mirror of
https://github.com/Decentralized-ID/decentralized-id.github.io.git
synced 2025-12-15 00:19:44 -05:00
pages from data 0.1
This commit is contained in:
parent
35b743227d
commit
5a00e4c98d
17 changed files with 705 additions and 1379 deletions
File diff suppressed because one or more lines are too long
File diff suppressed because one or more lines are too long
|
|
@ -4,12 +4,24 @@ layout: single
|
|||
{%assign todo = "parent,use,sector,market,projects,feed,policy,event,tags" | split: ","%}
|
||||
{%assign socials = "discord,crunchbase,linkedin,telegram,twitter,youtube" | split: ","%}
|
||||
{%assign core = "docs,developers,app,forum,github" | split: ","%}
|
||||
{%assign other = "tech,standard" | split: ","%}
|
||||
{% if page.name %}
|
||||
{% assign name = page.name %}
|
||||
{% for row in site.data.companys %}
|
||||
{% if row.name == name %}
|
||||
{%if row.location %}<strong>Location:</strong> <em>{{row.location}}</em>{% elsif row.region%} <strong>Region: </strong><em>{{row.region}}</em>{%endif%}{%if row.authors.last != nil %} <strong>Founded by</strong>: {{row.authors.last}}{%endif%}{%if row.date.last != nil %} <strong>Founded date</strong>: {{row.date.last}} {%endif%} <strong>Main Links:</strong> <em><a href="{{row.link}}">Website</a> <a href="{{row.blog}}">Blog</a> </em>
|
||||
{% if row.name == page.name %}
|
||||
<p>{%if row.location %}
|
||||
<strong>Location:</strong> <em>{{row.location}}</em>
|
||||
{% elsif row.region%}
|
||||
<strong>Region: </strong><em>{{row.region}}</em>
|
||||
{%endif%}
|
||||
{%if row.founders != nil %}
|
||||
{% if row.founders contains ';' %}
|
||||
{% assign authors = row.founders | replace: ";","," %}
|
||||
<strong>Founders</strong>: {{authors}}
|
||||
{%else%}
|
||||
<strong>Founder</strong>: {{row.founders}}
|
||||
{%endif%}
|
||||
{%endif%}
|
||||
{%if row.date != nil %} <strong>Founded</strong>: {{row.date}} {%endif%}<br>
|
||||
<strong>Main:</strong> <em><a href="{{row.link}}">Website</a> <a href="{{row.blog}}">Blog</a> </em>
|
||||
{% for item in row %}
|
||||
{% if core contains item.first %}
|
||||
{% if item.last != nil %}
|
||||
|
|
@ -27,17 +39,110 @@ layout: single
|
|||
{% endfor %}
|
||||
<p><blockquote>{{row.text | markdownify }}</blockquote></p>
|
||||
{% endif%}
|
||||
{% endfor %}
|
||||
<h2>Content</h2>
|
||||
<ul>
|
||||
{% for row in site.data.content %}
|
||||
{% assign dname = row.main %}
|
||||
{% if dname == page.name %}
|
||||
{% if row.type != "Company"%}
|
||||
<li>{% if row.parent %}[{{row.parent}}] {% endif %}<a href="{{ row.link }}">{{ row.title }}</a>{% if row.authors %}{% assign authors = row.authors %}{% if authors contains ';' %}{% assign authors = authors | replace: ";","," %}{{authors | prepend: ": "}}{% else %}{% assign authors = row.authors | prepend: ", "%}{{authors}}{%endif%}{%endif%}</li>
|
||||
{% if row.text %}<blockquote>{{row.text | markdownify}}</blockquote>{%endif%}
|
||||
{% endif %}
|
||||
{% endif %}
|
||||
{% endfor %}</p>
|
||||
{%assign headers = "Meta,Ecosystem,Product,Standards,HowTo,Resources,Explainer" | split: "," %}
|
||||
{% for item in headers %}
|
||||
{%assign mark=''%}
|
||||
{% for row in site.data.content %}
|
||||
{% if row.section == item and row.main == page.name and mark != 1 %}{%assign mark = 1%}<h2 id="{{item}}">{{item | capitalize}}</h2><ul>{%endif%}
|
||||
{% if row.section == item and row.main == page.name %}
|
||||
{%assign attributes = "tags,market,use,sector,projects,tech,standard" | split: "," %}
|
||||
<li><small>
|
||||
{% if row.related contains ';' %}
|
||||
<strong>Relevant</strong>:{%assign related = row.related|split:';'%}
|
||||
{%assign trekker = 0%}
|
||||
{%for item in related%}
|
||||
{%assign trekker = trekker | plus: 1%}
|
||||
{%endfor%}
|
||||
{%for item in related%}
|
||||
{%if item != nil%} {{item|strip}}{%if trekker > 1%},{%assign trekker = trekker | minus: 1%}{%endif%}{%endif%}
|
||||
{%endfor%}
|
||||
{%elsif row.related == nil%}
|
||||
{%else%}
|
||||
<strong>Relevant</strong>: {{row.related}}
|
||||
{%endif%}
|
||||
{%if row.parent !=nil and row.parent != page.name%}<strong>Parent: </strong>{{row.parent}}{%endif%}
|
||||
<strong>Type: </strong>{{row.type|strip|capitalize}}</small>
|
||||
<strong><a href="{{ row.link }}">{{ row.title }}</a></strong>
|
||||
<small>
|
||||
{% if row.founders !=nil%}
|
||||
{% if row.founders contains ';' %}
|
||||
<strong>Author(s)</strong>{{ row.founders | replace: ";","," | prepend: ": "}}
|
||||
{% else %}
|
||||
<strong>Author</strong>{{row.founders | prepend: ": "}}
|
||||
{%endif%}
|
||||
{%endif%}
|
||||
{%if row.date != nil%} <strong>Date:</strong> ({{row.date}}){%endif%}
|
||||
{%for item in row%}
|
||||
{%if attributes contains item.first and item.last != nil %}
|
||||
{% if item.last contains ';' %}
|
||||
<strong>{{item.first|capitalize}}:</strong>
|
||||
{% assign ray = item.last | split: ';'%}
|
||||
{%for item in ray %}{%if item != " "%} {{item|strip}}{%endif%}{%endfor%}
|
||||
{%else%}
|
||||
<strong>{{item.first|capitalize}}:</strong> {{item.last}}
|
||||
{%endif%}
|
||||
{%endif%}
|
||||
{%endfor%}
|
||||
</small>
|
||||
</li>
|
||||
{% if row.text %}<blockquote>{{row.text | markdownify}}</blockquote>{%endif%}
|
||||
{%endif%}
|
||||
{% endfor %}
|
||||
</ul>
|
||||
{% endfor %}
|
||||
{%for row in site.data.content%}
|
||||
{% if row.main != page.name and row.related contains page.name %}
|
||||
{% assign count = 1 %}
|
||||
{%endif%}
|
||||
{%endfor%}
|
||||
{%if count == 1%}
|
||||
<h2 id="related">Related</h2>
|
||||
<p>From other pages on this site. (Beta)</p>
|
||||
<ul>
|
||||
{%assign attributes = "tags,market,use,sector,projects,tech,standard" | split: "," %}
|
||||
{%for row in site.data.content%}
|
||||
{% if row.main != page.name and row.type != "Company" and row.related contains page.name %}
|
||||
<li>
|
||||
{% if row.related contains ';' %}
|
||||
<strong>Relevant</strong>:{%assign related = row.related|split:';'%}
|
||||
{%assign trekker = 0%}
|
||||
{%for item in related%}
|
||||
{%assign trekker = trekker | plus: 1%}
|
||||
{%endfor%}
|
||||
{%for item in related%}
|
||||
{%if item != nil%} {{item|strip}}{%if trekker > 1%},{%assign trekker = trekker | minus: 1%}{%endif%}{%endif%}
|
||||
{%endfor%}
|
||||
{%elsif row.related == nil%}
|
||||
{%else%}
|
||||
<strong>Relevant</strong>: {{row.related}}
|
||||
{%endif%}
|
||||
{%if row.parent !=nil%}<strong>Parent: </strong>{{row.parent}}{%endif%}
|
||||
<strong>Type: </strong>{{row.type|strip|capitalize}}
|
||||
<strong>Title: </strong><a href="{{ row.link }}">{{ row.title }}</a>
|
||||
{% if row.founders !=nil%}
|
||||
{% if row.founders contains ';' %}
|
||||
<strong>Author(s)</strong>{{ row.founders | replace: ";","," | prepend: ": "}}
|
||||
{% else %}
|
||||
<strong>Author</strong>{{row.founders | prepend: ": "}}
|
||||
{%endif%}
|
||||
{%endif%}
|
||||
{%if row.date != nil%} <strong>Date:</strong> ({{row.date}}){%endif%}
|
||||
{%for item in row%}
|
||||
{%if attributes contains item.first and item.last != nil %}
|
||||
{% if item.last contains ';' %}
|
||||
<strong>{{item.first|capitalize}}:</strong>
|
||||
{% assign ray = item.last | split: ';'%}
|
||||
{%for item in ray %}{%if item != " "%} {{item|strip}}{%endif%}{%endfor%}
|
||||
{%else%}
|
||||
<strong>{{item.first|capitalize}}:</strong> {{item.last}}
|
||||
{%endif%}
|
||||
{%endif%}
|
||||
{%endfor%}
|
||||
{% if row.text %}<blockquote>{{row.text | markdownify}}</blockquote>{%endif%}
|
||||
</li>
|
||||
{%endif%}
|
||||
{%endfor%}
|
||||
</ul>
|
||||
{%endif%}
|
||||
{%endif%}
|
||||
|
|
@ -2,11 +2,13 @@
|
|||
date: 2019-03-06
|
||||
title: IBM Identity
|
||||
name: IBM
|
||||
|
||||
description: Smart identity and access management solutions for the hybrid, multicloud enterprise. Powered by AI. Backed by IBM Security®.
|
||||
excerpt: >
|
||||
IBM joined DIF because we believe it will take open community and standards to achieve the vision of self-sovereign identity. For example, members of DIF are focused on the establishment of an open web platform standard within the W3C standards organization called Decentralized Identifier (DID). A DID will provide a standard global resource naming scheme for identity.
|
||||
|
||||
There is a global Internet standard for naming resources called a uniform resource identifier or URI. When you type https://www.ibm.com into your browser, a URI ensures you always end up at IBM’s website. Similarly, we need one standard to identify an individual, as well.
|
||||
layout: single
|
||||
layout: companies
|
||||
header:
|
||||
image: /images/ibm-header.webp
|
||||
teaser: /images/ibmteaser.webp
|
||||
|
|
@ -15,31 +17,15 @@ permalink: companies/ibm/
|
|||
canonical_url: 'https://decentralized-id.com/companies/ibm/'
|
||||
redirect_from:
|
||||
- private-sector/ibm/
|
||||
- id-initiatives/ibm
|
||||
- id-initiatives/
|
||||
- id-initiatives/ibm/
|
||||
- private-sector/ibm
|
||||
- private-sector/
|
||||
categories: ["Companies"]
|
||||
tags: ["IBM","DIF","SecureKey","Indy","Sovrin Foundation","Verifiable Credentials","Mooti"]
|
||||
last_modified_at: 2019-03-06
|
||||
tags: ["DIF","SecureKey","Hyperledger","Indy","Sovrin Steward", "Sovrin Foundation","Mooti","IBM"]
|
||||
standards: ["Verifiable Credentials","DID"]
|
||||
use: [IT]
|
||||
last_modified_at: 2023-02-20
|
||||
toc: true
|
||||
---
|
||||
|
||||

|
||||
|
||||
* [Paving the Road to Self-Sovereign Identity with Blockchain, Open Standards](https://www.ibm.com/blogs/think/2017/10/self-sovereign-id-blockchain/)
|
||||
* [github.com/IBM-Blockchain-Identity](https://github.com/IBM-Blockchain-Identity) (Docker based tutorial sandbox env)
|
||||
* [How do we start tackling the existing identity problem](https://www.ibm.com/blogs/blockchain/2018/06/how-do-we-start-tackling-the-existing-identity-problem/)
|
||||
* [Swipe Right on Verifiably Credentials](https://developer.ibm.com/code/2018/05/22/swipe-right-on-verifiable-credentials/)
|
||||
* [WISeKey fully deployed its CertifyID integrating Digital Identity with Blockchain technology](https://globenewswire.com/news-release/2018/07/11/1535718/0/en/WISeKey-fully-deployed-its-CertifyID-integrating-Digital-Identity-with-Blockchain-technology.html)
|
||||
* [Mooti](https://mooti.co/) [[**D**](https://docs.mooti.co/)]
|
||||
* offers an "identity chain" technology that makes it possible to issue and revoke verified claims using elliptic curve cryptography (curve25519, secp256k1) and includes privay-enhancing features [[**ϟ**](https://www.cio.com/article/3147358/it-industry/ibm-building-blockchain-ecosystem.html)]
|
||||
* [SecureKey](http://securekey.com/): [partners with IBM](http://www-03.ibm.com/press/us/en/pressrelease/51841.wss) to enable a new digital identity and attribute sharing network based on Hyperledger Fabric blockchain.
|
||||
* [Towards Self Sovereign Identity](https://www.slideshare.net/alehors/towards-self-sovereign-identity-20180508) - A great slide-deck explaining Indy\Sovrin Architecture.
|
||||
|
||||
|
||||
## /IBM-Blockchain-Identity
|
||||
|
||||
[IBM-Blockchain-Identity/indy-tutorial-sandbox](https://github.com/IBM-Blockchain-Identity/indy-tutorial-sandbox) - Forked from brycecurtis/indy-tutorial-sandbox
|
||||
A turnkey, Docker-based sandbox that enables quick and easy exploration of Hyperledger Indy concepts.
|
||||
|
||||
[IBM-Blockchain-Identityindy-ssivc-tutorial](https://github.com/IBM-Blockchain-Identity/indy-ssivc-tutorial) - A turnkey, Docker-based tutorial for help developers get acquainted with Self-Sovereign Identity and Verifiable Credentials.
|
||||
|
||||
|
|
|
|||
|
|
@ -2,9 +2,10 @@
|
|||
date: 2019-03-08
|
||||
title: Microsoft Identity
|
||||
name: Microsoft
|
||||
description: Microsoft enables digital transformation for the era of an intelligent cloud
|
||||
excerpt: >
|
||||
Microsoft believes everyone has the right to own their digital identity, one that securely and privately stores all personal data. This ID must seamlessly integrate into daily life and give complete control over data access and use.
|
||||
layout: single
|
||||
layout: companies
|
||||
permalink: companies/microsoft/
|
||||
canonical_url: 'https://decentralized-id.com/companies/microsoft/'
|
||||
header:
|
||||
|
|
@ -15,74 +16,11 @@ redirect_from:
|
|||
- id-initiatives/microsoft/
|
||||
- id-initiatives/microsoft
|
||||
categories: ["Companies"]
|
||||
tags: ["Microsoft","DID","DIF","ION","Transmute","Consensys","WebAuthN","Blockstack","uPort","Ethereum","Bitcoin","FIDO","Mastercard","Secure Data Storage"]
|
||||
last_modified_at: 2020-11-05
|
||||
tags: ["ID2020","ID2020 Founder","VCI Founder","DID","DIF","ION","Transmute","Consensys","Blockstack","uPort","Ethereum","Bitcoin","FIDO","Mastercard","Microsoft"]
|
||||
use: ["IT","IAM","ID","SSI"]
|
||||
standards: ["WebAuthN","Secure Data Storage"]
|
||||
last_modified_at: 2023-02-20
|
||||
toc: true
|
||||
---
|
||||
|
||||

|
||||
|
||||
* [A Peek into the Future of Decentralized Identity](https://bok.idpro.org/article/id/51/)
|
||||
> As digital transformation sweeps across the globe, it has affected everyone – from citizens to employees, from corporations to governments. Digital identity is a foundational enabler for business processes in the digital economy. Decentralized identity is the next evolution of digital identity capabilities and brings with it an opportunity to streamline how people interact with other institutions, physical objects, and with one another. This paper considers the future world of decentralized identity and offers clarity around the benefits of decentralized identity, terminology, sample scenario, and a sample technical implementation, while also addressing some of the limitations of this model. This paper further grounds the reader in the current state of decentralized identity capabilities while outlining the evolution of identity practices from past to present.
|
||||
|
||||
|
||||
## News
|
||||
|
||||
> Today, we’re announcing an early preview of a [Sidetree-based DID network, called ION](https://techcommunity.microsoft.com/t5/Azure-Active-Directory-Identity/Toward-scalable-decentralized-identifier-systems/ba-p/560168) (Identity Overlay Network) which runs atop the Bitcoin blockchain based on an emerging set of open standards that we’ve developed working with many of our partners in the Decentralized Identity Foundation. This approach greatly improves the throughput of DID systems to achieve tens-of-thousands of operations per second
|
||||
|
||||
* [Introducing Element](https://medium.com/transmute-techtalk/introducing-element-328b4260e757)
|
||||
> Transmute is excited to announce Element, an implementation of the Sidetree Protocol on top of Ethereum and IPFS. This work was done in collaboration with Microsoft and Consensys under the Decentralized Identity Foundation (DIF)
|
||||
|
||||
|
||||
## didproject.azurewebsites.net
|
||||
|
||||
* [didproject.azurewebsites.net](https://didproject.azurewebsites.net/)
|
||||
* [Microsoft Azure Own your identity](https://azure.microsoft.com/en-us/overview/decentralized-identity/)
|
||||
* [didproject.azurewebsites.net/docs](https://didproject.azurewebsites.net/docs/overview.html)
|
||||
>We plan to add new technologies and features to this website over time. Here are some investments we currently have planned:
|
||||
> * DID standards & test methods - The W3C CCG has a draft spec for representing decentralized identities, allowing identities to be registered on different distributed ledgers while maintaining compatibility. To provide a reference implementation, a test DID method is built that allows temporary creation and usage of decentralized identities. This allows additional development to continue while progress is made on real DID methods.
|
||||
> * Authentication & initial APIs - Protocols for authenticating decentralized identities using public key credentials are proposed. A reference implementation with javascript APIs is built that allows a website to authenticate a decentralized identity. A sample user agent application is open sourced that demonstrates proper usage of the proposed protocols using a test DID method.
|
||||
Standardization continues
|
||||
> * Ongoing - Work continues between members of the decentralized identity foundation and other standards bodies to revise, refine, and formalize standards for decentralized identities. Topics include identifiers names & discovery, authentication protocols, storage and compute, claims and credentials, and more.
|
||||
> * Data storage in identity hubs - Identity hubs provide secure data storage for any information associated with an identity. Profile information, personal files, government issued documents, and more. Identity hubs offer users tools for controlling and reviewing access to their data, so that information can be confidently and privately shared with other parties. Data storage and retreival is based on industry standards to ensure that users have their choice of how and where to run their identity hub. Information in identity hubs can also be replicated to multiple instances of hubs to maintain the advantages of decentralization.
|
||||
> * Scaling registration of identities -Registration of identities on a distributed ledger typically requires a transaction to be submitted to the ledger's network. To offer decentralized identities to users at scale, a solution is needed to increase the throughput and or latency of an identity registration. SideTree is a proposed layer two protocol that can help address these problems and enable identity registration that works at real world scale.
|
||||
> * Key recovery mechanisms - To use decentralized identities, users must be able to secure private keys while using them to perform daily tasks and operations. Should a private key be lost or compromise, users run the risk of losing access to all of their online assests and personal data. Mechanisms are needed to help users avoid problems with their private keys and to recover from problems when they do happen.
|
||||
> * Mobile user agents - Easy to use and secure user agents are a critical component to decentralized identity. Mobile applications can help users secure their identity's private keys, respond to incoming requests, and manage access to their personal data.
|
||||
|
||||
* [DID Registration](https://didproject.azurewebsites.net/docs/registration.html)
|
||||
>The way you claim a DID and publish your public keys depends on which distributed ledger you use to register your DID. Each ledger has its own rules, formats, and quirks. Thankfully, the DID standard defines common ways to deal with DIDs, and our services expose the standard to you in a simple web API. Currently, we're developing support for the following ledgers:
|
||||
>
|
||||
>* Bitcoin
|
||||
>* Ethereum, via uPort
|
||||
>* Sovrin
|
||||
|
||||
## Whitepaper
|
||||
* [Microsoft’s strategy for Decentralized Identity](https://query.prod.cms.rt.microsoft.com/cms/api/am/binary/RE2DjfY)] **to empower every person on the planet to achieve more.**
|
||||
>Microsoft cloud identity systems already empower developers, organizations, and billions of people to work, play, and achieve more, but there’s so much more we can do to create a world where each of us, even in displaced populations, can pursue our life goals, including educating our children, improving our quality of life, and starting a business.To achieve this vision, we need to augment existing cloud identity systems with one that individuals, organizations, and devices can own so they can control their digital identity and data. This self-owned identity must seamlessly integrate into our daily lives, providing complete control over what we share and with whom we share it, and—when necessary—provide the ability to take it back. Instead of granting broad consent to countless apps and services and spreading their identity data across numerous providers, individuals need a secure, encrypted digital hub where they can store their identity data and easily control access to it.
