event Receipt Infrastructure](https://arxiv.org/abs/1907.02143), that provided inspiration for a way to think about and classify identity systems. In particular his terminology was helpful to me. This blog post uses terminology and ideas from Sam's paper to classify and analyze three different identity system architectures. I hope it provides a useful model for thinking about identity online.
|
||||||
* [The SSO Practitioner’s Introduction to Decentralized Identity](https://www.pingidentity.com/en/resources/blog/post/sso-practitioners-introduction-decentralized-identity.html)
|
* [The SSO Practitioner’s Introduction to Decentralized Identity](https://www.pingidentity.com/en/resources/blog/post/sso-practitioners-introduction-decentralized-identity.html)
|
||||||
|
|
|
||||||
|
|
@ -1,182 +0,0 @@
|
||||||
---
|
|
||||||
published: false
|
|
||||||
---
|
|
||||||
|
|
||||||
## Use-Case
|
|
||||||
* [25+ Proof of Concepts (PoCs) for Verifiable Credentials](https://academy.affinidi.com/25-proof-of-concept-poc-for-verifiable-credentials-edf684b592f2) 2021-05-20 Affinidi
|
|
||||||
> Today, we proudly present another 25+ Proof of Concepts for VC implementation. These use cases are a compilation of the [submissions](https://affinidipocathon.devpost.com/) (in no particular order) made by the participants of the Affindi PoCathon 2021.
|
|
||||||
* [26 Suggested Use Cases of Verifiable Credentials (With Some Real-World Examples)](https://academy.affinidi.com/25-real-world-use-cases-of-verifiable-credentials-4657c9cbc5e) Affinidi
|
|
||||||
> we hope that business leaders, entrepreneurs, and developers will use this article as a guide to create some breakthrough solutions that will benefit the society at large.
|
|
||||||
* [Self-Sovereign Identity: More Use Cases](https://www.bankinfosecurity.com/self-sovereign-identity-more-use-cases-a-16448): Heather Dahl and Ken Ebert of Indicio Discuss Decentralized ID Management
|
|
||||||
> In a video interview with Information Security Media Group, Dahl and Ebert discuss:
|
|
||||||
>
|
|
||||||
> - The evolution of Indicio.tech from the Sovrin Foundation;
|
|
||||||
> - Key initiatives in implementing and testing decentralized identity;
|
|
||||||
> - How a decentralized workforce is accelerating the need for identity management.
|
|
||||||
* [How Exactly Are Verifiable Credentials Making the World Better?](https://sgershuni.medium.com/how-exactly-are-verifiable-credentials-making-the-world-better-eb72145c061) Stepan Gershuni
|
|
||||||
> 6 stories of how verifiable credentials can improve the lives of every day people:
|
|
||||||
>
|
|
||||||
> Ajay is an Uber driver in San Francisco. He wants to try various temporary jobs while he’s studying but joining Lyft, Postmates and other platforms requires going through a long and tedious background verification and car certification process over and over again.
|
|
||||||
* [5 Promising Use Cases for Verifiable Credentials](https://hackernoon.com/5-promising-use-cases-for-verifiable-credentials-tu1y348k) Hackernoon
|
|
||||||
> several industries are already digging in. Here are some of the most visible and promising use cases.
|
|
||||||
* [Digital Identity Isn’t Only For People](https://www.forbes.com/sites/davidbirch/2020/12/22/digital-identity-isnt-only-for-people/) 2020-12-22 David Birch, Forbes
|
|
||||||
> fintechs and regtechs looking for opportunities in the digital identity space should cast their ideas net pretty wide. Digital identities are not only for people and the future desperately needs digital identities for pretty much everything to underpin recognition, relationships and reputation (the 3Rs of the online economy).
|
|
||||||
* [ID Verification Threats On the Horizon](https://stateofidentity.libsyn.com/id-verification-threats-on-the-horizon) Liminal Podcasts
|
|
||||||
> Cognito's CEO Alain Meier joins the State of Identity host Cameron D’Ambrosi to dive into why industries beyond financial services are now in the market for identity verification. They also unpack the impact of synthetic identity fraud across verticals, and how platforms find the balance when building their onboarding processes.
