mirror of
https://github.com/Decentralized-ID/decentralized-id.github.io.git
synced 2025-12-15 16:39:25 -05:00
reorganize + new categories
This commit is contained in:
parent
654be069ac
commit
5277911d7d
32 changed files with 312 additions and 277 deletions
|
|
@ -60,10 +60,6 @@ last_modified_at: 2023-06-17
|
|||
> So there’s demand for a new category of IoT and #IoMD that survives and thrives despite these challenges. Very low power consumption. Lots of storage and caching to hold on through power outages. Ruggedized for use outside clinics. Easy and cheap to field-repair. Lots of smarts inside so they work without an internet tap. Many flavors of connectivity to exploit opportunities as they knock. Open sourced, the better to adapt to new and unplanned problems.
|
||||
|
||||
## Organization
|
||||
* [Self-Sovereign Digital Twins](https://dlt.mobi/self-sovereign-digital-twins/) 2022-07-08 MOBI
|
||||
> A Citopia Self-Sovereign Digital Twin™ (SSDT™) is a digital twin whose controller has the ability to participate as an autonomous economic agent in trusted Web3 transactions.
|
||||
* [Battery Passport and the Battery Self-Sovereign Digital Twin](https://dlt.mobi/battery-passport-the-battery-ssdt/) 2022-09-28 MOBI
|
||||
> Similarly, a [battery passport](https://dlt.mobi/battery-passport) is nothing but a presentation of data points about a particular battery – who manufactured it, its physical and chemical composition, its current state of health, whether it was refurbished or repurposed from another battery, and so on.
|
||||
* [LFPH tackles the next frontier in Open Source Health Technology: The rise of Digital Twins](https://www.lfph.io/2022/08/29/lfph-tackles-the-next-frontier-in-open-source-health-technology-the-rise-of-digital-twins/) 2022-08-29 Linux Foundation Public Health
|
||||
> To create a pairing between the digital world and the real world, a digital twin leverages real time data, such as smart sensor technology, coupled with analytics, and often artificial intelligence (AI) in order to detect and prevent system failures, improve system performance, and explore innovative uses or functional models.
|
||||
* [SSI In IoT, The SOFIE Project](https://www.thedinglegroup.com/blog/2021/4/6/ssi-in-iot-the-sofie-project) 2021-04-06 The Dingle Group
|
||||
|
|
@ -71,6 +67,18 @@ last_modified_at: 2023-06-17
|
|||
* [Digital Twin Consortium](https://www.digitaltwinconsortium.org/)
|
||||
> Digital Twin Consortium drives the awareness, adoption, interoperability, and development of digital twin technology. Through a collaborative partnership with industry, academia, and government expertise, the Consortium is dedicated to the overall development of digital twins. We accelerate the market by propelling innovation and guiding outcomes for technology end-users.
|
||||
|
||||
### MOBI
|
||||
|
||||
* [Self-Sovereign Digital Twins](https://dlt.mobi/self-sovereign-digital-twins/) 2022-07-08 MOBI
|
||||
> A Citopia Self-Sovereign Digital Twin™ (SSDT™) is a digital twin whose controller has the ability to participate as an autonomous economic agent in trusted Web3 transactions.
|
||||
* [Battery Passport and the Battery Self-Sovereign Digital Twin](https://dlt.mobi/battery-passport-the-battery-ssdt/) 2022-09-28 MOBI
|
||||
> Similarly, a [battery passport](https://dlt.mobi/battery-passport) is nothing but a presentation of data points about a particular battery – who manufactured it, its physical and chemical composition, its current state of health, whether it was refurbished or repurposed from another battery, and so on.
|
||||
* [MOBI Web3 Technology Stack](https://dlt.mobi/web3-infrastructure/) Mobi
|
||||
> A Self-Sovereign Digital Twin™ (SSDT) is a digital twin which is anchored in a decentralized trust network using W3C’s DIDs)Standard (for MOBI’s community, this is the Integrated Trust Network, or ITN). By using the SSDT and W3C’s VC Standard, the controller of the SSDT can participate as an autonomous economic agent in trusted transactions through issuing VCs and Verifiable Presentations (VPs). For MOBI’s community, this is done using Citopia Marketplace. Citopia utilizes the network effect and Zero-Knowledge (ZK); allows for the onboarding of SSDT; and enables VCs and VPs.
|
||||
> * [Mobility Data Space](https://mobility-dataspace.eu/)
|
||||
> * [Standards - MOBI](https://dlt.mobi/standards/)
|
||||
> * [Working Groups - MOBI](https://dlt.mobi/mobi-working-groups/)
|
||||
|
||||
## Company Stories
|
||||
* [More Security in the Internet of Things – Thanks to ETO](https://www.etogruppe.com/en/news/news-from-eto/more-security-in-the-internet-of-things-thanks-to-eto.html) 2022-09-16 ETO [github](https://gitlab.com/anchor-bundle/angular-webapp)
|
||||
> The ETO GRUPPE has set itself the goal of automating communication in the Internet of Things (IoT) and, on top of that, making it more secure against access and manipulation. To achieve this, these "things" - machines, devices or vehicles - must first be given a unique identity. The solution of the innovative corporate group consists of a new type of network and authentication processes that have what it takes to revolutionize the way we use the Internet today. ETO uses a network of distributed digital identities (DIDs) and verifiable credentials (VCs). A side benefit from the perspective of human Internet users: they regain data sovereignty over their personal data. The ETO solution will enable secure logins on both the Internet and the Internet of Things (IoT)
|
||||
|
|
|
|||
|
|
@ -15,7 +15,7 @@ redirect_from:
|
|||
- id-initiatives/ethereum/
|
||||
- ethereum.html
|
||||
- ethereum/
|
||||
categories: ["Blockchain ID"]
|
||||
categories: ["Blockchains"]
|
||||
tags: ["Ethereum","Jolocom","Web3","Transmute","uPort","3box","Verifiable Credentials","OASIS","Microsoft","Consensys","Enterprise Ethereum Alliance","ERC725","Nuggets","Sidetree"]
|
||||
last_modified_at: 2020-11-05
|
||||
|
||||
|
|
@ -14,7 +14,7 @@ redirect_from:
|
|||
- blockchain/bitcoin
|
||||
- id-initiatives/bitcoin/
|
||||
- id-initiatives/bitcoin
|
||||
categories: ["Blockchain ID"]
|
||||
categories: ["Blockchains"]
|
||||
tags: ["Bitcoin","Blockchain","Microsoft","History","ION","BTCR","XDI","W3C","Ethereum","RWoT"]
|
||||
last_modified_at: 2020-01-07
|
||||
|
||||
|
|
|
|||
|
|
@ -8,7 +8,7 @@ layout: single
|
|||
header:
|
||||
image: /images/blockstack_header.webp
|
||||
teaser: /images/blockstack_teaser.webp
|
||||
categories: ["Blockchain ID"]
|
||||
categories: ["Blockchains"]
|
||||
tags: [Blockstack,Bitcoin,DID,Blockchain]
|
||||
permalink: blockchain/blockstack/
|
||||
toc: false
|
||||
|
|
|
|||
|
|
@ -8,7 +8,7 @@ header:
|
|||
teaser: /images/veres_one-teaser.webp
|
||||
layout: single
|
||||
permalink: /blockchain/veres-one/
|
||||
categories: ["Blockchain ID"]
|
||||
categories: ["Blockchains"]
|
||||
tags: ["Blockchain","Veres One","Verifiable Credentials","DID","Digital Bazaar","Veres One CG","W3C"]
|
||||
last_modified_at: 2020-11-10
|
||||
toc: false
|
||||
|
|
|
|||
|
|
@ -7,7 +7,7 @@ excerpt: >
|
|||
layout: single
|
||||
permalink: blockchain/ontology/
|
||||
canonical_url: 'https://decentralized-id.com/blockchain/ontology/'
|
||||
categories: ["Blockchain ID"]
|
||||
categories: ["Blockchains"]
|
||||
tags: ["Blockchain","Ontology","Ethereum","NEO","Polkadot","Microsoft","Consensys","Verifiable Credentials","Universal Resolver"]
|
||||
header:
|
||||
image: /images/ontology_header.webp
|
||||
|
|
|
|||
|
|
@ -7,7 +7,7 @@ excerpt: >
|
|||
layout: single
|
||||
permalink: blockchain/dragonchain-factor/
|
||||
canonical_url: 'https://decentralized-id.com/blockchain/dragonchain-factor/'
|
||||
tags: [Dragonchain,Blockchain]
|
||||
tags: ["Dragonchain","Blockchain"]
|
||||
header:
|
||||
image: /images/dragonchain-factor-header.webp
|
||||
teaser: /images/dragon-teaser.webp
|
||||
|
|
|
|||
|
|
@ -4,7 +4,7 @@ title: Ethereum Oasis Open Project • Baseline Protocol
|
|||
description: To develop clear, open standards, high-quality documentation, and shared test suites that facilitate new features and enhancements to the Ethereum protocol.
|
||||
excerpt: >
|
||||
The Ethereum OASIS Open Project is an OASIS Open Project that exists to provide a neutral forum for diverse stakeholders to create high-quality specifications that facilitate Ethereum’s longevity, interoperability, and ease of integration. The Ethereum OASIS Project intends to develop clear, open standards, high-quality documentation, and shared test suites that facilitate new features and enhancements to the Ethereum protocol.
|
||||
categories: ["Blockchain ID"]
|
||||
categories: ["Web 3","Open Source Projects"]
|
||||
tags: ["OASIS","Ethereum","Enterprise Ethereum Alliance","Ethereum Foundation","Consensys","Chainlink","Provide","Unibright","Ernst & Young","Microsoft","Limechain"]
|
||||
last_modified_at: 2020-12-01
|
||||
header:
|
||||
|
|
|
|||
|
|
@ -9,7 +9,7 @@ excerpt: >
|
|||
layout: single
|
||||
permalink: blockchain/iota-foundation/
|
||||
canonical_url: 'https://decentralized-id.com/blockchain/iota-foundation/'
|
||||
category: ["Blockchain ID"]
|
||||
category: ["Blockchains"]
|
||||
tags: ["IOTA","Blockchain","Dark Matter Labs","Eclipse"]
|
||||
header:
|
||||
image: /images/iota-identity.webp
|
||||
|
|
|
|||
|
|
@ -8,7 +8,7 @@ layout: single
|
|||
toc: false
|
||||
permalink: blockchain/cosmos/
|
||||
canonical_url: 'https://decentralized-id.com/blockchain/cosmos/'
|
||||
categories: ["Blockchain ID"]
|
||||
categories: ["Blockchains"]
|
||||
tags: ["Cosmos","oCap","Commercio"]
|
||||
last_modified_at: 2020-11-19
|
||||
header:
|
||||
|
|
|
|||
|
|
@ -15,7 +15,7 @@ redirect_from:
|
|||
- rebooting-web-of-trust
|
||||
- rebooting-web-of-trust/
|
||||
toc_sticky: false
|
||||
categories: ["Web Standards","Literature","Events"]
|
||||
categories: ["Resources","Events"]
|
||||
tags: ["RWoT","Bitcoin","Ethereum","DID","DPKI","Verifiable Credentials","Consensys","Blockstack","JSON-LD","Data Hubs","Self Sovereign Identity","eIDAS","Blockcerts","GDPR","PGP","Veres One","W3C","XDI","BTCR","California","DKMS","Digital Bazaar","IPID"]
|
||||
last_modified_at: 2020-10-10
|
||||
---
|
||||
|
|
|
|||
|
|
@ -14,7 +14,7 @@ redirect_from:
|
|||
- hgf-2018
|
||||
- hgf-2018/
|
||||
categories: ["Events"]
|
||||
tags: ["Hyperledger Forum","GDPR","MyCuID","Sovrin Foundation","DigiCert","Indy","Fabric","Blockcerts","Evernym","R3","Verifiable Organizations Network","CULedger","ATB","Switzerland"]
|
||||
tags: ["Hyperledger Forum","GDPR","MyCuID","Sovrin Foundation","DigiCert","Indy","Fabric","Blockcerts","Evernym","R3","Verifiable Organizations Network","CULedger","ATB","Switzerland","HGF 2018"]
|
||||
last_modified_at: 2019-03-06
|
||||
header:
|
||||
image: /images/hyperledger-global-forum-header.webp
|
||||
|
|
|
|||
|
|
@ -17,7 +17,7 @@ redirect_from:
|
|||
- government/canada/von/hgf-2018-presentation/
|
||||
permalink: /government/canada/bcgov/von/hgf-2018-production-government-deployment-hyperledger-indy/
|
||||
categories: ["Regional","History"]
|
||||
tags: ["Indy","Verifiable Organizations Network","Verifiable Credentials","Canada","BCGov","Hyperledger Forum","W3C","Transcript","Real World"]
|
||||
tags: ["HGF 2018","Indy","Verifiable Organizations Network","Verifiable Credentials","Canada","BCGov","Hyperledger Forum","W3C","Transcript","Real World"]
|
||||
last_modified_at: 2019-07-11
|
||||
---
|
||||
|
||||
|
|
|
|||
|
|
@ -188,7 +188,7 @@ Markus Sabadello began work on Project Danube, on the creation of an XDI based p
|
|||
|
||||
* [Top Bitcoin Companies Propose the Windhover Principles - A New Dig...](https://www.ccn.com/top-bitcoin-companies-propose-windhover-principles-new-digital-framework-digital-identity-trust-open-data/)
|
||||
> ID3, founded out of the MIT Media Lab, has teamed up with nearly two dozen leading digital currency firms to announce the Windhover Principles. ID3 is a research and educational nonprofit with a mission to develop a new social ecosystem of trusted digital institutions. The Wi...