|
||||
|
||||
## [Microsoft Identity Standards Blog](https://techcommunity.microsoft.com/t5/Identity-Standards-Blog/bg-p/IdentityStandards)
|
||||
|
||||
* [All about FIDO2, CTAP2 and WebAuthn](https://techcommunity.microsoft.com/t5/Identity-Standards-Blog/All-about-FIDO2-CTAP2-and-WebAuthn/ba-p/288910)
|
||||
> To understand how FIDO2 authenticators work, you need knowledge of two specifications in two different standards bodies. The WebAuthentication (aka WebAuthn) spec lives at W3C (where the browser makers meet) while the Client-to-Authenticator (aka CTAP2) spec lives at the FIDO Alliance (where hardware and platform folks have joined to solve the problem of Fast IDentity Online).
|
||||
* [Why does standards certification matter?](https://techcommunity.microsoft.com/t5/Identity-Standards-Blog/Why-does-standards-certification-matter/ba-p/638937)
|
||||
> It’s a good month for identity certification at Microsoft! We are excited to have achieved two important goals: OpenID Certification for Azure Active Directory and also FIDO Certification for Windows 10. You may or may not know what these particular protocols do, but even if you don’t, it’s worth talking about what these certification programs accomplish.
|
||||
* [Why WebAuthn will change the world](https://techcommunity.microsoft.com/t5/Identity-Standards-Blog/Why-WebAuthn-will-change-the-world/ba-p/482286)
|
||||
>With WebAuthn, any web entity can call a simple Javascript API and ask for a cryptographically secure credential. What happens next is pretty cool – the world’s browsers have worked with the world’s operating system makers and the world’s hardware manufacturers, so that when a website asks for a credential, the browsers work with the underlying platform to securely locate compliant local hardware and talk to it!
|
||||
* [To Understand WebAuthn, Read CredMan](https://techcommunity.microsoft.com/t5/Identity-Standards-Blog/To-Understand-WebAuthn-Read-CredMan/ba-p/339652)
|
||||
> take a cruise through the [W3C Credential Management (aka CredMan) specification](https://www.w3.org/TR/credential-management-1/) first. CredMan sets up the object model for the Credential object model that WebAuthn's PublicKeyCredential extends.
|
||||
>
|
||||
> **CredMan Base Definitions**
|
||||
>
|
||||
> CredMan unsurprisingly centers on the concept of a Credential. Actions on Credentials are requested by a relying party using JavaScript and fulfilled by a user agent (generally a browser). Credentials can be created stored, retrieved for validation by a relying party and so on. In addition to actions, CredMan defines standardized dictionaries that communicate context.
|
||||
|
||||
## History
|
||||
|
||||
|
||||
6/16 — [Microsoft Building Open Blockchain-Based Identity System With Blockstack, ConsenSys](https://bitcoinmagazine.com/articles/microsoft-building-open-blockchain-based-identity-system-with-blockstack-consensys-1464968713/)
|
||||
|
||||
[](https://www.microsoft.com/en-us/security/technology/own-your-identity)
|
||||
* [microsoft.com/en-us/security/technology/own-your-identity](https://www.microsoft.com/en-us/security/technology/own-your-identity)
|
||||
* [Mastercard, Microsoft Join Forces to Advance Digital Identity Innovations](https://newsroom.mastercard.com/press-releases/mastercard-microsoft-join-forces-to-advance-digital-identity-innovations/)
|
||||
* [Decentralized digital identities and blockchain: The future as we see it](https://www.microsoft.com/en-us/microsoft-365/blog/2018/02/12/decentralized-digital-identities-and-blockchain-the-future-as-we-see-it/)
|
||||
* [Microsoft is quietly testing a project that aims to hand people complete control over their online data](http://www.businessinsider.fr/us/microsoft-working-on-project-bali-to-give-people-control-over-data-2019-1)
|
||||
|
||||
|
||||
|
|
|
|||
|
|
@ -5,7 +5,7 @@ name: Danube
|
|||
description: The longest running firm working towards user-owned and controlled internet identity.
|
||||
excerpt: >
|
||||
This is an open-source project offering software for identity and personal data services on the Internet. The core of this project is an XDI-based Personal Data Store - a semantic database for your personal data, which always remains under your control. Applications on top of this database include the Federated Social Web, the selective sharing of personal data with organizations, and much more.
|
||||
layout: single
|
||||
layout: companies
|
||||
permalink: companies/danube-tech/
|
||||
canonical_url: 'https://decentralized-id.com/companies/danube-tech/'
|
||||
redirect_from:
|
||||
|
|
@ -17,254 +17,8 @@ header:
|
|||
image: /images/danube-header.webp
|
||||
teaser: /images/danube-teaser.webp
|
||||
categories: ["Companies"]
|
||||
tags: ["DIF","Danube Tech","XDI","DHS","DID","Verifiable Credentials","W3C","Ethereum","ERC725","Universal Resolver","OASIS","OAuth","BTCR","Indy"]
|
||||
toc_sticky: false
|
||||
last_modified_at: 2020-11-09
|
||||
last_modified_at: 2023-02-20
|
||||
toc: true
|
||||
---
|
||||
|
||||
|
||||
**Digital identity and personal data, including personal agents, semantic graphs, and blockchain.**
|
||||
|
||||
**[Website](http://danubetech.com/) • [Twitter](https://twitter.com/peacekeeper) • [GitHub](https://github.com/peacekeeper) • [Medium](https://medium.com/@markus.sabadello)**\
|
||||
**[Markus Sabadello (Peacekeeper)](http://mydata2016.org/speaker/markus-sabadello/) • [Blockchain-Identity](https://github.com/peacekeeper)**
|
||||
|
||||
> DANUBE TECH is a company working on technologies in the field of digital identity and personal data, including personal agents, semantic graphs, and decentralized identity.
|
||||
>
|
||||
> These emerging tools essentially place individuals at the center of their online relationships and transactions, and give us all the ability to create, manage, use, and destroy our online identities according to our own rules, and without delegating power to intermediaries.
|
||||
|
||||
* [A position paper on blockchain enabled identity and the road ahead](https://www.bundesblock.de/wp-content/uploads/2018/10/ssi-paper.pdf)—Identity Working Group of the German Blockchain Association [[**ϟ**](https://www.bundesblock.de/2018/10/23/position-paper-self-sovereign-identity/)]
|
||||
>In a SSI proof-of-concept during the first half of 2018, 3 banks, an insurance company, the Austrian Post, and an institution representing notaries has cooperated to implement a range of use cases based on DIDs, Verifiable Credentials, Sovrin, and the XDI protocol. The use cases included:
|
||||
> * digital ID onboarding for existing clients,
|
||||
> * SSO for new clients,
|
||||
> * sharing of KYC data between organizations,
|
||||
> * dynamic data verification (change-of-address),
|
||||
> * secure communication (e-mail with ID confirmation),
|
||||
> * change of identity service providers,
|
||||
> * personal ID verification in a peer-to-peer marketplace
|
||||
|
||||
* [Developer Showcase Series: Markus Sabadello, Danube Tech](https://www.hyperledger.org/blog/2018/08/15/developer-showcase-series-markus-sabadello-danube-tech)
|
||||
> I have worked on digital identity technologies for a long time, the question of who we are, how we present ourselves, and what do others know about us in the digital world. There’s this concept of user-centric identity, and more recently self-sovereign identity, which places individuals at the center of their online relationships and transactions, and gives us all the ability to create, manage, use, and destroy our online identities according to our own rules.
|
||||
|
||||
* [News Release: DHS S&T Awards 143K for Blockchain Interoperability Infrastructure](https://www.dhs.gov/science-and-technology/news/2019/09/26/news-release-dhs-st-awards-143k-blockchain-interoperability) • [ledgerinsights.com](https://www.ledgerinsights.com/blockchain-credentials-homeland-security-identity-danube-tech/)
|
||||
> “Danube Tech is building core interoperability infrastructure for issuers and verifiers,” said Anil John, SVIP Technical Director. “Interoperability between blockchains is enabled by using emerging World Wide Web Consortium standards to globally resolve and find information where it exists on a particular blockchain.”
|
||||
|
||||
## [Publications](https://danubetech.com/download.html)
|
||||
|
||||
### 2020
|
||||
|
||||
* [RWoT#10: Why Matrix Parameters?](https://github.com/WebOfTrustInfo/rwot10-buenosaires/blob/master/topics-and-advance-readings/why-matrix-parameters.md)
|
||||
> This enables not only self-sovereign identifiers for applications such as DID Auth or DIDComm agents, but it also enables persistent, self-sovereign URLs for identifying any arbitrary resource on the web. In order to not interfere with that, the core DID specification must not define any special uses of the traditional syntax components path, query string, and fragment, in the same way as the HTTP(S) specification does not define special uses of path, query string, and fragment.
|
||||
|
||||
### 2019
|
||||
|
||||
* [RWoT#9: DID Resolution collected diagrams](https://github.com/WebOfTrustInfo/rwot9-prague/blob/master/topics-and-advance-readings/did-resolution-collected-diagrams.md)
|
||||
> The DID Resolution spec is a work item of the W3C Credentials Community Group (CCG) that builds on the main DID spec. A version v0.1 has recently been released as part of the CCG's Work Item Process. The released v0.1 is still an early draft; work now continues on v0.2.
|
||||
>
|
||||
> The following is a collection of the diagrams that have been used so far to illustrate various key topics of DID Resolution.
|
||||
* [RWoT#9: Rubrics for Decentralization of DID Methods Creative Brief](https://github.com/WebOfTrustInfo/rwot9-prague/blob/master/topics-and-advance-readings/rubrics.md)
|
||||
> The Rubrics for Decentralization of DID Methods document (the Document) will help people evaluate real or potential DID Methods. This document outlines the collaborative aspirations of the Document's editors.
|
||||
* [RWoT#9: Gently introducing DIDs to the Mastodon/ActivityPub Fediverse](https://github.com/WebOfTrustInfo/rwot9-prague/blob/master/topics-and-advance-readings/fediverse-did-integration.md)
|
||||
> Our goal is to bring self sovereign identity concepts to the current ActivityPub fediverse as soon and as securely as possible.
|
||||
>
|
||||
> The hypothesis behind that goal is that long term stability of a federated service crucially depends on persistent trust relations across all participants (developers, admins, users) that are not distorted by the implicit hierarchical structure of a centralized reference system, such as DNS.
|
||||
* [Markus Sabadello and Infominer33 on Identity Landscape](https://kumu.io/vijarn/markus-sabadello-and-infominer33-on-identity-landscape) (Kumu Visualization)
|
||||
* [RWoT#8: Universal DID Operations](https://github.com/WebOfTrustInfo/rwot8-barcelona/blob/master/topics-and-advance-readings/Universal-DID-Operations.md)
|
||||
>Decentralized Identifiers (DIDs) have seen increasing adoption across a wide number of distributed ledger ecosystems and blockchains. This is in large part due to our ability to effectively communicate by resolving these DIDs. The process of obtaining a DID Document associated with a particular DID is outlined in the DID Resolution spec.
|
||||
>
|
||||
>A blockchain-agnostic implementation of the spec is hosted at the Decentralized Identity Foundation and is fully open-sourced. The Universal Resolver can be found at its website and also runs locally or remotely through an API. It currently supports DIDs on Sovrin, BTCR, uPort, Jolocom, Veres One, ERC-725, Blockstack, IPFS, and DNS via a number of community-contributed drivers built on top of the Universal Resolver.
|
||||
* [Markus Sabadello and Infominer33 on Identity Landscape](https://kumu.io/vijarn/markus-sabadello-and-infominer33-on-identity-landscape)
|
||||
>Combination of Markus Sabadello and Infominer33 githubs
|
||||
>
|
||||
>about Self Sovereign Identity and Identity Landscape.
|
||||
>
|
||||
>This may take longer time to load and longer time to response to commands such as showcasing control since there are a lot of elements and codes.
|
||||
|
||||
### 2018
|
||||
|
||||
* [RWoT#6: Introduction to DID Auth](https://github.com/WebOfTrustInfo/rwot6-santabarbara/blob/master/final-documents/did-auth.md)
|
||||
>The term DID Auth has been used in different ways and is currently not well-defined. We define DID Auth as a ceremony where an identity owner, with the help of various components such as web browsers, mobile devices, and other agents, proves to a relying party that they are in control of a DID. This means demonstrating control of the DID using the mechanism specified in the DID Document's "authentication" object. This could take place using a number of different data formats, protocols, and flows. DID Auth includes the ability to establish mutually authenticated communication channels and to authenticate to web sites and applications. Authorization, Verifiable Credentials, and Capabilities are built on top of DID Auth and are out of scope for this document. This paper gives on overview of the scope of DID Auth, supported protocols and flows, and the use of components of the DID Documents that are relevant to authentication, as well as formats for challenges and responses.
|
||||
* [RWoT#6: did:erc725 method](https://github.com/WebOfTrustInfo/rwot6-santabarbara/blob/master/topics-and-advance-readings/DID-Method-erc725.md)
|
||||
>Decentralized Identifiers (DIDs, see [1]) are designed to be compatible with any distributed ledger or network (called the target system). In the Ethereum community, a pattern known as ERC725 (see [2]) utilizes smart contracts for standard key management functions. We propose a new DID method that allows ERC725 identities to be treated as valid DIDs. One advantage of this DID method over others appears to be the ability to use the full flexibility of Ethereum smart contracts for key management purposes.
|
||||
* [RWoT#7: DID Resolution Topics](https://github.com/WebOfTrustInfo/rwot7-toronto/blob/master/topics-and-advance-readings/did-resolution-topics.md)
|
||||
>We know that DID Resolution is the process of obtaining the DID Document associated with a DID. Sounds simple, but what are some of the deeper questions and topics to be considered here?
|
||||
|
||||
### 2017
|
||||
|
||||
* [RWoT#4: XDI Verifiable Claims and Link Contracts](https://github.com/WebOfTrustInfo/rwot4-paris/blob/master/topics-and-advance-readings/xdi-verifiable-claims-link-contracts.md)
|
||||
>There is a high level of interest in the Rebooting-the-Web-of-Trust community and beyond in "verifiable claims", i.e. "a cryptographically non-repudiable set of statements made by an entity about another entity" (see [1]). This work foresees that "the next generation of web applications will authorize entities to perform actions based on rich sets of credentials issued by trusted parties" (see [2]).
|
||||
>
|
||||
>XDI (eXtensible Data Interchange) is a technology for modeling, storing and sharing personal and organizational identity data. One key component of this technology is the "link contract", i.e. a "data sharing agreement between the publisher of the data, called the authorizing authority, and a party who wants to access the data, called the requesting authority" (see [3]).
|
||||
>
|
||||
>XDI link contracts contain a policy tree which is used to decide if the permissions granted by the link contract can be invoked by a requesting authority. This policy evaluates conditions based on input elements such as the authorizing authority, requesting authority, and an incoming request message. Simple conditions of the policy could e.g. require the presentation of a valid password or signature.
|
||||
* [A Universal Resolver for Self-Sovereign Identifiers](https://medium.com/decentralized-identity/a-universal-resolver-for-self-sovereign-identifiers-48e6b4a5cc3c)
|
||||
>This tool fulfills a similar purpose as Bind does in the DNS system: resolution of identifiers. However, instead of working with domain names, we work with self-sovereign identifiers that can be created and registered directly by the entities they refer to. This is important, because identifiers are the basis for any identity and communications system — without identifiers, we cannot have relationships, transactions, data sharing or messaging between entities. Historically identifiers have always been assigned to us by some kind of corporate or state authority. The Universal Resolver lets us build architectures and protocols on top of identifiers that are completely self-sovereign. There is no longer a need for a central authority to issue, maintain and revoke identifiers.
|
||||
>
|
||||
>However, just having an identifier is not enough. We need some further information in order to know how to communicate with the entity represented by the identifier. The job of a “Resolver” is to discover and retrieve this further information. At a minimum, this information includes elements such as service endpoints for communicating with the entity, as well as the cryptographic keys associated with it. The Universal Resolver performs this task to enable the basic building blocks of a self-sovereign identity world.
|
||||
* [RWoT#5: First XDI Link Contract between "btcr" DID and "sov" DID](https://github.com/WebOfTrustInfo/rwot5-boston/blob/master/topics-and-advance-readings/first-xdi-link-contract-between-btcr-did-and-sov-did.md)
|
||||
>We describe an XDI link contract established between two XDI peers, one of which is identified by a btcr DID, and one by a sov DID. We believe this is the first working example of cross-DID-method data sharing and messaging.
|
||||
|
||||
|
||||
### 2016
|
||||
|
||||
* [RWoT#2: XDI Graphs in IPFS](https://github.com/WebOfTrustInfo/rwot2-id2020/blob/master/topics-and-advance-readings/XDI-Graphs-in-IPFS.md)
|
||||
>XDI (eXtensible Data Interchange) is a technology for modeling, storing and connecting any kind of personal and organizational data. Its underlying data model is a graph consisting of nodes and directed arcs. XDI is well-suited for digital identity that is distributed and heterogeneous. Through the use of mappings and connectors, XDI can be used to model even data that is not itself natively in XDI format (e.g. a Facebook profile, a government ID, or a record in a corporate database). Traditionally, XDI assumes a network topology that involves service providers and endpoints, e.g. a connection can be established between an individual and an organization through their respective endpoints.
|
||||
* [RWoT#3: JXD Examples](https://github.com/WebOfTrustInfo/rwot3-sf/blob/master/topics-and-advance-readings/JXD-Examples.md)
|
||||
>JXD is a JSON-based serialization format for the XDI graph model, designed to combine the simplicity of JSON with the semantic richness of XDI.
|
||||
>
|
||||
>An XDI graph can sometimes be serialized to JXD in different ways (some more verbose, some more compact), but deserializing a JXD back to XDI always results in the same original XDI graph. Every XDI graph can be serialized to JXD, and every JXD document can be deserialized to a valid XDI graph.
|
||||
>
|
||||
>An XDI graph is built from XDI context nodes, which form a semantic tree. In JXD, an XDI context node is represented as a JSON object, with an @id JSON object key set to the XDI context node’s address.
|
||||
|
||||
### 2015
|
||||
|
||||
* [RWoT#1: XDI, Blockstore, and BIP32](https://github.com/WebOfTrustInfo/rwot1-sf/blob/master/topics-and-advance-readings/cool-hack-xdi-blockstore-bip32.md)
|
||||
>XDI (eXtensible Data Interchange) is a semantic graph technology for modeling, accessing, and linking any data online. It is similar to RDF insofar as it is also based on triples describing a graph of nodes that represent resources (called "contexts" in XDI), properties that connect resources (called "relations" in XDI), and literals. Unlike RDF which uses opaque URIs (mostly HTTP) as identifiers and which constructs all semantics purely from the graph structure, XDI identifiers use an abstract syntax where semantics are established not only from graph structure, but also from the identifiers themselves. For example, in RDF an identifier for a person may be http://danubetech.com#markus, whereas in XDI, an identifier for a person would be =markus. XDI often assigns two or more identifiers to a resource, e.g. while =markus is considered a "reassignable XDI name", a corresponding "permanent XDI number" such as =!:uuid:91f28153-f600-ae24-91f2-8153f600ae24 may also be assigned. Simply by parsing the identifiers, some limited semantics can already be extracted ("=" stands for person, "!" stands for permanent).
|
||||
* [Decentralized Public Key Infrastructure](https://danubetech.com/download/dpki.pdf)
|
||||
>Today’s Internet places control of online identities into the hands of third-parties. Email addresses, usernames, and website domains are borrowed or "rented" through DNS, X.509, and social networks. This results in severe usability and security challenges Internet-wide. This paper describes a possible alternate approach called decentralized public key infrastructure (DPKI), which returns control of online identities to the entities they belong to. By doing so, DPKI addresses many usability and security challenges that plague traditional public key infrastructure (PKI). DPKI has advantages at each stage of the PKI life cycle. It makes permissionless bootstrapping of online identities possible and provides for the simple creation of stronger SSL certificates. In usage, it can help “Johnny” to finally encrypt thanks to its relegation of public key management to secure decentralized datastores. Finally, it includes mechanisms to recover lost or compromised identifiers.
