mirror of
https://github.com/Decentralized-ID/decentralized-id.github.io.git
synced 2024-12-24 06:39:31 -05:00
sort
This commit is contained in:
parent
ed2e1ca13d
commit
4eae83bddb
@ -16,6 +16,8 @@ toc: false
|
||||
---
|
||||
|
||||
* [curated list] [Peacekeeper's Blockchain and Identity](https://github.com/peacekeeper/blockchain-identity) 2021-11-23
|
||||
* [Identity Blockchains and Energy Consumption](https://indicio.tech/identity-blockchains-and-energy-consumption/) 2021-10-19 Indicio
|
||||
A decentralized network using a blockchain-based distributed ledger means you can use [Peer DIDs](https://identity.foundation/peer-did-method-spec/) to move most “transactions” and their cryptographic proofing off ledger. This means that for those peer-to-peer interactions, identity blockchains don’t need to do any ledger transactions at all.
|
||||
* [NIST CYBERSECURITY WHITE PAPER] [**_A Taxonomic Approach to Understanding Emerging Blockchain Identity Management Systems_**](https://arxiv.org/pdf/1908.00929.pdf) 2019-06-09
|
||||
> Identity management systems (IDMSs) are widely used to provision user identities while managing authentication, authorization, and data sharing both within organizations as well as on the Internet more broadly. Traditional identity systems typically suffer from single points of failure, lack of interoperability, and privacy issues such as encouraging mass data collection and user tracking. Blockchain technology has the potential to support novel data ownership and governance models with built-in control and consent mechanisms, which may benefit both users and businesses by alleviating these concerns; as a result, blockchain-based IDMSs are beginning to proliferate. This work categorizes these systems into a taxonomy based on differences in architecture, governance models, and other salient features. We provide context for the taxonomy by describing related terms, emerging standards, and use cases, while highlighting relevant security and privacy considerations.
|
||||
* [Identity and Distributed Ledger - Today and Tomorrow - June 26 - Identiverse 2019](https://www.youtube.com/watch?v=l04AHP7kPPw) 2019-06-26
|
||||
|
||||
@ -22,6 +22,8 @@ last_modified_at: 2023-06-07
|
||||
> IEUDI, together with DINZ’s Te Kāhui Te Tiriti O DINZ and Digital Identity Services Trust Framework (DISTF) [work groups](https://digitalidentity.nz/working-groups/), detail the scope of DINZ’s mahi this year and into 2023 in pursuit of its mission – to create a digital identity ecosystem that enhances privacy, trust and improves access for all people in New Zealand. [...]
|
||||
>
|
||||
> The DISTF WG met last week also, to discuss the [Select Committee’s report](https://www.legislation.govt.nz/bill/government/2021/0078/latest/whole.html) following the [submissions](https://www.parliament.nz/en/pb/bills-and-laws/bills-proposed-laws/document/BILL_116015/tab/submissionsandadvice), containing its recommended changes to [the Bill](https://www.legislation.govt.nz/bill/government/2021/0078/latest/whole.html) prior to its Second Reading.
|
||||
* [Honouring Te Tiriti in our work](https://digitalidentity.nz/2021/11/18/honouring-te-tiriti-in-our-work/) 2021-11-18 DigitalNZ
|
||||
> We understand that our responsibility to guide conversations and decisions relating to digital identity means that we must acknowledge and understand Māori perspectives of identity. We also seek to engage with the Māori communities we serve to ensure that we are working in partnership and that mana whenua have the agency to inform our future. [Draft Statement of Intent; Te Tiriti o Waitangi at DINZ](https://www.dropbox.com/s/09tfy4m4e6jbq6l/DINZ%20Te%20Tiriti%20o%20Waitangi%20SOI%20%26%20Action%20Plan%20%28V2%29.pdf)
|
||||
* [A key place for Identity in the Digital Strategy for Aotearoa](https://digitalidentity.nz/2021/10/05/a-key-place-for-identity-in-the-digital-strategy-for-aotearoa/) < - Colin Wallis will now head Digital Identity.nz 2021-10-05
|
||||
> Our government is embarking on a journey to create [A Digital Strategy for Aotearoa](https://www.cio.com/article/3628718/national-strategy-digital-twin-and-skills-shortages-on-nz-tech-minister-s-mind.html) that seeks to respond to the social, economic, education and cultural opportunities from digital technology, along with the risks that these technologies can bring.
|
||||
* [The Trust Economy in a Future New Zealand](https://digitalidentity.nz/2021/06/16/the-trust-economy-in-a-future-new-zealand/) 2021-06-16
|
||||
|
||||
@ -33,6 +33,10 @@ last_modified_at: 2023-06-08
|
||||
|
||||
* [The European Digital Identity Regulation](https://www.european-digital-identity-regulation.com/) 2023-04-08
|
||||
> The Regulation amends Regulation (EU) 910/2014 on electronic identification and trust services for electronic transactions in the internal market (‘the eIDAS Regulation’). This amendment is required, as digitalisation of all functions of society has increased dramatically. The provision of both public and private services is increasingly becoming digital after the COVID-19 pandemic.
|
||||
* [Commission puts forward declaration on digital rights and principles for everyone in the EU](https://ec.europa.eu/commission/presscorner/detail/en/ip_22_452) 2022-01-26 EU Commission
|
||||
> The draft declaration covers key rights and principles for the digital transformation, such as placing people and their rights at its centre, supporting solidarity and inclusion, ensuring the freedom of choice online, fostering participation in the digital public space, increasing safety, security and empowerment of individuals, and promoting the sustainability of the digital future.
|
||||
>
|
||||
> These rights and principles should accompany people in the EU in their everyday life: affordable and high-speed digital connectivity everywhere and for everybody, well-equipped classrooms and digitally skilled teachers, seamless access to public services, a safe digital environment for children, disconnecting after working hours, obtaining easy-to-understand information on the environmental impact of our digital products, controlling how their personal data are used and with whom they are shared.
|
||||
* [Global state of SSI and how to build on it: EU report](https://www.biometricupdate.com/202201/global-state-of-ssi-and-how-to-build-on-it-eu-report) 2022-01-24
|
||||
> The European Union’s cybersecurity agency has been busy typing up its research. The latest report is an overview of Self-Sovereign Identity (SSI) technologies, standards, providers and regulation from around the world with a view to their relevance applicability to the EU project for digital identity for individuals and businesses.
|
||||
* [Digital Identity: Leveraging the SSI Concept to Build Trust](https://www.enisa.europa.eu/publications/digital-identity-leveraging-the-ssi-concept-to-build-trust)
|
||||
|
||||
@ -80,7 +80,7 @@ last_modified_at: 2023-06-09
|
||||
> The EBSI aims to become a “gold standard” digital infrastructure to support the launch and operation of EU-wide cross-border public services. It is a multi-blockchain network with multiple use-cases such as notarization of documents, ESSIF, certification of diplomas and trusted data sharing. While there is an EBSI wallet, it’s for test purposes only and not for the public. The consensus of the permissioned network will be achieved via proof of authority (POA) with one note per member state.
|
||||
* [Understanding the European Self-Sovereign Identity Framework (ESSIF) – Daniël Du Seuil and Carlos Pastor – Webinar 32](https://ssimeetup.org/understanding-european-self-sovereign-identity-framework-essif-daniel-du-seuil-carlos-pastor-webinar-32/) 2019-07-07 SSI-Meetup
|
||||
> European Blockchain Partnership (EBP) assists the European Commission in establishing a European Blockchain Services Infrastructure (EBSI). In the short term (2019-2020), the main objective is to start the operation of EU-wide Blockchain-based services and to promote the use of the EBSI in “virtually” every domain of the public sector able to benefit from Blockchain technology. The EBSI has a particular focus on cross-border public services. In 2018, the EBP identified a set of Use-Cases to be implemented on the EBSI one of these important use cases is the European Self Sovereign Identity Framework (ESSIF). The EBSI will implement a generic Self-Sovereign Identity capability that is integrated and interoperable with existing building blocks and legal frameworks like eIDAS and GDPR.
|
||||
* [Presentation] [European Self Sovereign Identity Framework](https://www.eesc.europa.eu/sites/default/files/files/1._panel_-_daniel_du_seuil.pdf) Europa.EU 2019-01-24
|
||||
* [Presentation] [European Self Sovereign Identity Framework](https://www.eesc.europa.eu/sites/default/files/files/1._panel_-_daniel_du_seuil.pdf) 2019-01-24 EU Commission
|
||||
> In European Blockchain Partnership NL-GER-BE started a initiative on
|
||||
> European Self Sovereign Identity framework (eSSIF).
|
||||
> ○ How to facilitate cross-border interaction with SSI.
|
||||
|
||||
@ -11,7 +11,7 @@ canonical_url: https://decentralized-id.com/organizations/decentralized-identity
|
||||
redirect_from:
|
||||
- organizations/identity-foundation/wg/interop/
|
||||
categories: ["Open Source Projects"]
|
||||
tags: ["Interop WG","DIF","IETF","W3C","Credentials Community Group","hyperledger foundation","Trust over IP"]
|
||||
tags: ["Interop WG","DIF","IETF","W3C","Credentials Community Group","Hyperledger Foundation","Trust over IP","Interop"]
|
||||
header:
|
||||
image: /images/dif-interop-head.webp
|
||||
teaser: /images/dif-interop-teaser.webp
|
||||
@ -40,3 +40,6 @@ last_modified_at: 2020-11-26
|
||||
>
|
||||
> This document is live-edited DURING each call, and stable/authoritative copies live on our github repo under /agenda.md . Please note that we might not notice a pullrequest in time, but you are free to propose agenda items for future meetings via hackmd .
|
||||
* [Input Documents + Bibliography](https://www.notion.so/dif/be6763341a014d248f655aea187d7890)
|
||||
* [Decentralzied Mapping Initiative](https://whimsical.com/decentralized-mapping-exercise-CUhk3dT4RUZvGa4Lt7rNvD) – DIF Interop WG
|
||||

|
||||
* [Bob Blakely shared his reflections on SAML interop work](https://us02web.zoom.us/rec/play/xnxk16ksNsA9CP4UgR9BqylnH6qT1WZlSpFc9LOweFI7HZNcn8KR3A-0OsUDbPuNM6o0tt1JrSMqGV4Z.dnAMXXLE5-62VAfX?continueMode=true&_x_zm_rtaid=Qs7tORTgRhmEiSBbcDzQLg.1645215091973.9fac74d22719638c1d1b641c83b0f5c7&_x_zm_rhtaid=448) 2022-09 DIF Interop WG
|
||||
@ -1,6 +1,10 @@
|
||||
---
|
||||
published: false
|
||||
---
|
||||
* [Is the Self-Sovereign digital identity the future digital business registry?](https://blogs.worldbank.org/psd/self-sovereign-digital-identity-future-digital-business-registry) GORAN VRANIC, ANDREJA MARUSIC; WorldBank
|
||||
> This rapid digitalization of the private sector exposed a challenge in the business registration paradigm. To use private digital platforms for e-Logistics or e-Commerce, SMEs have to register and confirm their identity with these platforms, despite already being identified in the government business registry.
|
||||
* [Apartment rentals and fraud: Discover technology that will ensure trusted content](https://medium.com/@michelplante/apartment-rentals-and-fraud-cf2ebc572890)
|
||||
> At the root of the problem is the fact that uniquely identifying a person is hard to do and that people can create fake IDs for themselves quite easily.
|
||||
|
||||
# Business
|
||||
|
||||
|
||||
@ -20,9 +20,6 @@ there is a push by corporations and international institutions such as the World
|
||||
* [India Will Once Again Require Biometric Attendance for Government Employees](https://findbiometrics.com/india-will-once-again-require-biometric-attendance-government-employees-110505/)
|
||||
|
||||
Public institutions in India will soon be resuming their use of contact-based biometric sensors. Biometric authentication had been mandatory for all government employees prior to the pandemic, but the Indian central government was [one of several institutions](https://findbiometrics.com/biometrics-news-hyderabad-punjab-join-governments-banning-fingerprint-based-biometrics-amid-fears-covid-19-030602/) that [suspended the practice](https://findbiometrics.com/authorities-in-pakistan-india-suspend-biometric-attendance-systems-over-covid-19-concerns-902281/) due to health concerns following the outbreak of COVID-19.