|
||||
* [The Windhover Principles for Digital Identity, Trust, and Data](https://www.tokencommons.org/Windhover-Principles-for-Digital-Identity-Trust-Data.html)
|
||||
* [The Windhover Principles for Digital Identity, Trust, and Data](https://www.scribd.com/document/335386296/Windhover-Principles)
|
||||
> Today we communicate, share and transact digitally over the Internet. Individuals who make use of the Internet for these purposes should have control over their digital
|
||||
* [HubID First to Deploy Windhover Principles and Framework for Digit...](https://hubculture.com/hubs/47/news/689/)
|
||||
> HubID, (the self-sovereign digital identity system at the core of Hub Culture and the Ven currency) is the first consumer application to deploy the Windhover Principles and features new frameworks for digital identity, trust and open data. The core technology has been in deve...
|
||||
|
|
|
|||
|
|
@ -1,12 +1,11 @@
|
|||
---
|
||||
date: 2020-12-09
|
||||
title: "The Dataweb: An Introduction to XDI"
|
||||
description: XRI Data Interchange is a service for generalized distributed data sharing and mediation
|
||||
excerpt: >
|
||||
The goal of XDI is to enable data from any data source to be identified, exchanged, linked, and synchronized into a machine-readable dataweb using XML documents just as content from any content source can linked into the human-readable Web using HTML documents today. Because the controls needed to mediate access and usage of shared data can be built right into every XDI link, the emergence of a global Dataweb has the potential to do for trusted data interchange what the Web did for open content exchange.
|
||||
last_modified_at: 2020-12-09
|
||||
permalink: /literature/dataweb-introduction-to-xdi/
|
||||
categories: ["Literature"]
|
||||
categories: ["History"]
|
||||
tags: ["XRI","XDI","Dataweb","Literature","History"]
|
||||
header:
|
||||
og_image: /images/dataweb/dataweb-og.webp
|
||||
|
|
|
|||
|
|
@ -1,114 +0,0 @@
|
|||
---
|
||||
date: 2018-12-18
|
||||
title: A Comparison Between SSI Principles, and Characteristics
|
||||
excerpt: >
|
||||
'No disrespect to Christopher Allen’s opening to the conversation, The Path to Self Sovereign Identity ‐ Christopher Allen 2016 http://www.lifewithalacrity.com/2016/04/the‐path‐to‐self‐soverereign‐identity.html
|
||||
|
||||
It gets a lot right, but leaves a few requirements out, e.g., recoverability and zero cost, and conflates “identities” and claims in an ambiguous manner. Chris clearly intended the paper would start the conversation; it has done a good job at that.'
|
||||
layout: single
|
||||
toc: false
|
||||
permalink: /literature/self-sovereign-identity/ssi-principles-vs-characteristics/
|
||||
canonical_url: 'https://decentralized-id.com/literature/self-sovereign-identity/ssi-principles-vs-characteristics/'
|
||||
redirect_from:
|
||||
- /self-sovereign-identity/ssi-principles-vs-characteristics
|
||||
- /self-sovereign-identity/ssi-principles-vs-characteristics/
|
||||
categories: ["Literature"]
|
||||
tags: ["Self Sovereign Identity","RWoT","Laws of Identity","Literature","notes","UNSDGs","Windhover Principles","History"]
|
||||
last_modified_at: 2020-01-05
|
||||
published: true
|
||||
|
||||
---
|
||||
|
||||
|
||||
In April of 2016, Christopher Allen published "[The Path to Self Sovereign Identity](https://github.com/WebOfTrustInfo/self-sovereign-identity/blob/master/ThePathToSelf-SovereignIdentity.md)."
|
||||
|
||||
>The idea of digital identity has been evolving for a few decades now, from centralized identities to federated identities to user-centric identities to self-sovereign identities. However, even today exactly what a self-sovereign identity is, and what rules it should recognize, aren’t well-known.
|
||||
>
|
||||
>This article seeks to begin a dialogue on that topic, by offering up a definition and a set of principles as a starting point for this new form of user-controlled and persistent identity of the 21st century.
|
||||
|
||||
His article details the history of digital identity standards, and the user experience accompanying those standards. After describing from where we've come, Allen draws from leading thought on digital identity to compose the [Principles of Self Sovereign Identity](https://github.com/WebOfTrustInfo/self-sovereign-identity/blob/master/self-sovereign-identity-principles.md).
|
||||
|
||||
That October, [Joe Andrieu](https://github.com/jandrieu) submitted [A Technology‐Free Definition of Self‐Sovereign Identity](https://github.com/jandrieu/rebooting-the-web-of-trust-fall2016/raw/master/topics-and-advance-readings/) to the third Rebooting the Web of Trust Design Workshop.
|
||||
|
||||
>1 No disrespect to Christopher Allen’s opening to the conversation, The Path to Self Sovereign Identity [...] It gets a lot right, but leaves a few requirements out, e.g., recoverability and zero cost, and conflates “identities” and claims in an ambiguous manner.
|
||||
|
||||
Andrieu explores what people need from self-sovereign identity, independant from technology. An important consideration, for Joe, is realizing UN Sustainable Development Goal 16.9 “Providing every last person on the planet with a legal identity by 2030."
|
||||
|
||||
>In order to fund, co‐develop, and eventually deploy a global self‐sovereign solution to UN Sustainable Development Goal 16.9, it would be prudent to begin with an explicit requirements process independent of any specific technology.
|
||||
|
||||
In conclusion, we are offered : **Control**. **Acceptance**. **Zero Cost**.
|
||||
|
||||
I'd like to review the <i>the fundamental characteristics of self‐sovereign identity</i> as detailed by Joe Andreiu, and compare each of the <i>principles</i> individually to ensure that all of the essentials are considered.
|
||||
|
||||
---
|
||||
|
||||
### Fundamental Characteristics of Self-Sovereign Identity
|
||||
|
||||
#### CONTROL
|
||||
* **Self‐sovereign identities are controlled by the individual:**
|
||||
* **Self‐generatable and Independent:** Individuals must be able to create identity information without asking for permission and be able to assert identity information from any authority. The resulting identity must have the same technical reliability as those provided by well‐known, “official” sources. The observer, of course, is always free to decide whether or not a given piece of information is meritorious, but the information must be able to be verified as a non‐repudiatable statement of correlation using exactly the same mechanisms regardless of source. Further, individuals must be able to present self‐generated identity information without disclosing that the authority in the claim is the subject of the claim.
|
||||
* **Opt‐in**: The affordance for asserting identity information starts with the individual. While an individual may present claims from known or accepted third party authorities, it is the individual who asserts that the claim applies to them. Self‐sovereign identities begin with the will of the individual, with the intentional presentation of identity information.
|
||||
* **Minimal Disclosure**: Individuals should be able to use services with minimal identity information. Features that depend on enhanced correlation must be understood by the average user. Such features should be permissioned with the highest granularity, so functions independent of correlation work equally well alongside those dependent on it. It is not acceptable to deny services because of a refusal to provide unrelated information.
|
||||
* **Non‐participation**: Individuals must be able to choose to not provide identity information for services where it isn’t absolutely required. Any spontaneous identifiers necessary for a service to function, such as cookies or session ids, must use the same infrastructure for consent, persistence, transience, and disclosure as if provided by the individual.
|
||||
* **Opt‐out**: Individuals should be able to opt‐out of identifying records post‐facto as a matter of course. People should be able to stop the use of a correlating identity information by request. Some transactions necessarily require long term retention of identity information, such as financial transactions, purchases, and shipments. Actions that create permanent records should be clearly marked and communicated such that the retention is expected and understood by the average person. All other actions which leverage a self‐sovereign identity should be de‐correlated on‐demand and said identifiers should no longer be used to correlate that individual across contexts.
|
||||
* **Recoverable**: Sovereign identities must be robust enough to be recovered even if hard drives are lost, wallets stolen, or birth certificates lost in a fire. Self‐sovereign identities must provide a way for individuals to recover and reassert that existing identify information applies to them even in the face of complete loss of credentials. This may be challenging given current technical proposals, but the point of this paper is to explore the non‐technical requirements of a self‐sovereign identity. To fully address the needs of UN Sustainable Development Goal 16.9, identity assurance can’t depend on pieces of paper, devices, or other artifacts that can be lost, stolen, destroyed, and falsified.
|
||||
|
||||
#### ACCEPTANCE
|
||||
* **Self‐sovereign identities are accepted wherever observers correlate individuals across contexts.**
|
||||
* **Standard**: There is an open, public standard managed through a formal standards body, free to use by anyone without financial or intellectual encumbrance. Simple The core standard (schema, serialization, and protocols) must be atomically minimal, providing the barest data set, allowing complexity to emerge not from a complicated data model but from a multiplicity of information types, authorities, and observations.
|
||||
* **Non‐repudiatable**: Individual claims should be cryptographically signed to assure non‐repudiatable statements of correlation. Long term, public and semi‐public ledgers should be used to record claims that become statistically impossible to falsify over time. Self‐sovereign identities, at a minimum depend on cryptographic assurances, and most likely will be further enabled by non‐repudiatable public ledgers.
|
||||
* **Reliable**: Access to self‐sovereign identities must be at least as reliable as access to the Internet. It should not rely on any individual or group of centralized servers, connections, or access technologies. Substantially Equivalent Above all, self‐sovereign identities must meet the needs of legacy identity observers at least as well as current solutions. If the core architecture is inherently less capable than existing approaches there is little hope of systemic adoption.
|
||||
|
||||
#### ZERO COST
|
||||
* **Finally, any proposed standard for self‐sovereign identity must be adoptable at absolutely minimal cost.**
|
||||
* Not only must it be free of licensing encumbrances, it must be implementable with readily available, inexpensive, commodity hardware running common operating systems. If it can’t be achieved using today’s commodity products, then we must help manufacturers incorporate what we need.
|
||||
|
||||
**In order to reach every last person on the planet**—the explicit target of UN Sustainable Development Goal 16.9—**self‐sovereign identity must be realizable at massive scale with close to zero marginal cost**.
|
||||
|
||||
The systems we use to make sense of the resulting identity transactions will provide more than enough consulting, software, and hardware revenue to finance the development of the core enabling technology. Just as the web browser was a zero cost entry into a vast economic and innovation engine of the world‐wide web, so too must self‐sovereign identity begin with the most cost‐effective on‐ramp that can be engineered.