|
|
||||||
* [SSI Essentials: 35 use cases of decentralized identities that will make your life easier](https://gataca.io/blog/ssi-essentials-35-use-cases-of-decentralized-identities-that-will-make-your-life-easier) Gataca
|
|
||||||
|
|
||||||
## Real World Implementations
|
|
||||||
* [Notes from W3C TPAC on major deployments of Verifiable Credentials](https://twitter.com/philarcher1/status/1570082512122294273) Manu Sporny via Phil Archer
|
|
||||||
> - Steel, Oil Agriculture Shipment into US Customs ($2.3T in good/year)
|
|
||||||
> - European Digital Wallet (€163M funding, 450M people)
|
|
||||||
> - Digital Education Credentials in Uganda, Nigeria, Kenya (323M people)
|
|
||||||
> - Digital Age Verfication (152k retail stores, 200M people)
|
|
||||||
> - Content Authenticity Initative (30M Adobe customers)
|
|
||||||
> - Digital Permanent Resident Cards (14M people)
|
|
||||||
* [IIW verifiable credentials - Decentralized VC integration with Eventbrite and Qiqo chat. This session will review the implementation process, lessons learned, and community discussion on related use cases.](https://iiw.idcommons.net/11A/_IIW_verifiable_credentials_-_Decentralized_VC_integration_with_Eventbrite_and_Qiqo_chat._This_session_will_review_the_implementation_process,_lessons_learned,_and_community_discussion_on_related_use_cases.) 2021-05-07 Mike Vesey, Karl Kneis
|
|
||||||
> * IIW is now issuing verifiable credentials for registration and access to live events managed through Qiqo chat forums.
|
|
||||||
> * Credentials, verification proofing, and integration provided by the IdRamp Zero Trust ecosystem management platform and APIs.
|
|
||||||
> * IIW credentials are interoperable with a range of standardised wallet providers.
|
|
||||||
> * Issuance and proofing are incorporated seamlessly within the existing customer communications flow.
|
|
||||||
> * Integration with Qiqo and Eventbrite required no significant development effort.
|
|
||||||
|
|
||||||
## Cases
|
|
||||||
|
|
||||||
* [Divitel & Ledger Leopard Team Up to Apply Blockchain & Self Sovereign Identity Technology to Video Distribution](https://www.canto.org/blog/divitel-and-ledger-leopard-team-up-to-apply-blockchain-self-sovereign-identity-technology-to-video-distribution/) 2021-06-11 Canto
|
|
||||||
> ready to market by end of end of 2022 offering increased flexibility, control, ease of use and speed when managing the access of video distribution ecosystem data, independent of the technology used. Divitel video carrier customers will be offered the option to include this blockchain module on top of their ecosystems.
|
|
||||||
|
|
||||||
### Loyalty programs
|
|
||||||
|
|
||||||
* [@_XPID_](https://twitter.com/_XPID_) · [Nov 2](https://twitter.com/_XPID_/status/1323371035484250113)
|
|
||||||
> Check out the latest version of our beta prototype in the Appstore for #verifiablecredentials for #LoyaltyPrograms. https://apps.apple.com/us/app/id1458328593 When #sovereign #decentralized #identity becomes a reality, your #Loyalty and #loyaltyrewards #Wallet will be on XPID. #SSI
|
|
||||||
* [Reimagining Customer Loyalty Programs With Verifiable Credentials: A Pravici Case Study](https://www.evernym.com/blog/customer-loyalty-verifiable-credentials/) 2021-04-15 Evernym
|
|
||||||
> [Pravici](https://pravici.com/), an Evernym customer and startup based out of Chandler, Arizona, is looking to flip the equation. Their solution, Tokenized Loyalty Points (TLP), uses verifiable credential technology to give individual consumers control over their data, while empowering them to direct how their favorite brands can use this data for loyalty and other campaigns.