|
||||
* [Why a Little-Known Blockchain-Based Identity Project in Ethiopia Should Concern Us All](https://www.cigionline.org/articles/why-a-little-known-blockchain-based-identity-project-in-ethiopia-should-concern-us-all/) Cigi Online
|
||||
|
||||
Hoskinson [says](https://iohk.io/en/blog/posts/2021/04/28/decentralized-identity-on-the-blockchain-is-the-key-to-iohks-vision-for-africa/) his mission is to give people in Africa control over their own lives. But in reality, his plans for Ethiopia appear crypto-colonial. As researcher Pete Howson [explains](https://www.coindesk.com/markets/2021/07/14/the-headache-of-crypto-colonialism/), “Innovators are not drawn to fragile states because they want to fix these things. Poverty and corruption are the ideal conditions for entrepreneurs exploring opportunities to extract resources from vulnerable communities.” 2021-07-14
|
||||
* [Singapore’s tech-utopia dream is turning into a surveillance state nightmare](https://restofworld.org/2021/singapores-tech-utopia-dream-is-turning-into-a-surveillance-state-nightmare/) RestofWorld
|
||||
|
||||
“What [technology] will do for people is make our lives a hell of a lot easier, more convenient, more easily able to plug into the good life,” said Monamie Bhadra Haines, an assistant professor at the Technical University of Denmark, who studies the intersection between technology and society. “But … the surveillance is what is here, now.”
|
||||
|
||||
@ -3,6 +3,8 @@ published: false
|
||||
---
|
||||
|
||||
# Explainer
|
||||
* [It’s time for digital self-sovereign identity](https://gcn.com/emerging-tech/2022/08/its-time-digital-self-sovereign-identity/375285/) GCN
|
||||
> the implementation of granular security measures to protect that data creates trusted networks between governments and the citizens they serve. Everyone wins.
|
||||
|
||||
* [Kaliya Young on Identikit with Michelle Dennedy](https://identitywoman.net/podcast-identikit-with-michelle-dennedy/)
|
||||
|
||||
@ -742,9 +744,6 @@ This is excellent work, with lots of references, by Dr. Nuttawut Kongsuwan ([Fin
|
||||
|
||||
* [The Verifiable Credential’s Model](https://trinsic.id/trinsic-basics-the-verifiable-credentials-model/)
|
||||
> At the core of every self-sovereign identity (SSI) use case is what we call the verifiable credentials model. This simple yet effective model helps conceptualize how verifiable credentials are exchanged between people and organizations.
|
||||
* [What Is a Blockchain (SSI) Self-Sovereign Identity?](https://www.youtube.com/watch?v=uq0MQH4fAgc&t=3s) Blockchain Africa Conference 2022
|
||||
|
||||
What is the value of Self-Sovereign Identity (SSI) for organisations and citizens? What are the current initiatives and traction of SSI in South Africa? What are the economic benefits and the hurdles to SSI adoption in South Africa?
|
||||
|
||||
|
||||
|
||||
|
||||
@ -3,6 +3,9 @@ published: false
|
||||
---
|
||||
|
||||
# Future of Digital Identity
|
||||
* [The Future of Digital Identity: Separating the digital from the individual](https://www.finextra.com/the-long-read/421/the-future-of-digital-identity-separating-the-digital-from-the-individual) 2022-07-27 ([Report](https://www.finextra.com/finextra-downloads/research/documents/245/the-future-of-digital-identity-2022.pdf)
|
||||
|
||||
While biometrics are now part and parcel of life in 2022 – with the prevalence of mobile payments with Face ID and Touch ID – the concept of real-time and frictionless processes is what is driving the future of digital identity forward.
|
||||
|
||||
* [The Future of Identity. A collection of interconnected research](https://borgbraincrypto.medium.com/the-future-of-identity-eee42109efd2)
|
||||
> A collection of interconnected research and thoughts, on the topics, technologies, and projects concerning the future of identification, DID’s, SSI’s, biometrics, data, ai, reputation, credentials, medical history, blockchain, privacy, and ethics, on what it should mean to us as humans, and the implications for the future of this world and our relationship with it.
|
||||
|
||||
@ -85,9 +85,6 @@ a simple mechanism to provide public information concerning an entity by adverti
|
||||
> Machine-readable governance is composed of elements that help to establish trust and enable interoperability: trusted participants, schemas (templates for structuring information in a credential), and rules and flows for presenting credentials and verifying them. Machine-readable governance can be hierarchical. Once a governance system is published, other organizations can adopt and then amend or extend the provided system.
|
||||
|
||||
|
||||
* [3 Stages of a Pan-African Identity Framework for Establishing Self-Sovereign Identity With Blockchain](https://www.frontiersin.org/articles/10.3389/fbloc.2021.631640/full) Solomon Darnell, Joseph Sevilla
|
||||
|
||||
Three stages have been identified as necessities to accomplish the development of this system before opening it further beyond the pan-African worldwide community. The three stages are defined by systems that allow for biometric/demographic registration (stage 1), interoperability and security hardening (stage 2), and biometric modality data analysis/organization/association (stage 3).
|
||||
* [Governance: Clarifying or confusing the marketplace?](https://iiw.idcommons.net/19A/_Governance:_Clarifying_or_confusing_the_marketplace%3F)
|
||||
|
||||
Governance in decentralized identity is more akin to “technical rules and instructions.” This is highly disfluent in part because it is so extensive and in part because it relies on a new vocab that uses familiar words in unfamiliar ways. All of this creates disfluency to such a degree that it is unpleasant to contemplate and that unpleasantness is transferred onto the product.
|
||||
|
||||
@ -4,6 +4,8 @@ published: false
|
||||
|
||||
# Fido Alliance
|
||||
|
||||
- [SSI and FIDO2: Different approaches for a passwordless world](https://blog.avast.com/ssi-fido2)
|
||||
|
||||
++++ LoginWithFIDO.com https://loginwithfido.com/
|
||||
|
||||
++++ Consumer Research https://fidoalliance.org/consumerresearch/
|
||||
|
||||
@ -14,6 +14,9 @@ published: false
|
||||
- Apple
|
||||
- Google
|
||||
|
||||
## Microsoft
|
||||
* [They are using Entra!](https://www.credivera.com/the-exchange/verifiable-credentials)
|
||||
|
||||
## Apple
|
||||
|
||||
* [iOS 15 Code Points to Biometric Onboarding for Apple’s Mobile ID](https://findbiometrics.com/ios-15-code-points-biometric-onboarding-apples-mobile-id-77202104/) 2021-07-30 FindBiometrics
|
||||
@ -25,6 +28,15 @@ published: false
|
||||
Amazon customers will first need to register their palm(s) using a scanner at the store. They will then be able to link a debit or a credit card to that palm print, which will in turn allow them to pay for their purchases with only a palm recognition scan the next time they pass through checkout.
|
||||
|
||||
## Evernym
|
||||
* [Evernym Selected as a 2021 Technology Pioneer by the World Economic Forum](https://www.evernym.com/blog/wef-technology-pioneer/) Evernym
|
||||
> The 2021 cohort of Tech Pioneers includes many future headline-makers at the forefront of their industries. These companies show great potential to not only shake up their industries but offer real solutions to global problems.
|
||||
|
||||
* [Introducing Veramo](https://medium.com/uport/introducing-veramo-5a960bf2a5fe)
|
||||
> In our last post we briefly presented Veramo and how it evolved from the [challenges faced with uPort’s libraries](https://medium.com/uport/veramo-uports-open-source-evolution-d85fa463db1f). In this next series of articles we will give Veramo a proper introduction and answer some of the basics: why it exists and what it does, followed by articles describing the architecture in more detail, and how to build applications using [Veramo](https://veramo.io).
|
||||
|
||||
## Auth0
|
||||
* [Verifiable Credentials with Auth0 and MATTR](https://auth0.com/blog/verifiable-credentials-with-auth0-and-mattr/)
|
||||
> How to issue Verifiable Credentials from Auth0 user data using MATTR's Auth0 Marketplace Integration
|
||||
|
||||
* [CULedger partners with decentralized identity innovator Evernym to create MyCUID](https://www.cuinsight.com/press-release/culedger-partners-decentralized-identity-innovator-evernym-create-mycuid) 2018-02-26
|
||||
> CULedger, builder of innovative blockchain-based products for credit unions and their members, teamed up with Evernym to launch MyCUID, a new consumer-focused digital identity solution. With MyCUID, credit union members can confidently protect themselves from financial fraud and identity theft, while enriching the trusted relationships members have with their credit unions.
|
||||
@ -128,13 +140,6 @@ It starts with IdentityOps embracing high assurance for connected devices. You
|
||||
|
||||
Gravity and Tykn are pleased to announce our continued collaboration to advance the interoperability of our two distinct decentralized identity solutions for improved identity management in the humanitarian sector.
|
||||
|
||||
|
||||
### Cardano
|
||||
|
||||
* [Ethiopia: Innovation - Here's What Cardano (ADA) Has Been Up to With the Ethiopia Project](https://allafrica.com/stories/202108190100.html)
|
||||
|
||||
"The vision of the company is to improve the systems of the world for everyone everywhere, and the places that need better systems aren't necessarily Berlin or New York City. So you have to go to places that are a little more difficult, and you have to be very careful as you do it."
|
||||
|
||||
### Gimly
|
||||
|
||||
* [Gimly ID: SSI with OpenID authentication](https://www.loom.com/share/d49e005bb32349d7950022e83d55b944)
|
||||
@ -274,11 +279,6 @@ Demonstrates a financial "KYC" identity proofing using TrustBloc DIDComm capabil
|
||||
> - Rules and standards
|
||||
> - Operational considerations
|
||||
|
||||
### Onfido
|
||||
* [Remittances Specialist Leverages Biometric Onboarding Via Onfido](https://findbiometrics.com/remittances-specialist-leverages-biometric-onboarding-via-onfido-050604/) Find Biometrics
|
||||
|
||||
Chipper Cash has become the latest financial institution to adopt Onfido’s identity verification technology. The company currently operates one of the largest money transfer platforms in Africa, and is hoping
|
||||
|
||||
### IDWorks
|
||||
|
||||
* [IDWorks turned to Tarmac to help accelerate their mobile app and backend development](https://www.tarmac.io/case-study/idworks.html)
|
||||
|
||||
@ -65,29 +65,6 @@ KYC-Chain will enter a partnership with enVoy. enVoy offers sustainable DeFi, to
|
||||
|
||||
The way many businesses have traditionally implemented KYC is by taking a manual, fragmented approach – essentially implementing various different KYC processes using different tools, methods and resources, including human compliance teams.
|
||||
|
||||
## Africa SSI Startups
|
||||
- [Daon Provides Biometric Authentication for African Blockchain Identity Platform](https://findbiometrics.com/daon-provides-biometric-authentication-african-blockchain-identity-platform-06100/)
|
||||
|
||||
### Diwala
|
||||
|
||||
### FLexID
|
||||
|
||||
* [FlexID gets Algorand funding to offer self-sovereign IDs to Africa’s unbanked](https://techcrunch.com/2022/05/26/zimbabwe-flexid-algorand-funding-decentralized-identity/) TechCrunch 2022-05-26
|
||||
|
||||
FlexID is giving users a blockchain wallet that stores their verificable credentials. Verification is done on-chain through Algorand, which bills itself as a solution to the [blockchain trilemma](https://www.google.com/search?q=algorand+trilemma&oq=algorand+trilem&aqs=chrome.0.0i512j69i57j0i390.2391j0j9&sourceid=chrome&ie=UTF-8) of security, scalability and decentralization. FlexID will also be integrating with other Algorand decentralized apps (dApps).