|
||||
|
||||
---
|
||||
|
||||
### Principles of Self-Sovereign Identity
|
||||
|
||||
Now we'll review Christopher Allen's [Principles of Self Sovereign Identity](https://github.com/WebOfTrustInfo/self-sovereign-identity/blob/master/self-sovereign-identity-principles.md) one at a time to see how well the characteristics compare.
|
||||
|
||||
>1. **Existence.** *Users must have an independent existence.* Any self-sovereign identity is ultimately based on the ineffable “I” that’s at the heart of identity. It can never exist wholly in digital form. This must be the kernel of self that is upheld and supported. A self-sovereign identity simply makes public and accessible some limited aspects of the “I” that already exists.
|
||||
|
||||
I believe, the *Existance* principle is well represented by the first bulletpoint under the characteristic of *Control*, Self‐generatable and Independent.
|
||||
|
||||
>2. **Control.** *Users must control their identities.* Subject to well-understood and secure algorithms that ensure the continued validity of an identity and its claims, the user is the ultimate authority on their identity. They should always be able to refer to it, update it, or even hide it. They must be able to choose celebrity or privacy as they prefer. This doesn’t mean that a user controls all of the claims on their identity: other users may make claims about a user, but they should not be central to the identity itself.
|
||||
|
||||
The principle of Control must be well represented, since the characteristic of *Control* has the following 5 sub-points: **Self Generatable and Independent**, **Opt-In**, **Minimal Disclosure**, **Non-participation**, **Opt-out**, **Recoverable**.
|
||||
|
||||
>3. **Access.** *Users must have access to their own data.* A user must always be able to easily retrieve all the claims and other data within his identity. There must be no hidden data and no gatekeepers. This does not mean that a user can necessarily modify all the claims associated with his identity, but it does mean they should be aware of them. It also does not mean that users have equal access to others’ data, only to their own.
|
||||
>4. **Transparency**. *Systems and algorithms must be transparent.* The systems used to administer and operate a network of identities must be open, both in how they function and in how they are managed and updated. The algorithms should be free, open-source, well-known, and as independent as possible of any particular architecture; anyone should be able to examine how they work.
|
||||
|
||||
Access and Transparency are not explicitly represented in the Characteristics of SSI. The *Control* characteristic should be examined in relation.
|
||||
|
||||
>5. **Persistence.** *Identities must be long-lived.* Preferably, identities should last forever, or at least for as long as the user wishes. Though private keys might need to be rotated and data might need to be changed, the identity remains. In the fast-moving world of the Internet, this goal may not be entirely reasonable, so at the least identities should last until they’ve been outdated by newer identity systems. This must not contradict a “right to be forgotten”; a user should be able to dispose of an identity if he wishes and claims should be modified or removed as appropriate over time. To do this requires a firm separation between an identity and its claims: they can't be tied forever.
|
||||
>6. **Portability.** *Information and services about identity must be transportable.* Identities must not be held by a singular third-party entity, even if it's a trusted entity that is expected to work in the best interest of the user. The problem is that entities can disappear — and on the Internet, most eventually do. Regimes may change, users may move to different jurisdictions. Transportable identities ensure that the user remains in control of his identity no matter what, and can also improve an identity’s persistence over time.
|
||||
>7. **Interoperability.** *Identities should be as widely usable as possible.* Identities are of little value if they only work in limited niches. The goal of a 21st-century digital identity system is to make identity information widely available, crossing international boundaries to create global identities, without losing user control. Thanks to persistence and autonomy these widely available identities can then become continually available.
|
||||
|
||||
These principles could be more closely examined against the sub-points of the *Acceptance* characteristic.
|
||||
|
||||
>8. **Consent.** *Users must agree to the use of their identity.* Any identity system is built around sharing that identity and its claims, and an interoperable system increases the amount of sharing that occurs. However, sharing of data must only occur with the consent of the user. Though other users such as an employer, a credit bureau, or a friend might present claims, the user must still offer consent for them to become valid. Note that this consent might not be interactive, but it must still be deliberate and well-understood.
|
||||
>9. **Minimalization.** *Disclosure of claims must be minimized.* When data is disclosed, that disclosure should involve the minimum amount of data necessary to accomplish the task at hand. For example, if only a minimum age is called for, then the exact age should not be disclosed, and if only an age is requested, then the more precise date of birth should not be disclosed. This principle can be supported with selective disclosure, range proofs, and other zero-knowledge techniques, but non-correlatibility is still a very hard (perhaps impossible) task; the best we can do is to use minimalization to support privacy as best as possible.
|
||||
|
||||
I think these two principles are well represented by the *Control* characteristic.
|
||||
|
||||
>10. **Protection.** *The rights of users must be protected.* When there is a conflict between the needs of the identity network and the rights of individual users, then the network should err on the side of preserving the freedoms and rights of the individuals over the needs of the network. To ensure this, identity authentication must occur through independent algorithms that are censorship-resistant and force-resilient and that are run in a decentralized manner.
|
||||
|
||||
This is an important principle that I don't think is represented in the Characteristics.
|
||||
|
||||
|
||||
---
|
||||
|
||||
I think these ideas are worth examining further. Perhaps a continuing with a comparative exploration of other responses, similar frameworks, with a consideration for the United Nations SDGs.
|
||||
|
||||
* [The Laws of Identity](https://www.identityblog.com/stories/2005/05/13/TheLawsOfIdentity.pdf)
|
||||
* [The Windhover Principles for Digital Identity, Trust, and Data](https://www.tokencommons.org/Windhover-Principles-for-Digital-Identity-Trust-Data.html)
|
||||
* [Self-Sovereign Bill of Rights](https://github.com/WebOfTrustInfo/self-sovereign-identity/blob/master/self-sovereign-identity-bill-of-rights.md)
|
||||
* [Schutte's Take](https://github.com/WebOfTrustInfo/self-sovereign-identity/blob/master/Schutte-on-SSI.md) offers criticism on the 10 principles.
|
||||
|
||||
More on that : [Evolution of SSI]({{ site.baseurl }}/literature/self-sovereign-identity/evolution-of-ssi/)
|
||||
|
|
@ -1,87 +0,0 @@
|
|||
---
|
||||
date: 2018-12-22
|
||||
title: "The Evolution of Self Sovereign Identity (notes)"
|
||||
description: A start at examining leading thought around SSI since 2016, and presenting the idea of "modularizing" essential components of SSI documentation.
|
||||
excerpt: >
|
||||
There are a few different ways to approach and describe SSI. What I aim to do is come up with a list of different "SSI Cases" to modularize the treatment of the subject. This will allow each to contribute in the way that makes most sense for themselves, rather than trying to discuss SSI as a whole in a single whitepaper.
|
||||
layout: single
|
||||
toc: false
|
||||
redirect_from:
|
||||
- /literature/self-sovereign-identity/evolution-of-ssi
|
||||
- /self-sovereign-identity/evolution-of-ssi/
|
||||
- /self-sovereign-identity/evolution-of-ssi
|
||||
permalink: /literature/self-sovereign-identity/evolution-of-ssi/
|
||||
canonical_url: 'https://decentralized-id.com/literature/self-sovereign-identity/evolution-of-ssi/'
|
||||
categories: ["History","Web Standards"]
|
||||
tags: ["Self Sovereign Identity","notes","Literature","lifeID","RWoT"]
|
||||
last_modified_at: 2019-07-10
|
||||
published: true
|
||||
|
||||
---
|
||||
|
||||
|
||||
Christopher Allen's seminal work, [The Path to Self Sovereign Identity](https://github.com/WebOfTrustInfo/self-sovereign-identity/blob/master/ThePathToSelf-SovereignIdentity.md) continues to be an important and influential document for the Self Sovereign Identity community and movement. Rightly so, Allen does a superb job of outlining where digital identity has come from and where its going. However, Christopher intended for the [Principles of SSI](https://github.com/WebOfTrustInfo/self-sovereign-identity/blob/master/self-sovereign-identity-principles.md), gathered from the leading thought on digital identity, to be the start of a conversation.
|
||||
|
||||
In order to stimulate the discussion, I've been going through a [infominer33/self-sovereign-identity](https://github.com/infominer33/self-sovereign-identity) and organizing some thoughts on SSI since Christopher's 2016 post. There are a few different ways to approach and describe SSI. What I aim to do is come up with a list of different "SSI Cases" to modularize the treatment of the subject. This will allow each to contribute in the way that makes most sense for themselves, rather than trying to discuss SSI as a whole in a single whitepaper.
|
||||
|
||||
That October, [Joe Andrieu](https://github.com/jandrieu) submitted [A Technology‐Free Definition of Self‐Sovereign Identity](https://github.com/jandrieu/rebooting-the-web-of-trust-fall2016/raw/master/topics-and-advance-readings/a-technology-free-definition-of-self-sovereign-identity.pdf) to the third Rebooting the Web of Trust Design Workshop. Within it, he describes the Characteristics of SSI: **Control**, **Acceptance**, and **Zero Cost**.
|
||||
|
||||
>1 No disrespect to Christopher Allen’s opening to the conversation, The Path to Self Sovereign Identity [...] It gets a lot right, but leaves a few requirements out, e.g., recoverability and zero cost, and conflates “identities” and claims in an ambiguous manner.
|
||||
|
||||
I decided to put the **10 Principles of SSI** up next to Joe Andrieu's **Characteristics of SSI**
|
||||
|
||||
* [SSI Principles vs. Characteristics]({{ site.baseurl }}/literature/self-sovereign-identity/ssi-principles-vs-characteristics/)
|
||||
|
||||
Which should also be considered against:
|
||||
|
||||
* [Self-Sovereign Bill of Rights](https://github.com/WebOfTrustInfo/self-sovereign-identity/blob/master/self-sovereign-identity-bill-of-rights.md) - lifeID (founded by [Chris Boscolo](https://github.com/cboscolo)) adapted the 10 Principles of Self-Sovereign Identity into a [Bill of Rights](https://medium.com/@lifeID_io/lifeid-self-sovereign-identity-bill-of-rights-d2acafa1de8b) that all self-sovereign identity solution should uphold.
|
||||
|
||||
* [Schutte's Take](https://github.com/infominer33/self-sovereign-identity/blob/master/Schutte-on-SSI.md) which offers criticism on the 10 principles.
|
||||
|
||||
I think all of this thought should be consolidated into a cohesive declaration of ssi. The idea is to come up with list of phinciples, or characteristics, or rights, that is as complete as possible, while also as concise as possible. There are a few 10 pointed lists, I'm ok with combining them as necessary and if it turns into 19, for example, I'm ok w that. I'd rather err on the side of too much and pare it down gradually, than to not include enough.
|
||||
|
||||
* Next, there are the [7 Myths of SSI](https://github.com/decentralized-id/self-sovereign-identity/blob/master/7-myths-of-self-sovereign-identity.md) from Timothy Ruff's recent blog post. I've extracted them from his two part series into a concise document. There are surely other myths, and perhaps folk who have encountered them first hand will have some comment on the matter. And my condensed version of his myths could surely be improved upon.
|
||||
|
||||
* [A gentle introduction to self-sovereign-identity](https://bitsonblocks.net/2017/05/17/gentle-introduction-self-sovereign-identity/) by @antonylewis has a great section, How would self-sovereign identity work for the user?
|
||||
|
||||
* [How to Convince Dad* of the Importance of Self-Sovereign Identity](https://github.com/WebOfTrustInfo/rwot7/blob/master/final-documents/convincing-dad.md)
|
||||
* \*and your sister and your daughter and your best friend and your nephew (SSI Use-Cases)
|
||||
|
||||
* [Principles or Cult - An Irreverant Discussion on the Principles of SSI](https://www.thedinglegroup.com/blog/2021/9/1/principles-or-cult-an-irreverant-discussion-on-the-principles-of-ssi) 2021-09-01 Dingle Group
|
||||
> The evolution of the Principles of SSI came about through the need to differentiate what is ‘true’ SSI versus marketing forces twisting the concept. This market driven motivator can bring cultish overtones to the process.