|
|
||||||
|
|
||||||
### Finance
|
|
||||||
* [Julian Wilson: Self-Sovereign Data meets Open Banking](https://mastersofprivacy.com/julian-wilson-self-sovereign-data-meets-open-banking/) Masters of Privacy
|
|
||||||
> Julian Wilson began his career at Apple in the late 80s [...] joined Ecospend in 2019 to build a self-sovereign data service on top of an Open Banking platform. He describes his role as putting an Internet lens onto product design.
|
|
||||||
* [Impacts from a new reality drive the need for an enhanced digital identity framework](https://bankautomationnews.com/allposts/risk-security/impacts-from-a-new-reality-drive-the-need-for-an-enhanced-digital-identity-framework/) Bank Automation News
|
|
||||||
> While US-based entities are adhering to an enhanced regulatory framework, these mandates are particularly applicable in Europe, where there is necessary compliance with enacted standards (such as the General Data Protection Regulation—commonly known as GDPR—and the Payment Service Providers Directive 2—referred to as PSD2. A clear need for a true and persistent digital identity as a solution to the ancillary—and sometimes unforeseen—challenges that have arisen.
|
|
||||||
* [Banking’s identity problem](https://www.globalbankingandfinance.com/bankings-identity-problem/) Global Banking and Finance
|
|
||||||
> Banks have sought to overcome some of these challenges with the use of biometrics such as facial recognition and fingerprints. These are now more commonly used to login to, or unlock devices, and increase usability, but still leave the challenge of proving the authenticity of a document wide open to abuse.
|
|
||||||
- [New Bank Account Use Case](https://www.youtube.com/watch?v=YRLu4U4hSZ8)
|
|
||||||
* [Building an SSI Ecosystem: MemberPass and Credit Unions](https://www.windley.com/archives/2021/06/building_an_ssi_ecosystem_memberpass_and_credit_unions.shtml) 2021/06 Phil Windley
|
|
||||||
> Credit unions and their members face the threat of fraud on all sides. And credit unions employ lots of tools to fight it. But ultimately, the problem comes down to the member and credit union authenticating each other. The problem is that doing this securely annoys people.
|
|
||||||
|
|
||||||
* [How to Prevent Fraud using #MARKs](https://dhiway.com/prevent-credential-fraud/) DHIWay
|
|
||||||
> Credential fraud has, unfortunately, become commonplace in today’s instant electronic age. Especially problematic in [higher education](https://dhiway.com/hashmarks-in-the-education-sector/), credential fraud has spiralled into a multi-billion-dollar industry
|
|
||||||
* [Opening the domestic card rails to innovation](https://blog.meeco.me/opening-the-domestic-card-rails-to-innovation/) Meeco
|
|
||||||
> Enabling Australian FinTechs a direct avenue to discuss how they partner and collaborate to access the eftpos payments network through the Committee resulted in recommendations that covered a number of central themes, including consultation and engagement, regulation, and technology and solutionsBen Tabell, eftpos Chief Information Officer and Committee Chair
|
|
||||||
* [MemberPass Digital ID can help Reduce Expenses and Build Member Trust](https://www.memberpass.com/2021/06/memberpass-digital-id-can-help-reduce-expenses-and-build-member-trust/)
|
|
||||||
|
|
||||||
You can probably use the good news. It’s never been easy to run a credit union, especially when you get whacked from all sides. Regulations change, members always seem to want access to another shiny new technology gadget, and financial fraud continues to be a threat. On top of that, we’ve all had to grapple with the pervasive life-changing effects of the coronavirus pandemic for the past year.
|
|
||||||
* [A banking approach to decentralized identity and building a credential ecosystem - Mike Brown](https://www.slideshare.net/SSIMeetup/a-banking-approach-to-decentralized-identity-and-building-a-credential-ecosystem-mike-brown)
|
|
||||||
|
|
||||||
### Security
|
|
||||||
* [Hackers Gaining Power of Subpoena Via Fake “Emergency Data Requests”](https://krebsonsecurity.com/2022/03/hackers-gaining-power-of-subpoena-via-fake-emergency-data-requests/) 2022-03
|
|
||||||
> If there was a trust framework for police departments and a DID registry for them - the police departments could issue VCs to their officers.