|
||||
|
||||
* [Local digital identity startup FlexID receives funding from Algorand Foundation](https://www.techzim.co.zw/2022/05/local-digital-identity-startup-flexid-receives-funding-from-algorand-foundation/) TechZim
|
||||
|
||||
Zimbabwean founded blockchain start-up, [FlexID Technologies](https://www.flexfintx.com/) (formerly FlexFinTx), has signed a Simple Agreement For Equity (SAFE) with the [Algorand Foundation](https://www.algorand.com/), to further develop and scale their Self Sovereign Identity (SSI) platform
|
||||
|
||||
### Gravity Earth
|
||||
* [Q&A with Gravity’s lead engineer: François Guérin](https://medium.com/gravity-earth/q-a-with-gravitys-lead-engineer-fran%C3%A7ois-gu%C3%A9rin-babb3659be86)
|
||||
|
||||
As the Lead Developer, a big part of my role is to build Gravity’s decentralized identity protocol and blockchain architecture on Tezos.
|
||||
* [Gravity’s Decentralized Identity Protocol, Built on Tezos, To Power DIGID Project in Kenya](https://medium.com/gravity-earth/gravitys-decentralized-identity-protocol-built-on-tezos-to-power-digid-project-in-kenya-a85069f2a027)
|
||||
|
||||
This month, Gravity joined some of the largest international NGOs in the world to launch the [Dignified Identities in Cash Programming (DIGID)](https://hiplatform.org/digid) project in Kenya. The goal of this project is to help the Kenya Red Cross leverage Gravity’s decentralized identity protocol on Tezos to provide much-needed cash transfers to vulnerable Kenyan populations.
|
||||
|
||||
## EU SSI Startups
|
||||
|
||||
- MyDex
|
||||
|
||||
@ -76,7 +76,19 @@ JSON-LD
|
||||
### FIDO
|
||||
- [ID-Non-SSI] FIDO (FIDO)
|
||||
|
||||
## VC
|
||||
|
||||
* [New search engine, mobile wallet, verifiable credentials and delivery technologies.](https://twitter.com/HUMBLPay/status/1574454647384813568) via Twitter ([ANN](https://www.globenewswire.com/en/news-release/2022/04/13/2421969/0/en/HUMBL-Selected-To-Pilot-Digital-Wallet-Program-On-Behalf-of-The-County-of-Santa-Cruz-California.html) 2022-04-13 HUMBL @HUMBLPay
|
||||
*using verifiable credentials in their wallet.*
|
||||
> #HUMBL x GF2GO - San Diego, CA - [Pilot Program](https://www.youtube.com/watch?v=H_HAFEzmkWU)
|
||||
|
||||
## DIDs
|
||||
W3C Press Release - [Decentralized Identifiers (DIDs) v1.0 becomes a W3C Recommendation](https://www.w3.org/2022/07/pressrelease-did-rec) worth reading to see who contributed comments (and notice who didn’t)
|
||||
|
||||
For individuals in particular, DIDs can put them back in control of their personal data and consent, and also enable more respectful bi-directional trust relationships where forgery is prevented, privacy is honored, and usability is enhanced.
|
||||
|
||||
## DID Auth
|
||||
|
||||
* [SSI Interaction Patterns](https://www.windley.com/archives/2021/06/ssi_interaction_patterns.shtml)
|
||||
> While the DID Authn pattern is simple, it is not as flexible as we need in some situations. For more complicated scenarios, we can use verifiable credentials. The first scenario we’ll consider is where the same organization is issuing and verifying the credential.
|
||||
> 
|
||||
|
||||
@ -19,3 +19,6 @@ published: false
|
||||
* [Identiproof demonstrates early commitment to Open Badges V3](https://www.crosswordcybersecurity.com/post/identiproof-demonstrates-early-commitment-to-open-badges-v3) Crossworld Cybersecurity
|
||||
|
||||
It does this through selective disclosure, whereby the recipient requests the minimum of information in conformance with GDPR. Identiproof is one of the first systems built to the 2019 W3C recommendations: The Verifiable Credentials Data Model and Web Authentication (FIDO2) - two new global web security standards.
|
||||
|
||||
## Velocity Network
|
||||
Having a look at [the Velocity Whitepaper](https://www.velocitynetwork.foundation/wp-content/uploads/2020/11/Velocity-Non-Technical-Whitepaper-091120-V1.15-Published.pdf) it does mention they are keeping an eye on the work developing in W3C and DIF.
|
||||
|
||||
@ -1,6 +1,10 @@
|
||||
---
|
||||
published: false
|
||||
---
|
||||
* [@Steve_Lockstep · Apr 23](https://twitter.com/Steve_Lockstep/status/1517861150129795072)
|
||||
> I had a stab at why Cardspace failed, in “[Identities Evolve: Why Federated Identity is Easier Said than Done](https://papers.ssrn.com/sol3/papers.cfm?abstract_id=2163241)
|
||||
>
|
||||
> Why does digital identity turn out to be such a hard problem? People are social animals with deep seated intuitions and conventions around identity, but exercising our identities online has been hugely problematic.
|
||||
|
||||
* [4 Keys to Self-sovereign Identity Adoption](https://medium.com/trinsic/4-keys-to-self-sovereign-identity-adoption-ad269b208569) 2021-01-19 Trinsic
|
||||
> Many implementers won’t realize the potential of SSI until it’s deployed at scale, but in order to get to scale, we need implementers to realize value. It’s the classic chicken & egg problem.
|
||||
|
||||
@ -25,3 +25,7 @@ published: false
|
||||
* [eKYC & Identity Assurance WG](https://openid.net/wg/ekyc-ida/)
|
||||
Among the many dots Mark is connecting on behalf of the OpenID Foundation is work with the Global Legal Entity Identifier Foundation, the Open Identity Exchange Trust Framework Initiatives and the Open Banking Implementation Entity.
|
||||
|
||||
* [What Is Self-Sovereign Identity Verification and How Is It Changing Background Screening?](https://www.corporatescreening.com/blog/what-is-self-sovereign-identity-verification-and-how-is-it-changing-background-screening)
|
||||
> A prime example is self-sovereign identity verification, one of the game-changing [background screening trends of 2021](https://www.corporatescreening.com/2021-trends-interactive-infographic). When combined with screening activities, self-sovereign identity solutions offer opportunities to obtain more accurate candidate background data and deliver it to employers faster.
|
||||
* [Coinfirm Adds Close To 1 Million Tokens To AML Platform, Offering Full Coverage](https://www.coinfirm.com/blog/1-million-tokens-aml-crypto/) Coinfirm
|
||||
> LONDON, United Kingdom – In the largest update of protocol coverage in Coinfirm’s history, the firm has added support for 840,361 new tokens to the AML Platform, offering total digital asset coverage of 17 blockchains. Now, the company’s industry-recognized blockchain agnostic AML Platform supports ~846 thousand cryptocurrencies and tokens.
|
||||
|
||||
@ -1,106 +0,0 @@
|
||||
---
|
||||
published: false
|
||||
---
|
||||
|
||||
# IOT
|
||||
|
||||
## Explainer
|
||||
|
||||
* [Distributed Ledger Technologies, IAM, and the Truth in Things](https://www.youtube.com/watch?v=VV2rLgH9TUE) 2019-06-27 Identiverse Robert Brown
|
||||
> The Internet of Things has a problem with data silos – it’s difficult for data to move across domains and prove where it came from. Users of IoT data must understand how Things were made and kept up-to-date if they are to know the data received is truthful. Yet keeping Things healthy is not the sole responsibility of a single actor; components of a Thing may be shared amongst hardware and software vendors, system integrators, retailers, system operators, owners, regulators or third parties. Safety and security rests with all involved in authorizing updates, how and when they are applied as well as the right to repair when Things are no longer officially supported. Shared device lifecycle assurance is the basis for verifiable service histories of Things which give data provenance. When data can be proven to originate from reliable sources, its value increases while reducing the risk of using it. Enabling third parties to build value from data would unlock the true value of IoT which in turn could fund its upkeep. This talk will outline how identity and shared ledger technology have key roles to building Truth in Things for a sustainable IoT.
|
||||
* [Alternatives to the CompuServe of Things](https://www.windley.com/archives/2021/07/alternatives_to_the_compuserve_of_things.shtml) 2021-07 Phil Windley
|
||||
> The current model for connected things puts manufacturers in between people and their things. That model negatively affects personal freedom, privacy, and society. Alternate models can provide the same benefits of connected devices without the societal and personal costs.
|
||||
|
||||
* [Why Machines Need Self-Sovereign Identities](https://www.peaq.com/blog/why-machines-need-self-sovereign-identities) Peaq
|
||||
> As the world becomes even more connected and more machines are hooked up to the internet, the ability for machines to move, trade and interact securely and efficiently becomes increasingly important to life and business. Today’s centralized networks do not enable this. Machines today exist on closed, permission-based environments which massively limit which other machines can be interacted with, what machines can do and where they can go.
|
||||
|
||||
* [Why is Trusted Identity Important in IoT Commerce?](https://dlt.mobi/why-is-trusted-identity-important-in-iot-commerce/)
|
||||
> The evident solution is to imbue connected entities with unique, tamper-evident, self-sovereign, [Decentralized Identifiers (DIDs)](https://www.w3.org/TR/did-core/?mc_cid=1a98f7f0e4&mc_eid=UNIQID), developed by the [W3C](https://www.w3.org/?mc_cid=1a98f7f0e4&mc_eid=UNIQID), anchored in a decentralized trust network. For MOBI’s community, this is the [Integrated Trust Network, or ITN](http://dlt.mobi/itn?mc_cid=1a98f7f0e4&mc_eid=UNIQID).
|
||||
|
||||
* [Self-Sovereign Identity and IoT – insights from the Sovrin Foundation](https://insureblocks.com/ep-146-self-sovereign-identity-and-iot-insights-from-the-sovrin-foundation/) Insureblocks
|
||||
> Michael Shea is the Managing Director of the Dingle Group and the Chair of Sovrin Foundation’sSSI in IoT Working Group. In this podcast we discussed the white paper he authored on Self Sovereign Identity and IoT. To explain the opportunities SSI can provide to IoT, Michael introduces us to three profiles: Jamie (machine to person), Bob (machine to machine) and Bessie the cow (digital twin).
|
||||
|
||||
* [Relationships in the Self-Sovereign Internet of Things](https://www.windley.com/archives/2020/12/relationships_in_the_self-sovereign_internet_of_things.shtml)
|
||||
> DIDComm-capable agents provide a flexible infrastructure for numerous internet of things use cases. This post looks at Alice and her digital relationship with her F-150 truck. She and the truck have relationships and interactions with the people and institutions she engages as she co-owns, lends and sells it. These and other complicated workflows are all supported by a standards-based, open-source, protocol-supporting system for secure, privacy-preserving messaging.
|
||||
|
||||
* [APPLYING CONCEPTS FROM SELF SOVEREIGN IDENTITY TO IOT DEVICES](https://www.theinternetofthings.eu/tim-weingartner-oskar-camenzind-identity-things-applying-concepts-self-sovereign-identity-iot) IOT dot EU
|
||||
> Devices are equipped by the manufacturer with an identity stored in a trusted execution environment (TEE) and secured by a blockchain. This identity can be used to trace back the origin of the device. During the bootstrapping process on the customer side, the identity registration of the device is updated in the blockchain. This process is performed by a so-called registrar. Smart contracts prevent unsolicited transfer of ownership and track the history of the device. Besides proof of origin and device security our concept can be used for device inventory and firmware upgrade.