|
||||
<!-- This could also be modularized -->
|
||||
|
||||
Other content highlighted in [WebOfTrustInfo/self-sovereign-identity](https://github.com/WebOfTrustInfo/self-sovereign-identity) that I haven't had a chance to fully review, yet:
|
||||
|
||||
* [Identity and Digital Self-Sovereignty](https://medium.com/learning-machine-blog/identity-and-digital-self-sovereignty-1f3faab7d9e3#.3jcgvnbok) - Blog post by [Natalie Smolenski](https://medium.com/@nsmolenski)
|
||||
|
||||
* [SSI: A Roadmap for Adoption](https://github.com/WebOfTrustInfo/rebooting-the-web-of-trust-spring2018/blob/master/final-documents/a-roadmap-for-ssi.md) from Rebooting the web of trust, Spring 2018.
|
||||
> This document proposes the formation of a short-term team to develop consistent messaging for the Self-Sovereign Identity (SSI) market.
|
||||
|
||||
|
||||
|
||||
### What I'm hoping for:
|
||||
|
||||
This is a modular breakdown of SSI documentation I would like to facilitate:
|
||||
(each, perhaps, around 800-1200 words)
|
||||
|
||||
1. History of Digital Identity. Along the lines of Christopher Allen
|
||||
|
||||
2. "How SSI works for the User" something along the line of how Antony Lewis
|
||||
- At its essence, this describes "ssi architecture" so to speak: 'wallet', 'identifier', 'credential' etc and how it interelates
|
||||
|
||||
3. "Principles of SSI" whatever you wanna call it, a complete, concise, and "exhaustive" list of foundational SSI principles or progress in that direction.
|
||||
|
||||
4. SSI Why Blockchain?
|
||||
|
||||
5. Myths of SSI
|
||||
|
||||
6. SSI Use Cases. (a'la "how to convince dad")
|
||||
- This uses the foundation "how SSI works for the USER" to go into more specific details of real life UX
|
||||
|
||||
I'm not limited to those 6, and I'm not glued to that order, but thats a general goal, and "how I would do it." We have the foundations of some core SSI content\documentation that I think will improve SSI education\onboarding. Just as in modularizing a codebase, modularizing SSI documentation will make it easier for any aspect to be improved as needed. I hope for these to become living community driven documents. Personally, I'm good at collecting, organizing, and digesting information, but am new to the SSI community, so I'm sure there's plenty I'm not considering.
|
||||
|
||||
I can see that I'll need to spend a lot more time with this content, am just learning my way around it right now.
|
||||
|
||||
I'm not the most qualified, I just have time and motivation. (Specifically, sometimes I write about Self-Sovereign Identity. But I want to write about it in an accurate way, which is difficult to do until some order is made of all this material.)
|
||||
|
||||
|
|
@ -6,13 +6,15 @@ description: A selection of DID related literature and top level resources for d
|
|||
excerpt: A selection of DID related literature and top level resources for discovery of more.
|
||||
header:
|
||||
image: /images/literature-christian-wiediger-unsplash.webp
|
||||
categories: ["Literature"]
|
||||
categories: ["Resources"]
|
||||
tags: ["Literature"]
|
||||
toc: true
|
||||
toc_sticky: false
|
||||
redirect_from: literature
|
||||
permalink: literature/
|
||||
canonical_url: 'https://decentralized-id.com/literature'
|
||||
redirect_from:
|
||||
- literature
|
||||
- literature/
|
||||
permalink: resources/literature/
|
||||
canonical_url: 'https://decentralized-id.com/resources/literature/'
|
||||
last_modified_at: 2023-06-19
|
||||
---
|
||||
|
||||
|
|
@ -2,10 +2,12 @@
|
|||
date: 2021-04-17
|
||||
title: SSI and Decentralized Identity Podcasts
|
||||
layout: single
|
||||
permalink: podcasts/
|
||||
redirect_from: media/
|
||||
canonical_url: 'https://decentralized-id.com/podcasts/'
|
||||
categories: ["Media"]
|
||||
permalink: resources/podcasts/
|
||||
redirect_from:
|
||||
- media/
|
||||
- podcasts/
|
||||
canonical_url: 'https://decentralized-id.com/resources/podcasts/'
|
||||
categories: ["Resources"]
|
||||
last_modified_at: 2021-04-17
|
||||
---
|
||||
|
||||
|
|
@ -1,6 +1,5 @@
|
|||
---
|
||||
date: 2019-04-11
|
||||
title: Blockchain Identity
|
||||
title: Blockchain and Self Sovereign Identity
|
||||
description: "Why Blockchain for Identity? + Assorted Blockchain ID Initiatives"
|
||||
excerpt: "Traditional identity systems typically suffer from single points of failure, lack of interoperability, and privacy issues such as encouraging mass data collection and user tracking. Blockchain technology has the potential to support novel data ownership and governance models with built-in control and consent mechanisms, which may benefit both users and businesses by alleviating these concerns; as a result, blockchain-based IDMSs are beginning to proliferate."
|
||||
header:
|
||||
|
|
@ -8,8 +7,10 @@ header:
|
|||
caption: "[NIST Cybersecurity (DRAFT) Blockchain Identity Management Approaches](https://arxiv.org/pdf/1908.00929.pdf)"
|
||||
teaser: /images/blockchain-Tumisu_3019121.webp
|
||||
layout: single
|
||||
permalink: /blockchain/
|
||||
categories: [Blockchain ID]
|
||||
permalink: /tech/blockchain/
|
||||
canonical_url: "https://decentralized-id.com/tech/blockchain/"
|
||||
redirect_from: /blockchain/
|
||||
categories: ["Technologies"]
|
||||
tags: ["NIST","Identiverse",Authenteq,Blockstack,Civic,Microsoft,Datum,ProCivis]
|
||||
last_modified_at: 2023-06-09
|
||||
toc: true
|
||||
|
|
@ -7,9 +7,12 @@ description: These hyperlinks connect all Linked Data into a single global data
|
|||
excerpt: >
|
||||
The idea behind these principles is on the one hand side, to use standards for the representation and the access to data on the Web. On the other hand, the principles propagate to set hyperlinks between data from different sources.
|
||||
tags: ["Linked Data","Solid","JSON-LD","RDF","W3C","Veres One","RSA"]
|
||||
categories: ["Web Standards"]
|
||||
permalink: /web-standards/linked-data/
|
||||
redirect_from: /specs-standards/linked-data/
|
||||
categories: ["Technologies"]
|
||||
permalink: /tech/linked-data/
|
||||
canonical_url: "https://decentralized-id.com/tech/linked-data/"
|
||||
redirect_from:
|
||||
- /specs-standards/linked-data/
|
||||
- /web-standards/linked-data/
|
||||
last_modified_at: 2023-06-02
|
||||
---
|
||||
|
||||
|
|
|
|||
|
|
@ -1,5 +1,4 @@
|
|||
---
|
||||
date: 2021-04-18
|
||||
name: Object Capabilities
|
||||
layout: standards
|
||||
headings: ["Main","Literature"]
|
||||
|
|
@ -7,9 +6,12 @@ title: "Object Capability Model"
|
|||
description: in which a capability describes a transferable right to perform one (or more) operations on a given object.
|
||||
excerpt: >
|
||||
Computer scientist E. Dean Tribble stated that in smart contracts, identity-based access control did not support well dynamically changing permissions, compared to the object-capability model. He analogized the ocap model with giving a valet the key to one's car, without handing over the right to car ownership.
|
||||
categories: ["Web Standards"]
|
||||
categories: ["Technologies"]
|
||||
tags: ["oCap","JSON-LD","zCap","Cosmos"]
|
||||
permalink: web-standards/object-capabilities/
|
||||
permalink: /tech/object-capabilities/
|
||||
canonical_url: "https://decentralized-id.com/tech/object-capabilities/"
|
||||
redirect_from:
|
||||
- /web-standards/object-capabilities/
|
||||
last_modified_at: 2023-05-22
|
||||
---
|
||||
|
||||
|
|
|
|||
65
_posts/technologies/2023-06-13-biometrics.md
Normal file
65
_posts/technologies/2023-06-13-biometrics.md
Normal file
|
|
@ -0,0 +1,65 @@
|
|||
---
|
||||
title: Biometrics and Self Sovereign Identity
|
||||
description: "How can biometrics help improve accessibility to critical services?"
|
||||
excerpt: >
|
||||
Instead of putting PII and biometrics in the same database, we need to put them in different places, but prove that there's a link between the holder of a biometric cred and the holder of other PII.
|
||||
layout: single
|
||||
permalink: /tech/biometrics/
|
||||
canonical_url: "https://decentralized-id.com/tech/biometrics/"
|
||||
categories: ["Technologies"]
|
||||
tags: ["Biometrics"]
|
||||
last_modified_at: 2023-06-09
|
||||
toc: true
|
||||
toc_sticky: true
|
||||
---
|
||||
|
||||
## Explainer
|
||||
|
||||
* [My Voice is my Password](https://stateofidentity.libsyn.com/my-voice-is-my-password) 2022-04-21 State of Identity
|
||||
> How can biometrics help improve accessibility to critical services? On this week’s State of Identity podcast, host Cameron D’Ambrosi is joined by Chief Fraud Prevention Officer for security and biometrics at Nuance, Simon Marchand. Tune in for their discussion about the cutting edge of biometric voice recognition technology, and its potential to transform identity verification and the user experience across channels.
|
||||
* [Survey Finds Customers Frustrated With Passwords, Open to Biometrics](https://findbiometrics.com/survey-finds-customers-frustrated-passwords-open-biometrics-7102106/) 2021-10-14 FindBiometrics
|
||||
> Passwords were a major point of contention in that regard, with a strong majority (68 percent) of consumers indicating that it is difficult to remember and key in a large number of passwords. Nearly half (44 percent) believe that biometric authenticators are easier to use, while 34 percent would prefer to use them as their primary means of identity
|
||||
* [Exploring Facial Biometrics](https://diacc.ca/2020/12/16/exploring-facial-biometrics-what-is-it/) 2020-12-16 DIACC
|
||||
> Policymakers, privacy advocates, and regulators understand that new technologies are being added to existing facial biometric matching to render leaked personal data useless and ensure that any leaked biometric data is both isolated and encrypted to reduce the impacts on individuals from an identity fraud perspective.
|
||||
|
||||
## Guidance
|
||||
* [Guidance on the Acceptable Use of Biometrics – DIACC Special Interest Group Insights](https://diacc.ca/2022/01/13/guidance-on-the-acceptable-use-of-biometrics/) 2022-01-13 DIACC
|
||||
> With input from public and private sector DIACC members and liaisons, the following guidance was created as a recommendation that the DIACC’s Trust Framework Expert Committee (TFEC) agreed to consider. Specified business, legal, and technical process requirements will be identified and considered by the TFEC for inclusion in future versions of the PCTF.
|
||||
|
||||
## Policy
|
||||
* [China’s Supreme Court Bars Use of Facial Recognition Without Consent](https://findbiometrics.com/chinese-supreme-court-bars-use-facial-recognition-without-consent-073007/) 2021-07-30 FindBiometrics
|
||||
China’s highest court has issued a ruling that could significantly limit the scope of facial recognition programs in the country. To that end, the Supreme People’s Court has stated that […] The post China’s Supreme Court Bars Use of Facial Recognition Without Consent appeared first on FindBiometrics
|
||||
* [Biden Reverses Trump Order to Expand DHS’s Biometrics Collection](https://findbiometrics.com/biden-reverses-trump-order-expand-dhss-biometrics-collection-070802/) 2021-07-08 FindBiometrics
|
||||
> In a move that is likely to please privacy advocates across the country, the Biden Administration has announced that it has officially rescinded a policy proposed by the Trump Administration that [would have considerably expanded](https://findbiometrics.com/proposed-policy-would-give-dhs-sweeping-powers-collect-biometric-data-092106/) the Department of Homeland Security’s (DHS) powers to collect biometric data from immigrants.