|
||||
|
||||
### 2012
|
||||
|
||||
* [Personal Data Journal: Decentralized Architectures](https://danubetech.com/download/PDEC-Decentralized-Architectures.pdf)
|
||||
>One of the most fundamental challenges for the PDE to consider will be the design and deployment of suitable underlying architectures for realizing emerging visions around the management and use of personal data. The basic organizational structures, according to which participants of an ecosystem exchange information with each other, influence many of its fundamental properties, such as privacy, security, flexibility, discovery, or the dependencies between different actors. The possible types of architectural patterns that can be implemented are highly diverse, with centralized structures on one end of the spectrum, and fully distributed systems on the other end. On the Internet, very different forms have always existed, depending on the infrastructural layer and the concrete applications and services one looks at.
|
||||
* [Personal Data Journal: Understanding OAuth](https://danubetech.com/download/PDEC-OAuth.pdf)
|
||||
>Selecting the OAuth (“Open Authorization”) protocol as the topic for the second feature article of our Personal Data Journal is a logical choice for two reasons. Firstly, the vision of establishing an ecosystem around personal data is intrinsically linked to the topics of authorization and access control. Whether we are talking about giving individuals more privacy and more control over their personal data, or whether we are exploring new economic models to be built around it, the question of who can access what under which permissions and obligations is central to achieving them.
|
||||
* [Personal Data Journal: Privacy By Design](https://danubetech.com/download/PDEC-Privacy-By-Design.pdf)
|
||||
>The idea of an emerging Personal Data Ecosystem (PDE) is based on several different lines of thought. Ultimately the purpose of the PDE is to help us all make sense of the unprecedented amount of online personal data we observe today. It is about creating new business models and economic opportunities based on this personal data, which has been called a new currency, or asset. It will give individuals the means to control how this asset is used. In doing so, an awareness of the importance of privacy will develop on one hand and on the other privacy by design will become one of the key principles of the concrete solutions that ecosystem members are developing. In this article, we will offer a quick introduction to privacy and then move on to describe concrete resources and approaches to Privacy-By-Design, which is the idea of “baking in” privacy up front into the design of software architectures, rather than considering it a secondary or 3rd-party aspect of classic software engineering or deployment.
|
||||
* [Personal Data Journal: Startup Technology Report](https://danubetech.com/download/PDEC-Tech-Research-Phase-One-Report.pdf)
|
||||
>The Internet Society thorough our Trust and Identity Initiatives have followed with great interest the work of the user-centric developers and deployers within the Identity EcoSystem. The recent work on Personal Data offers a number of interesting choices for individual users and we are pleased to support this initial survey of some of the leading solutions currently under way. It is our hope this information will encourage additional dialogue within the community and will lead to greater interoperability and better engagement with end-users.
|
||||
|
||||
### 2011
|
||||
|
||||
* [A Federated Social Web for Peace](https://danubetech.com/download/A-Federated-Social-Web-for-Peace.pdf)
|
||||
> For a global civil society to truly work, both the architectural structure and the governance mechanisms of its communication channels must be based on civil society principles itself. This paper argues that the main promise of the Federated Social Web – in addition to the obvious advantages of improved privacy, control and resistance to manipulation – will be a network structure that deep at its core resembles civil society and is therefore a powerful instrument for a more peaceful world.
|
||||
* [Human Rights in the Information Society](https://danubetech.com/download/Human-Rights-in-the-Information-Society.pdf)
|
||||
> Much has been said about the potential threats and opportunities of modern communication technologies, and about whether they provide a liberating potential at the human level, or whether they constitute yet another mechanism for reinforcing old structures and for transferring wealth from the poor to the rich. In light of such discourses and in the best tradition of the “Golden Rule” of Human Rights, we must lay out a system of freedoms and obligations for a prosperous and just Information Society, in which we all do (not) to others what we (do not) want others to do to us.
|
||||
* [ICTs for a Global Civil Society](https://danubetech.com/download/ICTs-for-a-Global-Civil-Society.pdf)
|
||||
> Having always been closely linked to the ideal of peace, the concept of civil society has a long history as a third actor besides the state and the economy. It is a nonviolent “zone of civility” that can debate and address war and other problems. In today’s interconnected world we see the emergence of a “global civil society”, which transcends national borders and attempts to solve global challenges that established political and economic structures fail to address. This global civil society is organized like a network, just like the global communication systems that produced it are also organized like a network. However, while popular social network services such as Facebook, Twitter and Youtube are often said to be powerful tools for peace and democracy, they are in fact highly centralized services operated by for-profit companies. For a global civil society to truly work, both the architectural structure and the governance mechanisms of its communication channels must themselves be based on civil society principles.
|
||||
* [ICTs for a Global Culture of Peace](https://danubetech.com/download/ICTs-for-a-Global-Culture-of-Peace.pdf)
|
||||
> The concept of culture is closely linked to that of identity. Our identity is what defines us as an individual. Identity is complex and always in transition. It can be defined by oneself, or it can be observed by others, and it exists on multiple levels. On the micro level, our personal identity includes features that are specific to us alone, such as our name, address, phone number, or our educational and professional curriculum. On a higher level, our social identity determines our role and position within a society. It includes our overall social roles and status, our friends, and our social responsibilities such as being a parent. Finally, on the macro level, our cultural identity determines cultural features that we embody within ourselves and share with others to a more or less extent.
|
||||
* [ICTs for Citizen and Peace Journalism](https://danubetech.com/download/ICTs-for-Citizen-and-Peace-Journalism.pdf)
|
||||
>The profession of journalism has traditionally often been described as playing an important role for maintaining a strong civil society and therefore contributing to democracy and peace. Today, modern Information and Communication Technologies (ICTs) such as the Internet, cell phones and other “new media” have decisively contributed to the globalization process and had numerous impacts on social and political structures and the ways in which we interact with each other world-wide1. These technologies have greatly transformed the way in which information is being generated, processed, transmitted, interlinked and received. As a medium, they are cheaper, faster and more interactive than more traditional media such as radio or television. It is therefore obvious that the introduction and widespread availability of modern ICTs have also in multiple ways affected the field of journalism, a field in which the creation, handling and publishing of information lie at the very core of activities.
|
||||
* [ICTs and Democratic Processes](https://danubetech.com/download/Democratic-Processes-and-ICTs.pdf)
|
||||
> It is interesting to note that the very idea of establishing world peace through a global communication system is not new. With the introduction of the telegraph 200 years ago, as well as with the introduction of the communications satellite 50 years ago, there was a general sense that such technologies would overcome barriers of space and time, and therefore enable all peoples of the world to communicate with each other at a new level, which would enable the democratic solving of conflicts and therefore lead to lasting peace.
|
||||
>
|
||||
> This paper is an attempt to first quickly establish the link between democracy and peace (see section 2), to discuss the instrument of voting (see section 3), and then to touch on how democratic processes can be supported by ICTs (see section 4), as well as on how democratic processes occur within ICTs themselves (see section 5). Finally there will be some reservations and criticism (see section 6) as well as a conclusion (see section 7).
|
||||
* [Scenarios: ICTs for Peace and Conflict in 2020](https://danubetech.com/download/Scenarios_-ICTs-for-Peace-and-Conflict-in-2020.pdf)
|
||||
> This paper is an attempt to apply the Scenario Building technique to consider the role that ICTs might have for peace and conflict in the year 2020. This chosen topic is especially challenging for two reasons: First, hardly any field moves as fast as modern ICTs. The speed and unpredictability of achievements in computer technology and the Internet have again and again astonished both the general public and professional analysts. Second, when trying to make statements about the future role of technology, there is always a general tendency to emotional debate and to overstating their influence. For example, with the introduction of the telegraph 200 years ago, as well as with the introduction of the communications satellite 50 years ago, there was a general sense that such technologies would overcome barriers of space and time, and therefore enable all peoples of the world to communicate with each other at a new level, which would avoid conflicts altogether and lead to a perpetual peace.
|
||||
* [Oppression and Liberation with Social Networks](https://danubetech.com/download/Oppression-and-Liberation-with-Social-Networks.pdf)
|
||||
>**"Slacktivism" or NewTool forPolitical Change?**
|
||||
>Web-based activism platforms like Avaaz.org claim to herald a new era of global citizen empowerment for political change. Critics object that theymight do moreharm thangood. Whatare their arguments?
|
||||
>
|
||||
>In today’s "global village", the Internet has made it possible to distribute more information to a larger number of people in less time than ever before. This development has not spared social and political movements: web-based activ-ism platforms have emerged which aim at turning large-scale public attention towards a causein order to transform it into pressure on decision makers. The impact of these communities, how-ever,is controversial: While proponents hail them as a powerful new tool of bringing about change,critics hold that they not only lack effectiveness, but may even be harmful to citizen engagement
|
||||
* [Rationale and Design for the Peace Box](https://danubetech.com/download/Rationale-and-Design-for-the-Peace-Box.pdf)
|
||||
> This thesis offers a summary of different lines of thought on how Information and Communication Technologies (ICTs) can be used for promoting the ideal of peace, for example by helping to manage a crisis, by supporting development and education, by overcoming authoritaran regimes, or by promoting a global civil society and global culture of peace. After introducing these ideas, the concept of a „Peace Box“ is presented, which is a small computer-like device that can be set up in any home or office to provide applications and services for actively supporting the various visions of using ICTs for peace.
|
||||
* [The Role of New Media for the Democratization Processes in the Arab World (Article)](https://danubetech.com/download/The-Role-of-New-Media-for-the-Democratization-Processes-in-the-Arab-World-Article.pdf)
|
||||
>Reflections on the Role of Civil Society, Human Rights and New Media in the Transformation Processes
|
||||
* [The Role of New Media for the Democratization Processes in the Arab World (Presentation)](https://danubetech.com/download/The-Role-of-New-Media-for-the-Democratization-Processes-in-the-Arab-World-Presentation.pdf)
|
||||
|
||||

|
||||
|
||||
### 2010
|
||||
|
||||
* [Potential of ICTs for Peace](https://danubetech.com/download/Potential-of-ICTs-for-Peace.pdf)
|
||||
> Information and Communication Technologies (ICTs) have greatly transformed societies, cultures and economies as well as created both new opportunities and threats for humankind. The academic field of Peace and Conflict Studies with its inherent character of being based on concrete values rather than striving to always be objective on all accounts is especially suited and challenged to explore how ICTs should be judged and used when it comes to working toward an ideal – the ideal of peace.
|
||||
* [Potential of ICTs for Conflict](https://danubetech.com/download/Potential-of-ICTs-for-Conflict.pdf)
|
||||
> Following Sigmund Freud’s concept of the two forces Eros and Thanatos – a drive for creation and a drive for destruction which both live in all of us, the Internet has often been described as a neutral tool which can be used for good or evil, just like a hammer can be used to build a house or to murder a person. When the Internet became widely available in mainstream society during the 1990s, the fast spreading of this then new technology sparked strong reactions on both ends of the spectrum, ranging from utopist hopes that new levels of democracy and transparency would lead to a more peaceful and just world, to the fear that its effects on humanity would threaten political and social orders world-wide.
|
||||
* [Comparing terrorist and Internet networks](https://danubetech.com/download/Comparing-terrorist-and-Internet-networks.pdf)
|
||||
> The network, stronger than the node, Can circumvent a failing part, Security and control code keep alive the network’s heart. But what if every spark goes dark, abandons network, node and core, what if they cease to light the night, because the people send no more?
|
||||
|
||||
## On Github
|
||||
|
||||
* [projectdanube/indy-sdk-java](https://github.com/projectdanube/indy-sdk-java) - Java binding to the native Indy SDK
|
||||
* [projectdanube/blockstack-cli-java](https://github.com/projectdanube/blockstack-cli-java) - Java client for Blockstore
|
||||
|
||||
### XDI
|
||||
|
||||
>[XDI.org](https://xdi.org) is a non-profit public trust organization whose purpose is to provide public infrastructure for digital identity, security, and privacy using the open standard XDI semantic data interchange protocol developed by the OASIS XDI Technical Committee.
|
||||
* [projectdanube/xdi-tutorial](https://github.com/projectdanube/xdi-tutorial) - XDI Tutorial
|
||||
* [projectdanube/XDINinja-swing](https://github.com/projectdanube/XDINinja-swing) - XDI-enabled standalone client application
|
||||
* [projectdanube/xdi2-tools](https://github.com/projectdanube/xdi2-tools) - XDI2 maintenance and other tools
|
||||
* [projectdanube/xdi2-connector-personal](https://github.com/projectdanube/xdi2-connector-personal) - A connector plugin for the XDI2 server that maps data from Personal.com to XDI
|
||||
* [projectdanube/xdi2-docker](https://github.com/projectdanube/xdi2-docker) - Dockerfiles for XDI2
|
||||
* [projectdanube/xdi2-connect-buttonbuilder](https://github.com/projectdanube/xdi2-connect-buttonbuilder) - "Button Builder" component for the XDI Connect protocol
|
||||
|
||||
#### Libraries
|
||||
|
||||
* [projectdanube/xdi2](https://github.com/projectdanube/xdi2) - XDI2 general purpose library and server
|
||||
* [projectdanube/xdi-js](https://github.com/projectdanube/xdi-js) - XDI client library for JavaScript
|
||||
* [projectdanube/xdi2-connect-core](https://github.com/projectdanube/xdi2-connect-core) - Shared library for the XDI Connect protocol
|
||||
|
||||
#### Integrations
|
||||
|
||||
* [projectdanube/xdi2-bdb](https://github.com/projectdanube/xdi2-bdb) - Support for using BDB as XDI2 backend storage
|
||||
* [projectdanube/xdi2-mongodb](https://github.com/projectdanube/xdi2-mongodb) - Support for using MongoDB as XDI2 backend storage
|
||||
* [projectdanube/xdi2-server-heroku](https://github.com/projectdanube/xdi2-server-heroku) - XDI2 Server deployed via Heroku
|
||||
* [projectdanube/xdi2-redis](https://github.com/projectdanube/xdi2-redis) - Support for using Redis as XDI2 backend storage
|
||||
* [projectdanube/xdi2-tor](https://github.com/projectdanube/xdi2-tor) - Integration of XDI and Tor
|
||||
* [projectdanube/xdi2-ipfs](https://github.com/projectdanube/xdi2-ipfs) - Integration of XDI and IPFS
|
||||
* [projectdanube/withsqlite](https://github.com/projectdanube/withsqlite) - A module for a python dict that back ends on an sqlite3 database. It's bit like shelve but with json and sqlite3.
|
||||
- Forked from jvasile/withsqlite
|
||||
|
||||
#### Configuration
|
||||
|
||||
* [projectdanube/xdi2-selfhosted](https://github.com/projectdanube/xdi2-selfhosted) - A configuration profile of the XDI2 server for self-hosting a single XDI graph.
|
||||
* [projectdanube/xdi2-csp](https://github.com/projectdanube/xdi2-csp) - A configuration profile of the XDI2 server for hosting a dynamic number of XDI graphs.
|
||||
* [projectdanube/xdi2-registry](https://github.com/projectdanube/xdi2-registry) -
|
||||
A configuration profile of the XDI2 server for hosting a registry of XDI names and XDI numbers.
|
||||
|
||||
#### Examples
|
||||
|
||||
* [projectdanube/xdi2-example-messaging](https://github.com/projectdanube/xdi2-example-messaging) - XDI2 Examples: Basic messaging functionality.
|
||||
* [projectdanube/xdi2-example-advanced-server](https://github.com/projectdanube/xdi2-example-advanced-server) - XDI2 Examples: Setting up advanced XDI servers.
|
||||
* [projectdanube/xdi2-example-core](https://github.com/projectdanube/xdi2-example-core) - XDI2 Examples: Simple uses of the core functionality.
|
||||
* [projectdanube/xdi2-example-client](https://github.com/projectdanube/xdi2-example-client) - XDI2 Examples: Writing XDI client applications.
|
||||
* [projectdanube/xdi2-example-secp256k1-server](https://github.com/projectdanube/xdi2-example-secp256k1-server) - Example XDI server using cid-2 cryptographic XDI numbers.
|
||||
* [projectdanube/xdi2-example-ec25519-server](https://github.com/projectdanube/xdi2-example-ec25519-server) - Example XDI server using cid-1 cryptographic XDI numbers.
|
||||
* [projectdanube/xdi2-connect-acmenews](https://github.com/projectdanube/xdi2-connect-acmenews) - +acmenews XDI2 demo
|
||||
* [projectdanube/xdi2-connect-leshop](https://github.com/projectdanube/xdi2-connect-leshop) - +leshop XDI2 demo
|
||||
* [projectdanube/xdi2-example-secp256k1-client](https://github.com/projectdanube/xdi2-example-secp256k1-client) - Example XDI client using cid-2 cryptographic XDI numbers.
|
||||
* [projectdanube/xdi2-example-ec25519-client](https://github.com/projectdanube/xdi2-example-ec25519-client) - Example XDI client using cid-1 cryptographic XDI numbers.
|
||||
|
||||
#### Plugins
|
||||
|
||||
* [projectdanube/xdi2-crypto-secp256k1](https://github.com/projectdanube/xdi2-crypto-secp256k1) - This is an secp256k1 crypto plugin for the XDI2 client and server.
|
||||
* [projectdanube/xdi2-crypto-ec25519](https://github.com/projectdanube/xdi2-crypto-ec25519) - This is an Ed25519 crypto plugin for the XDI2 client and server.
|
||||
* [projectdanube/xdi2-connector-facebook](https://github.com/projectdanube/xdi2-connector-facebook) - A connector plugin for the XDI2 server that maps data from Facebook to XDI
|
||||
* [projectdanube/xdi2-connector-meeco](https://github.com/projectdanube/xdi2-connector-meeco) - A connector plugin for Meeco
|
||||
* [projectdanube/XDINinja-plugin](https://github.com/projectdanube/XDINinja-plugin) - A browser plugin that is like "Twitter for data"
|
||||
* [projectdanube/xdi2-connector-cozy](https://github.com/projectdanube/xdi2-connector-cozy) - A connector plugin for CozyCloud
|
||||
* [projectdanube/xdi2-filesys](https://github.com/projectdanube/xdi2-filesys) - Plugin for an XDI2 server to integrate with a local filesystem
|
||||
|
||||
#### Aeternam
|
||||
|
||||
* [projectdanube/aeternam-xdi-sncf](https://github.com/projectdanube/aeternam-xdi-sncf) - Aeternam PNR Demo: SNCF
|
||||
* [projectdanube/aeternam-xdi-db](https://github.com/projectdanube/aeternam-xdi-db) - Aeternam PNR Demo: Deutsche Bahn
|
||||
* [projectdanube/aeternam-xdi-tests](https://github.com/projectdanube/aeternam-xdi-tests) - XDI experimentation for ÆTERNAM / ÆVATAR
|
||||
* [projectdanube/aeternam-xdi-maria](https://github.com/projectdanube/aeternam-xdi-maria) - Aeternam PNR Demo: Maria
|
||||
* [projectdanube/aeternam-xdi-webshop](https://github.com/projectdanube/aeternam-xdi-webshop) - Aeternam PNR Demo: Webshop
|
||||
* [projectdanube/aeternam-xdi-oebb](https://github.com/projectdanube/aeternam-xdi-oebb) - Aeternam PNR Demo: ÖBB
|
||||
|
||||
#### XDI Cloud
|
||||
|
||||
* [projectdanube/xdi2-cloudcards](https://github.com/projectdanube/xdi2-cloudcards) - XDI Cloud Card Viewer
|
||||
* [projectdanube/xdi2-messenger](https://github.com/projectdanube/xdi2-messenger) - XDI Cloud Messenger
|
||||
* [projectdanube/xdi2-manager](https://github.com/projectdanube/xdi2-manager) - XDI Cloud Manager
|
||||
* [projectdanube/xdi2-pixel](https://github.com/projectdanube/xdi2-pixel) - Tool to translate a personal cloud policy language (Pixel) to XDI link contracts.