|
||||
|
||||
* [Easier IoT Deployments with LoraWan and Helium](https://www.windley.com/archives/2022/04/easier_iot_deployments_with_lorawan_and_helium.shtml) 2022-04 Phil Windley
|
||||
> Unlike a Wifi network, you don't put the network credentials in the device, you put the devices credentials (keys) in the network. Once I'd done that, the sensor started connecting to hotspots near my house and transmitting data. Today I've been driving around with it in my truck and it's roaming onto other hotspots as needed, still reporting temperatures.
|
||||
|
||||
* [Digital Twins and Self-Sovereign Identity: Build the next generation of Simulation with privacy preservation](https://iotpractitioner.com/digital-twins-and-self-sovereign-identity-build-the-next-generation-of-simulation-with-privacy-preservation/) IOT Practicioner
|
||||
> Managing IoT devices and user identities as well as the relationships among various devices and their digital twins face significant challenges. First, a lack of Identity Credential and Access Management (ICAM) standards for IoT creates proprietary standards and a lack of interoperability. Second, the operational lifecycle of IoT devices complicates integration of traditional ICAM. Lastly, ICAM technology must adapt to the proliferation of connected devices. This evolution requires a digital trust framework and the decentralized architecture of Self-Sovereign Identity (SSI).
|
||||
|
||||
* [Smart Property](https://www.windley.com/archives/2021/08/smart_property.shtml) Windley
|
||||
> Smart property is much more than the anemic connected things we have now. Smart property imagines a world where every thing participates in digital communities and ecosystems, working through programmable agents under the owners control.
|
||||
|
||||
### Digital Twins
|
||||
|
||||
* [Digital Twins and Self-Sovereign Identity: Build the next generation of Simulation with privacy preservation](https://iotpractitioner.com/digital-twins-and-self-sovereign-identity-build-the-next-generation-of-simulation-with-privacy-preservation/) IOT Practicioner
|
||||
> The rise in the use of advanced analytics, machine learning (ML) and Artificial Intelligence (AI) and the Internet of Things (IoT) today have driven the technology of simulation into the concept of the digital twin. Digital twins are generally defined as a virtual digital model of a physical system that is used to make better decisions about the real world physical system. Digital twins are usually intertwined with sensors and include a two-way interaction between the physical and digital twin.
|
||||
|
||||
## Hackathon Entries
|
||||
|
||||
* [Decentralized Identity of Things](https://blog.darrenjrobinson.com/decentralized-identity-of-things/) Winner Microsoft Decentralized Identity Hackathon
|
||||
> In a real world scenario we anticipate a software based wallet for Decentralized Identity of Things. That would allow automation of online stores to obtain verifiable credentials programmatically.
|
||||
|
||||
* [DIDoT - DID of Things. Decentralized Identity of Things](https://devpost.com/software/did-of-things-didot-allergen-management-in-food-shopping).
|
||||
> Allergen management in food shopping. Based on the concept of ‘things’ having verifiable credentials. [...] Our proposed solution requires a virtual wallet that can be orchestrated programmatically. We discussed how other self sovereign solutions have this capability and confirmed with the AAD Verifiable Credentials hackathon support team that this capability is not available.
|
||||
|
||||
## Company Stories
|
||||
* [More Security in the Internet of Things – Thanks to ETO](https://www.etogruppe.com/en/news/news-from-eto/more-security-in-the-internet-of-things-thanks-to-eto.html) ETO [github](https://gitlab.com/anchor-bundle/angular-webapp)
|
||||
> The ETO GRUPPE has set itself the goal of automating communication in the Internet of Things (IoT) and, on top of that, making it more secure against access and manipulation. To achieve this, these "things" - machines, devices or vehicles - must first be given a unique identity. The solution of the innovative corporate group consists of a new type of network and authentication processes that have what it takes to revolutionize the way we use the Internet today. ETO uses a network of distributed digital identities (DIDs) and verifiable credentials (VCs). A side benefit from the perspective of human Internet users: they regain data sovereignty over their personal data. The ETO solution will enable secure logins on both the Internet and the Internet of Things (IoT)
|
||||
|
||||
* [Trust but Verify](https://stateofidentity.libsyn.com/trust-but-verify) Liminal Podcasts
|
||||
> Peter Padd, Co-Founder & CEO at Fortifyedge shares how he's built Zero Trust authentication software that provides IoT device OEM's with password-free authentication utilizing Tiny Machine Learning at the edge.
|
||||
|
||||
* [Capitalizing on Self-Sovereign Identity for Machines](https://venafi.com/blog/capitalizing-self-sovereign-identity-machines-part-one) [Part One]
|
||||
> By providing a means to globally define an indisputable link between a machine and its machine identity across different sites, networks and businesses, we can secure IoT like never before.
|
||||
>
|
||||
> The filancore integration for Verifiable Credentials is available now. You can learn more from the [Venafi Marketplace](https://marketplace.venafi.com/details/verifiable-credentials-for-iot/).
|
||||
|
||||
## Protocols
|
||||
|
||||
* [Picos at the Edge](https://www.windley.com/archives/2021/11/picos_at_the_edge.shtml) 2021-11 Phil Windley
|
||||
> You can play with this first hand at [NoFilter.org](https://nofilter.org/), which brands itself as a "the world's first unstoppable, uncensorable, undeplatformable, decentralized freedom of speech app." There's no server storing files, just a set of Javascript files that run in your browser. Identity is provided via [Metamask](https://metamask.io/) which uses an Ethereum address as your identifier. [I created some posts on NoFilter](https://nofilter.org/#/0xdbca72ed00c24d50661641bf42ad4be003a30b84) to explore how it works.
|
||||
|
||||
|
||||
## Infographic
|
||||
|
||||
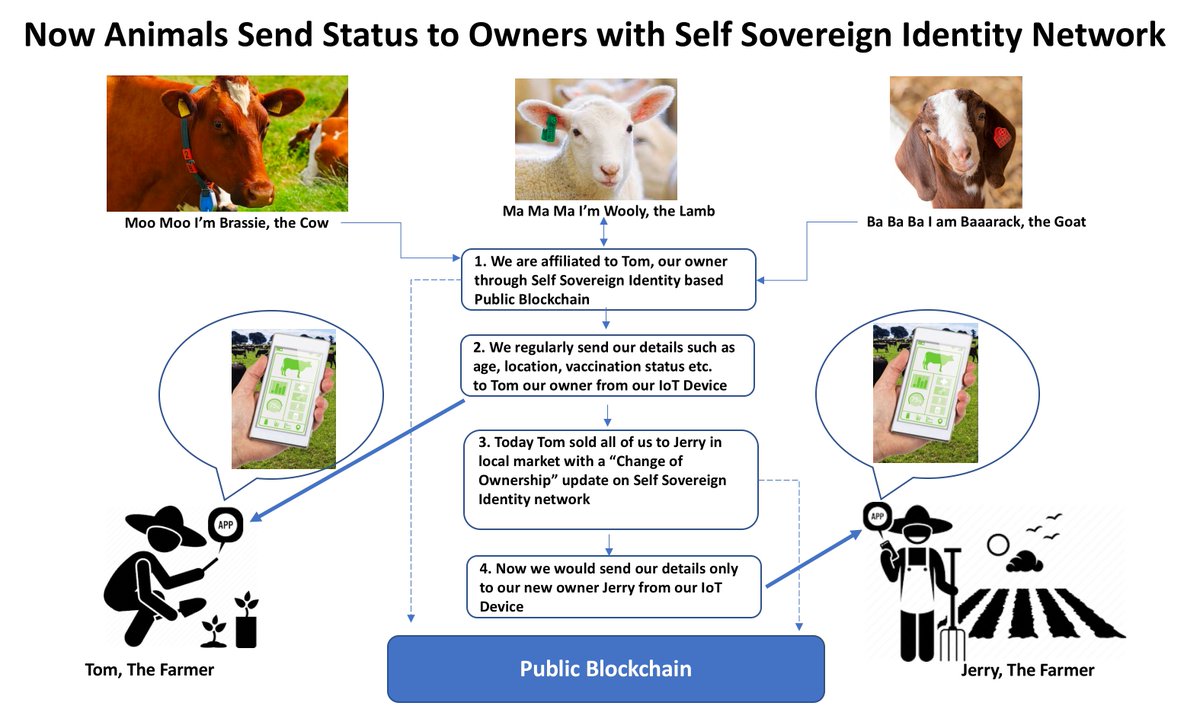
* [Now Animals too can have their own #decentralizedidentity to help them send their status updates](https://twitter.com/debimr75/status/1347915348293533699) Debajani Mohanty
|
||||
> to the rightful owner from their #IoT devices. #Decentralized #digitalidentity for #IoT devices would lead to #SmartFarming
|
||||
> 
|
||||
|
||||
## Organization
|
||||
* [Self-Sovereign Digital Twins](https://dlt.mobi/self-sovereign-digital-twins/) mobi
|
||||
> A Citopia Self-Sovereign Digital Twin™ (SSDT™) is a digital twin whose controller has the ability to participate as an autonomous economic agent in trusted Web3 transactions.
|
||||
* [Battery Passport and the Battery Self-Sovereign Digital Twin](https://dlt.mobi/battery-passport-the-battery-ssdt/) Mobi
|
||||
> Similarly, a [battery passport](https://dlt.mobi/battery-passport) is nothing but a presentation of data points about a particular battery – who manufactured it, its physical and chemical composition, its current state of health, whether it was refurbished or repurposed from another battery, and so on.
|
||||
* [LFPH tackles the next frontier in Open Source Health Technology: The rise of Digital Twins](https://www.lfph.io/2022/08/29/lfph-tackles-the-next-frontier-in-open-source-health-technology-the-rise-of-digital-twins/) 2022-08-29 Linux Foundation Public Health
|
||||
> To create a pairing between the digital world and the real world, a digital twin leverages real time data, such as smart sensor technology, coupled with analytics, and often artificial intelligence (AI) in order to detect and prevent system failures, improve system performance, and explore innovative uses or functional models.
|
||||
* [Digital Twin Consortium](https://www.digitaltwinconsortium.org/)
|
||||
> Digital Twin Consortium drives the awareness, adoption, interoperability, and development of digital twin technology. Through a collaborative partnership with industry, academia, and government expertise, the Consortium is dedicated to the overall development of digital twins. We accelerate the market by propelling innovation and guiding outcomes for technology end-users.
|
||||
|
||||
## User experience
|
||||
* [#ResistIoT: IoT as a medium for surveillance](https://wider.team/2021/04/21/resistiot/) wider team 2021-04-21
|
||||
> - Clinical technology as workplace surveillance. Hospital providers talk about their frustration with connected technologies because it feels like their every motion is being monitored and tracked, used by bosses to evaluate their speed and cost efficiency.
|
||||
> - Civic technologies as government surveillance. From [Oakland’s corner traffic cameras](https://www.aclunc.org/blog/how-fight-stop-oaklands-domain-awareness-center-laid-groundwork-oakland-privacy-commission) leading to mass rallies to [Boston Police](https://www.independent.co.uk/life-style/gadgets-and-tech/news/robots-police-dog-spot-boston-dynamics-a9218491.html) [tests](https://reason.com/2019/11/26/massachusetts-police-test-out-robot-dogs-is-dystopia-on-its-way/) and [NYPD robot dogs](https://www.theverge.com/2021/2/24/22299140/nypd-boston-dynamics-spot-robot-dog), IoT is deep in the creepy depths of [the uncanny valley](https://en.wikipedia.org/wiki/Uncanny_valley). 2019-11-26
|
||||
> - Consumer technology as commercial surveillance. Alexa, Google, and Apple know too much about you and use it to sell adjacent services.