|
|
||||||
>
|
|
||||||
> If you want to se how hard this was/would have been to achieve in earlier technology stacks take a look at [conceptual outlines](https://trustmark.gtri.gatech.edu/concept/) from this NSTIC (National Strategies for Trusted Identities in Cyberspace) developing a trust framework for law enforcement federations done by the Georgia Technology Reserach Institute and the [results/learnings.](https://trustmark.gtri.gatech.edu/insights/)
|
|
||||||
* [Digital IDs under attack: How to tackle the threat?](https://www.helpnetsecurity.com/2022/01/27/ssi-face-presentation-attacks/) 2022-01-27 HelpnetSecurity
|
|
||||||
> - photo attacks based on the presentation of facial evidence of an image of a face printed or displayed via a device’s screen.
|
|
||||||
> - video of user replay attack usually consisting of placing the screen of the attacker’s device in front of the camera.
|
|
||||||
> - 3D mask attacks where 3D masks are crafted to reproduce the real traits of a human face and even include eyes holes to fool the liveliness detection based on eye gaze, blinking and motion.
|
|
||||||
> - deepfake attacks make use of leveraging software capable to create a synthetic video or image realistically representing someone else. Attackers are suspected to have access to a wide dataset containing images or a video of their target.
|
|
||||||
* [The Equifax Incident, And How SSI Could Have Prevented It](https://europechain.io/identity/equifax-incident-ssi-prevented-it/) Europechain
|
|
||||||
> On March 8, 2017, Cisco staff found and reported a critical flaw in Apache Struts, an open-source framework that enables the creation of web-based Java applications. The vulnerability in question was identified as CVE-2017-5638. In short, Strut’s parser tool, Jakarta, could be manipulated to enable a malicious actor to upload files remotely to a server, and potentially run code on that compromised server.
|
|
||||||
|
|
||||||
### Career
|
|
||||||
|
|
||||||
* [Coming soon — a resume-validating blockchain network for job seeker](https://www.computerworld.com/article/3675547/coming-soon-a-resume-validating-blockchain-network-for-job-seekers.html#tk.rss_security) Computer World
|
|
||||||
> "Verifying applicant career records can take days, weeks, if not months, to complete," said Dror Gurevich, founder and CEO of the Velocity Network Foundation. "Hiring methods are severely outdated to the point that one in three Americans have [admitted to lying on their resumes](https://t.yesware.com/tt/0db4de0058ee9613cdfcabd5fae96c6ca51e1b7f/275468cd0c53df0b2dfa60dbb913464b/c19e9bd03a563c32bab519acc1fa9f5b/www.resumebuilder.com/1-in-3-americans-admit-to-lying-on-resume/), which slows the hiring process immensely.
|
|
||||||
* [Trusted Career Credentials](https://www.linkedin.com/pulse/trusted-career-credentials-dr-gordon-jones/) 2022-02-11 Dr Gordon Jones
|
|
||||||
> Today, even in this digital world that has expanded over the past two years, the job market still relies on self-reported attributes, records, resumes, and/or LinkedIn profiles, that individuals share with employers or recruiters as the source for applicants and employee data.
|
|
||||||
* [Self sovereign career identity](https://diginomica.com/self-sovereign-career-identity-conversation-meg-bear-sap-successfactors) Diginomica Meg Bear
|
|
||||||
> The Velocity piece is a way for me as an individual to own my credentials, to say, these are the things that I know. And these are the things I've done. And if I can own that, I have a lot more interest in it. And I can use it in a lot more interesting ways. In the past, that might have just been something that I built as reputation within a company, I can now make that a more dynamic and portable reputation I can take with me anywhere.