|
||||
|
||||
## Standards
|
||||
* [Veridium Advocates for Use of NIST-approved Contactless Fingerprint Technologies](https://findbiometrics.com/veridium-advocates-use-nist-approved-contactless-fingerprint-technologies-090305/) 2021-08-02 FindBiometrics
|
||||
Veridium is encouraging more organizations to embrace contactless fingerprint technologies, especially now that the NIST has laid out comprehensive guidelines for those interested in doing so. Those guidelines debuted in March of this year, with the release of NIST Special Publication 500-334.
|
||||
|
||||
## Development
|
||||
|
||||
* [Biometric and digital identity](https://iiw.idcommons.net/3H/_Biometric_and_digital_identity) by Robert Mitwicki / Adrian Gropper
|
||||
* [Biometric Health Card](https://docs.google.com/document/d/1o_773vzcbtSf59oU-iRUfAy5WSz3Wn9JUAvi0hKHE48/edit)
|
||||
> The novel concept is to add a quantized face that is still human-verifiable to the digital credential presentation. The hash of the quantized face, but not the face itself, would be signed and verifiable as part of the digital credential represented by the QR code.
|
||||
> 
|
||||
|
||||
## Caution
|
||||
* [Face Recognition Isn’t Just Face Identification and Verification: It’s Also Photo Clustering, Race Analysis, Real-time Tracking, and More](https://www.eff.org/deeplinks/2021/10/face-recognition-isnt-just-face-identification-and-verification) 2021-10 EFF
|
||||
> All forms of face recognition are a menace to privacy, free speech, and racial justice. This post explores many of the various kinds of face recognition, and explains why all must be addressed by laws.
|
||||
* [the link between biometrics and PII needs careful management](https://lists.w3.org/Archives/Public/public-credentials/2021Sep/0000.html) 2021-09-01 Daniel Hardman
|
||||
My takeaway: Instead of putting PII and biometrics in the same database, we need to put them in different places, but prove that there's a link between the holder of a biometric cred and the holder of other PII. I see companies like iRespond doing this, but I also seem some biometric applications that are more troubling.
|
||||
* [This is the real story of the Afghan biometric databases abandoned to the Taliban | MIT Technology Review](https://www.technologyreview.com/2021/08/30/1033941/afghanistan-biometric-databases-us-military-40-data-points/) 2021-08-30
|
||||
* [Afghans scramble to delete digital history, evade biometrics](https://www.context.news/surveillance/afghans-scramble-to-delete-digital-history-evade-biometrics) 2021-08-17 Context News
|
||||
> Thousands of Afghans struggling to ensure the physical safety of their families after the Taliban took control of the country have an additional worry: that biometric databases and their own digital history can be used to track and target them.
|
||||
* [Sexism in Facial Recognition Technology](https://medium.com/berkman-klein-center/sexism-in-facial-recognition-technology-d5e547a6e7bc) 2021-05-05 Berkman Klien Center
|
||||
> The use of facial recognition by law enforcement agencies has become common practice, despite increasing reports of [false arrests](https://www.nytimes.com/2020/06/24/technology/facial-recognition-arrest.html) and [jail time](https://www.nytimes.com/2020/12/29/technology/facial-recognition-misidentify-jail.html). While there are various downsides to facial recognition technology being used at all, including fears of mass surveillance and invasion of privacy, there are flaws within facial recognition technologies themselves that lead to inaccurate results. One such major challenge for this still-burgeoning technology is gender-based inaccuracies.
|
||||
|
||||
## Company
|
||||
* [Imageware to add Biometrics to Blockchain Powered Self Sovereign Identity (SSI)](https://imageware.io/imageware-to-add-biometrics-to-blockchainpowered-self-sovereign-identity-ssi/) 2021-10-24
|
||||
“As individual safety and privacy concerns become more prevalent in our daily lives, it’s vital that we have better, more decentralized methods of giving individuals autonomy over their identities. By joining the Decentralized Identity Foundation and Trust Over IP groups, we’ll be able to leverage their network and resources in our efforts to further develop a portfolio of SSI integrated biometric solutions.”
|
||||
|
||||
## Product
|
||||
* [Biometrics come to verifiable credentials with Applied Recognition and Sovrin Foundation](https://www.biometricupdate.com/202105/biometrics-come-to-verifiable-credentials-with-applied-recognition-and-sovrin-foundation) 2021-05 Biometric Update
|
||||
> Making wallet available, with support from companies like Applied Rec supplying biometrics that people can use for free, therefore extends Sovrin’s mission of supporting SSI. The companies generous enough to donate their technology to the wallet get commercial upside from next steps of service for banks and other organizations leveraging the open-source wallet, Raczkowski says.
|
||||
|
||||
|
||||
64
_posts/technologies/2023-06-14-pico-iot.md
Normal file
64
_posts/technologies/2023-06-14-pico-iot.md
Normal file
|
|
@ -0,0 +1,64 @@
|
|||
---
|
||||
title: "PICOs: Persistent Compute Objects"
|
||||
description: "Computational node for anything: person, place, organization, smart thing, dumb thing, concept, even a pothole."
|
||||
excerpt: >
|
||||
every pico is serverless and cloud-native, presenting an API that can be fully customized by developers. Because they're persistent, picos support databaseless programming with intuitive data isolation. As an actor-model programming system, different picos can operate concurrently without the need for locks, making them a natural choice for easily building decentralized systems.
|
||||
layout: single
|
||||
permalink: /tech/biometrics/
|
||||
canonical_url: "https://decentralized-id.com/tech/biometrics/"
|
||||
categories: ["Technologies"]
|
||||
tags: ["PICO","IOT"]
|
||||
last_modified_at: 2023-06-09
|
||||
toc: true
|
||||
toc_sticky: true
|
||||
---
|
||||
|
||||
## Explainer
|
||||
|
||||
* [The Most Inventive Thing I've Done](https://www.windley.com/archives/2022/07/the_most_inventive_thing_ive_done.shtml) 2022-07 Phil Windley
|
||||
> every pico is serverless and cloud-native, presenting an API that can be fully customized by developers. Because they're persistent, picos support databaseless programming with intuitive data isolation. As an actor-model programming system, different picos can operate concurrently without the need for locks, making them a natural choice for easily building decentralized systems.
|
||||
* [Introduction to Picos](https://iiw.idcommons.net/4C/_Introduction_to_Picos) 2021-05-06 Phil Windley
|
||||
> IoT, digital twins, device shadows, Conflict-free replicated data type (CRDT), CSP over DIDcomm
|
||||
> * [https://picolabs.io](https://picolabs.io) Pico Labs
|
||||
> * [https://github.com/Picolab/](https://github.com/Picolab/) repos
|
||||
> * [https://picolabs.atlassian.net/wiki](https://picolabs.atlassian.net/wiki) documentation
|
||||
> * [http://stackoverflow.com/questions/tagged/krl](http://stackoverflow.com/questions/tagged/krl) programming Q&A
|
||||
* [Persistence, Programming, and Picos](https://www.windley.com/archives/2021/02/persistence_programming_and_picos.shtml) Phil Windley 2021-02
|
||||
> Picos show that image-based development can be done in a manner consistent with the best practices we use today without losing the important benefits it brings.
|
||||
>
|
||||
> The project name, PICOS, is an abbreviation of “Privacy and Identity Management for Community Services”. The objective of the project is to advance the state of the art in technologies that provide privacy-enhanced identity and trust management features within complex community-supporting services that are built on Next Generation Networks and delivered by multiple communication service providers. The approach taken by the project is to research, develop, build trial and evaluate an open, privacy-respecting, trust-enabling identity management platform that supports the provision of community services by mobile communication service providers.
|
||||
>
|
||||
> Learn more about the [motivation](http://www.picos-project.eu/Motivation.181.0.html), the [objectives](http://www.picos-project.eu/Objectives.182.0.html), [tasks](http://www.picos-project.eu/Tasks.183.0.html) and [achievements](http://www.picos-project.eu/Achievements.190.0.html) of PICOS, and get to know the PICOS exemplary [communities](http://www.picos-project.eu/Communities.184.0.html).
|
||||
|
||||
## Application
|
||||
* [Picos at the Edge](https://www.windley.com/archives/2021/11/picos_at_the_edge.shtml) 2021-11 Phil Windley
|
||||
> You can play with this first hand at [NoFilter.org](https://nofilter.org/), which brands itself as a "the world's first unstoppable, uncensorable, undeplatformable, decentralized freedom of speech app." There's no server storing files, just a set of Javascript files that run in your browser. Identity is provided via [Metamask](https://metamask.io/) which uses an Ethereum address as your identifier. [I created some posts on NoFilter](https://nofilter.org/#/0xdbca72ed00c24d50661641bf42ad4be003a30b84) to explore how it works.
|
||||
* [Ten Reasons to Use Picos for Your Next Decentralized Programming Project](https://www.windley.com/archives/2021/07/ten_reasons_to_use_picos_for_your_next_decentralized_programming_project.shtml) 2021-07
|
||||
> Summary: Picos are a programming model for building decentralized applications that provide significant benefits in the form of abstractions that reduce programmer effort. Here are ten eleven reasons you should use picos for your next decentralized application. Temperature Sensor Network Built from Picos I didn't start out to write a programming language that naturally supports
|
||||
* [Credential-based login to a Pico-based application](https://iiw.idcommons.net/11P/_Credential-based_login_to_a_Pico-based_application) 2021-05-06 Bruce Conrad [slides](https://bruceatbyu.com/s/HRDDSiiw32)
|
||||
> The application that I wanted to demonstrate is what I call a fully-sharded database. BYU wants a community facing Human Resources domain data store, which means that other organizations on campus may wish to access HR data and so far they’ve been doing it by dipping directly into the production transactional database and that's not a good idea. And so, they have a team implementing a proof of concept using Postgres. And, I’m using picos to implement a fully-sharded alternative proof of concept.
|
||||
* [Building Decentralized Applications with Pico Networks](https://www.windley.com/archives/2021/02/building_decentralized_applications_with_pico_networks.shtml) 2021-02 Phil Windley
|
||||
> Building a system of picos for a specific application requires programming them to perform the proper lifecycle management tasks to create the picos that model the application. Wrangler is a ruleset installed in every pico automatically that is the pico operating system. Wrangler provides rules and functions for performing these life-cycle management tasks.
|
||||
|
||||
## Development
|
||||
* [Announcing Pico Engine 1.0](https://www.windley.com/archives/2021/02/announcing_pico_engine_10.shtml) 2021-02 Phil Windley
|
||||
> Pico is short for “Persistent Compute Objects.”
|
||||
> Why Picos
|
||||
> - Persistent, personal, computational nodes → More individual autonomy
|
||||
> - Computational node for anything: person, place, organization, smart thing, dumb thing, concept, even a pothole
|
||||
> - Better, more scalable model for IoT → trillion node networks
|
||||
> - Picos support social things and trustworthy spaces
|
||||
> - Better sharing, more natural relationship-based interactions (borrow my truck, Fuse with two owners)
|
||||
> - Scales
|
||||
> - Substitutable hosting model → freedom of choice
|
||||
> - pico mesh
|
||||
> [...]
|
||||
> What are Picos?
|
||||
> - “Pico” is a neologism for persistent compute objects.
|
||||
> - Persistence is a core feature of how picos work.
|
||||
> - Picos exhibit persistence in three ways:
|
||||
> - Persistent identity—Picos exist, with a single identity, continuously from the moment of their creation until they are destroyed.
|
||||
> - Persistent state—Picos have state that programs running in the pico can see and alter.
|
||||
> - Persistent availability—Picos are always on and ready to process queries and events.