|
||||
|
||||
#### XDI Server Deployed Via
|
||||
|
||||
* [projectdanube/xdi2-server-grizzly](https://github.com/projectdanube/xdi2-server-grizzly) - XDI2 Server deployed via Grizzly
|
||||
* [projectdanube/xdi2-server-mina](https://github.com/projectdanube/xdi2-server-mina) - XDI2 Server deployed via Apache MINA
|
||||
* [projectdanube/xdi2-server-netty](https://github.com/projectdanube/xdi2-server-netty) - XDI2 Server deployed via netty
|
||||
* [projectdanube/xdi2-server-undertow](https://github.com/projectdanube/xdi2-server-undertow) - XDI2 Server deployed via Undertow
|
||||
* [projectdanube/xdi2-server-vertx](https://github.com/projectdanube/xdi2-server-vertx) - XDI2 Server deployed via vert.x
|
||||
|
||||
#### Sevices
|
||||
* [projectdanube/xdi2-connect-service](https://github.com/projectdanube/xdi2-connect-service) - This is a "Connect Service" component for the XDI Browser binding.
|
||||
* [projectdanube/neustar-discovery-service](https://github.com/projectdanube/neustar-discovery-service) - Neustar XDI Discovery Service based on XRI Resolution
|
||||
- Forked from neustarpc/neustar-discovery-service
|
||||
* [projectdanube/xdi2-connect-auth-service-war](https://github.com/projectdanube/xdi2-connect-auth-service-war) - "Authorization Service" for the XDI Connect protocol, packaged as .WAR file
|
||||
* [projectdanube/xdi2-connect-service-war](https://github.com/projectdanube/xdi2-connect-service-war) - "Connect Service" for the XDI Connect protocol, packaged as .WAR file
|
||||
* [projectdanube/xdi-grapheditor](https://github.com/projectdanube/xdi-grapheditor) - An XDI Graph Editor
|
||||
-Forked from neustar/xdi-grapheditor
|
||||
* [projectdanube/xdi2-connect-auth-service](https://github.com/projectdanube/xdi2-connect-auth-service) - This is a "Connect Auth Service" component for the XDI Browser binding.
|
||||
|
|
|
|||
|
|
@ -1,71 +1,22 @@
|
|||
---
|
||||
title: Digital Bazaar
|
||||
layout: single
|
||||
name: DigitalBazaar
|
||||
layout: companies
|
||||
description: Leaders in the creation of decentralized digital identity for the Web.
|
||||
excerpt: >
|
||||
We pioneer payment, identity, and credential technologies that will power the next generation Web. We have been heavily involved in Web standards for over a decade, participate in cutting edge research and development, and contribute to the open source community.
|
||||
toc: false
|
||||
permalink: companies/digital-bazaar/
|
||||
canonical_url: 'https://decentralized-id.com/companies/digital-bazaar/'
|
||||
categories: ["Companies"]
|
||||
tags: ["Digital Bazaar","DHS","Veres One","DID","JSON-LD","Encrypted Data Vaults","W3C","Verifiable Credentials","GS1","SecureKey","TradeLens","Linked Data"]
|
||||
last_modified_at: 2020-11-04
|
||||
tags: ["IETF","Web Payments IG","VCTF","CCG","DHS","Veres One","W3C","GS1","SecureKey","TradeLens","Sovrin Steward","Founding Sovrin Steward","USC&B"]
|
||||
use: ["ID", "Payments"]
|
||||
standards: ["XHTML+RDFa","HTML5+RDFa","Semantic Web","OpenID Connect","WebID","JSON-LD","RDFa","Verifiable Credentials","DID"]
|
||||
tech: ["Encrypted Data Vaults","Linked Data"]
|
||||
last_modified_at: 2023-02-20
|
||||
toc: true
|
||||
header:
|
||||
teaser: /images/digital-bazaar-teaser.webp
|
||||
published: false
|
||||
---
|
||||
|
||||

|
||||
|
||||
* [Digital Bazaar](https://digitalbazaar.com/) [[twitter](https://twitter.com/digitalbazaar)] [[github](https://github.com/digitalbazaar)]
|
||||
> We have over a decade of extensive experience with web standards at the World Wide Web Consortium (W3C) and the Internet Engineering Task Force including leadership roles in the Web Payments Interest Group as well the Verifiable Claims Task Force and the Credentials Community Group at the W3C.
|
||||
>
|
||||
> Digital Bazaar is deeply involved in the latest Web research and development standards groups including XHTML+RDFa, HTML5+RDFa, Semantic Web, OpenID Connect, and WebID.
|
||||
>
|
||||
> Digital Bazaar also oversees technical development of core Web technologies across a wide variety of technology areas and has been a primary driving force in getting open identity and Linked Data technologies like JSON-LD and RDFa adopted at companies like Google, Microsoft, Yahoo!, Facebook and agencies in the US Federal Government.
|
||||
|
||||
* [Veres.io](https://veres.io/)
|
||||
> Veres is a credentialing platform that uses Verifiable Claims technology to digitize any credential that can be stored in a physical wallet. Veres enables more secure and efficient exchange of customer and employee credentials (ID cards, digital offers, receipts, tickets) across a wide variety of industries (government, education, healthcare, financial services). Other benefits include reduced risk and easier regulatory compliance.
|
||||
|
||||
* [NAFTA/CAFTA Proof of Concept Overview & Results](https://www.cbp.gov/sites/default/files/assets/documents/2019-Oct/Final-NAFTA-CAFTA-Report.pdf)
|
||||
> A joint effort was spearheaded by Customs and Border Protection (CBP), Department of Homeland Security (DHS) and private sector organizations. The POC specifically tested the feasibility of the technology for receiving certificate of origin (CO) data and conducting free trade agreement (FTA) origin verifications.\
|
||||
> [...]\
|
||||
> **Appendix C – Digital Bazaar: NAFTA/CAFTA POC Findings**\
|
||||
> The goal of the NAFTA/CAFTA POC was to evaluate the application of Blockchain technology to the Entry Summary submission process with a specific focus on submitting the Certificate of Origin and enabling content integrity verification before it is requested by a CBP Import Specialist.
|
||||
|
||||
## Projects
|
||||
|
||||
Digital Bazaar founder, Manu Sporney, proposed the [W3C Credentials Community Group](http://web.archive.org/web/20181206060143/https://www.w3.org/community/credentials/charter-20140808/) in 2014.
|
||||
> "to forge a path for a secure, decentralized system of credentials that would empower both individual people and organizations on the Web to store, transmit, and receive digitally verifiable proof of qualifications and achievements."
|
||||
|
||||
* [Veres.One](https://veres.one/summary/) A Globally Interoperable Network for Identity
|
||||
> Digital Bazaar is the Founder, and is the company that created the Veres One Blockchain technology and has been spearheading work on payments, identity, and blockchain for the Web for over 14 years. Manu Sporny, the CEO, and Dave Longley, the CTO, have co-invented numerous technologies like Decentralized Identifiers (DIDs), Verifiable Credentials, Linked Data Signatures, the Web Ledger protocol, JSON-LD, and a variety of other technologies broadly deployed by large multinational organizations such as Google, Microsoft, Yandex, and the BBC.
|
||||
|
||||
* [Encrypted Data Vaults](https://digitalbazaar.github.io/encrypted-data-vaults/)
|
||||
> We store a significant amount of sensitive data online, such as personally identifying information (PII), trade secrets, family pictures, and customer information. The data that we store is often not protected in an appropriate manner. This specification describes a privacy-respecting mechanism for storing, indexing, and retrieving encrypted data at a storage provider. It is often useful when an individual or organization wants to protect data in a way that the storage provider cannot view, analyze, aggregate, or resell the data. This approach also ensures that application data is portable and protected from storage provider data breaches.
|
||||
|
||||
## DHS Funding
|
||||
|
||||
* [DHS S&T Awards $1.3 Million to Small Businesses for Cyber Security Research and Development](https://www.dhs.gov/science-and-technology/news/2016/08/12/news-release-dhs-st-awards-13-million-small-businesses-cyber) - August 12, 2016
|
||||
> WASHINGTON —The Department of Homeland Security (DHS) Science and Technology Directorate (S&T) has awarded $1.3 million to 13 small businesses for the development of new cyber security technology.\
|
||||
> [...]\
|
||||
> 1. Applicability of Blockchain Technology to Identity Management and Privacy Protection: The goal of this topic is to use blockchain technology, which centralizes and validates new entries added into an existing data field to support identity verification. Awardees are:
|
||||
>
|
||||
> Digital Bazaar, Inc., Blacksburg, Virginia, is developing a Linked Data ledger format and architecture to demonstrate how to publish identity credentials.
|
||||
* [DHS S&T awards $9.7M for 13 Phase II Small Business Innovation Research Projects](https://www.dhs.gov/science-and-technology/news/2017/05/02/press-release-dhs-st-awards-97m-13-phase-ii-sbir-projects) - May 2, 2017
|
||||
> Each Phase II award contract received approximately $750,000 to develop a prototype based on the feasibility of the technologies demonstrated in the Phase I effort, which were completed in November 2016.\
|
||||
> [...]\
|
||||
> • Digital Bazaar (Blacksburg, VA), Verifiable Claims and Fit-for-Purpose Decentralized Ledgers
|
||||
* [DHS S&T Awards $750K to Virginia Tech Company for Blockchain Identity Management Research and Development](https://www.dhs.gov/science-and-technology/news/2017/09/25/news-release-dhs-st-awards-750k-virginia-tech-company) - September 25, 2017
|
||||
> WASHINGTON— The Department of Homeland Security (DHS) Science and Technology Directorate (S&T) has awarded a $749,241 Small Business Innovation Program (SBIR) contract to Digital Bazaar, Inc. to develop fit-for-purpose blockchains for identity and access management.
|
||||
>
|
||||
> Under the SBIR Phase II contract, the Blacksburg, Virginia-based technology company will develop a flexible software ecosystem that combines fit-for-purpose distributed ledger technology, digital credentials and digital wallets to address a wide variety of identity management and online access use cases for the Homeland Security Enterprise (HSE).
|
||||
* [DHS Awards $199K for Blockchain Credential Lifecycle Management](https://www.dhs.gov/science-and-technology/news/2019/11/14/news-release-dhs-awards-199k-blockchain-tech) November 14, 2019
|
||||
> Digital Bazaar Phase 1 award project “Interoperable Enterprise Identity and Credential Life-cycle Management” will enhance their existing product offering that supports emerging global World Wide Web Consortium (W3C) security, privacy and interoperability standards such as Decentralized Identifiers and Verifiable Credentials with enterprise workforce and credential lifecycle management features. Digital Bazaar proposes to build out its digital credentialing and blockchain application solution to build a viable credentialing product for large organizations with the long-term goal to bring its customized solution to market.
|
||||
|
||||
## SecureKey Partnership
|
||||
|
||||
* [Digital Bazaar and SecureKey Join Forces to Develop Global Standards for Organizational Identity](https://security.world/digital-bazaar-and-securekey-join-forces-to-develop-global-standards-for-organizational-identity/)
|
||||
> Digital Bazaar and SecureKey Technologies recently announced a strategic collaboration to leverage new digital identity standards intended to enhance existing paper-based identity verification processes.
|
||||
>
|
||||
> Both companies join a growing web of technology providers —including GS1 US and TradeLens— that are working together to improve data sharing and collaboration through blockchain-based approaches and innovative authorization technologies.
|
||||
""
|
||||
|
|
@ -5,51 +5,20 @@ name: Evernym
|
|||
description: The creators of Sovrin and Hyperledger Indy
|
||||
excerpt: >
|
||||
The world’s leading platform for verifiable credentials. Build and deploy self-sovereign identity solutions, with the technology and go-to-market resources powering the largest implementations of digital credentials in production.
|
||||
layout: single
|
||||
layout: companies
|
||||
header:
|
||||
image: /images/evernym-header.webp
|
||||
teaser: /images/evernym-teaser.webp
|
||||
permalink: companies/evernym/
|
||||
canonical_url: 'https://decentralized-id.com/companies/evernym/'
|
||||
categories: ["Companies","Sovrin Foundation"]
|
||||
tags: ["Evernym","DHS","Indy","DID","Respect Network","Trust over IP","Sovrin Foundation","DIF","Verifiable Credentials","ATB","IOTA"]
|
||||
toc_sticky: false
|
||||
last_modified_at: 2020-11-02
|
||||
categories: ["Companies"]
|
||||
|
||||
tags: ["Evernym","DHS","Indy","Respect Network","Trust over IP","Sovrin Foundation","DIF","ATB","IOTA"]
|
||||
standards: ["Verifiable Credentials","DID"]
|
||||
use: ["ID","privacy","security"]
|
||||
tech: ["Sovrin","Indy"]
|
||||
last_modified_at: 2023-02-20
|
||||
toc: true
|
||||
---
|
||||
|
||||

|
||||
|
||||
* [Evernym - About](https://www.evernym.com/about-evernym/)
|
||||
> Evernym was founded in 2013 to solve the digital identity crisis. We envisioned a world where consumers are in complete control of their digital identity, where privacy is a basic human right, and where consumers and organizations can foster a new relationship rooted in trust.
|
||||
* [Identity System Essentials](https://www.evernym.com/wp-content/uploads/2017/02/Identity-System-Essentials.pdf) by Samuel M. Smith Ph.D. and Dmitry Khovratovich Ph.D (March 2016)
|
||||
> The purpose of this white paper is to describe the essential characteristics of an identity system that provides sovereignty, security and privacy. Here the meaning of identity is derived from the characteristics of the identity system, that is, what the identity system provides. Instead of defining identity a priori, this white paper describes an identity system and then defines identity within the context of that identity system. Many of the features of the identity system has been influenced and inspired other proposed systems such as Open Reputation. This paper argues that an identity system that simultaneously provides a high degrees of sovereignty, security and privacy is best obtained via an open platform that employs distributed consensus protocols and modern cryptographic techniques.
|
||||
* [Sovrin Foundation Launches First Dedicated Self-Sovereign Identity Network](https://www.prnewswire.com/news-releases/sovrin-foundation-launches-first-dedicated-self-sovereign-identity-network-300336702.html)
|
||||
> LONDON, Sept. 29, 2016 /PRNewswire-USNewswire/ -- Evernym, Inc. announced today at the Ctrl-Shift Personal Information Economy conference that it has donated the intellectual property for the Sovrin Identity Network—the world's first and only dedicated self-sovereign identity platform—to a newly-formed nonprofit organization. The Sovrin Foundation, which is run by a group of internationally recognized identity experts, has a mission to empower everyone with a digital identity which they fully own and control.
|
||||
* [Hyperledger Welcomes Project Indy](https://www.hyperledger.org/blog/2017/05/02/hyperledger-welcomes-project-indy)
|
||||
> The Indy code base, originally developed by Evernym, was donated to the Sovrin Foundation to establish a strong open source foundation for the Sovrin Network. The Sovrin Foundation has been building a global community of developers who are passionate about Independent Identity and the economic and social benefits it brings to both individuals and enterprises.
|
||||
>
|
||||
> Now the contribution of Indy to Hyperledger takes the next step in that process, opening up Project Indy to the entire Hyperledger family of developers. Our hope is to attract even more developers who want to unleash the transformative power of digital identity that is truly decentralized, self-sovereign, and independent of any silo. We would also like to explore direct synergies with the identity management goals and requirements of the other Hyperledger projects.
|
||||
* [Evernym releases a Credential Exchange SDK](https://www.evernym.com/blog/open-source-tools-for-creating-digital-identities/)
|
||||
> For Evernym to achieve our mission, we need:
|
||||
> - The Hyperledger Indy open source project to be an innovative and stable platform for building distributed identity networks.
|
||||
> - The Sovrin Foundation to be successful in running a global public utility for self-sovereign identity.
|
||||
> - Independent developers and businesses to build solutions that are easily adopted by people from every walk of life.
|
||||
> To meet these goals, we recently released [our library for Verifiable Credential eXchange](http://github.com/evernym/sdk) (libVCX) under a permissive open source license.
|
||||
* [Evernym Joins Hyperledger](https://www.evernym.com/blog/evernym-joins-hyperledger/)
|
||||
> Today it was officially announced that Evernym has joined Hyperledger. It may strike readers familiar with our history as odd to learn that we’ve just now officially become part of the effort, since we are the inventors of Hyperledger Indy, one of the five Hyperledger projects. But this is how it’s worked out.\
|
||||
> [...]\
|
||||
> in the fall of 2015 we decided to find the best way to make the ledger truly independent, and recognized that the solution was to give it away. At the time we didn’t know exactly what that meant, apart from the fact that we would be turning the ledger into a global public utility upon which any entity (including future Evernym competitors) could build their own SSI applications.
|
||||
* [Evernym and IBM team up to accelerate adoption of self-sovereign identity](https://www.evernym.com/blog/evernym-and-ibm-team-up/)
|
||||
> In my previous posts, I highlighted the Job-Creds POC — a self-sovereign identity (SSI) collaboration between Evernym, IBM, and others, and most recently introduced Evernym’s Accelerator program. In this article, I’m excited to introduce an expanded partnership with IBM
|
||||
* [Evernym accepted into Cohort 5 of the FCA’s Regulatory Sandbox](https://www.evernym.com/blog/evernym-accepted-into-fca-regulatory-sandbox/)
|
||||
> We’re excited to announce that Evernym has been accepted into the fifth cohort of the Financial Conduct Authority’s (FCA) Regulatory Sandbox. The Financial Conduct Authority is the conduct regulator for 58,000 financial services firms and financial markets in the UK and the prudential regulator for over 18,000 of those firms.
|
||||
* [Introducing the Alberta Credentials Ecosystem](https://www.evernym.com/blog/alberta-credentials-ecosystem/)
|
||||
> The initiative is driven by ATB Financial, a Crown corporation owned by the province of Alberta that provides financial services to over 750,000 Albertans, with the support of Evernym, a leading decentralized identity solutions provider. A wide range of sectors and organizations are already involved, including the cities of Calgary and Edmonton, the Alberta Blue Cross, Telus, the Northern Alberta Institute of Technology (NAIT), the Southern Alberta Institute of Technology (SAIT), the University of Calgary, and a number of others from around the province to be announced soon.
|
||||
* [Meet Connect.Me, the first Sovrin-based digital wallet](https://www.evernym.com/blog/connect-me-sovrin-digital-wallet/)
|
||||
> Today, we’re proud to say we are one step closer to a world of self-sovereignty—to a world where anyone can take back ownership of their digital identity—with the “general availability” release of Connect.Me, the first digital wallet app built on Sovrin.
|
||||
* [Staying True to SSI Principles: Our Concerns about GADI](https://www.evernym.com/blog/ssi-principles-our-concerns-about-gadi/)
|
||||
> While appearing to march under the banner of self-sovereign or “decentralized identity,” several aspects of the press release and the DID Alliance website are strikingly opposed to the very essence of what decentralized identity is all about. We want to call out these concerns, not as a criticism of GADI or the DID Alliance, but as a way to encourage dialog on how the industry can move forward with a framework for identity that’s truly decentralized and accessible for all.
|
||||
* [Launching the Trust over IP Foundation & What It Means For Portable, Digital Identity](https://www.evernym.com/blog/trust-over-ip-foundation/)
|
||||
> Today, Evernym and 28 other founding member organizations launched the Trust over IP Foundation, a new project hosted by the Linux Foundation to enable the trustworthy exchange and verification of data between any two parties on the Internet.
|
||||
>
|
||||
> The ToIP Foundation’s mission is to provide a robust, common standard that gives people and businesses the confidence that data is coming from a trusted source, allowing them to connect, interact, and innovate at a speed and scale not possible today.
|
||||
|
|
@ -1,43 +1,23 @@
|
|||
---
|
||||
date: 2020-11-02
|
||||
title: Factom Inc.
|
||||
name: Accumulate
|
||||
description:
|
||||
title: Accumulate Network (Was Factom Inc.)
|
||||
description: "Accumulate’s story starts with the founding of Factom in 2014, a data publishing layer atop major blockchains."
|
||||
excerpt: >
|
||||
Established in 2014, the founders recognized bitcoin’s limitations to be a practical blockchain for Enterprise data solutions. Generally, distributed records, information and documents have been difficult to protect, challenging to synchronize, and impossible to truly verify because of the manual effort involved. In response to these challenges, we built the Factom blockchain as open source, reaching full decentralization in May 2018.
|
||||
layout: single
|
||||
permalink: companies/factom/
|
||||
canonical_url: 'https://decentralized-id.com/companies/factom/'
|
||||
The Accumulate protocol is based on many of the best concepts that came of the Factom protocol, including data and identity focus while combining the components in a new and unique configuration.
|
||||
|
||||
The Accumulate protocol is designed by Paul Snow. Paul Snow is the Chief Blockchain Scientist at Inveniam and Defi Devs. Previously, he was the CEO and chief architect of the Factom protocol and co-author of the Factom White Paper, developing and implementing a “multi-leader” consensus algorithm for the blockchain network. Of note, he was founder and chief architect for DTRules, an open-source project providing decision table-based rules engines. He is listed as inventor on many of Factom’s 40+ patents, both issued and in progress, which serve as a foundation for Accumulate."