|
|
||||||
* [Blockchain and the Decentralised Workforce](https://workforcefuturist.substack.com/p/blockchain-and-the-decentralised-workforce) WorkforceFuturist
|
|
||||||
* [How Blockchain Technology and Self-Sovereign Identity Enables the New Normal of Remote Learning, Training and Working](https://www.linkedin.com/pulse/how-blockchain-technology-self-sovereign-identity-enables-hossain-) Md Sabbir Hossain
|
|
||||||
|
|
||||||
## IOT
|
|
||||||
|
|
||||||
* [SSI for smart locks](https://twitter.com/AnimoSolutions/status/1394895595236626433) h\t Animo
|
|
||||||
|
|
||||||
## Gaming
|
|
||||||
* [Self-Sovereign Identity for Online Gaming, VR, & AR – Crucible](https://identity-economy.de/self-sovereign-identity-for-online-gaming-vr-ar-crucible) Evernym (via identity-economy.de)
|
|
||||||
> Crucible's CEO (Ryan Gill) and CTO (Toby Tremayne) for a discussion on what self-sovereign identity (SSI) and verifiable credentials mean for gaming and the greater online entertainment sector.
|
|
||||||
|
|
||||||
## Business
|
|
||||||
* [Growing confidence is programmed in – how self-sovereign digital identities make business relationships easier](https://www.bosch.com/research/blog/economy-of-things/technology/#ssi_) Bosch
|
|
||||||
> Bosch will now also systematically transfer the self-sovereign identity (SSI) principle to the B2B sector – in other words to business relationships between companies. A further step will involve transferring it to secure and trustworthy interactions between machines.
|
|
||||||
* [Self-Sovereign E-Commerce](https://iiw.idcommons.net/23J/_Self-Sovereign_E-Commerce) by Doc Searls
|
|
||||||
There is momentum here, and a need to start building out much of what was discussed.
|
|
||||||
> Doc introduced the session with the slide deck [here](https://www.slideshare.net/dsearls/day3iiw-sesion), wearing his hat as a founding member of [Customer Commons](http://customercommons.org), the .org working on the Intention Byway discussed at earlier IIW sessions and described in [this blog](https://customercommons.org/2021/04/27/a-new-way/), posed later. 2021-04-27
|
|
||||||
>
|
|
||||||
> His case is that the incumbent e-commece system hasn’t progressed past its dependence on the cookie, and perhaps never will; and that there is a need to stand up an alternate model, built on asynchronous pub-sub messaging and compute nodes that run apps that don’t have to come from the stores of Apple and Google.
|
|
||||||
>
|
|
||||||
> First examples of target areas (where communities are already active) are food distribution in Michigan and real estate in Boston. Hadrian Zbarcea led the discussion of both, using slides from the deck above.
|
|
||||||
|
|
||||||
## Property Management
|
|
||||||
|
|
||||||
* [A brighter future for tenant/landlord relationships](https://domilabs.io/tenant-landlord-relationships/) Domi Labs
|
|
||||||
> it’s hard to keep track since some call, some… email, and still others send you a message on WhatsApp.” Going through all of these disparate messages is its own fulltime job!
|
|
||||||
>
|
|
||||||
> That’s why Domi locates all communication about a property in one place, making it easy for tenants and property managers to stay in touch.
|
|
||||||
* [The Nail Finds a Hammer: Self-Sovereign Identity, Design Principles, and Property Rights in the Developing World](https://www.newamerica.org/future-property-rights/reports/nail-finds-hammer/) 2018-10-18 New America
|
|
||||||
>
|
|
||||||
|
|
||||||
## Energy Systems
|
|
||||||
|
|
||||||
* [Use Case: American Electric Power](https://idramp.com/use-case-american-electric-power/)
|
|
||||||
> What kind of strategy will take you to being a next-generation utility company? For AEP Ohio, a large electric utility company based in Columbus, this challenge began with a comprehensive review of their entire ecosystem and which identified their key pain points for innovation.