|
||||
* [ACA-Pico working group](https://docs.google.com/document/d/12dWUFyL7u6OQkhnPObJOOlV-U2LDoHpF-ZQLj3hXbjA/edit)
|
||||
* [Picolab/aries-cloudagent-pico](https://github.com/Picolab/aries-cloudagent-pico)
|
||||
|
|
@ -16,6 +16,9 @@ last_modified_at: 2023-06-22
|
|||
---
|
||||
|
||||
## About Self Sovereign Identity
|
||||
* [The Off Chain Internet: Decentralized Identity & Verifiable Credentials - Evin McMullen](https://www.youtube.com/watch?v=EZ_Bb6j87mg) 2022-02-19 ETH Denver
|
||||
*FANTASTIC NEW TALK!!!!*
|
||||
> i'm excited to share with you a little bit more about the web 3 beyond the chain. Public ledgers are where we hang out most of the time, but the best of web 3 is yet to be because it hasn't yet been built and embraced fully by all of us.
|
||||
* [Video] [Exploring the Decentralized Web, Episode 4: Digital Identity](https://www.youtube.com/watch?v=jm8y56KMkIw) 2022-01-05 Filecoin Foundation
|
||||
> Episode 4 explores the relationship between authentication and authorization, the rise of single sign-on platforms, and the advantages of and use cases for self-sovereign identity. Guests include Brian Behlendorf, Rainey Reitman, Danny O'Brien, Sarah Friend, Wendy Hanamura, Andrew Hill, and Brad Kam.
|
||||
* [#SSI gives its owner control over some aspects of identity, but not all](https://twitter.com/GETJolocom/status/1470791578780413953) 2021-12-14 Jolocom
|
||||
|
|
@ -26,8 +29,6 @@ last_modified_at: 2023-06-22
|
|||
> Solving the identity paradox: the tradeoff between privacy, security, & user experience
|
||||
* [Self-Sovereign Identity Crisis](https://lionsgate.io/self-sovereign-identity-crisis/) 2021-11-23 Lionsgate
|
||||
> Through deceptive marketing practices the first-movers in the Digital ID market have done-away with the sovereignty. As a result a burgeoning new industry is experiencing a Self-Sovereign Identity Crisis.
|
||||
* [Evolution of Self-Sovereign Identity (SSI)](https://lionsgate.io/evolution-of-self-sovereign-identity-ssi/) 2021-11-16 LionsGate
|
||||
> The public keys of the user and the third-party organization for verifying the digital signature are recorded in a distributed ledger, and the user of the identity information verifies the provided information using them. In this way, users can control their own identity information without relying on a specific central administrator.
|
||||
* [Video] [Understanding the SSI Identity Model with Verifiable Credentials](https://www.youtube.com/watch?v=TRuz39SEX7E) 2021-11-13 Manning
|
||||
> Drummond Reed, an expert in Internet identity, security, privacy, and trust frameworks, explains the basic building blocks of SSI and how this new identity model fundamentally works.
|
||||
* [What is Self Sovereign Identity](https://medium.com/coinmonks/what-is-self-sovereign-identity-a8087b2bf0ea) 2021-10-13 Florian Strauf
|
||||
|
|
@ -60,8 +61,6 @@ last_modified_at: 2023-06-22
|
|||
> Verifiable credentials, DIDs, and blockchain are evidence of what's to come: Web3, a more secure, widespread, machine-to-machine internet.
|
||||
* [Introduction to Decentralized Identity](https://wiki.iota.org/identity.rs/decentralized_identity) IOTA Wiki
|
||||
> Decentralized Identity or Self-Sovereign Identity (SSI) defines a new method for identity management and authentication. It removes the centralized aspects and puts the Identity subject in full control over its own identity. Decentralized Identity provides a solution for the increasing amount of database breaches, the lack of trust in any digital setting, and the increasingly difficult to comply with privacy legislation, such as GDPR.
|
||||
* [The Three Pillars of Self-Sovereign Identity](https://www.evernym.com/blog/the-three-pillars-of-self-sovereign-identity/) 2019-12-10 Evernym
|
||||
> When implemented for the purpose of identity, everyone everywhere can issue, hold, and verify any credentials about anything. This means no more proprietary silos “owning” your identity. The combination of human and cryptographic trust in this environment means that you can finally get increased security and reduced friction at the same time.
|
||||
* [Self-Sovereign Identity — wiki.p2pfoundation](https://wiki.p2pfoundation.net/Self-Sovereign_Identity) 2019-11-13 P2P Foundation
|
||||
> The beauty of sovereignty isn't complete and total control, but rather balance of power that leads to negotiations about the nature of the relationships between various entities in the system."
|
||||
|
||||
|
|
@ -109,14 +108,8 @@ last_modified_at: 2023-06-22
|
|||
> 
|
||||
* [The Implications of Bring Your Own Identity](https://www.idsalliance.org/blog/2020/12/03/the-implications-of-bring-your-own-identity/) Identity Defined Security Alliance 2020-12-03
|
||||
> My short stint as “Mark Jannell" taught me a lot of about trust and ease of use in a bring your own identity model. Trust, as always in security, is essential to this new class of relationships and must be established and then protected from abuse. Ease of use, it turns out, is a key factor in protecting that trust and promoting the adoption of good identity patterns. I’m sure that I could have learned these lessons in some other way, but I’ll never forget my half year answering to a pseudonym.
|
||||
* [The Mental Models of Identity Enabled by SSI](https://ssi-ambassador.medium.com/the-mental-models-of-identity-enabled-by-ssi-d3e2d8d0f2b6) 2020-12-03 Adrian Doerk
|
||||
The Models: Space Time • Presentation • Attribute • Relationship • Capability
|
||||
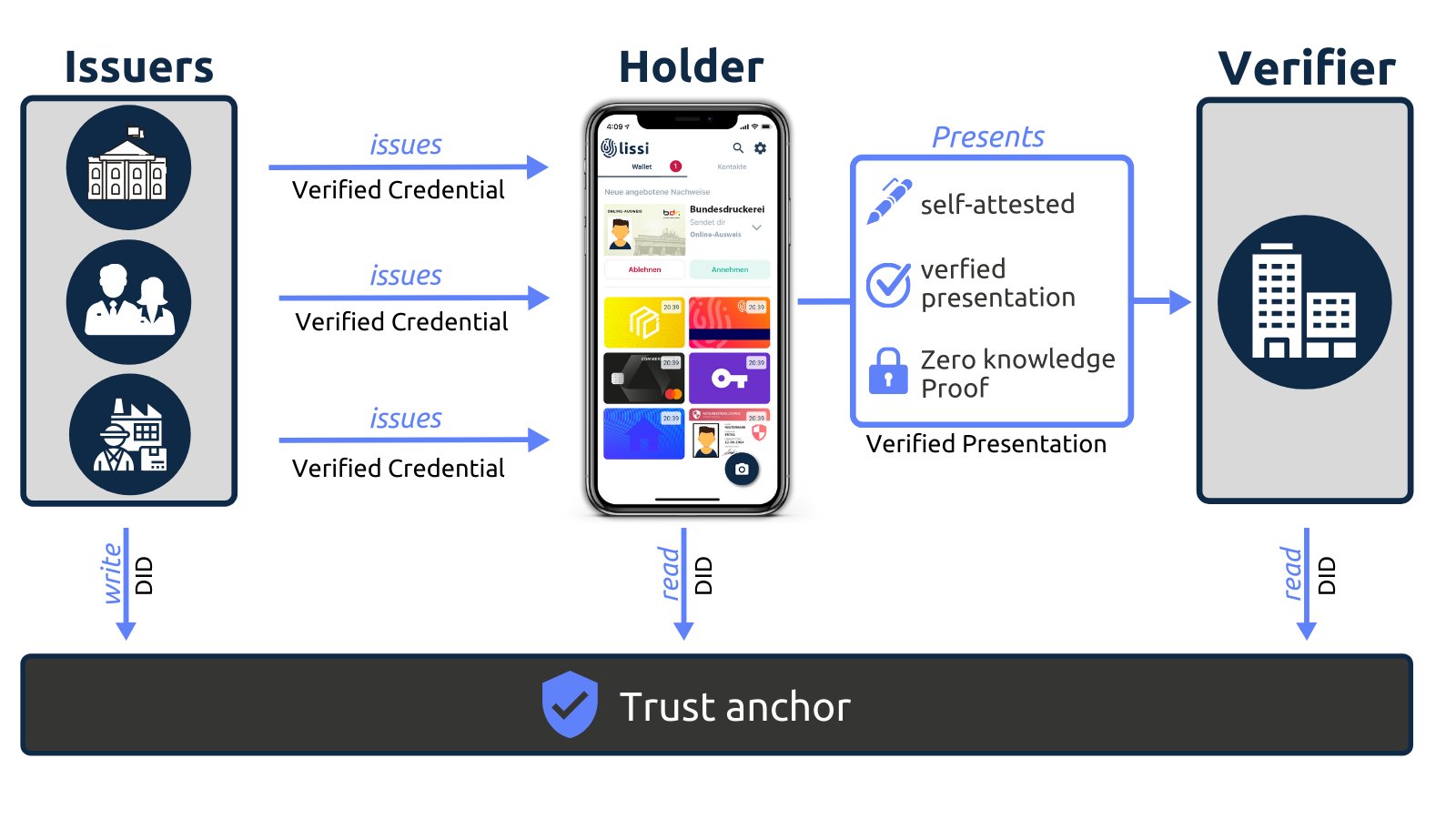
* [What is the Trust Triangle?](https://academy.affinidi.com/what-is-the-trust-triangle-9a9caf36b321) 2021-08-23 Affinidi
|
||||
> The relationship between the issuers, holders, and verifiers is called the trust triangle simply because you need an element of trust among these entities for them to work together.
|
||||
* [The 5P’s of a Self-Sovereign Identity](https://markvanrijmenam.medium.com/the-5ps-of-a-self-sovereign-identity-e6f6eb802d75) 2019-06-05 Dr Mark van Rijmenam
|
||||
> A self-sovereign identity can be defined by the 5P’s as it is personal (it is about you), portable (meaning you can take your identity and data from one platform to another), private (you control your identity and data), persistent (it does not change without your consent) and protected (they cannot steal your identity).
|
||||
* [LESS identity](https://medium.com/@trbouma/less-identity-65f65d87f56b) 2018-12-09 Tim Bouma
|
||||
> I arrived at the term ‘Less Identity’ through some fun wordplay (yes, I do this stuff in my spare time). I was thinking about ‘Trust Frameworks’ and ‘Trustless Networks.’ When I factored out the common ‘Trust’, I arrived at ‘Trust[Less Networks and Frameworks].’
|
||||
* [A Primer on Functional Identity](https://github.com/WebOfTrustInfo/rebooting-the-web-of-trust-fall2017/blob/master/topics-and-advance-readings/functional-identity-primer.md) 2017-08-26 Joe Andrieu rwot05-boston
|
||||
> Unfortunately, digital systems can unwittingly compromise real-world identity. Sometimes this occurs because digital identity systems neglect to consider external effects. Other times, it happens with systems that didn’t even realize they were dealing with identity-related personal information. A functional perspective allows engineers to see beyond static attributes and traditional notions of “Personally Identifiable Information” to better understand how engineering choices can impact identity, even outside their systems.
|
||||
|
||||
|
|
@ -147,16 +140,6 @@ The Models: Space Time • Presentation • Attribute • Relationship • Capab
|
|||
* [Digital identities – steps on the path to an ID ecosystem](https://bankenverband.de/en/digitisation/digital-identities-steps-path-id-ecosystem/) 2021-03-18 Bankenverband
|
||||
*This article is very very good in articulating the big picture of how SSI systems relative to older system and emerging fragmetned systems.*
|
||||
> An answer to these challenges is an ecosystem in which digital identity data can be exchanged in a way that is secure, reliable, scalable and convenient. This will have a positive impact on the economic future of Germany and Europe while at the same time enhancing the private sphere of the individual.
|
||||
* [The Basic Building Blocks of SSI](https://freecontent.manning.com/the-basic-building-blocks-of-ssi/) 2020-07-29 Drummond Reed, Alex Preukschat Manning
|
||||
> In many cases these core concepts have been established for decades. What’s new is how they’re put together to create a new model for digital identity management. The purpose of this article is to quickly familiarize you with these seven basic building blocks from a conceptual and technical point-of-view.