|
||||
layout: companies
|
||||
permalink: companies/accumulate/
|
||||
redirect_from:
|
||||
- companies/accumulate
|
||||
- companies/factom/
|
||||
- companies/factom
|
||||
canonical_url: 'https://decentralized-id.com/companies/accumulate/'
|
||||
categories: ["Blockchain"]
|
||||
tags: ["Factom","DID","DHS","Blockchain"]
|
||||
toc_sticky: false
|
||||
toc: false
|
||||
header:
|
||||
image: /images/factom_header.webp
|
||||
teaser: /images/factom-teaser.webp
|
||||
last_modified_at: 2020-11-02
|
||||
tags: ["DHS","Factom","Accumulate"]
|
||||
standards: ["DID","Verifiable Credentials"]
|
||||
last_modified_at: 2023-02-20
|
||||
toc: true
|
||||
---
|
||||
|
||||

|
||||
|
||||
* [Factom - About](https://www.factom.com/company/about-us/)
|
||||
> We provide a Blockchain-as-a-Service platform for data provenance and integrity solutions built on the Factom blockchain. We help our customers and partners build business-ready apps that preserve evidence, demonstrate compliance, increase process transparency, streamline audits, reduce cost, and automate transactions. All without cryptocurrency exposure or costly infrastructure.
|
||||
|
||||
<blockquote class="twitter-tweet"><p lang="en" dir="ltr">What's next:<br>◻️ Mobile app bringing <a href="https://twitter.com/hashtag/verifiablecredentials?src=hash&ref_src=twsrc%5Etfw">#verifiablecredentials</a> to your pocket (in partnership with <a href="https://twitter.com/Off_Blocks?ref_src=twsrc%5Etfw">@Off_Blocks</a> )<br>◻️ Verifiable organizations<br>◻️ Guardianship, delegation, & controllership credentials<br>◻️ Extended <a href="https://twitter.com/hashtag/interoperability?src=hash&ref_src=twsrc%5Etfw">#interoperability</a> w/ <a href="https://twitter.com/TransmuteNews?ref_src=twsrc%5Etfw">@TransmuteNews</a> and <a href="https://twitter.com/Mavennet_?ref_src=twsrc%5Etfw">@Mavennet_</a> <br><br>Stay tuned 📻</p>— Factom Inc. (@factom) <a href="https://twitter.com/factom/status/1219276914281648133?ref_src=twsrc%5Etfw">January 20, 2020</a></blockquote> <script async src="https://platform.twitter.com/widgets.js" charset="utf-8"></script>
|
||||
|
||||
## History
|
||||
|
||||
* [Factom - About](https://www.factom.com/company/about-us/)
|
||||
> Factom, Inc. is a blockchain innovations company. Established in 2014, the founders recognized bitcoin’s limitations to be a practical blockchain for Enterprise data solutions. Generally, distributed records, information and documents have been difficult to protect, challenging to synchronize, and impossible to truly verify because of the manual effort involved. In response to these challenges, we built the Factom blockchain as open source, reaching full decentralization in May 2018.\
|
||||
> [...]\
|
||||
> In 2017, we raised over $8 million in a Series A led by Tim Draper, of Draper Associates. This series of funding included many valuable investors such as Medici Ventures, a wholly owned subsidiary of Overstock.com, Inc., Peeli Ventures, and Harvest Equity. With our Series A funding, we built Factom Harmony, our Blockchain-as-a-Service platform
|
||||
* [DHS S&T Awards $199K to Austin Based Factom Inc. for Internet of Things Systems Security](https://www.dhs.gov/science-and-technology/news/2016/06/17/st-awards-199k-austin-based-factom-inc-iot-systems-security) (2016)
|
||||
> The Department of Homeland Security (DHS) Science and Technology Directorate (S&T) today awarded $199,000 to Factom Inc. based in Austin, Texas, to advance the security of digital identity for Internet of Things (IoT) devices.
|
||||
* [Factom Inc. Wins Contract Award from the Department of Homeland Security: Preventing Forgery & Counterfeiting](https://www.factom.com/company-updates/factom-inc-wins-contract-award-from-the-department-of-homeland-security-preventing-forgery-counterfeiting/)
|
||||
> The Department of Homeland Security (DHS) Science and Technology Directorate’s Silicon Valley Innovation Program (SVIP) has given a performance-based contract award to **Factom** Inc. The award will be used to develop cross-blockchain technology to help prevent the forgery and counterfeiting of certificates and licenses.
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
|
|
|
|||
|
|
@ -5,41 +5,21 @@ name: Mattr
|
|||
description: Building an extensive set of capabilities for verifiable credential issuance, verification, and storage.
|
||||
excerpt: >
|
||||
We’ve designed our products based on a few key principles: extensible data formats, secure authentication protocols, a rigorous semantic data model, industry-standard cryptography, and the use of drivers and extensions to allow modular and configurable use of the platform over time.
|
||||
layout: single
|
||||
layout: companies
|
||||
permalink: companies/mattr/
|
||||
canonical_url: 'https://decentralized-id.com/companies/mattr/'
|
||||
categories: ["Companies"]
|
||||
tags: ["DHS","MATTR","BBS Signatures","DID","JSON-LD","Sovrin Foundation","Verifiable Credentials","Linked Data","Schema.org"]
|
||||
last_modified_at: 2020-11-04
|
||||
tags: ["DHS","MATTR","Sovrin Foundation"]
|
||||
standards: ["DID","Verifiable Credentials","Schema.org","JSON-LD"]
|
||||
use: [ID]
|
||||
tech: ["BBS Signatures","Linked Data"]
|
||||
header:
|
||||
image: /images/MATTR_.webp
|
||||
teaser: /images/mattr_teaser.webp
|
||||
toc: false
|
||||
last_modified_at: 2023-02-20
|
||||
toc: true
|
||||
---
|
||||
|
||||
**[Docs](https://learn.mattr.global/) • [News](https://mattr.global/resources/news/) • [Articles](https://mattr.global/resources/articles/) • [Presentations](https://mattr.global/resources/presentations/)**
|
||||
|
||||
- [Introducing the MATTR Platform](https://mattr.global/introducing-the-mattr-platform/)
|
||||
> Here at MATTR, we have been hard at work building a suite of products to serve the next generation of digital trust. We’ve designed our products based on a few key principles: extensible data formats, secure authentication protocols, a rigorous semantic data model, industry-standard cryptography, and the use of drivers and extensions to allow modular and configurable use of the platform over time. By combining our core capabilities with extensions and drivers, our platform offers developers convenience without compromising flexibility or choice.
|
||||
- [SSI? What we really need is full data portability](https://mattr.global/ssi-what-we-really-need-is-full-data-portability/)
|
||||
> Governments and other stakeholders exploring SSI are less interested in ideology and more interested in improving the user experience for their customers and constituents. They want to increase access to services, improve service delivery, and safely digitalize interactions, while mitigating privacy and data security-related risks. The key to these objectives lies in full data portability—this means granting individuals robust legal rights, as well as straightforward technical tools and capabilities, to manage and use identity credentials and other personal data with more trust, confidence and ease, so that they can share medical records with a new doctor, port professional credentials to a new employer, and the like.
|
||||
- [A solution for privacy-preserving Verifiable Credentials](https://mattr.global/a-solution-for-privacy-preserving-verifiable-credentials/)
|
||||
> Here at MATTR, we are piloting an approach to ZKPs based on BBS+ signatures. Beyond the privacy and security benefits of ZKPs in general, this approach has a number of additional benefits compared to the ZKP implementations that exist today.
|
||||
- [JWT vs Linked Data Proofs: comparing Verifiable Credentials](https://mattr.global/jwt-vs-linked-data-proofs-comparing-verifiable-credentials/)
|
||||
> Linked Data Proofs offer more flexibility and are thus more scalable for global decentralized networks. Plus, because they natively work with JSON-LD, they encourage adoption of an open-world data model and re-usage of schemas that makes JSON-LD so powerful.
|
||||
>
|
||||
> JWTs, in contrast, offer a simple and straightforward way to express data with a limited semantic vocabulary. Using JWTs with JSON-LD provides a potential compromise between the two approaches, but loses much of the flexibility provided by Linked Data Security.
|
||||
- [Using privacy-preserving ZKP credentials on the MATTR Platform](https://mattr.global/using-privacy-preserving-zkp-credentials-on-the-mattr-platform/)
|
||||
> By leveraging pairing-friendly elliptic-curve cryptography in the context of Linked Data Proofs, our approach provides an unprecedented way to perform zero-knowledge proofs using the semantics of JSON-LD. This allows credential issuers to tap into vast data vocabularies that exist on the web today, such as schema.org and Google Knowledge Graph, making user data more context-rich without sacrificing security and privacy of the user in the process. Not only is this approach more interoperable with existing implementations of the VC data model and semantic web technologies, it also doesn’t rely on any external dependencies to operate (like a distributed ledger), meaning it’s far more efficient than other approaches based on CL-signatures and zk-SNARKs. We’ve open-sourced our LD-Proofs suite for VCs including performance benchmarks so you can check it out yourself.
|
||||
- [DID Extensibility on the MATTR Platform](https://mattr.global/did-extensibility-on-the-mattr-platform/)
|
||||
> DID Web helps to bridge the gap between the way that trust is established on the internet today, namely using domains, and new and emerging ecosystems using DIDs. When using DID Web, rather than anchoring a DID to a decentralized ledger such as a blockchain, the DID is instead associated with a specific domain name, and subsequently anchored to the web host registered with that domain via DNS resolution. Effectively, this allows a DID using this scheme to be resolved as simply as one resolves a web URL, every time they click on a link. For example, we’ve set up a DID Web using our own domain, which can be resolved at did:web:mattr.global.
|
||||
- [New to JSON-LD? Introducing JSON-LD Lint](https://mattr.global/new-to-json-ld-introducing-json-ld-lint/)
|
||||
> The rise in popularity of javascript (due to its natural language monopoly in web-browsers) led to a mass exile from XML and shift over to JSON as the prefered data representation format. In the process, certain valuable features of XML were lost, in particular those that provide a standardised semantic syntax. JSON-LD defines this missing layer of syntax, which improves semantic reasoning around data. This is critical for maintaining data quality and trust in data, which is particularly important as we increase our reliance on digital infrastructure, IOT and AI.
|
||||
- [Adding support for revocation of Verifiable Credentials](https://mattr.global/adding-support-for-revocation-of-verifiable-credentials/)
|
||||
> Integrating revocation into our platform brings us one step closer to building a fully realized verifiable data ecosystem, an environment where verifiers can have more confidence and trust in the decisions they’re making and people can participate in the sharing and exchange of information without eroding their basic privacy. We look forward to continuing to collaborate with the community and gathering feedback from industry to enhance and extend different ways to accomplish revocation while respecting users’ digital rights.
|
||||
|
||||
---
|
||||
|
||||
* [DHS Awards $200K for Issuing and Validating Essential Work and Task Licenses](https://www.dhs.gov/science-and-technology/news/2020/10/09/news-release-dhs-awards-200k-issuing-and-validating-essential-work-and-task-licenses)
|
||||
> MATTR is currently building an extensive set of foundational capabilities in a software-as-a-service (SaaS) platform for verifiable credential issuance, verification, and storage. An essential worker or a person performing an essential task would receive various credentials and attestations from many issuers containing relevant assertions about their essential work or task status. Their solution also offers the option to validate the information further by using either public or private registries of authoritative verifiable information.
|
||||
|
||||
|
|
|
|||
|
|
@ -5,7 +5,7 @@ name: Jolocom
|
|||
description: Jolocom builds global infrastructure to support decentralized digital identity management.
|
||||
excerpt: >
|
||||
The protocol logic encodes a granular, claim-based model of identity that is highly generalized and unrestrictive in scope in order to accommodate a multiplicity of potential use cases and broad range of subjects of identity (users), including individual persons as well non-person entities like organizations (e.g. companies, governmental bodies), IoT devices (e.g. hardware/software agents), and autonomous agents (e.g. DAOs).
|
||||
layout: single
|
||||
layout: companies
|
||||
permalink: companies/jolocom/
|
||||
canonical_url: 'https://decentralized-id.com/companies/jolocom/'
|
||||
categories: ["Companies","Ethereum"]
|
||||
|
|
@ -13,21 +13,9 @@ tags: ["Jolocom","DIF","T-Labs","Ethereum","DID","Solid","BigchainDB","IOTA"]
|
|||
header:
|
||||
image: /images/jolocom.webp
|
||||
teaser: /images/jolocom-teaser.webp
|
||||
last_modified_at: 2020-11-04
|
||||
toc: false
|
||||
last_modified_at: 2023-02-20
|
||||
toc: true
|
||||
---
|
||||
|
||||
|
||||
* [Jolocom](http://jolocom.com/)
|
||||
* a "SmartWallet" for everyone to own their personal digital identity, using [Social Linked Data](https://github.com/solid/solid-spec), WebID, and verifiable claims standards via Ethereum smart contracts.
|
||||
* [A universal identity layer we can only build together](https://stories.jolocom.com/a-universal-identity-layer-we-can-only-build-together-e297ed5ae4ed)
|
||||
* [A Decentralized, Open Source Solution for Digital Identity and Access Management](https://jolocom.io/wp-content/uploads/2019/12/Jolocom-Whitepaper-v2.1-A-Decentralized-Open-Source-Solution-for-Digital-Identity-and-Access-Management.pdf) (Whitepaper)
|
||||
> The protocol logic encodes a granular, claim-based model of identity that is highly generalized and unrestrictive in scope in order to accommodate a multiplicity of potential use cases and broad range of subjects of identity (users), including individual persons as well non-person entities like organizations (e.g. companies, governmental bodies), IoT devices (e.g. hardware/software agents), and autonomous agents (e.g. DAOs).
|
||||
- [FAQ](https://stories.jolocom.com/faq-34d24e2579d2)
|
||||
- [Trusted Data Sharing with Social Linked Data (Solid) and Ethereum](https://stories.jolocom.com/trusted-data-sharing-with-social-linked-data-solid-and-ethereum-in-the-internet-of-things-iot-7dc242944624)
|
||||
> At the core of Solid is the WebID, which Jolocom integrates with the Ethereum blockchain, to build a self-sovereign digital identity that allows you to represent yourself and to enrich your data with semantic meaning. Besides that and storing data, it also lets other applications ask for your data. Solid authenticates the DApps (Decentralized Applications) through Access Control Lists (ACLs) and if you’ve given access permission to the requester of the data, the Solid server delivers it.
|
||||
- [PRESS RELEASE: T-Labs (Deutsche Telekom) announces project with major blockchain startups](https://stories.jolocom.com/press-release-t-labs-deutsche-telekom-announces-project-with-major-blockchain-startups-e6ac451d8b3)
|
||||
> Benefiting from the expertise in Berlin, T-Labs partnered with BigchainDB, IOTA, Jolocom and Riddle & Code to abstract the complexity of blockchain development for enterprises. With the prototype developers can combine different DLTs to enable decentralized storage, identity management, smart contracts and payments. This allows enterprises to build a decentralized back-end in a matter of minutes.
|
||||
- [5 years of decentralizing identities](https://stories.jolocom.com/5-years-of-decentralizing-identities-e04dcd5b4494)
|
||||
|
||||

|
||||
|
|
@ -5,41 +5,15 @@ name: Meeco
|
|||
description: Zero Knowledge Proofs of the modern digital life for access, control, delegation and consent of identity and personal data
|
||||
excerpt: >
|
||||
Meeco enables people (data subjects)to provide their own verified records and controlled consent. This API-of-Me allows Meeco to provide a meta-data driven attribute wallet with no knowledge of the data to any authenticated identity of a user,which in turn enables an auditable personal-event chain of data interactions at scale.
|
||||
layout: single
|
||||
layout: companies
|
||||
permalink: companies/meeco/
|
||||
canonical_url: 'https://decentralized-id.com/companies/meeco/'
|
||||
categories: ["Companies"]
|
||||
tags: ["Meeco","MyData","Respect Network","DIF","GDPR"]
|
||||
tags: ["MyData","Respect Network","DIF","Meeco"]
|
||||
header:
|
||||
image: /images/meeco_header.webp
|
||||
teaser: /images/meeco-teaser.webp
|
||||
last_modified_at: 2020-11-05
|
||||
toc: false
|
||||
last_modified_at: 2023-02-20
|
||||
toc: true
|
||||
---
|
||||
|
||||
**[Website](https://meeco.me) • [Katryna Dow](https://katrynadow.me/about/) • [Blog](https://blog.meeco.me/) • [Dev Portal](https://dev.meeco.me/) • [App](https://app.meeco.me/) • [Twitter](https://twitter.com/meeco_me)**
|
||||
|
||||
* Meeco Whitepaper- [Zero Knowledge Proofs of the modern digital lifefor access, control, delegation and consent of identity andpersonal data](https://media.meeco.me/public-assets/white_papers/Meeco_Zero%20Knowledge%20Proofs%20of%20the%20modern%20digital%20life_V1.0_20180513.compressed.pdf)
|
||||
> The Meeco solution provides access, control, delegation and consent from the perspective of the individual user. Meeco enables people (data subjects)to provide their own verified records and controlled consent. This API-of-Me allows Meeco to provide a meta-data driven attribute wallet with no knowledge of the data to any authenticated identity of a user,which in turn enables an auditable personal-event chain of data interactions at scale.
|
||||
|
||||
* [European Strategy for Data](https://media.meeco.me/public-assets/reports/Meeco_Review_of_European_Strategy_for_Data.pdf) • [data](https://www.meeco.me/data)
|
||||
> A Meeco Review of the European Strategy for Data Communication from the European Commission on February 19th, 2020
|
||||
|
||||
* [Meeco Positioned as Leader in Personal Identity Products in One World Identity’s Identity Industry Landscape](https://blog.meeco.me/meeco-positioned-as-leader-in-personal-identity-products-in-one-world-identitys-identity-industry-landscape/)
|
||||
> Meeco has been recognized as a leader in Personal Identity Products. Meeco is a GDPR compliant multi-sided personal data platform to offer personalised solutions and channels to build trust. Organisations can incorporate Meeco’s secure data enclave inside existing applications to create value for customers by simplifying onboarding and personalising experiences. This balance of Me2B and B2Me, enabling new privacy enhanced business models to emerge, is core to Meeco’s unique position in the emerging personal data market.
|
||||
|
||||
* [Meeco joins RegTech Association of Australia](https://blog.meeco.me/innovate-beyond-compliance/)
|
||||
> History has shown us that at times of national emergency, personal rights and freedoms are often traded for the greater good. Whilst these measures may be appropriate in the eye of the storm, society is often left with the legacy of less than optimal freedoms when life becomes more stable.
|
||||
>
|
||||
> One of the tools we have at our disposal is the rise of RegTech; specifically, the ability to implement greater monitoring, governance and separation of concerns that can help society balance between what we need to know, and the hard-fought freedoms of global citizens.
|
||||
|
||||
* [Katryna Dow Named as a Top 100 Identity Influencer](https://blog.meeco.me/katryna-dow-named-top-100-identity-influencer/)
|
||||
> Katryna has been pioneering personal data rights since 2002, when she envisioned a time when personal sovereignty, identity and contextual privacy would be as important as being connected. Now within the context of GDPR and Open Banking, distributed ledger, cloud, AI and IoT it has never been so important to make sure identity works for us all.
|
||||
|
||||
* [Understanding the difference between Identity, Authentication and Authorisation](https://blog.meeco.me/do-you-really-need-to-know-who-i-am/)
|
||||
> - Identity is the answer to the “Who am I?” or “What am I?” question.
|
||||
> - Authentication is about asking can I trust who or what this is?
|
||||
> - Authorisation follows authentication to determine what services are available to the trusted party.
|
||||
|
||||
* [Advancing human-centric personal data: MyData 2016 powered by MeCast](https://blog.meeco.me/advancing-human-centric-personal-data/)
|
||||
> For conference attendees, whether participating in-person, or engaging with the MyData community in the comfort of your home or office, MyData 2016 powered by MeCast is the hub of personal data activity, conversation, thought leadership and action throughout August and September.
|
||||
|
|
|
|||
|
|
@ -5,165 +5,18 @@ name: Transmute
|
|||
description: Transmute’s technology connects enterprise infrastructure with emergent identity, credential, and data storage solutions.