|
|
||||||
* [Digital identities – building block for an automated energy system](https://www.smart-energy.com/digitalisation/digital-identities-building-block-for-an-automated-energy-system/) Smart Energy
|
|
||||||
> New features include credential revocation and expiration, full support for role-authorised issuance, credential issuance based on email verification and asset administration as well as better alignment with the W3C’s Verifiable Credential Standards.
|
|
||||||
|
|
||||||
## Record Keeping
|
|
||||||
|
|
||||||
* [A Holochain DocuSign Challenge](https://blog.holochain.org/a-holochain-docusign-challenge/)
|
|
||||||
* [Trusted Timestamping Part 1: Scenarios](https://medium.com/finema/trusted-timestamping-part-1-scenarios-9bf4a7cc2364) Nunnaphat Songmanee, Finema
|
|
||||||
> Evidentiary value is an essential component of important transactions. When a transaction is recorded in a printed document, one way to impart evidentiary value is by including date and time
|
|
||||||
|
|
||||||
## Employee
|
|
||||||
* [Survey: How Do You Use Your Identity at Work?](https://findbiometrics.com/survey-how-do-you-use-your-identity-at-work/) FindBiometrics
|
|
||||||
> The COVID-19 pandemic rapidly shifted the way we work, coinciding with digital transformation trends that depend on strong identity assurance. Hybrid workplaces are more common, as is completely remote work
|
|
||||||
* [Blockchains in HR: Prosoon and Talao go together on SSI and HR credentials](https://medium.com/@talao_io/blockchains-in-hr-prosoon-and-talao-go-together-on-ssi-and-hr-credentials-3b92968011fe) Talao
|
|
||||||
> This partnership will enable the use of Blockchain and Self-Sovereign Identity technologies such as verifiable credentials to enable the support of diplomas and professional certifications in compliance with personal data in a decentralized environment (#web3).
|
|
||||||
|
|
||||||
## Education
|
|
||||||
* [The Importance of Verifiable Credentials to Training Providers](https://uploads-ssl.webflow.com/6269810a06ae9fafd52556a3/629f94235eabc454ea48c117_The%20Importance%20of%20Verifiable%20Credentials%20for%20Training%20Providers.pdf?__hstc=100632769.d32f75d38c42eaa77409051b21d73653.1655033322879.1655033322879.1655033322879.1&__hssc=100632769.1.1655033322879&__hsfp=2803731784) Credivera
|
|
||||||
> Digital badges or PDF credentials lack proof of being authentic and current, and can be easily reproduced or falsified, impacting both the individual and the reputation of the training provider.
|
|
||||||
|
|
||||||
## Reputation
|
|
||||||
|
|
||||||
* [An autonomous reputation system](https://reb00ted.org/tech/20220810-autonomous-reputation-system/) reb00ted
|
|
||||||
> we need to figure out how to give more power to “better” actors within a given community or context, and disempower or keep out the detractors and direct opponents. All without putting a centralized authority in place.
|
|
||||||
|
|
||||||
## Account managment
|
|
||||||
* [Transferable Accounts Putting Passengers at Risk](https://www.windley.com/archives/2022/06/transferable_accounts_putting_passengers_at_risk.shtml) Phil Windley
|
|
||||||
> The non-transferability of verifiable credential is one of their super powers. This post examines how that super power can be used to reduce fraud and increase safety in a hired car platform.
|
|
||||||
|
|
||||||
## Bots
|
|
||||||
|
|
||||||
* [War Against the Robots – Pick your Side with SelfKey & Metaproof Platform](https://selfkey.org/war-against-the-robots-pick-your-side-with-selfkey-metaproof-platform/) SelfKey Foundation
|
|
||||||
> Trying to ban or sideline bots is not a solution. The solution is to distinguish bots from humans so that humans can do human stuff and bots can do bot stuff.