|
||||
> - Verifiable credentials (aka digital credentials)
|
||||
> - Issuers, holders, and verifiers
|
||||
> - Digital wallets
|
||||
> - Digital agents and hubs
|
||||
> - Decentralized identifiers (DIDs)
|
||||
> - Blockchains
|
||||
> - Governance frameworks (aka trust frameworks)
|
||||
|
||||
|
||||
[](https://www.researchgate.net/figure/Self-Sovereign-Identity-Locus-of-Control-Bouma-2019_fig1_340938808)
|
||||
|
||||
|
|
|
|||
107
_posts/topics/2018-12-22-characteristics-principles.md
Normal file
107
_posts/topics/2018-12-22-characteristics-principles.md
Normal file
|
|
@ -0,0 +1,107 @@
|
|||
---
|
||||
title: "Principles and Characteristics of Self Sovereign Identity"
|
||||
description: This page is devoted to leading thought around what are the most important characteristics of Self Sovereign Identity.
|
||||
excerpt: >
|
||||
There are a few different ways to approach and describe SSI. What I aim to do is come up with a list of different "SSI Cases" to modularize the treatment of the subject. This will allow each to contribute in the way that makes most sense for themselves, rather than trying to discuss SSI as a whole in a single whitepaper.
|
||||
layout: single
|
||||
toc: false
|
||||
redirect_from:
|
||||
- /self-sovereign-identity/ssi-principles-vs-characteristics
|
||||
- /self-sovereign-identity/ssi-principles-vs-characteristics/
|
||||
- /literature/self-sovereign-identity/evolution-of-ssi
|
||||
- /self-sovereign-identity/evolution-of-ssi/
|
||||
- /self-sovereign-identity/evolution-of-ssi
|
||||
- /literature/self-sovereign-identity/ssi-principles-vs-characteristics/
|
||||
- /literature/self-sovereign-identity/evolution-of-ssi/
|
||||
permalink: /topic/characteristics/
|
||||
canonical_url: 'https://decentralized-id.com/topic/characteristics/'
|
||||
categories: ["Topics"]
|
||||
tags: ["Self Sovereign Identity","notes","Literature","lifeID","RWoT","Laws of Identity","Literature","UNSDGs","Windhover Principles","History"]
|
||||
last_modified_at: 2023-06-24
|
||||
---
|
||||
|
||||
## The Path to Self Sovereign Identity
|
||||
Christopher Allen's seminal work, [The Path to Self Sovereign Identity](http://www.lifewithalacrity.com/2016/04/the-path-to-self-soverereign-identity.html), helped to concretize and proliferate the ideals behind, and movement towards, Self Sovereign Identity.
|
||||
|
||||
His article details the history of digital identity standards, and the user experience accompanying those standards. After describing from where we've come, Allen draws from leading thought on digital identity to compose the [Principles of Self Sovereign Identity](https://github.com/WebOfTrustInfo/self-sovereign-identity/blob/master/self-sovereign-identity-principles.md).
|
||||
|
||||
### Principles of Self Sovereign Identity
|
||||
|
||||
1. **Existence.** *Users must have an independent existence.* Any self-sovereign identity is ultimately based on the ineffable “I” that’s at the heart of identity. It can never exist wholly in digital form. This must be the kernel of self that is upheld and supported. A self-sovereign identity simply makes public and accessible some limited aspects of the “I” that already exists.
|
||||
2. **Control.** *Users must control their identities.* Subject to well-understood and secure algorithms that ensure the continued validity of an identity and its claims, the user is the ultimate authority on their identity. They should always be able to refer to it, update it, or even hide it. They must be able to choose celebrity or privacy as they prefer. This doesn’t mean that a user controls all of the claims on their identity: other users may make claims about a user, but they should not be central to the identity itself.
|
||||
3. **Access.** *Users must have access to their own data.* A user must always be able to easily retrieve all the claims and other data within his identity. There must be no hidden data and no gatekeepers. This does not mean that a user can necessarily modify all the claims associated with his identity, but it does mean they should be aware of them. It also does not mean that users have equal access to others’ data, only to their own.
|
||||
4. **Transparency**. *Systems and algorithms must be transparent.* The systems used to administer and operate a network of identities must be open, both in how they function and in how they are managed and updated. The algorithms should be free, open-source, well-known, and as independent as possible of any particular architecture; anyone should be able to examine how they work.
|
||||
5. **Persistence.** *Identities must be long-lived.* Preferably, identities should last forever, or at least for as long as the user wishes. Though private keys might need to be rotated and data might need to be changed, the identity remains. In the fast-moving world of the Internet, this goal may not be entirely reasonable, so at the least identities should last until they’ve been outdated by newer identity systems. This must not contradict a “right to be forgotten”; a user should be able to dispose of an identity if he wishes and claims should be modified or removed as appropriate over time. To do this requires a firm separation between an identity and its claims: they can't be tied forever.
|
||||
6. **Portability.** *Information and services about identity must be transportable.* Identities must not be held by a singular third-party entity, even if it's a trusted entity that is expected to work in the best interest of the user. The problem is that entities can disappear — and on the Internet, most eventually do. Regimes may change, users may move to different jurisdictions. Transportable identities ensure that the user remains in control of his identity no matter what, and can also improve an identity’s persistence over time.
|
||||
7. **Interoperability.** *Identities should be as widely usable as possible.* Identities are of little value if they only work in limited niches. The goal of a 21st-century digital identity system is to make identity information widely available, crossing international boundaries to create global identities, without losing user control. Thanks to persistence and autonomy these widely available identities can then become continually available.
|
||||
8. **Consent.** *Users must agree to the use of their identity.* Any identity system is built around sharing that identity and its claims, and an interoperable system increases the amount of sharing that occurs. However, sharing of data must only occur with the consent of the user. Though other users such as an employer, a credit bureau, or a friend might present claims, the user must still offer consent for them to become valid. Note that this consent might not be interactive, but it must still be deliberate and well-understood.
|
||||
9. **Minimalization.** *Disclosure of claims must be minimized.* When data is disclosed, that disclosure should involve the minimum amount of data necessary to accomplish the task at hand. For example, if only a minimum age is called for, then the exact age should not be disclosed, and if only an age is requested, then the more precise date of birth should not be disclosed. This principle can be supported with selective disclosure, range proofs, and other zero-knowledge techniques, but non-correlatibility is still a very hard (perhaps impossible) task; the best we can do is to use minimalization to support privacy as best as possible.
|
||||
10. **Protection.** *The rights of users must be protected.* When there is a conflict between the needs of the identity network and the rights of individual users, then the network should err on the side of preserving the freedoms and rights of the individuals over the needs of the network. To ensure this, identity authentication must occur through independent algorithms that are censorship-resistant and force-resilient and that are run in a decentralized manner.
|
||||
|
||||
### Related
|
||||
|
||||
* [Principles or Cult - An Irreverant Discussion on the Principles of SSI](https://www.thedinglegroup.com/blog/2021/9/1/principles-or-cult-an-irreverant-discussion-on-the-principles-of-ssi) 2021-09-01 Dingle Group
|
||||
> The evolution of the Principles of SSI came about through the need to differentiate what is ‘true’ SSI versus marketing forces twisting the concept. This market driven motivator can bring cultish overtones to the process.
|
||||
* [Self-Sovereign Bill of Rights](https://github.com/WebOfTrustInfo/self-sovereign-identity/blob/master/self-sovereign-identity-bill-of-rights.md) 2019-07-05 lifeID [Article](https://medium.com/@lifeID_io/lifeid-self-sovereign-identity-bill-of-rights-d2acafa1de8b)
|
||||
> There is a definitional gap to be filled, establishing what we think are the foundational attributes of a truly self-sovereign identity. It is our goal to inspire discussion and agreement within our community for what comprises a self-sovereign identity to ensure the success, integrity and sustainability of these solutions for people throughout the world.
|
||||
>
|
||||
> In light of this, we hold these truths to be self-evident features of any self-sovereign identity solution.
|
||||
* [Schutte’s Critique of the Self-Sovereign Identity Principles](https://github.com/WebOfTrustInfo/self-sovereign-identity/blob/master/Schutte-on-SSI.md) 2016-10-26 Rebooting Web of Trust
|
||||
> I’m taking a quick pass through Christopher Allen’s 10 principles for Self-Sovereign Identity, with an eye toward highlighting the primary shortcomings that I perceive. Note: I have a very unusual take on this. I understand that. I’m trying to be guided primarily by how mechanisms of coherence formation, perception and interaction amongst agents operate in complex adaptive systems.
|
||||
|
||||
## Opening Up the Conversation
|
||||
|
||||
> The idea of digital identity has been evolving for a few decades now, from centralized identities to federated identities to user-centric identities to self-sovereign identities. However, even today exactly what a self-sovereign identity is, and what rules it should recognize, aren’t well-known.
|
||||
>
|
||||
> This article seeks to begin a dialogue on that topic, by offering up a definition and a set of principles as a starting point for this new form of user-controlled and persistent identity of the 21st century. - [The Path to Self Sovereign Identity](https://github.com/WebOfTrustInfo/self-sovereign-identity/blob/master/ThePathToSelf-SovereignIdentity.md) 2016-04 Rebooting Web of Trust
|
||||
|
||||
It was intended for that article to help open the conversation, not necessarily define the movement. All the same, the [Principles of Self Sovereign Identity](https://github.com/WebOfTrustInfo/self-sovereign-identity/blob/master/self-sovereign-identity-principles.md) have remained a guiding beacon for the development of Self Sovereign Identity systems.
|
||||
|
||||
That, said, the principles don't represent the entirety of thought on necessary characteristics for Sovereign identity systems. This page is devoted to continued thought around what are the most important characteristics of Self Sovereign Identity.
|
||||
|
||||
## A Technology Free Definition of Self Sovereign Identity
|
||||
That October, [Joe Andrieu](https://github.com/jandrieu) submitted [A Technology‐Free Definition of Self‐Sovereign Identity](https://github.com/jandrieu/rebooting-the-web-of-trust-fall2016/raw/master/topics-and-advance-readings/a-technology-free-definition-of-self-sovereign-identity.pdf) to the third Rebooting the Web of Trust Design Workshop. Within it, he describes the Characteristics of SSI: **Control**, **Acceptance**, and **Zero Cost**.
|
||||
|
||||
>1 No disrespect to Christopher Allen’s opening to the conversation, The Path to Self Sovereign Identity [...] It gets a lot right, but leaves a few requirements out, e.g., recoverability and zero cost, and conflates “identities” and claims in an ambiguous manner.
|
||||
|
||||
### Fundamental Characteristics of Self-Sovereign Identity
|
||||
|
||||
#### CONTROL
|
||||
* **Self‐sovereign identities are controlled by the individual:**
|
||||
* **Self‐generatable and Independent:** Individuals must be able to create identity information without asking for permission and be able to assert identity information from any authority. The resulting identity must have the same technical reliability as those provided by well‐known, “official” sources. The observer, of course, is always free to decide whether or not a given piece of information is meritorious, but the information must be able to be verified as a non‐repudiatable statement of correlation using exactly the same mechanisms regardless of source. Further, individuals must be able to present self‐generated identity information without disclosing that the authority in the claim is the subject of the claim.
|
||||
* **Opt‐in**: The affordance for asserting identity information starts with the individual. While an individual may present claims from known or accepted third party authorities, it is the individual who asserts that the claim applies to them. Self‐sovereign identities begin with the will of the individual, with the intentional presentation of identity information.
|
||||
* **Minimal Disclosure**: Individuals should be able to use services with minimal identity information. Features that depend on enhanced correlation must be understood by the average user. Such features should be permissioned with the highest granularity, so functions independent of correlation work equally well alongside those dependent on it. It is not acceptable to deny services because of a refusal to provide unrelated information.
|
||||
* **Non‐participation**: Individuals must be able to choose to not provide identity information for services where it isn’t absolutely required. Any spontaneous identifiers necessary for a service to function, such as cookies or session ids, must use the same infrastructure for consent, persistence, transience, and disclosure as if provided by the individual.