|
||||
excerpt: >
|
||||
Transmute digitizes trade documentation in a way that is cryptographically verifiable and traceable across an entire logistics ecosystem. The company’s approach combines decentralized identifier (DID), verifiable credential (VC), and blockchain technology with existing cloud-based systems to eliminate the paper hassle of trade docs and provide unprecedented visibility into customers’ supplier networks by effectively memorializing trade data at every step in a products’ journey from point of origin to point of import and beyond.
|
||||
layout: single
|
||||
layout: companies
|
||||
permalink: companies/transmute/
|
||||
canonical_url: 'https://decentralized-id.com/companies/transmute/'
|
||||
redirect_from:
|
||||
- blockchain/ethereum/transmute/
|
||||
categories: ["Companies","Ethereum"]
|
||||
tags: ["Transmute","Ethereum", "Microsoft","DID","Verifiable Credentials","Consensys","DIF","Encrypted Data Vaults","Oracle","OAuth","OIDC"]
|
||||
tags: ["Microsoft","Consensys","DIF","Encrypted Data Vaults","Oracle"]
|
||||
header:
|
||||
image: /images/transmute.webp
|
||||
teaser: /images/transmute_thumb.webp
|
||||
last_modified_at: 2021-04-19
|
||||
last_modified_at: 2023-02-20
|
||||
toc: true
|
||||
---
|
||||
|
||||
**[Transmute Industries](https://www.transmute.industries/) • [Blog](https://medium.com/@Transmute) • [Tech Talk](https://medium.com/transmute-techtalk/) • [Github](https://github.com/transmute-industries) • [Twitter](https://twitter.com/transmutenews) • [Linkedin](https://www.linkedin.com/company/transmute-industries/)**
|
||||
|
||||
> Transmute secures critical supplier, product, and shipment data to give customers a competitive edge in the increasingly dynamic global marketplace.
|
||||
|
||||
## The Story of Karyl Fowler and Transmute
|
||||
|
||||
> For all the sexy tech stuff happening, it’s deep comprehension of the business challenges that will drive adoption. This is one area my team has an advantage as Orie and I have almost no overlapping skill sets, which has allowed us to move fast, divide & conquer the business and technology components in parallel. - Karyl Fowler, CEO and Co-founder of Transmute
|
||||
|
||||
Towards the end of 2020, I was Contacted about an upcoming company announcement from Transmute. I took the opportunity to learn more about their work, and even got the chance to have a call with Karyl Fowler.
|
||||
|
||||
Transmute has been gaining momentum following [their work with the US Department Homeland Security](https://www.dhs.gov/science-and-technology/news/2019/11/08/news-release-dhs-awards-198k-raw-material-import-tracking) (DHS) Science and Technology Directorate’s Silicon Valley Innovation Program.
|
||||
|
||||
The announcement came on [OCTOBER 21, 2020](https://www.prweb.com/releases/transmute_closes_2m_seed_round_from_moonshots_capital_tmv_kerr_tech_investments/prweb17487962.htm), with the news of Transmute closing a 2 million dollar seed round from Moonshots Capital, TMV, and Kerr Tech Investments.
|
||||
|
||||
With a clear opportunity to grow rapidly in the enterprise market, Transmute plans to deploy the new capital to expand its Austin, Texas-based team to service increasing customer demand. The company secures critical supplier, product, and shipment data to give customers a competitive edge in an increasingly dynamic, global marketplace.
|
||||
|
||||
These are clearly exciting times for Transmute and the industry as a whole.
|
||||
|
||||
### Karyl's Education and Background
|
||||
|
||||
While working in Economic Development for the Greater Austin Chamber of Commerce, Karyl earned a Masters of Science in Technology Commercialization from the University of Texas at Austin, Red McCombs School of Business.
|
||||
|
||||
Her work during this time focused mainly on recruiting tech and manufacturing companies to Austin, TX as well as supporting management of the city’s Foreign Trade Zone initiatives.
|
||||
|
||||
Karyl then worked for a semiconductor company, Novati Technologies, whose core business was in the defense sector. There, she leveraged data-driven strategies to achieve sustainable development partnerships and expand Novati’s bioelectronics portfolio to become a more integral component of their overall market strategy.
|
||||
|
||||
It was in that role when Karyl first became interested in data privacy, discovering business models that were being created around DNA sequencing, and seeing how little agency an individual had over their own genetic data.
|
||||
|
||||
This experience also gave her a front seat view of global supply chains - both the inherent complexity and even intentional opacity involved in moving highly regulated products across borders.
|
||||
|
||||
### Early Hackathon Success
|
||||
|
||||
Upon graduation, Karyl began participating in hackathons with her co-founder, Orie Steele. Incidentally, most hackathon participants don’t arrive with a business-person.
|
||||
|
||||
This is where Karyl gave the team an edge, enabling them to show up with something just a little more polished than engineer-only teams.
|
||||
|
||||
They entered Austin’s first blockchain hackathon in early 2016, held at the [Capital Factory](https://www.capitalfactory.com/), where they built a user-centric and traceable identity management application for refugees who were pouring into Europe at the time.
|
||||
|
||||
> Understanding concerns about business models, built on your most intimate data, I wanted to see something where I had more control over who could access that, and I would actually own it. - Karyl Fowler, [Giant Robots #324](https://www.giantrobots.fm/324)
|
||||
|
||||
### Being blockchain agnostic
|
||||
|
||||
After discussing Karyl’s background and the story of Transmute, the subject came up about Transmute being largely blockchain agnostic. I was curious to know exactly what that means.
|
||||
|
||||
Karyl shared that Transmute has always felt strongly about interoperability, and just like cloud technologies, this would not be a winner-take-all scenario. They took a lot of flack for that position in earlier days, and for a while were feeling “too blockchain for the enterprise and too enterprise for the blockchain,” but ultimately their thesis is playing out.
|
||||
|
||||
She also shared that they are building in a time where the “winners” are still shaking out, and warned that some folks in the enterprise space are cornering themselves into a particular solution stack that could easily become obsolete.
|
||||
|
||||
To solve for this challenge, Transmute uses a flexible, ledger-agnostic architecture with adapters for a variety of ledger options depending upon the needs of where it’s being applied. An important component of [interoperability involves building on open standards](https://github.com/transmute-industries/interoperability)..
|
||||
|
||||
### DHS Silicon Valley Innovation Program
|
||||
|
||||
Anil John and Melissa Oh, of the Silicon Valley Innovation Program (SVIP), were recently interviewed on the [Federal Blockchain News](https://www.federalblockchainnews.com/podcast/episode/7975a493/dhs-melissa-oh-and-anil-john-of-silicon-valley-innovation-program) Podcast, which sheds light into exactly what values the program operates under.
|
||||
|
||||
The DHS is focused on creating increased transparency in the cross-border supply-chain, which can lead to greater efficiencies in trade and unlock massive economic value. The DHS is focused on open-source, open-standards, and interoperability.
|
||||
|
||||
> There was a significant push by large platform players and others, to set up a platform model […] sit in the middle and extract value from that platform. As a government, we are rather familiar with being walked into a corner and told that there is only one product that you will buy because it will solve the problem. - *Anil John, [Federal Blockchain News](https://www.federalblockchainnews.com/podcast/episode/7975a493/dhs-melissa-oh-and-anil-john-of-silicon-valley-innovation-program)
|
||||
|
||||
> We believe there is a fundamental layer of security privacy and interoperability that should be common across all platforms. Then you build value-added services on top of it. - *Anil John, [Federal Blockchain News](https://www.federalblockchainnews.com/podcast/episode/7975a493/dhs-melissa-oh-and-anil-john-of-silicon-valley-innovation-program)
|
||||
|
||||
|
||||
## Transmute News
|
||||
|
||||
- [did:(customer)](https://medium.com/transmute-techtalk/did-customer-4ca8b7957112)
|
||||
> Transmute builds solutions that solve real business problems. For this reason, we support a number of different decentralized identifier (DID) methods. While we are committed to providing optionality to our customers, it’s equally important to communicate the selection criteria behind these options so that customers can consider the tradeoffs of underlying DID-methods alongside the problem set they’re solving for. Essentially, we help them pick the right tool for the job.
|
||||
- [Transmute Closes $2M Seed Round](https://medium.com/transmute-techtalk/transmute-closes-2m-seed-round-a0a2e6c90467)
|
||||
> Closing our seed round coincides with another exciting announcement: our recent launch of Phase II work with the U.S. [Department of Homeland Security, Science & Technology’s Silicon Valley Innovation Program (SVIP)](https://www.dhs.gov/science-and-technology/news/2019/11/08/news-release-dhs-awards-198k-raw-material-import-tracking) to enhance “transparency, automation and security in processing the importation of raw materials” like steel.
|
||||
- [Transmute Releases Technical Workbenches](https://medium.com/transmute-techtalk/transmute-releases-technical-workbenches-892f8140ac6e)
|
||||
> - [Element Ropsten Workbench](http://staging.element.transmute.industries/)
|
||||
> - [Encrypted Data Vault Workbench](https://staging.data-vault.transmute.industries/)
|
||||
> - [DID Key Workbench](http://did.key.transmute.industries/)
|
||||
- [NFC + DIDs](https://medium.com/transmute-techtalk/nfc-dids-6d56fda45831)
|
||||
> Supply chains are complicated. While over 80% of logistics companies are investing in digitization to bring their supply chains into the 21st century, at the end of the day, not every step along the way can be web-enabled.
|
||||
>
|
||||
> Transmute has been working on a solution: tying DIDs to Tangem NFC Cards, which carry a passport-grade secure chip, which implements public key cryptography. Near Field Communication (NFC) is the technology that enables things like contactless payments [...] increasingly used in supply chains for things like inventory and warehouse management
|
||||
* [Blockchain-secured Documents for Global Trade](https://medium.com/transmute-techtalk/blockchain-secured-documents-for-global-trade-3369d4cfab1f)
|
||||
> On May 14th, 2020 Conexus Indiana and Transmute hosted an interactive webinar titled “Blockchain-secured Documents for Global Trade” as part of the Emerging Technology Showcase series.
|
||||
|
||||
{% include video id="EKiqQnKQ-nM" provider="youtube" %}
|
||||
|
||||
- [The Business Case for Interoperability](https://medium.com/transmute-techtalk/the-business-case-for-interoperability-a1a2b884297d)
|
||||
> For Transmute, the foundations required to technically interoperate are considered pre-competitive, and our ability to interoperate widely is a strategic feature. This feature powers a competitive advantage that ensures Transmute customers’ critical trade documents are verifiable at every step in the supply chain, regardless of where they’re stored and what blockchain they’re anchored to. Transmute customers realize maximum confidence about data integrity and access far richer insights about the health of their supply chains as a result.
|
||||
- [Verifiable Credentials with Transmute and Otaka](https://medium.com/transmute-techtalk/verifiable-credentials-with-transmute-and-okta-574edaec887b)
|
||||
> Okta provides a mechanism for adding custom claims to id_tokens and access_tokens: [Hooks](https://www.okta.com/hooks/) and [Custom Authorization Servers](https://developer.okta.com/docs/guides/customize-authz-server/overview/). These components can enable automated integrations with emergent technology including decentralized identifiers and verifiable credentials.
|
||||
- [Federated Enterprise Agents with Transmute and Okta](https://medium.com/transmute-techtalk/federated-enterprise-agents-with-transmute-and-okta-2f1855dd3944)
|
||||
> The [Okta Identity Cloud](https://www.okta.com/learn/okta-identity-cloud/) provides secure identity management with Single Sign-On, Multi-factor Authentication, Lifecycle Management (Provisioning), and more. Transmute provides a configurable Enterprise Agent enabling Decentralized Identity and Verifiable Credential capabilities for OAuth / OIDC users. Read on to learn about some of the ways Transmute and Okta enable enterprises to rapidly unlock the security benefits of decentralized identities.
|
||||
- [Encrypted Data Vaults](https://medium.com/transmute-techtalk/encrypted-data-vaults-c794055b170e)
|
||||
> EDVs allow users and companies to store data with their favorite cloud storage providers without fear of vendor lock-in, while also ensuring that the storage provider has no access to their data whatsoever. With an EDV, the client does their own encryption and decryption using keys associated with decentralized identifiers they manage, and as such, acts as the true controller of their data.
|
||||
* [DHS Awards $198K for Raw Material Import Tracking Using Blockchain](https://www.dhs.gov/science-and-technology/news/2019/11/08/news-release-dhs-awards-198k-raw-material-import-tracking)
|
||||
> Its Phase 1 award project “Verifiable Provenance, Traceability, and Regulatory Compliance for Raw Material Imports” will adapt Transmute ID, its core technology product that leverages centralized and decentralized identity infrastructures to secure individual agency identities and verifiable credentials to ensure that CBP has visibility into the provenance, traceability and regulatory compliance of raw material imports.
|
||||
- [Element Block Explorer](https://medium.com/transmute-techtalk/element-block-explorer-bb6d2c712664)
|
||||
> We’ve made some serious upgrades to the Element-lib which is the javascript library we use to implement the Element DID. As we mentioned in our last post here, Element is a Sidetree Protocol based DID Method that relies on Ethereum and IPFS. Our implementation is unique in that we provide a JavaScript library that runs in both the browser and node.js, in addition to providing a server-based REST API.
|
||||
>
|
||||
> Our first implementation of Element enabled users to anchor their DID directly via a MetaMask-powered DApp thanks to Infura, and also use our “Full Node” to submit operations. Supporting both modes introduced a lot of complexity, and highlighted some scalability issues which we’ve recently fixed.
|
||||
- [Introducing: Element](https://medium.com/transmute-techtalk/introducing-element-328b4260e757) - The Sidetree Protocol Implemented on Ethereum
|
||||
> the scalability that Sidetree brings to DIDs is unprecedented. Our product, Transmute ID — enterprise-grade decentralized identity — must support scale that we could not achieve otherwise, so we are proud to offer Element as an alternative DID method for Transmute ID customer deployments.
|
||||
|
||||
<center><iframe src="//www.slideshare.net/slideshow/embed_code/key/2ct2imQLUnzp1j" width="595" height="485" frameborder="0" marginwidth="0" marginheight="0" scrolling="no" style="border:1px solid #CCC; border-width:1px; margin-bottom:5px; max-width: 100%;" allowfullscreen> </iframe> <div style="margin-bottom:5px"> <strong> <a href="//www.slideshare.net/SSIMeetup/the-element-did-method-sidetree-ethereum-ipfs-orie-steele" title="The Element DID Method: Sidetree, Ethereum & IPFS – Orie Steele" target="_blank">The Element DID Method: Sidetree, Ethereum & IPFS – Orie Steele</a> </strong> from <strong><a href="https://ssimeetup.org/element-did-method-sidetree-ethereum-ipfs-orie-steele-webinar-31/" target="_blank">SSIMeetup</a></strong> </div></center>
|
||||
|
||||
* [transmute-industries/sidetree.js](https://github.com/transmute-industries/sidetree.js)
|
||||
> Sidetree.js is an implementation of v0.1.0 of the sidetree specification
|
||||
* [Summer 2019 Update](https://medium.com/transmute-techtalk/summer-2019-update-c11df7806a79)
|
||||
> Supply chain logistics companies are particularly interesting with how they manage their extended business networks as they compete for new business. This includes faster and safer on-boarding of customers and third-party vendors, and new ways to manage the lifecycle and associated data of those relationships.
|
||||
>
|
||||
> The potential of integrating Transmute’s user/company managed identities (DIDs) and trusted data (verifiable credentials) as tools for powering this new way of networking is leading to increased interest from prospective enterprise customers. As a result, we are expanding both our thought leadership and systems design consulting offerings.
|
||||
|
||||
## Early work on an Ethereum dApp Platform
|
||||
|
||||
* [Back to the Basics](https://medium.com/transmute-techtalk/back-to-the-basics-9158f47f4eb6) 6/16/19
|
||||
> Several mentors have encouraged me to publicly share a more detailed account of Transmute’s choice to shift focus solely to commercializing Transmute ID, the decentralized identity component of our original product, the Transmute Platform — a Heroku-like rapid dApp builder that seamlessly bridged centralized and decentralized tech, specifically for existing enterprises.\
|
||||
> [...]\
|
||||
> there was zero near-term enterprise demand in the token-powered functionality of the platform. We searched high and low, interviewing most of the major enterprise storage solutions out there and couldn’t even find one willing to admit that investing decentralized storage tech was on their 5 year innovation roadmap.\
|
||||
> [...]\
|
||||
> we did uncover a demand for user-centric identity tech (e.g. increased security, privacy, portability, infinite federation/scalable, etc.) and an enormous demand for the resulting efficiency gains and untapped revenue potential of implementing a decentralized identity solution. Because these directly address problems enterprises are facing today, and they directly connect to the cost/profit levers that enterprise stakeholders care most about.
|
||||
- [GitHub DID](https://github-did.com/) - ([source](https://www.npmjs.com/package/@transmute/github-did))
|
||||
> `npm i -g @github-did/cli`\
|
||||
> `ghdid init "my-password" https://github.com/USERNAME/ghdid`\
|
||||
> `# if you need to revoke all / reset your DID`\
|
||||
> `ghdid init "my-password" https://github.com/USERNAME/ghdid --force`
|
||||
- [Transmute ID Alpha](https://medium.com/transmute-techtalk/transmute-id-alpha-ba66cdc112fe) 1/2019 (sixth monthly release)
|
||||
> One thing we learned from our Orbit DB PoC is that the DID spec offers a lot of valuable flexibility. Most DID systems achieve censor resistant decentralized storage and cryptographic decentralized identity protocols through a single identifier (hash of or full public key). We found it is possible to create a valid DID implementation that is anchored by 2 public keys, one for updating the filesystem, the other for managing the integrity of the documents, identities and claims.
|
||||
- [Release 0: Sol](https://medium.com/transmute-techtalk/release-0-sol-9d8fd06d2f4f) 6/2018 (1st release since finishing Techstars)
|
||||
> This release was focused on building support for decentralized identities into centralized directory technology that is already widely adopted by enterprises. This work involved adding UI to our React dashboard and updating our API to support registration and group management. We have also done some exploratory work regarding the DID spec and LDAP integration
|
||||
> [...]\
|
||||
> This release we focused on the centralized side of group membership. This use case relies on the integrity of the directory and discretionary access control. In other words, the directory admins can move users between groups, but users cannot control what groups they are assigned to.
|
||||
* [Release: The Transmute Framework Alpha](https://medium.com/transmute-techtalk/release-the-transmute-framework-alpha-ad45acd42bdc) 4/18
|
||||
> The Transmute Framework helps developers build on decentralized technologies like Ethereum and IPFS via a familiar javascript interface. We support rapid prototyping by enabling developers with Redux experience to quickly build out decentralized applications.
|
||||
>
|
||||
> This release focuses on support and documentation for the EventStore. Using the EventStore and the Transmute Framework, developers can save events to Ethereum and IPFS, track and query the event-sourced data models, and leverage the immutability properties of IPFS and Ethereum.
|
||||
* [Transmute IoT](https://medium.com/transmute-techtalk/transmute-iot-2d00fdcf53e9) 6/17
|
||||
> The Transmute team joined forces with other Austin hackers to participate in [the first Mobility X hackathon at Capital Factory sponsored by car2go](https://www.eventbrite.com/e/mobilityx-hackathon-presented-by-car2go-tickets-33718213083#) a few weekends ago where hackers were challenged to address how to handle rider demand fluctuations or ensure consistent vehicle connectivity.
|
||||
>
|
||||
> Maintaining network connectivity felt like the most urgent problem to solve given an effective solution would mean more accurate data on the car2go fleets, resulting in an expanded capacity to address rider demand changes. Mesh networks have been explored as a natural solution for maintaining network connectivity among distributed assets that are moving around geographically. …
|
||||
|
||||
## [Co-Founders](https://www.transmute.industries/team/)
|
||||
|
||||
> Transmute is committed to accelerating the adoption of decentralized identifiers and verifiable credentials to enable secure, dynamic trade. We charge ourselves and the greater digital identity community to focus on building evolved solutions that challenge the status quo to find superior economic models and reliable data security practices, resulting in a better future for everyone.
|
||||
|
||||
| **Karyl Fowler** (CEO) | **Orie Steele** (CTO) |
|
||||
| ---- | ---- |
|
||||
|  |  |
|
||||
| [@TheKarl](https://twitter.com/TheKaryl) – [linkedin](https://www.linkedin.com/in/karylfowler/) | [@or13b](https://twitter.com/or13b) – [linkedin](https://www.linkedin.com/in/or13b/) |
|
||||
|
||||
## Resources
|
||||
|
||||
* [How Refugees Sparked this Startup to Solve the Enterprise Identity Crisis](https://blogs.oracle.com/startup/how-refugees-sparked-this-startup-to-solve-the-enterprise-identity-crisis)
|
||||
> In the spring of 2016, technologists Karyl Fowler and Orie Steele entered Austin’s first blockchain hackathon contest aimed at solving mobility challenges which drew project topics from smart parking apps to addressing social mobility barriers. At the time, thousands of refugees were pouring into Europe with no means to identify themselves. Government organizations had no integrated way to validate and track identities across the variety of disparate systems they use to manage the asylum process, complicating an already massive humanitarian crisis. So, Fowler and Steele built an identity management application for refugees that was user-centric, secure and traceable.