|
|
||||||
|
|
||||||
## Climate
|
|
||||||
* [OpenEarth partners with BCGov to develop a digital trust marketplace for climate accounting](https://www.openearth.org/blog/openearth-partners-with-the-government-of-british-columbia-to-develop-a-digital-trust-marketplace-for-climate-accounting) OpenEarth Foundation
|
|
||||||
> OpenEarth Foundation partnered with the Mines Digital Trust initiative to allow BC companies to also share their greenhouse gas (GHG) emissions credentials to the [OpenClimate](https://www.openearth.org/projects/openclimate) platform so that they can be integrated into BC’s subnational climate inventory and showcased to interested purchasers and civic society
|
|
||||||
|
|
||||||
## Events
|
|
||||||
* [Event tickets as verifiable credentials](https://lissi-id.medium.com/event-tickets-as-verifiable-credentials-31f4a10b28cc) Lissi
|
|
||||||
> This article explains how verifiable credentials can be used to benefit event organizers and visitors alike based on a practical usage of the Lissi team.
|
|
||||||
|
|
||||||
## Content Attribution
|
|
||||||
* [Yes, verifiable authentic human content is important.](https://twitter.com/OR13b/status/1573100718164164610) Orie Steele
|
|
||||||
*The [Content Authenticity Initiative](https://contentauthenticity.org/how-it-works) one of Orie’s favoriate Use-cases for VCS*
|
|
||||||
> I also think cryptography can provide better transparency for synthetic content. It's one of my favorite applications of W3C Verifiable Credentials.
|
|
||||||
* [Self sovereign online identity is going to be a CRITICAL tool for everyone on the internet.](https://twitter.com/ericxtang/status/1575645620659900417) EricTang.eth
|
|
||||||
> Without it, we will lose trust of any content on the internet due to AI advancement in the next 12-24 months.
|
|
||||||
>
|
|
||||||
> This one of the most urgent issues in our society today.
|
|
||||||
* [Creating trust in assertions, claims and the authenticity of the original content](https://liccium.com/) LICCIUM
|
|
||||||
|
|
||||||
|
|
||||||
|
|
@ -7,6 +7,10 @@ published: false
|
||||||
|
|
||||||
what gives Aggregators their power is not their control of supply: they are not the only way to find websites, or to post your opinions online; rather, it is their control of demand. People are used to Google, or it is the default, so sites and advertisers don’t want to spend their time and money on alternatives; people want other people to see what they have to say, so they don’t want to risk writing a blog that no one reads, or spending time on a social network that because it lacks the network has no sense of social.
|
what gives Aggregators their power is not their control of supply: they are not the only way to find websites, or to post your opinions online; rather, it is their control of demand. People are used to Google, or it is the default, so sites and advertisers don’t want to spend their time and money on alternatives; people want other people to see what they have to say, so they don’t want to risk writing a blog that no one reads, or spending time on a social network that because it lacks the network has no sense of social.
|
||||||
|
|
||||||
|
## Gaming
|
||||||
|
* [Self-Sovereign Identity for Online Gaming, VR, & AR – Crucible](https://www.youtube.com/watch?v=Jd2YdxJ-LWA) Evernym
|
||||||
|
> Crucible's CEO (Ryan Gill) and CTO (Toby Tremayne) for a discussion on what self-sovereign identity (SSI) and verifiable credentials mean for gaming and the greater online entertainment sector.
|
||||||
|
|
||||||
* [Web3 and Digital Embodiment](https://www.windley.com/archives/2022/01/web3_and_digital_embodiment.shtml) Phil Windley
|
* [Web3 and Digital Embodiment](https://www.windley.com/archives/2022/01/web3_and_digital_embodiment.shtml) Phil Windley
|
||||||
|
|
||||||
Web3 will make a difference for all of us if it enables people to become digitally embodied, able to recognize, remember, and react to other people and organizations online—without the need to be in someone else's database.
|
Web3 will make a difference for all of us if it enables people to become digitally embodied, able to recognize, remember, and react to other people and organizations online—without the need to be in someone else's database.
|
||||||
|
|
|
||||||
Loading…
Add table
Add a link
Reference in a new issue