|
||||
|
||||
## Paper
|
||||
|
||||
* [IoT Swarms + SSI in constrained networks](https://docs.google.com/presentation/d/15ix2vzR_Dq9xcs-8OY0qBjapy9dpY-WdRKph9SiEY-0/edit?usp=sharing) [source](https://iiw.idcommons.net/12E/_IoT_Swarms_+_SSI_in_constrained_networks) - [paper](https://arxiv.org/abs/2107.10232) Geovane Fedrecheski, Laisa C. P. Costa, Samira Afzal, Jan M. Rabaey, Roseli D. Lopes, Marcelo K. Zuffo
|
||||
> One of the challenges identified by this last paper is the overhead of using SSI, which poses a challenge for adoption on constrained IoT networks. For example, while the Long Range (LoRa) communication, often used in IoT systems, only allows payloads of up to 240 bytes, a single DID Document typically occupies 500 bytes or more. Similarly, messages using DIDComm tend to use at least 1 kilobyte, which prevents its use on constrained networks.<br>Figure 1. Binary versions of DIDComm and DID Documents are needed to allow transmission in LoRa networks. The payload, in blue, is a DID Document. The overhead, in orange, is the protocol overhead due to the message signature.
|
||||
>
|
||||
> A low-overhead approach for self-sovereign identity in IoT We present a low-overhead mechanism for self-sovereign identification and communication of IoT agents in constrained networks. Our main contribution is to enable native use of Decentralized Identifiers (DIDs) and DID-based secure communication on constrained networks, whereas previous works either did not consider the issue or relied on proxy-based architectures. We propose a new extension to DIDs along with a more concise serialization method for DID metadata. Moreover, in order to reduce the security overhead over transmitted messages, we adopted a binary message envelope. We implemented these proposals within the context of Swarm Computing, an approach for decentralized IoT. Results showed that our proposal reduces the size of identity metadata in almost four times and security overhead up to five times. We observed that both techniques are required to enable operation on constrained networks.
|
||||
|
||||
* [Self-Sovereign Identity for IoT Devices](https://dltc.spbu.ru/images/articles/Kulabukhova2019_Chapter_Self-SovereignIdentityForIoTDe_compressed.pdf) 2019 Nataliia Kulabukhova, Andrei Ivashchenko, Iurii Tipikin, and Igor Minin
|
||||
> in our point of view, a lot of development groups are working in parallel on the similar topics, yet it is not clear what is going on inside. In this paper we will try to define the differences and discuss both pros and cons of using such commonly known technologies as Sovrin based upon the Hyperledger Indy technology, Civic, Jolocom, uPort and some others. Besides, we’ll tackle the idea of using the SSI for inanimate object and how it can be constructed in this way.
|
||||
|
||||
## Government
|
||||
|
||||
* [SSI In IoT, The SOFIE Project](https://www.thedinglegroup.com/blog/2021/4/6/ssi-in-iot-the-sofie-project) The Dingle Group
|
||||
> For the 22nd Vienna Digital Identity Meetup* we hosted three of the lead researchers from the [EU H2020](https://ec.europa.eu/programmes/horizon2020/) funded The [SOFIE Project](https://www.sofie-iot.eu/). The SOFIE Project wrapped up at the end of last year a key part of this research focused on the the use of SSI concepts in three IoT sectors (energy, supply chain, and mixed reality gaming) targeting integrating SSI in without requiring changes to the existing IoT systems.
|
||||
|
||||
|
||||
@ -1,61 +0,0 @@
|
||||
---
|
||||
published: false
|
||||
---
|
||||
* [Credential-based login to a Pico-based application](https://iiw.idcommons.net/11P/_Credential-based_login_to_a_Pico-based_application) by Bruce Conrad
|
||||
> Verifiable credentials, authentication, picos, pico-based application
|
||||
>
|
||||
> The slides are at [https://bruceatbyu.com/s/HRDDSiiw32](https://bruceatbyu.com/s/HRDDSiiw32)
|
||||
|
||||
* [Announcing Pico Engine 1.0](https://www.windley.com/archives/2021/02/announcing_pico_engine_10.shtml) 2021-02 Phil Windley
|
||||
> In addition to the work on the engine itself, one of the primary workstreams at present is to complete Bruce Conrad's excellent work to use DIDs and DIDComm as the basis for inter-pico communication, called ACA-Pico (Aries Cloud Agent - Pico). [...] This work is important because it will replace the current subscriptions method of connecting heterarchies of picos with DIDComm. [...] because DIDComm is protocological, this will support protocol-based interactions between picos, including credential exchange.
|
||||
* [The Most Inventive Thing I've Done](https://www.windley.com/archives/2022/07/the_most_inventive_thing_ive_done.shtml) 2022-07 Phil Windley
|
||||
> every pico is serverless and cloud-native, presenting an API that can be fully customized by developers. Because they're persistent, picos support databaseless programming with intuitive data isolation. As an actor-model programming system, different picos can operate concurrently without the need for locks, making them a natural choice for easily building decentralized systems.
|
||||
|
||||
* [ACA-Pico working group](https://docs.google.com/document/d/12dWUFyL7u6OQkhnPObJOOlV-U2LDoHpF-ZQLj3hXbjA/edit)
|
||||
|
||||
* [Picolab/aries-cloudagent-pico](https://github.com/Picolab/aries-cloudagent-pico)
|
||||
* [Announcing Pico Engine 1.0](https://www.windley.com/archives/2021/02/announcing_pico_engine_10.shtml) Phil Windley 2021-02
|
||||
> In addition to the work on the engine itself, one of the primary workstreams at present is to complete Bruce Conrad's excellent work to use DIDs and DIDComm as the basis for inter-pico communication, called ACA-Pico (Aries Cloud Agent - Pico). [...] This work is important because it will replace the current subscriptions method of connecting heterarchies of picos with DIDComm. [...] because DIDComm is protocological, this will support protocol-based interactions between picos, including credential exchange.
|
||||
* [Introduction to Picos](https://iiw.idcommons.net/4C/_Introduction_to_Picos) by Phil Windley
|
||||
> IoT, digital twins, device shadows, Conflict-free replicated data type (CRDT), CSP over DIDcomm
|
||||
> * [https://picolabs.io](https://picolabs.io) Pico Labs
|
||||
> * [https://github.com/Picolab/](https://github.com/Picolab/) repos
|
||||
> * [https://picolabs.atlassian.net/wiki](https://picolabs.atlassian.net/wiki) documentation
|
||||
> * [http://stackoverflow.com/questions/tagged/krl](http://stackoverflow.com/questions/tagged/krl) programming Q&A
|
||||
|
||||
* [Announcing Pico Engine 1.0](https://www.windley.com/archives/2021/02/announcing_pico_engine_10.shtml) 2021-02 Phil Windley
|
||||
> Pico is short for “Persistent Compute Objects.”
|
||||
> Why Picos
|
||||
> - Persistent, personal, computational nodes → More individual autonomy
|
||||
> - Computational node for anything: person, place, organization, smart thing, dumb thing, concept, even a pothole
|
||||
> - Better, more scalable model for IoT → trillion node networks
|
||||
> - Picos support social things and trustworthy spaces
|
||||
> - Better sharing, more natural relationship-based interactions (borrow my truck, Fuse with two owners)
|
||||
> - Scales
|
||||
> - Substitutable hosting model → freedom of choice
|
||||
> - pico mesh
|
||||
> [...]
|
||||
> What are Picos?
|
||||
> - “Pico” is a neologism for persistent compute objects.
|
||||
> - Persistence is a core feature of how picos work.
|
||||
> - Picos exhibit persistence in three ways:
|
||||
> - Persistent identity—Picos exist, with a single identity, continuously from the moment of their creation until they are destroyed.
|
||||
> - Persistent state—Picos have state that programs running in the pico can see and alter.
|
||||
> - Persistent availability—Picos are always on and ready to process queries and events.
|
||||
|
||||
Pico Engine 1.0 released in January
|
||||
* [Persistence, Programming, and Picos](https://www.windley.com/archives/2021/02/persistence_programming_and_picos.shtml) Phil Windley 2021-02
|
||||
> Picos show that image-based development can be done in a manner consistent with the best practices we use today without losing the important benefits it brings.
|
||||
>
|
||||
> The project name, PICOS, is an abbreviation of “Privacy and Identity Management for Community Services”. The objective of the project is to advance the state of the art in technologies that provide privacy-enhanced identity and trust management features within complex community-supporting services that are built on Next Generation Networks and delivered by multiple communication service providers. The approach taken by the project is to research, develop, build trial and evaluate an open, privacy-respecting, trust-enabling identity management platform that supports the provision of community services by mobile communication service providers.
|
||||
>
|
||||
> Learn more about the [motivation](http://www.picos-project.eu/Motivation.181.0.html), the [objectives](http://www.picos-project.eu/Objectives.182.0.html), [tasks](http://www.picos-project.eu/Tasks.183.0.html) and [achievements](http://www.picos-project.eu/Achievements.190.0.html) of PICOS, and get to know the PICOS exemplary [communities](http://www.picos-project.eu/Communities.184.0.html).
|
||||
* [Announcing Pico Engine 1.0](https://www.windley.com/archives/2021/02/announcing_pico_engine_10.shtml) 2021-02 Phil Windley
|
||||
> I'm excited to announce a new, stable, production-ready pico engine. The latest release of the Pico Engine (1.X) provides a more modular design that better supports future enhancements and allows picos to be less dependent on a specific engine for operation.
|
||||
|
||||
* [Building Decentralized Applications with Pico Networks](https://www.windley.com/archives/2021/02/building_decentralized_applications_with_pico_networks.shtml) 2021-02 Phil Windley
|
||||
|
||||
|
||||
* [Ten Reasons to Use Picos for Your Next Decentralized Programming Project](https://www.windley.com/archives/2021/07/ten_reasons_to_use_picos_for_your_next_decentralized_programming_project.shtml) 2021-07
|
||||
> Summary: Picos are a programming model for building decentralized applications that provide significant benefits in the form of abstractions that reduce programmer effort. Here are ten eleven reasons you should use picos for your next decentralized application. Temperature Sensor Network Built from Picos I didn't start out to write a programming language that naturally supports
|
||||
|
||||
@ -5,71 +5,58 @@ published: false
|
||||
# Travel
|
||||
|
||||
* [IDnow joins Accelerate@IATA to shape the future of seamless air travel](https://www.idnow.io/pr/idnow-joins-accelerateiata/) IDnow
|
||||
|
||||
The goal of IATA One ID is to set industry standards that further streamline the passenger journey with digitalization of admissibility and a contactless process through secure biometric enabled identification.
|
||||
|
||||
> The goal of IATA One ID is to set industry standards that further streamline the passenger journey with digitalization of admissibility and a contactless process through secure biometric enabled identification.
|
||||
|
||||
* [Is the biggest tech change for travel since the internet and mobile the shift to self-sovereign identity tech?](https://centreforaviation.com/analysis/video/is-the-biggest-tech-change-for-travel-since-the-internet-and-mobile-the-shift-to-self-sovereign-identity-tech-1594) CAPA TV
|
||||
|
||||
- What are some of the benefits of this new wave, such as reduced cybersecurity risk and enhanced travel experiences/personalisation?
|
||||
- Will this affect the way travel is distributed and paid for change?
|
||||
- What can players in the established travel eco-system expect?
|
||||
- When will we see this come about – where will we be by 2030?
|
||||
> - What are some of the benefits of this new wave, such as reduced cybersecurity risk and enhanced travel experiences/personalisation?
|
||||
> - Will this affect the way travel is distributed and paid for change?
|
||||
> - What can players in the established travel eco-system expect?
|
||||
> - When will we see this come about – where will we be by 2030?
|
||||
* [Q&A: The Potential of Decentralized ID in Travel](https://www.webintravel.com/qa-the-potential-of-decentralized-digital-id-in-travel/) WebInTravel
|
||||
> Since February he has also been the informal chair of the [Hospitality and Travel Special Interest Group](https://www.notion.so/dif/HOSPITALITY-TRAVEL-SIG-242105321e1747f8bce776bf634a55b3), a subset within the Decentralized Identity Foundation, an organization creating technical specifications and reference implementations for decentralized identity and working with industries for commercial applications of such technologies.