|
||||
* [324: Tap the Market (Karyl Fowler)](https://www.giantrobots.fm/324)
|
||||
> Karyl Fowler, CEO & Co-founder of Transmute, discusses utilizing block chain for decentralized identity-management, exploring finding the right customer profile fits, education around data-security, her time at Techstars, and the startup community in Austin.
|
||||
|
|
|
|||
|
|
@ -1,57 +1,21 @@
|
|||
---
|
||||
date: 2020-11-07
|
||||
title: Spherity
|
||||
name: Spherity
|
||||
title: Spherity
|
||||
description: Bringing secure identities (“Digital Twins”) to machines, algorithms, and other non-human entities.
|
||||
excerpt: >
|
||||
Spherity is building decentralized identity management solutions to power the 4th industrial revolution, bringing secure identities (“Digital Twins”) to machines, algorithms, and other non-human entities.
|
||||
layout: single
|
||||
layout: companies
|
||||
permalink: companies/spherity/
|
||||
canonical_url: 'https://decentralized-id.com/companies/spherity/'
|
||||
categories: ["Companies"]
|
||||
tags: ["Sovrin Foundation","DIF","Ontology","ISO 27001","IOT","DID","AI","eIDAS","Verifiable Credentials","W3C","Swisscom"]
|
||||
tags: ["Sovrin Foundation","DIF","Ontology","eIDAS","Verifiable Credentials","W3C","Swisscom"]
|
||||
use: ["ID","Digital Twins","AI","IOT"]
|
||||
standards: ["ISO 27001","DID","Verifiable Credentials"]
|
||||
header:
|
||||
image: /images/spherity_banner.webp
|
||||
teaser: /images/spherity_teaser.webp
|
||||
last_modified_at: 2020-11-07
|
||||
toc: false
|
||||
last_modified_at: 2023-02-20
|
||||
toc: true
|
||||
---
|
||||
|
||||
**[website](https://spherity.com) • [Blog](https://medium.com/@spherityy) • [Twitter](https://twitter.com/spherityproject) • [Youtube](https://www.youtube.com/channel/UCJd30vQ46EYCq0KFysJtRMg) • [Linkedin](https://de.linkedin.com/company/spherity)**
|
||||
|
||||
* [Pharma Industry Solutions](https://spherity.com/pharma-solutions/)
|
||||
* [Pharma Third Party Risk Management](https://spherity.com/pharma-third-party-risk-management/)
|
||||
> How can we shorten the supplier onboarding effort in Third Party Risk Management from the thirty days that is typical today, to only three days?
|
||||
* [Authorized Trading Partners](https://spherity.com/pharma-authorized-trading-partners/) - DSCSA-Compliant Verification of Authorized Trading Partners
|
||||
> Spherity is working together with global pharmaceutical manufacturers, wholesalers, distributors, the Healthcare Distribution Alliance and other solution providers to develop a production-grade solution for the Authorized Trading Partner legislation by Autumn 2020. Spherity’s Cloud Identity Wallet enables the exchange and verification of electronic state licenses.
|
||||
* [One-Button Trusted Release](https://spherity.com/pharma-one-button-trusted-release/) - Medical products with verifiable credentials
|
||||
> Imagine a digitalized Trusted Release process on a batch with instant access to all the relevant information in verifiable form, rather than dealing with multiple distributed paper documents. Digitized and pre-validated data allows the Qualified Person to dig deeper or double-check any input with a minimum friction of effort.
|
||||
|
||||
### Blog
|
||||
* [Spherity Achieves ISO 27001 Information Security Standard Certification](https://medium.com/spherity/spherity-achieves-iso-27001-certification-f687ee42c40e)
|
||||
> “To guarantee business continuity and protect data, we have built up an Information Security Management System (ISMS) in accordance with ISO/IEC 27001. For us as a company that deals directly with one of the most valuable assets that civilization has — identity — it was the logical pathway to give information security an appropriate degree of importance. Furthermore, we see it as our duty to our customers and employees to enter into this self-imposed obligation and to guarantee the highest possible level of information security — also as an investment in the deep mutual trust and ongoing cooperation with our clients.”
|
||||
|
||||
* [Swisscom Blockchain & Spherity are Co-developing Cloud Identity Wallets](https://medium.com/spherity/swisscom-blockchain-spherity-are-co-developing-cloud-identity-wallets-632babc50a6c)
|
||||
> [Swisscom Blockchain](https://www.blockchain.swisscom.com/) and [Spherity](http://www.spherity.com/) have both built interoperable Cloud Identity Wallet solutions that handle this kind of world-class, highly trustworthy data, allowing it to transcend silos, proprietary systems, and blockchains. Binding data to digital identities at a low level is the key to bringing more value to all stakeholders in any industry, and making data trustworthy and verifiable anywhere. At its heart, this is what an identity wallet does, and we are proud to have developed two industry-leading, enterprise-grade identity wallets tailored to the documentation needs of the pharmaceutical industry.
|
||||
|
||||
* [Ontology Partners with Spherity to Advance Digital Identity Solutions](https://medium.com/spherity/ontology-partners-with-spherity-to-advance-digital-identity-solutions-4d2c95b288)
|
||||
> Partnership will involve integration of Ontology blockchain into Spherity’s Cloud Identity Wallet
|
||||
|
||||
* [Spherity becomes a Sovrin Steward](https://medium.com/spherity/spherity-becomes-a-sovrin-steward-b813cff2999b)
|
||||
> Spherity has assumed the role of Steward in the Sovrin Network, a not-for-profit worldwide alliance of companies that operate nodes supporting distributed ledger operations so that the network can provide identity for all.
|
||||
|
||||
* [Spherity connects the dots between SSI, AI, and European Data Infrastructure](https://medium.com/spherity/spherity-connects-the-dots-between-ssi-ai-and-european-data-infrastructure-1f626e77ba7)
|
||||
> [Juan Caballero](https://medium.com/u/7da78f634e80) attended the stakeholder meeting for the European Blockchain Services Infrastructure project in Brussels, where architects and legal counsel presented their requirements and reports for the next round of development in partnership with industry leaders and contractors. [...] The most interesting development [...] the report from Nacho Alamilla, a key legal advisor for EBSI, on the functional limits of the current eIDAS (cross-border electronic signature mutual recognition) system in Europe and possible revisions or refinements of it being discussed in the EU.\
|
||||
> [...]\
|
||||
> [Carsten Stöcker](https://medium.com/u/2d7ca4c61292) and [Ricky Thiermann](https://medium.com/u/16518b469d1e) were in Bonn attended the High-Tech Partnering Conference [#HTPC20](https://www.htpc-htgf.de/en-gb/home) organized by our lead investor [High-Tech Gründerfonds](https://high-tech-gruenderfonds.de/en/the-decentralized-identity-and-digital-twin-pioneer-spherity-receives-seed-financing-from-htgf/) (HTGF). Carsten had a keynote about “How to unlock the untapped business potential of IOT devices with digital identity”. Further we were able to exchange with the other start-ups of High-Tech Gründerfonds’ portfolio and to establish relations to HTGF’s industry and corporate partners.\
|
||||
> [...]\
|
||||
> At the end of January, [Juan Caballero](https://medium.com/u/7da78f634e80) and [Carsten Stöcker](https://medium.com/u/2d7ca4c61292) were in Amsterdam, attending the specification-writing face-to-face meeting of the Worldwide Web Consortium’s Decentralized Identifier Working Group (W3C DID-WG). [...] The main event at this meeting was the renegotiation of the limits and interoperability of [DID Documents](https://medium.com/spherity/ssi101-what-exactly-gets-written-to-a-blockchain-69ef1a88fa3c), which has become a sticking point in recent months due to the complexity of ongoing development based on different encodings (traditional JSON, JSON-LinkedData, CBOR, and even ASN.1 and PDF).\
|
||||
> [...]\
|
||||
> On 31st January [Marius Goebel](https://medium.com/u/3a23dedbeb33) attended the steering committee of the “Standardization Roadmap Artificial Intelligence” for the German Federal Ministry of Economics and Energy ([BMWi](https://www.bmwi.de/Navigation/EN/Home/home.html)) hosted by [DIN](https://www.din.de/en) [German Institute for Standardization] and [DKE](https://www.dke.de/en) [German Commission for Electrical, Electronic & Information Technologies].\
|
||||
> [...]\
|
||||
> [Sphertiy](http://www.spherity.com/) is contributing to the working groups around the fields of “IT security in artificial intelligence (AI) systems” and “Certification and quality of AI systems” delivering its expertise in the fields of digital identities, in particular auditability, authenticity, traceability and identifiability of data and artificial intelligences (AIs).
|
||||
|
||||
* [Spherity joins VSDI (Secure Digital Identity Association)](https://medium.com/spherity/spherity-joins-vsdi-secure-digital-identity-association-101d160d267f)
|
||||
> Membership in the association allows [Spherity](http://www.spherity.com/) to participate in consultative processes around future tenders and initiatives, keeping us up to date on the needs of government digitization and the trends moving through state and federal bodies on these topics. It also fosters communication with companies working in specialized fields like military information technology, public services computing, finance, and cross-border issues.
|
||||
>
|
||||
> The VSDI sees itself as a practice-oriented competence network for politics, administration and business. The association communicates the bundled expertise of its members and advocates through its initiatives to enable secure, user-friendly and data protection-compliant digital identities.
|
||||
|
|
@ -5,64 +5,17 @@ name: HylandCreds
|
|||
description: The world leader in blockchain-secured digital records that are recipient owned, vendor independent, and verifiable anywhere.
|
||||
excerpt: >
|
||||
Hyland Credentials started as Learning Machine, a startup that architected the Blockcerts open standard with the MIT Media Lab and co-chaired of the W3C Credentials Community Group. Since that inception, we’ve become the global leader in blockchain-based digital credentials. As the only records provider in the world with a product in market for multi-chain issuing and self-sovereign identity, our offering is revolutionizing the way organizations around the world issue and verify records.
|
||||
layout: single
|
||||
layout: companies
|
||||
permalink: companies/hyland-credentials-learning-machine/
|
||||
canonical_url: 'https://decentralized-id.com/companies/hyland-credentials-learning-machine/'
|
||||
categories: ["Companies"]
|
||||
tags: ["Highland Credentials","DIF","Learning Machine","Blockcerts","Verifiable Credentials","W3C"]
|
||||
tags: ["DIF","Learning Machine","W3C","Highland Credentials"]
|
||||
tech: ["Blockcerts"]
|
||||
standards: ["Verifiable Credentials"]
|
||||
header:
|
||||
image: /images/learning-machine-hyland.webp
|
||||
teaser: /images/hyland-teaser.webp
|
||||
last_modified_at: 2020-11-08
|
||||
toc: false
|
||||
last_modified_at: 2023-02-20
|
||||
toc: true
|
||||
---
|
||||
|
||||
[Twitter](https://twitter.com/HylandCredent) • [Blog](https://www.hylandcredentials.com/blog/) • [Community](http://community.blockcerts.org/)
|
||||
|
||||
* [Why Hyland Credentials](https://www.hylandcredentials.com/our-approach/)
|
||||
> Your organization will find that an engagement with Hyland Credentials is a lot more than buying software, we address the needs of your whole organization. We look forward to working with you to make secure, digital credentialing an enduring part of your institution’s legacy.
|
||||
|
||||
## Hyland
|
||||
|
||||
> [Hyland](https://www.hyland.com/) is a leading content services provider that enables thousands of organizations to focus on what they do best and deliver better experiences to the people they serve. A new Forrester Consulting study says “content is critical to improving the customer experience, but few are able to leverage its full potential.” Learn to leverage your full potential with Hyland.
|
||||
|
||||
### Forester Study
|
||||
|
||||
* [Study: Optimizing use of content is critical to enhancing customer experiences](https://www.hyland.com/en/learn/it-programs/forrester-content-at-your-service-wp)
|
||||
> According to a new commissioned study conducted by Forrester Consulting, organizations recognize that “content is critical to improving the customer experience, but few are able to leverage its full potential.”
|
||||
|
||||
### Hyland Acquires Learning Machine
|
||||
* [Hyland acquires blockchain-credentialing provider Learning Machine](https://news.hyland.com/hyland-acquires-blockchain-credentialing-provider-learning-machine)
|
||||
> Hyland, a leading content services provider, announced its acquisition of Learning Machine, an innovator in blockchain-anchored digital credentialing solutions. The acquisition was effective February 1, 2020.
|
||||
|
||||
## Learning Machine Blog
|
||||
* [Remaking Credentials](https://www.hylandcredentials.com/remaking-credentials/)
|
||||
> When desktop computers came into the workplace 25 years ago, the problem of paper remained. How could print layouts be shared and displayed across a variety of electronic machines and operating systems? The most prominent solution that emerged was Adobe’s Portable Document Format (PDF), a proprietary solution released in the 1990’s as a way to share documents that included text formatting and in-line images. Even though more features were added over time, in essence, PDFs operated as a paper analogue for computers.
|
||||
* [A Passport to Greater Opportunity](https://www.hylandcredentials.com/passport-greater-opportunity/)
|
||||
> One of the earliest challenges of statecraft was developing a legible view of its populations. Translating local complexities into simple and summary descriptions was necessary to enable traditional state functions like taxation and planning. This need to describe impelled various standardization efforts, including permanent last names, land registries, and population surveys, which gave society a visible shape that could be centrally recorded and used within legal frameworks to wield state power.
|
||||
* [Badges and Blockcerts](https://www.hylandcredentials.com/badges-and-blockcerts/)
|
||||
> Education and training providers have long been wrestling with the legacy of the credit hour and how to adapt credentialing to a modern world that values skills more than time spent in the classroom. This is in part why the industry has seen an explosion of traditional and alternative providers that are experimenting with new credential formats appropriate for the information age. One of the questions we most frequently encounter at Learning Machine from these providers is: What are the differences between different credentials formats? The implicit question behind that one is: When should I use different types of digital credentials, and why?
|
||||
* [Credential (n.)](https://www.hylandcredentials.com/credential-n/)
|
||||
> *Summary of MIT and Learning Machine co-presenting verifiable digital credentials at EDUCAUSE 2018 in Denver Colorado*.\
|
||||
> [...]\
|
||||
> Former FBI agent Allen Ezell, and John Bear, Ph.D., have written a book that focuses on corruption within academic credentialing titled, [Degree Mills: The Billion-Dollar Industry That Has Sold Over a Million Fake Diplomas](https://www.cbsnews.com/news/your-md-may-have-a-phony-degree/). Of course, loss of trust in these formats has resulted in byzantine processes for the transmission and verification of records that is inconvenient and expensive for everyone involved. This is why MIT and Learning Machine started working together in 2016, to make a new kind of digital record that restores trust in credentials like academic records. The result was launching [Blockcerts.org](http://www.blockcerts.org)
|
||||
* [Digital Identity](https://www.hylandcredentials.com/digital-identity/)
|
||||
> A framework for organizing the categories of digital identity and an analysis of where disruptive innovation is most likely to succeed.\
|
||||
> [...]\
|
||||
> Learning Machine has made the strategic choice to disrupt paper documents with verifiable digital records (software), rather than competing directly within the traditional identity space. The following analysis explains why. Note that some startup challengers will be named as exemplars in their categories, which is not meant to imply any criticism of those companies. In fact, many of these companies are collaborating behind the scenes on data standards that will form a common foundation for future interoperability.
|
||||
* [Flexible Systems](https://www.hylandcredentials.com/flexible-systems)
|
||||
> Top-down initiatives to reconstruct entire sectors like digital identity are too brittle to succeed. Flexible systems require a different mindset.\
|
||||
> [...]\
|
||||
> unlike every other sector (media, communications, engineering, finance, etc.), official records largely rely on old formats like paper, wax, and PDF for certification, all of which are hard to verify and easy to fake. This is big reason why public blockchains are exciting, because they have the power to prove the authenticity, ownership, and integrity of a natively digital record. The combination of strong cryptography and public blockchains provide a new technical infrastructure that gives people the ability to manage their own records of achievement in a format that is digital, easily shared, and instantly verifiable using a global verification network.
|
||||
* [Why Use a Blockchain?](https://www.hylandcredentials.com/why-use-a-blockchain/)
|
||||
> Everyone wants digital records to be shareable and verifiable, but it is only now that we have the technical infrastructure to reliably accomplish that goal. The innovation that makes this possible is blockchain-enabled networks that synchronize around a single truth. While digital signatures and public key infrastructure (PKI) are important pieces of a secure credentialing solution, it is the addition of a decentralized verification network that adds the highest level of security, longevity, and recipient ownership to digital records.
|
||||
* [Hosted ≠ Verified](https://www.hylandcredentials.com/hosted-%e2%89%a0-verified/)
|
||||
> Have you ever seen a person’s certification listed on LinkedIn, and then followed the link to the actual credential? It typically resides on the domain of a software vendor, or on the domain of the issuing institution, with the intention of communicating authenticity. While hosted credentials provide convenience for both credential holders and verifiers, hosting is not enough to provide a secure basis for verification.
|
||||
|
||||
## DHS Funding
|
||||
|
||||
* [Learning Machine wins DHS Grant to align Blockcerts with the W3C specifications for Verifiable Credentials and Decentralized Identifiers.](https://www.hylandcredentials.com/future-proof)
|
||||
> Today, **Learning Machine** is proud to announce that we have won Phase-1 funding for our response to the open call “Preventing Forgery & Counterfeiting of Certificates and Licenses through the use of Blockchain and Distributed Ledger Technology.” The purpose of the call was to develop vendor-neutral technology solutions that prevent the forgery and counterfeiting of official records for immigration, travel, visas, and other use cases pertaining to national and citizen security. Our grant application addressed DHS requirements by proposing an upgrade to the Blockcerts open standard, making it capable of issuing W3C Verifiable Credentials.
|
||||
* [DHS Awards 159K for Infrastructure to Prevent Credential Fraud](https://www.dhs.gov/science-and-technology/news/2019/11/12/news-release-dhs-awards-159k-prevent-credential-fraud)
|
||||
> Phase 1 award project “Leveraging **Learning Machine**’s Commercial Offering in Public Infrastructure for Fraud Prevention” will adapt their current commercial technology using the open-source Blockcerts standard to support emerging global World Wide Web Consortium (W3C) security, privacy and interoperability standards such as decentralized identifiers (DID) and verifiable credentials for credential issuance and verification solutions. The proposed approach enables credential user and DID provider independence from vendor-specific accounts to access credentials and promotes holder control and interoperability.
|
||||
|
||||
|
|
|
|||
|
|
@ -7,59 +7,18 @@ excerpt: >
|
|||
We make it easy to implement Self-Sovereign Identity based on Decentralized Identifiers (DIDs) and Verifiable Credentials (VCs), a new digital identity standard. Our software is based on the open-source Hyperledger Aries project, to which we are a primary contributor.
|
||||
|
||||
Together with proper governance, SSI enables, for the first time, the Trust over IP (ToIP) stack. Once trust can effectively be conveyed over IP, a tremendous number of opportunities arise in every industry vertical imaginable. We build the tools to help you capitalize on this opportunity.
|
||||
layout: single
|
||||
layout: companies
|
||||
permalink: companies/trinsic/
|
||||
canonical_url: 'https://decentralized-id.com/companies/trinsic/'
|
||||
categories: ["Companies"]
|
||||
tags: ["Trinsic","DIF","Sovrin Foundation","Verifiable Organizations Network","Covid Credentials","Trust over IP","Hyperledger Foundation","DID","Aries","Verifiable Credentials","W3C"]
|
||||
tags: ["DIF","Sovrin Foundation","Verifiable Organizations Network","Covid Credentials","Trust over IP","Hyperledger Foundation","Verifiable Credentials","W3C"]
|
||||
standards: ["Verifiable Credentials","DID"]
|
||||
tech: ["Aries","Indy"]
|
||||
use: ["ID","Software"]
|
||||
|
||||
header:
|
||||
image: /images/trinsic_banner.webp
|
||||
teaser: /images/trinsic_teaser.webp
|
||||
last_modified_at: 2020-11-08
|
||||
toc: false
|
||||
last_modified_at: 2023-02-20
|
||||
toc: true
|
||||
---
|
||||
|
||||
**[Website](https://trinsic.id/) • [Blog](https://trinsic.id/blog/) • [Twitter](https://twitter.com/trinsic_id) • [Linkedin](https://www.linkedin.com/company/trinsic-id/) • [Wallet](https://trinsic.id/trinsic-wallet/) • [Studio](https://trinsic.id/trinsic-studio/) - [Docs](https://docs.trinsic.id/docs)**
|
||||
|
||||
> We make it easy to implement Self-Sovereign Identity based on Decentralized Identifiers (DIDs) and Verifiable Credentials (VCs), a new digital identity standard. Our software is based on the open-source Hyperledger Aries project, to which we are a primary contributor.