|
||||
* **Opt‐out**: Individuals should be able to opt‐out of identifying records post‐facto as a matter of course. People should be able to stop the use of a correlating identity information by request. Some transactions necessarily require long term retention of identity information, such as financial transactions, purchases, and shipments. Actions that create permanent records should be clearly marked and communicated such that the retention is expected and understood by the average person. All other actions which leverage a self‐sovereign identity should be de‐correlated on‐demand and said identifiers should no longer be used to correlate that individual across contexts.
|
||||
* **Recoverable**: Sovereign identities must be robust enough to be recovered even if hard drives are lost, wallets stolen, or birth certificates lost in a fire. Self‐sovereign identities must provide a way for individuals to recover and reassert that existing identify information applies to them even in the face of complete loss of credentials. This may be challenging given current technical proposals, but the point of this paper is to explore the non‐technical requirements of a self‐sovereign identity. To fully address the needs of UN Sustainable Development Goal 16.9, identity assurance can’t depend on pieces of paper, devices, or other artifacts that can be lost, stolen, destroyed, and falsified.
|
||||
|
||||
#### ACCEPTANCE
|
||||
* **Self‐sovereign identities are accepted wherever observers correlate individuals across contexts.**
|
||||
* **Standard**: There is an open, public standard managed through a formal standards body, free to use by anyone without financial or intellectual encumbrance. Simple The core standard (schema, serialization, and protocols) must be atomically minimal, providing the barest data set, allowing complexity to emerge not from a complicated data model but from a multiplicity of information types, authorities, and observations.
|
||||
* **Non‐repudiatable**: Individual claims should be cryptographically signed to assure non‐repudiatable statements of correlation. Long term, public and semi‐public ledgers should be used to record claims that become statistically impossible to falsify over time. Self‐sovereign identities, at a minimum depend on cryptographic assurances, and most likely will be further enabled by non‐repudiatable public ledgers.
|
||||
* **Reliable**: Access to self‐sovereign identities must be at least as reliable as access to the Internet. It should not rely on any individual or group of centralized servers, connections, or access technologies. Substantially Equivalent Above all, self‐sovereign identities must meet the needs of legacy identity observers at least as well as current solutions. If the core architecture is inherently less capable than existing approaches there is little hope of systemic adoption.
|
||||
|
||||
#### ZERO COST
|
||||
* **Finally, any proposed standard for self‐sovereign identity must be adoptable at absolutely minimal cost.**
|
||||
* Not only must it be free of licensing encumbrances, it must be implementable with readily available, inexpensive, commodity hardware running common operating systems. If it can’t be achieved using today’s commodity products, then we must help manufacturers incorporate what we need.
|
||||
|
||||
**In order to reach every last person on the planet**—the explicit target of UN Sustainable Development Goal 16.9—**self‐sovereign identity must be realizable at massive scale with close to zero marginal cost**.
|
||||
|
||||
The systems we use to make sense of the resulting identity transactions will provide more than enough consulting, software, and hardware revenue to finance the development of the core enabling technology. Just as the web browser was a zero cost entry into a vast economic and innovation engine of the world‐wide web, so too must self‐sovereign identity begin with the most cost‐effective on‐ramp that can be engineered.
|
||||
|
||||
## Furthering the discussion
|
||||
|
||||
* [The Mental Models of Identity Enabled by SSI](https://ssi-ambassador.medium.com/the-mental-models-of-identity-enabled-by-ssi-d3e2d8d0f2b6) 2020-12-03 Adrian Doerk
|
||||
*The Models: Space Time • Presentation • Attribute • Relationship • Capability*
|
||||
> The following five mental models describe what people refer to, when speaking about identity and provide a useful structure of how these models can be executed in a digital environment leveraging SSI infrastructure and components.
|
||||
* [The Three Pillars of Self-Sovereign Identity](https://www.evernym.com/blog/the-three-pillars-of-self-sovereign-identity/) 2019-12-10 Evernym
|
||||
> When implemented for the purpose of identity, everyone everywhere can issue, hold, and verify any credentials about anything. This means no more proprietary silos “owning” your identity. The combination of human and cryptographic trust in this environment means that you can finally get increased security and reduced friction at the same time.
|
||||
* [The 5P’s of a Self-Sovereign Identity](https://markvanrijmenam.medium.com/the-5ps-of-a-self-sovereign-identity-e6f6eb802d75) 2019-06-05 Dr Mark van Rijmenam
|
||||
> A self-sovereign identity can be defined by the 5P’s as it is personal (it is about you), portable (meaning you can take your identity and data from one platform to another), private (you control your identity and data), persistent (it does not change without your consent) and protected (they cannot steal your identity).
|
||||
* [LESS identity](https://medium.com/@trbouma/less-identity-65f65d87f56b) 2018-12-09 Tim Bouma
|
||||
> I arrived at the term ‘Less Identity’ through some fun wordplay (yes, I do this stuff in my spare time). I was thinking about ‘Trust Frameworks’ and ‘Trustless Networks.’ When I factored out the common ‘Trust’, I arrived at ‘Trust[Less Networks and Frameworks].’
|
||||
|
||||
## Prior Art
|
||||
* [The Windhover Principles for Digital Identity, Trust, and Data](http://web.archive.org/web/20180228025834/https://www.tokencommons.org/Windhover-Principles-for-Digital-Identity-Trust-Data.html) 2014-09-21
|
||||
>
|
||||
* [The Laws of Identity](https://www.identityblog.com/stories/2005/05/13/TheLawsOfIdentity.pdf) 2005-05-13
|
||||
|
|
@ -4,14 +4,16 @@ title: Microledgers and Edge-Chains - A Primer
|
|||
description: A Transcript of Daniel Hardman of Evernym Presenting at Hyperledger Global Forum — 2018
|
||||
excerpt: "Evernym’s Chief Architect Daniel Hardman takes the Hyperledger community through Evernym’s work on Microledgers and Edge-Chains Architecture. Attendees will gain insight into the theory, applications and evolution in Hyperledger Indy along with a practical discussion of their potential."
|
||||
image: "https://i.imgur.com/qbVl47T.png"
|
||||
canonical_url: 'https://decentralized-id.com/hyperledger/hgf-2018/Microledgers-Edgechains-Hardman-HGF/'
|
||||
canonical_url: 'https://decentralized-id.com/topics/Microledgers-and-Edgechains_Daniel-Hardman_HGF2018/'
|
||||
redirect_from:
|
||||
- /hgf-2018/Microledgers-Edgechains-Hardman-HGF/
|
||||
- /hgf-2018/Microledgers-Edgechains-Hardman-HGF
|
||||
permalink: organizations/hyperledger/hgf-2018/Microledgers-Edgechains-Hardman-HGF/
|
||||
permalink:
|
||||
redirect_from:
|
||||
- organizations/hyperledger/hgf-2018/Microledgers-Edgechains-Hardman-HGF/
|
||||
author_profile: false
|
||||
categories: ["Literature"]
|
||||
tags: ["Indy","Transcript","Hyperledger Forum","Evernym","GDPR","DID:PEER","Literature"]
|
||||
categories: ["Topics"]
|
||||
tags: ["Indy","Transcript","Hyperledger Forum","Evernym","GDPR","DID:PEER","Literature","HGF 2018"]
|
||||
published: true
|
||||
last_modified_at: 2019-12-11
|
||||
---
|
||||
|
|
@ -26,6 +26,15 @@ last_modified_at: 2023-06-23
|
|||
> 4. Reveals whether or not the credential has been revoked
|
||||
* [Token-Based Identity](https://www.windley.com/archives/2021/10/token-based_identity.shtml) 2021-10 Phil Windley
|
||||
> Token-based identity systems move us from talking about who, to thinking about what, so that people can operationalize their digital lives. Token-based identity systems support complex online interactions that are flexible, ad hoc, and cross-domain.
|
||||
* [The Basic Building Blocks of SSI](https://freecontent.manning.com/the-basic-building-blocks-of-ssi/) 2020-07-29 Drummond Reed, Alex Preukschat Manning
|
||||
> In many cases these core concepts have been established for decades. What’s new is how they’re put together to create a new model for digital identity management. The purpose of this article is to quickly familiarize you with these seven basic building blocks from a conceptual and technical point-of-view.
|
||||
> - Verifiable credentials (aka digital credentials)
|
||||
> - Issuers, holders, and verifiers
|
||||
> - Digital wallets
|
||||
> - Digital agents and hubs
|
||||
> - Decentralized identifiers (DIDs)
|
||||
> - Blockchains
|
||||
> - Governance frameworks (aka trust frameworks)
|
||||
* [Your User is Your API](https://www.evernym.com/blog/your-user-is-your-api/) 2021-05-17 Evernym
|
||||
> The customer becomes the integration point. The customer is the API. Rather than having one huge, expensive, and probably illegal data hub, every customer becomes a data hub in their own right. They provide the data needed, just-in-time, under their control.
|
||||
* [The Unbundling of Authentication vs Authorization - What You Need to Know](https://www.pingidentity.com/en/company/blog/posts/2021/authentication-vs-authorization.html) 2021-09-08 Ping Identity
|
||||
|
|
|
|||
|
|
@ -8,7 +8,7 @@ header:
|
|||
image: /images/uport.webp
|
||||
caption: "[Releasing uPort Libraries 1.0](https://medium.com/uport/releasing-uport-developer-platform-1-0-97d6f70c5e4a)"
|
||||
teaser: /images/uport-teaser.webp
|
||||
categories: ["Blockchain ID"]
|
||||
categories: ["Web 3"]
|
||||
tags: ["Ethereum","Credentials Community Group","GDPR","DID","DIDComm","Consensys","Verifiable Credentials","uPort","Web3","Zug","GLEIF","PWC","Onfido","DIF","uPortlandia","Switzerland"]
|
||||
redirect_from:
|
||||
- id-initiatives/ethereum/uport
|
||||
|
|
@ -10,7 +10,7 @@ layout: single
|
|||
author_profile: false
|
||||
permalink: /blockchain/3box/
|
||||
canonical_url: 'https://decentralized-id.com/blockchain/3box/'
|
||||
categories: ["Blockchain ID"]
|
||||
categories: ["Web 3"]
|
||||
tags: ["Ethereum","DIF","Web3","3box","uPort","Verifiable Credentials","IPID"]
|
||||
last_modified_at: 2020-11-05
|
||||
toc: false
|
||||
|
|
@ -7,7 +7,7 @@ excerpt: >
|
|||
header:
|
||||
image: /images/consensys-header.webp
|
||||
teaser: /images/consensys-teaser.webp
|
||||
categories: ["Blockchain ID","Organizations"]
|
||||
categories: ["Web 3"]
|
||||
tags: ["Ethereum","Web3","Consensys","Zug","uPort","DIF","uPortlandia","RWoT"]
|
||||
permalink: blockchain/ethereum/consensys/
|
||||
canonical_url: https://decentralized-id.com/blockchain/ethereum/consensys/
|
||||
|
|
@ -1,16 +1,5 @@
|
|||
---
|
||||
date: 2019-04-01
|
||||
layout: single
|
||||
title: SSI-Meetup
|
||||
excerpt: >
|
||||
SSI Meetup is an open, collaborative community to help SSI evangelists around the world, independent of company interests or standards. Our main mission is to help you connect with other SSI enthusiasts and create a dynamic, local, yet globally connected community.
|
||||
toc_sticky: false
|
||||
categories: ["Media"]
|
||||
tags: ["SSI-Meetup","GDPR","Aries","MyData","IIW","Self Sovereign Identity","Alastria","CULedger","MyCuID","Trust Framework","Media"]
|
||||
canonical_url: 'https://decentralized-id.com/organizations/ssi-meetup/'
|
||||
redirect_from: organizations/ssi-meetup
|
||||
permalink: organizations/ssi-meetup/
|
||||
last_modified_at: 2019-07-20
|
||||
published: false
|
||||
---
|
||||
|
||||
|
||||
Loading…
Add table
Add a link
Reference in a new issue