|
||||
* [SOUNDING OFF: A MAJOR - AND OVERDUE - POWER SHIFT IS COMING TO TRAVEL](https://www.phocuswire.com/sounding-off-144-ssi-power-shift-in-travel) Phocuswire
|
||||
> When this comes to fruition – and not if, but when – it will be a transformative change, shifting power from travel suppliers to travelers themselves and giving travelers more choice, better personalization, lower friction and more security.
|
||||
|
||||
When this comes to fruition – and not if, but when – it will be a transformative change, shifting power from travel suppliers to travelers themselves and giving travelers more choice, better personalization, lower friction and more security.
|
||||
* [Businesses’ desire to store less digital identity data stokes travel’s SSI brushfire](https://www.biometricupdate.com/202201/businesses-desire-to-store-less-digital-identity-data-stokes-travels-ssi-brushfire) 2022-01 BiometricUpdate
|
||||
> The potential use cases for self-sovereign identity to transform the travel industry are almost limitless, particularly with the impending arrival of [decentralized identifier communications](https://decentralized-id.com/organizations/decentralized-identity-foundation/wg/did-comm/), also known as DIDComm, attendees of a [PhocusWire](https://www.phocuswire.com/how-ssi-eliminates-friction-adds-control-for-travelers) roundtable discussion on the role of SSI in the future of identity and travel at the Phocuswright Conference 2021 heard from an panel of digital identity experts.
|
||||
|
||||
* [Businesses’ desire to store less digital identity data stokes travel’s SSI brushfire](https://www.biometricupdate.com/202201/businesses-desire-to-store-less-digital-identity-data-stokes-travels-ssi-brushfire) BiometricUpdate
|
||||
|
||||
The potential use cases for self-sovereign identity to transform the travel industry are almost limitless, particularly with the impending arrival of [decentralized identifier communications](https://decentralized-id.com/organizations/decentralized-identity-foundation/wg/did-comm/), also known as DIDComm, attendees of a [PhocusWire](https://www.phocuswire.com/how-ssi-eliminates-friction-adds-control-for-travelers) roundtable discussion on the role of SSI in the future of identity and travel at the Phocuswright Conference 2021 heard from an panel of digital identity experts.
|
||||
|
||||
* [Airports continue to deploy biometrics as SSI ‘big wave’ approaches](https://www.biometricupdate.com/202110/airports-continue-to-deploy-biometrics-as-ssi-big-wave-approaches) Biometric Update
|
||||
|
||||
The conflation of biometrics and SSI is somewhat disturbing.
|
||||
|
||||
TravelScrum Co-founder and Chairman Gene Quinn described self-sovereign ID (SSI) as “a big wave of change that’s coming,” and advised that organizations can “ride this wave by swimming at it, greeting it, and rolling gently over it as it heads to shore, or you can be caught in the shore-break and have it consume you later.”
|
||||
* [Airports continue to deploy biometrics as SSI ‘big wave’ approaches](https://www.biometricupdate.com/202110/airports-continue-to-deploy-biometrics-as-ssi-big-wave-approaches) 2021-10 Biometric Update
|
||||
> The conflation of biometrics and SSI is somewhat disturbing.
|
||||
>
|
||||
> TravelScrum Co-founder and Chairman Gene Quinn described self-sovereign ID (SSI) as “a big wave of change that’s coming,” and advised that organizations can “ride this wave by swimming at it, greeting it, and rolling gently over it as it heads to shore, or you can be caught in the shore-break and have it consume you later.”
|
||||
|
||||
* [Making travelling more seamless and relaxed](https://www.idnow.io/blog/how-digital-identity-improves-passenger-journey/) IDNow
|
||||
> Until now, we relied on physical id document such as ID cards [driving licenses to identify](https://www.idnow.io/mobility/driver-license-verification/) ourselves in the real world as well as online. Digital attributes and credentials were solely used online. Digital identity wallets, like the [IDnow Wallet](https://www.idnow.io/products/identity-wallet/), are about to change that, as they are simultaneously addressing our digital and real-world requirements by bringing physical and digital credentials together.
|
||||
|
||||
Until now, we relied on physical id document such as ID cards [driving licenses to identify](https://www.idnow.io/mobility/driver-license-verification/) ourselves in the real world as well as online. Digital attributes and credentials were solely used online. Digital identity wallets, like the [IDnow Wallet](https://www.idnow.io/products/identity-wallet/), are about to change that, as they are simultaneously addressing our digital and real-world requirements by bringing physical and digital credentials together.
|
||||
|
||||
* [Op Ed: Sam Hilgendorf On The Role Of Self-Sovereign Identification In Travel](https://www.thecompanydime.com/sam-hilgendorf-self-sovereign-identification/)
|
||||
* [Op Ed: Sam Hilgendorf On The Role Of Self-Sovereign Identification In Travel](https://www.thecompanydime.com/sam-hilgendorf-self-sovereign-identification/) The Company Dime
|
||||
* [How DID and SSI will Transform the Travel Experience Market](https://www.phocuswire.com/how-did-ssi-will-transform-travel-experience-market) Phocuswire
|
||||
|
||||
Over time the evolution of DID/SSI is likely to be a travel industry game-changer, enabling travelers to manage their own personal information to maximize personal economic effect and protect personal privacy.
|
||||
|
||||
The DID/SSI effort is already gaining a foothold in the banking and medical industries. Like travel, these are sectors that need to engage with consumers of all types en masse while requiring proof of identity prior to the certified exchange of digital documents.
|
||||
|
||||
> Over time the evolution of DID/SSI is likely to be a travel industry game-changer, enabling travelers to manage their own personal information to maximize personal economic effect and protect personal privacy.
|
||||
>
|
||||
> The DID/SSI effort is already gaining a foothold in the banking and medical industries. Like travel, these are sectors that need to engage with consumers of all types en masse while requiring proof of identity prior to the certified exchange of digital documents.
|
||||
|
||||
* [WHY THE TRAVEL INDUSTRY SHOULD CARE ABOUT SSI AND DID](https://www.phocuswire.com/why-travel-should-care-about-self-sovereign-decentralized-id) PhocusWire
|
||||
|
||||
As chair of the [Hospitality and Travel Special Interest Group](https://lists.identity.foundation/g/hospitalityandtravel) within the Decentralized Identity Foundation, Price is one of the leading voices on how DID and SSI will impact all sectors of travel.
|
||||
|
||||
At [Phocuswright Europe](https://www.phocuswrighteurope.com/), [Nick] Price explains how this technology – and the trusted, permissioned, secure communication it enables - will change the way suppliers and travelers interact and eliminate impediments that exist today.
|
||||
> As chair of the [Hospitality and Travel Special Interest Group](https://lists.identity.foundation/g/hospitalityandtravel) within the Decentralized Identity Foundation, Price is one of the leading voices on how DID and SSI will impact all sectors of travel.
|
||||
>
|
||||
> At [Phocuswright Europe](https://www.phocuswrighteurope.com/), [Nick] Price explains how this technology – and the trusted, permissioned, secure communication it enables - will change the way suppliers and travelers interact and eliminate impediments that exist today.
|
||||
|
||||
* [Traveller ID Ecosystem | ProofSpace x RateTiger Integration](https://www.youtube.com/watch?v=ExHEUpl9lKo) ProofSpace
|
||||
|
||||
Guests can reclaim, re-use and protect their personal data, the "Traveller ID", within the ecosystem of participating hotels.
|
||||
|
||||
The Traveller ID and other credentials in this solution are Atala PRISM Verifiable Credentials on Cardano blockchain - a global first for hospitality.
|
||||
> Guests can reclaim, re-use and protect their personal data, the "Traveller ID", within the ecosystem of participating hotels.
|
||||
>
|
||||
> The Traveller ID and other credentials in this solution are Atala PRISM Verifiable Credentials on Cardano blockchain - a global first for hospitality.
|
||||
|
||||
* [TSA Seeks Contractor for Upgraded Passenger Identification System](https://findbiometrics.com/tsa-seeks-contractor-for-upgraded-passenger-identification-system-508302/) FindBiometrics
|
||||
> Essentially, the TSA wants a CAT2 system that confirms and displays passenger information, including flight reservation information and pre-screening status, to TSA operators, and that uses facial recognition to match travelers to their photo ID.
|
||||
|
||||
Essentially, the TSA wants a CAT2 system that confirms and displays passenger information, including flight reservation information and pre-screening status, to TSA operators, and that uses facial recognition to match travelers to their photo ID.
|
||||
|
||||
|
||||
|
||||
* [You’ll soon be able to use your iPhone as ID at the airport: Apple Wallet is also getting support for hotel keys](https://www.theverge.com/2021/6/7/22522864/apple-wallet-iphone-airport-ids-hotel-key-card-ios-15-wwdc)
|
||||
|
||||
Apple has announced a forthcoming update to its Wallet app that will allow you to use your iPhone as digital identification in select US airports. The company showed how you’ll be able to scan your driver’s license or state ID in participating US states, which will then be encrypted and stored in the iPhone’s secure enclave. The company says it’s working with the TSA to enable the iPhone to be used as identification at airport security checkpoints.
|
||||
* [World's Airports And Leading Airlines Join CommonTrust Network And Begin Roll-out Of CommonPass](https://www.prnewswire.com/news-releases/worlds-airports-and-leading-airlines-join-commontrust-network-and-begin-roll-out-of-commonpass-in-december-in-support-of-safer-border-reopening-301179752.html)
|
||||
* [You’ll soon be able to use your iPhone as ID at the airport: Apple Wallet is also getting support for hotel keys](https://www.theverge.com/2021/6/7/22522864/apple-wallet-iphone-airport-ids-hotel-key-card-ios-15-wwdc) 2021-06-07 The Verge
|
||||
> Apple has announced a forthcoming update to its Wallet app that will allow you to use your iPhone as digital identification in select US airports. The company showed how you’ll be able to scan your driver’s license or state ID in participating US states, which will then be encrypted and stored in the iPhone’s secure enclave. The company says it’s working with the TSA to enable the iPhone to be used as identification at airport security checkpoints.
|
||||
* [World's Airports And Leading Airlines Join CommonTrust Network And Begin Roll-out Of CommonPass](https://www.prnewswire.com/news-releases/worlds-airports-and-leading-airlines-join-commontrust-network-and-begin-roll-out-of-commonpass-in-december-in-support-of-safer-border-reopening-301179752.html) PRNewswire
|
||||
> The CommonTrust Network is enabled by a global network of labs, vaccine distributors, and health care providers that agree to provide individuals with digital access to their own health information using open, globally-interoperable standards (e.g. HL7 FHIR, W3C verifiable credentials). The network includes hundreds of health systems covering thousands of locations in the United States and a growing network of labs and health care providers around the world.
|
||||
* [IATA unveils key design elements of travel pass](https://japantoday.com/category/features/travel/iata-unveils-key-design-elements-of-travel-pass)
|
||||
* [IATA unveils key design elements of travel pass](https://japantoday.com/category/features/travel/iata-unveils-key-design-elements-of-travel-pass) Japan Today
|
||||
> The IATA Travel Pass three critical design elements:
|
||||
>
|
||||
> - The IATA Travel Pass stores encrypted data including verified test or vaccination results on the mobile device of the traveler. The traveler controls what information is shared from their phone with airlines and authorities. No central database or data repository is storing the information. By keeping travelers 100% in control of their information, the highest standards for data privacy are ensured. IATA Travel Pass is also built on the highest standards of data protection laws, including General Data Protection Regulation (EU GDPR).
|
||||
> - Global standards recognized by governments to ensure verified identity and test/vaccine information.
|
||||
> - Convenience and biosafety will be enhanced with integration into contactless travel processes. The ICAO CART recommendations for biosafety include the use of contactless travel processes to reduce the risk of virus transmission when documents need to be exchanged in the travel process.
|
||||
|
||||
The IATA Travel Pass three critical design elements:
|
||||
|
||||
- The IATA Travel Pass stores encrypted data including verified test or vaccination results on the mobile device of the traveler. The traveler controls what information is shared from their phone with airlines and authorities. No central database or data repository is storing the information. By keeping travelers 100% in control of their information, the highest standards for data privacy are ensured. IATA Travel Pass is also built on the highest standards of data protection laws, including General Data Protection Regulation (EU GDPR).