|
||||
|
||||
> Together with proper governance, SSI enables, for the first time, the Trust over IP (ToIP) stack. Once trust can effectively be conveyed over IP, a tremendous number of opportunities arise in every industry vertical imaginable. We build the tools to help you capitalize on this opportunity.
|
||||
|
||||
## Blog
|
||||
|
||||
* [Trinsic Introduces Interactive Connections in Trinsic Wallet & Platform](https://trinsic.id/interactive-connections/)
|
||||
> Current digital wallet implementations fall short of the vision of self-sovereign identity (SSI) because they only allow wallet holders to respond to, not initiate, interactions with institutions. This reduces wallet holders to a passive role, which at best delivers suboptimal utility to the holder, and at worst can reinforce the unhealthy power asymmetries between institutions and people that exist today.
|
||||
>
|
||||
> Interactive connections solve this problem by creating a two-way street between a wallet holder and an institution. Instead of a passive responder, the wallet holder is a peer who can initiate actions of their own. In addition, wallet holders can interact not only with institutions, but also with other wallet holders, to communicate securely and share verified information.
|
||||
* [Webinar Recap: Making Money with SSI](https://trinsic.id/webinar-recap-making-money-with-ssi/)
|
||||
> In our recent expert-panel webinar, “Making Money with SSI,” we dive in to the details of creating a business out of SSI from experts who’ve done it. Whether you missed the webinar or just want to refer back to the best parts, we’ve got you covered with a full recording. Scroll below the recording to view a highlight reel!
|
||||
* [Trinsic Cements its Commitment to Interoperability Ahead of Internet Identity Workshop XXXI](https://trinsic.id/trinsic-commitment-to-interoperability-ahead-of-iiw/)
|
||||
> Interoperability has always been of paramount importance to Trinsic. That story begins at an [IIW #28 demo](https://vonx.io/how_to/iiwbook) with the Government of British Columbia where we demonstrated the first mobile app and enterprise SSI platform to comply with the Hyperledger Aries RFCs, achieving interoperability with the open source ariescloudagent-python. This was the first time two separate codebases demonstrated true interoperability.
|
||||
* [Trinsic & Zapier Partner to Bring SSI to 2000+ Applications](https://trinsic.id/trinsic-and-zapier-partner/)
|
||||
> If you’ve interacted with Trinsic much, you know we issue credentials for all sorts of things. Many of those workflows, including the Stripe, Calendly, and Zoom integrations, were done using Zapier and took less than 15 minutes to set up. We even issued our employees an Employee ID credential using Zapier! But we’re not the only ones who love this feature—see how other innovators are using Trinsic and Zapier to make self-sovereign identity a reality.
|
||||
* [Trinsic Basics: The Three Models of Digital Identity](https://trinsic.id/the-three-models-of-digital-identity/)
|
||||
> Digital identity has advanced over time, most recently culminating in self-sovereign identity (SSI). In this Trinsic Basics post, we are going to briefly cover the different models of digital identity and how SSI is the next step in the digital identity evolution. The content in this post is inspired by a [blog post](https://medium.com/evernym/the-three-models-of-digital-identity-relationships-ca0727cb5186) written by digital identity expert Timothy Ruff in 2018.\
|
||||
> 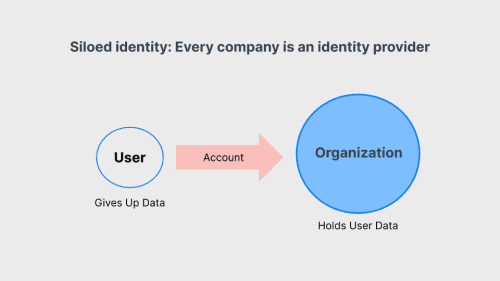
|
||||
* [Combining Verifiable Credentials and Smart Contracts for COVID-19 Data Management](https://trinsic.id/verifiable-credentials-and-smart-contracts-for-covid19-data-management/)
|
||||
> The app is called “State Surveillance System for Covid19 Testing and Vaccine Distribution Management”. It is a prototype app developed using [DAML](https://daml.com/) (Digital Assets Modeling Language) and [W3C’s verifiable credentials](https://www.w3.org/TR/vc-data-model/). The app showcases a prototype solution that provides a digital, secure experience for citizens, health clinic providers, and state agencies to share COVID-19 test results, “proof of vaccine” administration, and other “immunity proofs” using a centralized ledger.
|
||||
* [Trinsic Basics: What Are Decentralized Identifiers (DIDs)?](https://trinsic.id/trinsic-basics-what-are-decentralized-identifiers-dids/)
|
||||
> Most identifiers are given to us by centralized registration authorities like governments, telephone companies, and email providers. But that puts an organization in between us and our ability to access basic services, compromising privacy and putting individuals in a position of powerlessness. The answer to this problem is a [W3C standard](https://www.w3.org/TR/did-core/) called [Decentralized Identifiers](https://www.w3.org/TR/did-core/) (DIDs).
|
||||
* [Simplifying SSI-Based Solutions to Focus on Adoption](https://trinsic.id/simplifying-ssi-based-solutions-to-focus-on-adoption/)
|
||||
> After the COVID-19 pandemic hit the state of Oregon and we shuttered shops and public places, here in my little piece of heaven—the city of Sisters—I went to some of my friends at [Economic Development for Central Oregon](https://edcoinfo.com/covid-19-central-oregon-business-resources/) and told them how I wanted to reopen the Sisters economy without reopening the pandemic. They both loved the idea. Two of my physicians heard me explain how I was planning to accomplish this mission (I wanted to know how medical providers would react). One doctor was enthusiastic, and the other had an arguable HIPAA-allergic reaction.
|
||||
* [Trinsic Basics: What Are SSI Digital Wallets?](https://trinsic.id/what-are-ssi-digital-wallets/)
|
||||
> A digital wallet, in the context of self-sovereign identity, is a software application and encrypted database that stores credentials, keys, and other secrets necessary for self-sovereign identity.³\
|
||||
> 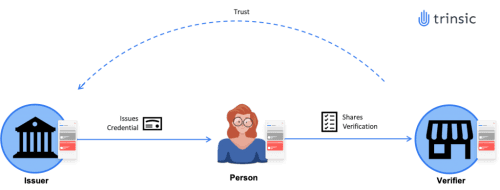
|
||||
* [Trinsic Leads SSI Digital Wallet Portability](https://trinsic.id/ssi-digital-wallet-portability/)
|
||||
> When we talk about wallet portability with other vendors, we mean you can seamlessly transfer your SSI wallet between these different applications by exporting from one wallet and importing into another (“import/export”). With import/export functionality, you are no longer tied to or reliant on a single technology provider.
|
||||
>
|
||||
> “Portability between Aries wallets is a long time coming. It’s a huge win for the vision of SSI,” said Trinsic CEO Riley Hughes. “Import/export should be standard in any SSI wallet—because if a wallet doesn’t support portability, it’s not really self-sovereign.”\
|
||||
> 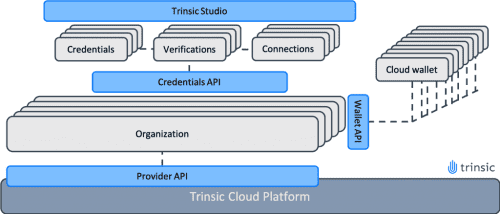
|
||||
* [Call to Action: Verifiable Credentials & COVID-19](https://medium.com/trinsic/call-to-action-verifiable-credentials-covid-19-a180155a157c)
|
||||
> Gates suggests that a digital certificate is needed because it will enable people to share trustworthy information with others. In other words, it is a tool at our disposal to help us reduce uncertainty around the virus. As uncertainty is reduced, additional information enables risk decisions⁴ to be made to ensure our economy doesn’t slip into a total depression. More people can go back to work, [faster](https://www.theguardian.com/world/2020/mar/30/immunity-passports-could-speed-up-return-to-work-after-covid-19).
|
||||
>
|
||||
> Bill Gates’ comment on Reddit caught attention among my colleagues, customers, and partners because there is already a [W3C](https://en.wikipedia.org/wiki/World_Wide_Web_Consortium) technology standard to accomplish this called [verifiable credentials](https://en.m.wikipedia.org/wiki/Verifiable_credentials) (VC). [Hundreds](http://www.sovrin.org/stewards) of organizations, including the largest companies in the world, are using VCs for all sorts of things. Verifiable credentials are like digital certificates but with special superpowers that give people privacy, control, and convenience.
|
||||
* [AgentFramework for .NET joins Hyperledger Aries](https://medium.com/trinsic/agentframework-for-net-joins-hyperledger-aries-14aba357da41)
|
||||
> <img src="https://res.cloudinary.com/identosphere/image/fetch/q_auto:eco,f_auto,w_500/https://cdn-images-1.medium.com/max/1374/1*EinsZ12p8APyf4ZMdfidIg.png"/>\
|
||||
> We’re excited to announce that AgentFramework for .NET — a library for building interoperable SSI agents for the .NET Core runtime, joined the Hyperledger Aries family of frameworks. Aries provides a shared, reusable, interoperable tool kit designed for initiatives and solutions focused on creating, transmitting, and storing verifiable digital credentials.
|
||||
* [The Story of Decentralized Identity](https://medium.com/trinsic/the-case-for-decentralized-identity-820b48527cba)
|
||||
> Most of the time we don’t realize how much our private data is exposed and shared. Often we don’t even question how much information about us we should share to get something. Do you really need all those sensitive details about me to go through even a simple process as a rental application for a tiny apartment? Why do you need to see my bank history to verify I have sufficient income, or see my name and address on my ID to verify I’m over 21? Why do we still rely on physical documents to prove something about us in this age of technological advancement?
|
||||
|
|
@ -1,7 +1,7 @@
|
|||
---
|
||||
date: 2020-11-11
|
||||
title: Tykn Tech
|
||||
name: Tykn
|
||||
title: Tykn Tech
|
||||
description: We envision a world where identities are portable, private and secure, so that no one has to lose access to their identity ever again. Creating a future of opportunity.
|
||||
excerpt: >
|
||||
Why is SSI better?
|
||||
|
|
@ -9,73 +9,16 @@ excerpt: >
|
|||
- A secure and digital peer-to-peer channel is established between ID Issuer, ID Owner and ID Verifier. When credentials are exchanged not even the Self-Sovereign Identity system provider knows what is being exchanged. Credential issuing becomes simpler and faster.
|
||||
- SSI Credentials are tamper-proof through the use of cryptography.
|
||||
- They are private and under your control. SSI uses Selective Identity disclosure technology.
|
||||
layout: single
|
||||
layout: companies
|
||||
permalink: companies/tykn-tech/
|
||||
canonical_url: 'https://decentralized-id.com/companies/tykn-tech/'
|
||||
categories: ["Companies"]
|
||||
tags: ["Tykn","Sovrin Foundation","Indy","Trust over IP","DIACC","Trust Framework"]
|
||||
tags: ["Sovrin Foundation","Trust over IP","DIACC","Founding Sovrin Steward"]
|
||||
tech: ["Indy"]
|
||||
standards: ["Trust Framework"]
|
||||
header:
|
||||
image: /images/tykn_header.webp
|
||||
teaser: /images/tykn_teaser.webp
|
||||
last_modified_at: 2020-11-11
|
||||
toc: false
|
||||
last_modified_at: 2023-02-20
|
||||
toc: true
|
||||
---
|
||||
|
||||
> When on paper it could be easily lost or destroyed. When digital it can be breached, hacked or leaked online. Sold on the black market and used for fraud. Vulnerable people like refugees are just the first to suffer the problems of identity.
|
||||
>
|
||||
> A third of the refugees in Europe are children, and while they are lucky to get documented, hundreds of thousands in Syrian Refugee camps do not have birth certificates, and newborns in camps are unable to complete the birth registration process, due to economic, geographical and complex administrative barriers.
|
||||
>
|
||||
> This and many more experiences of hardship that refugees suffer due to weak and outdated identity systems give Khalid Maliki and Jimmy J.P. Snoek the ongoing inspiration and motivation to lead Tykn’s vision of a future where identities are private and secure. Creating a future of opportunity through digital identity. - [About](https://tykn.tech/about/)
|
||||
|
||||
* [Blockchain Identity Management: The Definitive Guide (2020 Update)](https://tykn.tech/identity-management-blockchain/)
|
||||
> When talking about leveraging blockchain technology for identity management, it’s important to note that there are three different actors in play: **identity owners**, **identity issuers** and **identity verifiers**.
|
||||
>
|
||||
> The **identity issuer**, a trusted party such as local government, can issue personal credentials for an **identity owner** (the user). By issuing a credential, the identity issuer attests to the validity of the personal data in that credential (e.g. last name and date of birth). The identity owner can store those credentials in their personal identity wallet and use them later to prove statements about his or her identity to a third party (**the verifier**).
|
||||
>
|
||||
> A **Credential** is a set of multiple identity attributes and an identity attribute is a piece of information about an identity (a name, an age, a date of birth).
|
||||
>
|
||||
> Credentials are issued by second parties whom attest to the validity of the data inside the credential. The usefulness and reliability of a credential fully depends on the reputation/trustworthiness of the issuer.
|
||||
* [Why is Hyperledger Indy the best solution to start a Self-Sovereign Identity solution on?](https://tykn.tech/hyperledger-indy-self-sovereign-identity/)
|
||||
> Although Hyperledger Indy is still quite young with a lot to be discussed and done, we believe it is by far the best infrastructure to study and to start building in a Self-Sovereign Identity Solution on. Indy has one of the most mature codebase and an engaged community around it, researching, asking questions and working towards the maturity of the ecosystem. Not only are the best people in the identity field working on developing it but also because it’s part of a transparent consortium, a transparent foundation.
|
||||
* [“Changes in The Sovrin Foundation” – Tykn’s Statement](https://tykn.tech/changes-in-the-sovrin-foundation-tykn-statement/)
|
||||
> As you may have possibly [heard/read](https://sovrin.org/the-status-of-the-sovrin-foundation/) by now, due to the recent economic climate, The Sovrin Foundation’s funding model became no longer viable and the Foundation will, until further developments, be relying upon a full volunteer staff.
|
||||
>
|
||||
> Nonetheless, The Sovrin Network is operational.
|
||||
* [Interview with Joni Brennan (President of the Digital ID & Authentication Council of Canada – DIACC)](https://tykn.tech/joni-brennan-diacc-interview/)
|
||||
> Why should a member of the government care about digital identity?\
|
||||
> [...]\
|
||||
> What the DIACC is working on is a framework of industry standards and practices to enable “interoperable networks that will have verifiable data requesters ask for particular attributes to be verified and attribute verifiers to provide that verification” ([3](https://www.youtube.com/watch?v=ahsWWTWI2HM))
|
||||
>
|
||||
> Canadian companies claim they waste more than $10 billion every year on unnecessary bureaucracy ([4](https://www.cfib-fcei.ca/en/media/nearly-one-third-36-billion-cost-regulation-canada-unnecessary-red-tape)). Each Canadian business owner has to use three different tax numbers and navigate three different levels of governmental bureaucracy: local, provincial and federal.
|
||||
>
|
||||
> This interoperable framework – The Pan-Canadian Trust Framework – could enable citizens to start businesses and not deal with so much bureaucracy and have trustworthy transactions online.
|
||||
* [How To Find Private Keys in Hyperledger Indy](https://tykn.tech/how-to-find-private-keys-in-hyperledger-indy/)
|
||||
> It’s important to note that a private key can be used for multiple cryptography purposes. The same private key that generates my identity for Indy (for SSI, for Sovrin) can be used, for example, for a GPG signature for Github. It could be the same key that can be used for Ethereum or Bitcoin to generate an address.
|
||||
>
|
||||
> If the technical infrastructure where you are trying to use your keys accepts the same type of encryption – like Elliptic Curve Cryptography – you could use your Hyperledger Indy private keys there. Structures like HTTPS, Ethereum, Sovrin or Corda, for example, all accept this encryption. Right now it’s not possible to use those Hyperledger Indy’s private keys to establish connections with other parties of a user’s choice.
|
||||
* [Ransomware Attack – How to Prevent](https://tykn.tech/ransomware-attack-how-to-prevent/)
|
||||
> There has been an increase in ransomware attacks here in The Netherlands, mainly targeting SME and Startups. Our Tech Lead, [Eduardo Elias Saleh](https://twitter.com/elias_eti), kindly wrote an internal memo detailing how we should prevent and protect ourselves from a ransomware attack.
|
||||
>
|
||||
> “Security is not something we do once, it’s a culture.” – Eduardo
|
||||
* [Interview with Darrell O’Donnell (Founder at Continuum Loop, CTO at CULedger)](https://tykn.tech/darrell-odonnell-interview/)
|
||||
> What happens when an organization does not own my identity anymore? This is a question that [Darrell O’Donnell](https://twitter.com/darrello) – founder at [Continuum Loop Inc.](https://www.continuumloop.com/), currently CTO at CULedger, investor and advisor at several companies (including Tykn) – has been answering with his work in the Digital Identity space.
|
||||
>
|
||||
> According to Darrell, holding a digital identity database inside an organization is a liability. It’s a huge expense in data management – unless you are Google or Facebook and have a financial incentive to host such a database – and the liability of having an “honey pot” of personal data that could be leaked, hacked or breached is tremendous. As seen, for example, with the Equifax case in which the personal information of 147 million people was exposed.
|
||||
* [Tykn’s 2019: Year In Review](https://tykn.tech/2019-year-in-review/)
|
||||
> We started the year moving offices to The Hague, the city of peace and justice. It made sense not only because of the symbolic value of The Hague but also because of the strong NGO and social impact startup ecosystem. We became proud members of ImpactCity, a community of companies focused on doing business and doing good.
|
||||
* [Interview with Daniel Hardman (Chief Architect at Evernym and Technical Ambassador at Hyperledger)](https://tykn.tech/daniel-hardman-interview/)
|
||||
> We had a chance to ask Daniel a few questions:
|
||||
* > What are, in your opinion, the riskiest assumptions when writing an Software Development Kit?
|
||||
* > For you, what are the most promising SSI projects or repos?
|
||||
* > What do you believe are the bottlenecks for the cross-ledger SSI? How soon can we see cross-ledger credentials exchanges?
|
||||
* > What are the upsides of using Zero MQ over a common HTTP Rest connection?
|
||||
* > How hard would it be to replace the current Transport Layer Security architecture with SSI?
|
||||
* > Why was Rust chosen to write Indy-SDK?
|
||||
* > Specific roadblocks other people in this space should look out for?
|
||||
* > What are the books you have recommended most to others?
|
||||
* [Tykn finds new partner in IT entrepreneur Johan Mastenbroek](https://tykn.tech/tykn-investment/)
|
||||
> The Hague, May 20, 2019 – Tech start-up Tykn has received an investment of 1.2 million euros from Dutch IT entrepreneur Johan Mastenbroek. By using smart technology and blockchain the start-up is developing a digital identity management platform, which allows public and private institutions to issue and verify digital identity credentials. It is an innovative way to share and request personal data proofs, which protects identities against getting lost. A solution for the 1.2 billion people worldwide who have never had an identifying document or whose proof of existence got lost because of inefficient identity registration, wars or disasters.
|
||||
* [Self-Sovereign Identity: The Ultimate Beginners Guide!](https://tykn.tech/self-sovereign-identity/)
|
||||
> Decentralized Identifiers (DIDs) are an integral part of Self-Sovereign Identity. It allows for the creation of unique, private and secure **peer-to-peer** connections between two parties.
|
||||
>
|
||||
> Currently, we are reliant on the identifiers from **intermediaries** such as Google, Facebook, email providers or mobile network operators to connect us. This has big consequences for our privacy, since the **(meta)data** gathered by those parties from the interactions over those connections are **not within our control**.
|
||||
Loading…
Add table
Add a link
Reference in a new issue