|
||||
- Global standards recognized by governments to ensure verified identity and test/vaccine information.
|
||||
- Convenience and biosafety will be enhanced with integration into contactless travel processes. The ICAO CART recommendations for biosafety include the use of contactless travel processes to reduce the risk of virus transmission when documents need to be exchanged in the travel process.
|
||||
* [Drone Pilot Credentialing for Air Safety](https://www.youtube.com/watch?v=GqMsaI3P51o) TOIP
|
||||
> Discussed the approach and the implementation challenges of drone pilot credentialing for air safety using verifiable credentials at the July 21, 2022 Ecosystem Foundry Working Group of the Trust Over IP Foundation.
|
||||
|
||||
@ -17,13 +17,13 @@ published: false
|
||||
> Ajay is an Uber driver in San Francisco. He wants to try various temporary jobs while he’s studying but joining Lyft, Postmates and other platforms requires going through a long and tedious background verification and car certification process over and over again.
|
||||
* [Reimagining Customer Loyalty Programs With Verifiable Credentials: A Pravici Case Study](https://www.evernym.com/blog/customer-loyalty-verifiable-credentials/) Evernym
|
||||
> [Pravici](https://pravici.com/), an Evernym customer and startup based out of Chandler, Arizona, is looking to flip the equation. Their solution, Tokenized Loyalty Points (TLP), uses verifiable credential technology to give individual consumers control over their data, while empowering them to direct how their favorite brands can use this data for loyalty and other campaigns.
|
||||
* [26 Suggested Use Cases of Verifiable Credentials (With Some Real-World Examples)](https://academy.affinidi.com/25-real-world-use-cases-of-verifiable-credentials-4657c9cbc5e)
|
||||
* [26 Suggested Use Cases of Verifiable Credentials (With Some Real-World Examples)](https://academy.affinidi.com/25-real-world-use-cases-of-verifiable-credentials-4657c9cbc5e) Affinidi
|
||||
> we hope that business leaders, entrepreneurs, and developers will use this article as a guide to create some breakthrough solutions that will benefit the society at large.
|
||||
|
||||
## Supply Chain
|
||||
* [Trusted Supply Chain: end-to-end compliance in multi-tier supply chain](https://evan.network/use-cases/trusted-supply-chain/) Evan Network
|
||||
> In the real estate industry, TRUST&TRACE can be used by companies to obtain required compliance information from a network of participating companies. In this way, all property data is collected step by step: from building construction and leasing to sale and demolition.
|
||||
* [SAP Completes Pharmaceutical Industry Pilot to Improve Supply Chain Authenticity](https://news.sap.com/2021/03/pharmaceutical-supply-chain-industry-pilot/)
|
||||
* [SAP Completes Pharmaceutical Industry Pilot to Improve Supply Chain Authenticity](https://news.sap.com/2021/03/pharmaceutical-supply-chain-industry-pilot/) 2021-03 SAP
|
||||
> today announced the completion of an industry-wide pilot utilizing self-sovereign identity (SSI) credentials to establish trust in the pharmaceutical supply chain for indirect trade relationships.
|
||||
* [The missing link: digitizing supply chains with portable data](https://medium.com/mavennet/the-missing-link-digitizing-supply-chains-with-portable-data-583b66acc9bc) Mavnet
|
||||
> The traceability vocabulary bridges the gap between existing record-keeping systems and the verifiable exchange of supply chain information across organizations envisioned by proponents of these data portability technologies.
|
||||
@ -31,7 +31,7 @@ published: false
|
||||
> The digital and physical world are merging more than ever before. As the supply chain becomes more ‘phygital,’ innovative ways of sharing data – like using verifiable credentials – are helping to build more trust with data along the supply chain. Join us as we chat with Senior VP of Innovation & Partnerships at GS1 US, Melanie Nuce, as we explore what’s around the corner and how standards play
|
||||
* [How to Prevent Supply Chain Fraud With Blockchain](https://www.dock.io/post/supply-chain-fraud-blockchain) Dock
|
||||
> The global [supply chain management market size](https://www.prnewswire.com/news-releases/supply-chain-management-scm-market-size-worth--19-3-billion-globally-by-2028-at-9-02--cagr-verified-market-research-301540702.html) was valued at USD 10.1 Billion in 2020 and is projected to reach USD 19.3 Billion by 2028. Supply chain is the path for any product such as food, clothes, or appliances to go from where it was a produced, to distributors, procurement officers (quality inspections), and the market.
|
||||
* [SAP Pharma Solution Supports Supply Chain Compliance](https://insidesap.com.au/sap-pharma-solution-supports-supply-chain-compliance/)
|
||||
* [SAP Pharma Solution Supports Supply Chain Compliance](https://insidesap.com.au/sap-pharma-solution-supports-supply-chain-compliance/) SAP
|
||||
> SAP has chosen an open, interoperable technology to validate all stakeholders in the pharma supply chain in order to provide customers with the best solution for compliance under the U.S. Drug Supply Chain Security Act (DSCSA) requirements. The DSCSA also limits stakeholders’ interactions to ATPs.
|
||||
|
||||
## Personal Data
|
||||
@ -42,56 +42,24 @@ published: false
|
||||
|
||||
## Banking
|
||||
* [Impacts from a new reality drive the need for an enhanced digital identity framework](https://bankautomationnews.com/allposts/risk-security/impacts-from-a-new-reality-drive-the-need-for-an-enhanced-digital-identity-framework/) Bank Automation News
|
||||
|
||||
While US-based entities are adhering to an enhanced regulatory framework, these mandates are particularly applicable in Europe, where there is necessary compliance with enacted standards (such as the General Data Protection Regulation—commonly known as GDPR—and the Payment Service Providers Directive 2—referred to as PSD2. A clear need for a true and persistent digital identity as a solution to the ancillary—and sometimes unforeseen—challenges that have arisen.
|
||||
|
||||
> While US-based entities are adhering to an enhanced regulatory framework, these mandates are particularly applicable in Europe, where there is necessary compliance with enacted standards (such as the General Data Protection Regulation—commonly known as GDPR—and the Payment Service Providers Directive 2—referred to as PSD2. A clear need for a true and persistent digital identity as a solution to the ancillary—and sometimes unforeseen—challenges that have arisen.
|
||||
* [Banking’s identity problem](https://www.globalbankingandfinance.com/bankings-identity-problem/) Global Banking and Finance
|
||||
> Banks have sought to overcome some of these challenges with the use of biometrics such as facial recognition and fingerprints. These are now more commonly used to login to, or unlock devices, and increase usability, but still leave the challenge of proving the authenticity of a document wide open to abuse.
|
||||
- [New Bank Account Use Case](https://www.youtube.com/watch?v=YRLu4U4hSZ8)
|
||||
|
||||
|
||||
## Indicio
|
||||
* [Identity Blockchains and Energy Consumption](https://indicio.tech/identity-blockchains-and-energy-consumption/) Indicio
|
||||
A decentralized network using a blockchain-based distributed ledger means you can use [Peer DIDs](https://identity.foundation/peer-did-method-spec/) to move most “transactions” and their cryptographic proofing off ledger. This means that for those peer-to-peer interactions, identity blockchains don’t need to do any ledger transactions at all.
|
||||
|
||||
|
||||
* [How to Prevent Fraud using #MARKs](https://dhiway.com/prevent-credential-fraud/) DHIWay
|
||||
|
||||
Credential fraud has, unfortunately, become commonplace in today’s instant electronic age. Especially problematic in [higher education](https://dhiway.com/hashmarks-in-the-education-sector/), credential fraud has spiralled into a multi-billion-dollar industry
|
||||
|
||||
## business registry
|
||||
* [Is the Self-Sovereign digital identity the future digital business registry?](https://blogs.worldbank.org/psd/self-sovereign-digital-identity-future-digital-business-registry) GORAN VRANIC, ANDREJA MARUSIC; WorldBank
|
||||
|
||||
This rapid digitalization of the private sector exposed a challenge in the business registration paradigm. To use private digital platforms for e-Logistics or e-Commerce, SMEs have to register and confirm their identity with these platforms, despite already being identified in the government business registry.
|
||||
|
||||
|
||||
## Fraud
|
||||
|
||||
* [Apartment rentals and fraud: Discover technology that will ensure trusted content](https://medium.com/@michelplante/apartment-rentals-and-fraud-cf2ebc572890)
|
||||
|
||||
At the root of the problem is the fact that uniquely identifying a person is hard to do and that people can create fake IDs for themselves quite easily.
|
||||
> Credential fraud has, unfortunately, become commonplace in today’s instant electronic age. Especially problematic in [higher education](https://dhiway.com/hashmarks-in-the-education-sector/), credential fraud has spiralled into a multi-billion-dollar industry
|
||||
|
||||
## Security
|
||||
* [Digital IDs under attack: How to tackle the threat?](https://www.helpnetsecurity.com/2022/01/27/ssi-face-presentation-attacks/) 2022-01-27
|
||||
|
||||
- photo attacks based on the presentation of facial evidence of an image of a face printed or displayed via a device’s screen.
|
||||
- video of user replay attack usually consisting of placing the screen of the attacker’s device in front of the camera.
|
||||
- 3D mask attacks where 3D masks are crafted to reproduce the real traits of a human face and even include eyes holes to fool the liveliness detection based on eye gaze, blinking and motion.
|
||||
- deepfake attacks make use of leveraging software capable to create a synthetic video or image realistically representing someone else. Attackers are suspected to have access to a wide dataset containing images or a video of their target.
|
||||
* [Digital IDs under attack: How to tackle the threat?](https://www.helpnetsecurity.com/2022/01/27/ssi-face-presentation-attacks/) 2022-01-27 HelpnetSecurity
|
||||
> - photo attacks based on the presentation of facial evidence of an image of a face printed or displayed via a device’s screen.
|
||||
> - video of user replay attack usually consisting of placing the screen of the attacker’s device in front of the camera.
|
||||
> - 3D mask attacks where 3D masks are crafted to reproduce the real traits of a human face and even include eyes holes to fool the liveliness detection based on eye gaze, blinking and motion.
|
||||
> - deepfake attacks make use of leveraging software capable to create a synthetic video or image realistically representing someone else. Attackers are suspected to have access to a wide dataset containing images or a video of their target.
|
||||
|
||||
## Hiring \ Resume
|
||||
* [Trusted Career Credentials](https://www.linkedin.com/pulse/trusted-career-credentials-dr-gordon-jones/) Dr Gordon Jones
|
||||
|
||||
Today, even in this digital world that has expanded over the past two years, the job market still relies on self-reported attributes, records, resumes, and/or LinkedIn profiles, that individuals share with employers or recruiters as the source for applicants and employee data.
|
||||
|
||||
## Africa
|
||||
* [Digital identity can transform Africa’s economic landscape](https://www.globalbusinessoutlook.com/digital-identity-can-transform-africas-economic-landscape/)
|
||||
|
||||
In 2018, I was trying to open a bank account in my home town of Mutare, Zimbabwe, having just come back from the 1st world, I was under the impression it would take me at most 30 mins to an hour. I immediately realised I couldn’t provide most of the requirements such as my ‘Proof of Residence’ and many more. It turns out it took weeks and months for some to finish the entire process.
|
||||
|
||||
* [Self-sovereign digital identity is a game changer for African financial inclusion](https://it-online.co.za/2021/09/10/self-sovereign-digital-identity-is-a-game-changer-for-african-financial-inclusion/) ITOnline 2021-09-10
|
||||
|
||||
Much like cell phone technology and the internet, the true power of SSDI will only be unleashed when it is embedded across all sectors of society, from education and medical care to telecommunications and retail. And that will require all role players – government bodies, regulators, service providers, public and private agencies – to take up the SSDI baton and become part of the change.
|
||||
> Today, even in this digital world that has expanded over the past two years, the job market still relies on self-reported attributes, records, resumes, and/or LinkedIn profiles, that individuals share with employers or recruiters as the source for applicants and employee data.
|
||||
|
||||
### Smart Home
|
||||
|
||||
@ -108,37 +76,20 @@ Much like cell phone technology and the internet, the true power of SSDI will on
|
||||
|
||||
## Identos
|
||||
* [Groundwork laid for mass digital identity take up as use cases grow](https://www.biometricupdate.com/202108/groundwork-laid-for-mass-digital-identity-take-up-as-use-cases-grow) Biometric update
|
||||
|
||||
Identos is adding W3C (World Wide Web Consortium) verifiable credentials as a product feature for its digital ID solutions by the end of the year, announcing its position in the race to incorporate international standards for how digital credentials – from health records to degree certificates – are stored and verified.
|
||||
> Identos is adding W3C (World Wide Web Consortium) verifiable credentials as a product feature for its digital ID solutions by the end of the year, announcing its position in the race to incorporate international standards for how digital credentials – from health records to degree certificates – are stored and verified.
|
||||
|
||||
## Meeco
|
||||
* [Opening the domestic card rails to innovation](https://blog.meeco.me/opening-the-domestic-card-rails-to-innovation/) Meeco
|
||||
|
||||
Enabling Australian FinTechs a direct avenue to discuss how they partner and collaborate to access the eftpos payments network through the Committee resulted in recommendations that covered a number of central themes, including consultation and engagement, regulation, and technology and solutionsBen Tabell, eftpos Chief Information Officer and Committee Chair
|
||||
> Enabling Australian FinTechs a direct avenue to discuss how they partner and collaborate to access the eftpos payments network through the Committee resulted in recommendations that covered a number of central themes, including consultation and engagement, regulation, and technology and solutionsBen Tabell, eftpos Chief Information Officer and Committee Chair
|
||||
|
||||
## Gaming
|
||||
* [Self-Sovereign Identity for Online Gaming, VR, & AR – Crucible](https://identity-economy.de/self-sovereign-identity-for-online-gaming-vr-ar-crucible) Evernym (via identity-economy.de)
|
||||
|
||||
Crucible's CEO (Ryan Gill) and CTO (Toby Tremayne) for a discussion on what self-sovereign identity (SSI) and verifiable credentials mean for gaming and the greater online entertainment sector.
|
||||
> Crucible's CEO (Ryan Gill) and CTO (Toby Tremayne) for a discussion on what self-sovereign identity (SSI) and verifiable credentials mean for gaming and the greater online entertainment sector.
|
||||
|
||||
## Credit unions
|
||||
* [Building an SSI Ecosystem: MemberPass and Credit Unions](https://www.windley.com/archives/2021/06/building_an_ssi_ecosystem_memberpass_and_credit_unions.shtml)
|
||||
* [Building an SSI Ecosystem: MemberPass and Credit Unions](https://www.windley.com/archives/2021/06/building_an_ssi_ecosystem_memberpass_and_credit_unions.shtml) 2021/06 Phil Windley
|
||||
> Credit unions and their members face the threat of fraud on all sides. And credit unions employ lots of tools to fight it. But ultimately, the problem comes down to the member and credit union authenticating each other. The problem is that doing this securely annoys people.
|
||||
|
||||
Credit unions and their members face the threat of fraud on all sides. And credit unions employ lots of tools to fight it. But ultimately, the problem comes down to the member and credit union authenticating each other. The problem is that doing this securely annoys people.
|
||||
|
||||
|
||||
* [Evernym Selected as a 2021 Technology Pioneer by the World Economic Forum](https://www.evernym.com/blog/wef-technology-pioneer/)
|
||||
|
||||
The 2021 cohort of Tech Pioneers includes many future headline-makers at the forefront of their industries. These companies show great potential to not only shake up their industries but offer real solutions to global problems.
|
||||
|
||||
* [Introducing Veramo](https://medium.com/uport/introducing-veramo-5a960bf2a5fe)
|
||||
|
||||
In our last post we briefly presented Veramo and how it evolved from the [challenges faced with uPort’s libraries](https://medium.com/uport/veramo-uports-open-source-evolution-d85fa463db1f). In this next series of articles we will give Veramo a proper introduction and answer some of the basics: why it exists and what it does, followed by articles describing the architecture in more detail, and how to build applications using [Veramo](https://veramo.io).
|
||||
|
||||
## Auth0
|
||||
* [Verifiable Credentials with Auth0 and MATTR](https://auth0.com/blog/verifiable-credentials-with-auth0-and-mattr/)
|
||||
|
||||
How to issue Verifiable Credentials from Auth0 user data using MATTR's Auth0 Marketplace Integration
|
||||
|
||||
## Memberpass
|
||||
* [MemberPass Digital ID can help Reduce Expenses and Build Member Trust](https://www.memberpass.com/2021/06/memberpass-digital-id-can-help-reduce-expenses-and-build-member-trust/)
|
||||
@ -148,41 +99,28 @@ You can probably use the good news. It’s never been easy to run a credit union
|
||||
## E-Commerce
|
||||
|
||||
* [Self-Sovereign E-Commerce](https://iiw.idcommons.net/23J/_Self-Sovereign_E-Commerce) by Doc Searls
|
||||
|
||||
There is momentum here, and a need to start building out much of what was discussed.
|
||||
|
||||
Doc introduced the session with the slide deck [here](https://www.slideshare.net/dsearls/day3iiw-sesion), wearing his hat as a founding member of [Customer Commons](http://customercommons.org), the .org working on the Intention Byway discussed at earlier IIW sessions and described in [this blog](https://customercommons.org/2021/04/27/a-new-way/), posed later. 2021-04-27
|
||||
|
||||
His case is that the incumbent e-commece system hasn’t progressed past its dependence on the cookie, and perhaps never will; and that there is a need to stand up an alternate model, built on asynchronous pub-sub messaging and compute nodes that run apps that don’t have to come from the stores of Apple and Google.
|
||||
|
||||
First examples of target areas (where communities are already active) are food distribution in Michigan and real estate in Boston. Hadrian Zbarcea led the discussion of both, using slides from the deck above.
|
||||
> Doc introduced the session with the slide deck [here](https://www.slideshare.net/dsearls/day3iiw-sesion), wearing his hat as a founding member of [Customer Commons](http://customercommons.org), the .org working on the Intention Byway discussed at earlier IIW sessions and described in [this blog](https://customercommons.org/2021/04/27/a-new-way/), posed later. 2021-04-27
|
||||
>
|
||||
> His case is that the incumbent e-commece system hasn’t progressed past its dependence on the cookie, and perhaps never will; and that there is a need to stand up an alternate model, built on asynchronous pub-sub messaging and compute nodes that run apps that don’t have to come from the stores of Apple and Google.
|
||||
>
|
||||
> First examples of target areas (where communities are already active) are food distribution in Michigan and real estate in Boston. Hadrian Zbarcea led the discussion of both, using slides from the deck above.
|
||||
|
||||
### Career Creds
|
||||
* [Self sovereign career identity](https://diginomica.com/self-sovereign-career-identity-conversation-meg-bear-sap-successfactors) Diginomica with Meg Bear
|
||||
* [Self sovereign career identity](https://diginomica.com/self-sovereign-career-identity-conversation-meg-bear-sap-successfactors) Diginomica Meg Bear
|
||||
> The Velocity piece is a way for me as an individual to own my credentials, to say, these are the things that I know. And these are the things I've done. And if I can own that, I have a lot more interest in it. And I can use it in a lot more interesting ways. In the past, that might have just been something that I built as reputation within a company, I can now make that a more dynamic and portable reputation I can take with me anywhere.
|
||||
|
||||
## Velocity Network
|
||||
Having a look at [the Velocity Whitepaper](https://www.velocitynetwork.foundation/wp-content/uploads/2020/11/Velocity-Non-Technical-Whitepaper-091120-V1.15-Published.pdf) it does mention they are keeping an eye on the work developing in W3C and DIF.
|
||||
|
||||
## DHS
|
||||
- [DHS SVIP Plugfest #2: Limited Disclosure Scenario](https://www.youtube.com/watch?v=BBSX0ljiCPU)
|
||||
|
||||
## DOMI
|
||||
* [A brighter future for tenant/landlord relationships](https://domilabs.io/tenant-landlord-relationships/) Domi Labs
|
||||
|
||||
it’s hard to keep track since some call, some… email, and still others send you a message on WhatsApp.” Going through all of these disparate messages is its own fulltime job!
|
||||
|
||||
That’s why Domi locates all communication about a property in one place, making it easy for tenants and property managers to stay in touch.
|
||||
|
||||
> it’s hard to keep track since some call, some… email, and still others send you a message on WhatsApp.” Going through all of these disparate messages is its own fulltime job!
|
||||
>
|
||||
> That’s why Domi locates all communication about a property in one place, making it easy for tenants and property managers to stay in touch.
|
||||
|
||||
* [Blockchain and the Decentralised Workforce](https://workforcefuturist.substack.com/p/blockchain-and-the-decentralised-workforce) WorkforceFuturist
|
||||
|
||||
## Trade
|
||||
|
||||
* [Vincent Annunziato,](https://www.spreaker.com/user/13158652/ep8-cbp-vincent-annunziato) talks about his work with The Silicon Valley Innovation Program. He is the Director of Transformation & Innovation Division of the Customs and Border Patrol Office of Trade, talks about shaping blockchain technologies to make imports safer and more secure. CBP's current projects include tracking steel, oil, and natural gas imports from Canada.
|
||||
[Vincent Annunziato,](https://www.spreaker.com/user/13158652/ep8-cbp-vincent-annunziato) talks about his work with The Silicon Valley Innovation Program. He is the Director of Transformation & Innovation Division of the Customs and Border Patrol Office of Trade, talks about shaping blockchain technologies to make imports safer and more secure. CBP's current projects include tracking steel, oil, and natural gas imports from Canada.
|
||||
|
||||
* [What Is Self-Sovereign Identity Verification and How Is It Changing Background Screening?](https://www.corporatescreening.com/blog/what-is-self-sovereign-identity-verification-and-how-is-it-changing-background-screening)
|
||||
> A prime example is self-sovereign identity verification, one of the game-changing [background screening trends of 2021](https://www.corporatescreening.com/2021-trends-interactive-infographic). When combined with screening activities, self-sovereign identity solutions offer opportunities to obtain more accurate candidate background data and deliver it to employers faster.
|
||||
* [The Equifax Incident, And How SSI Could Have Prevented It](https://europechain.io/identity/equifax-incident-ssi-prevented-it/) Europechain
|
||||
> On March 8, 2017, Cisco staff found and reported a critical flaw in Apache Struts, an open-source framework that enables the creation of web-based Java applications. The vulnerability in question was identified as CVE-2017-5638. In short, Strut’s parser tool, Jakarta, could be manipulated to enable a malicious actor to upload files remotely to a server, and potentially run code on that compromised server.
|
||||
|
||||
@ -192,10 +130,8 @@ That’s why Domi locates all communication about a property in one place, makin
|
||||
> What kind of strategy will take you to being a next-generation utility company? For AEP Ohio, a large electric utility company based in Columbus, this challenge began with a comprehensive review of their entire ecosystem and which identified their key pain points for innovation.
|
||||
|
||||
|
||||
* [5 Promising Use Cases for Verifiable Credentials](https://hackernoon.com/5-promising-use-cases-for-verifiable-credentials-tu1y348k) - Hackernoon
|
||||
> verifiable credentials promise to appear in our daily lives in the not-too-distant future.
|
||||
>
|
||||
> In fact, several industries are already digging in. Here are some of the most visible and promising use cases.
|
||||
* [5 Promising Use Cases for Verifiable Credentials](https://hackernoon.com/5-promising-use-cases-for-verifiable-credentials-tu1y348k) Hackernoon
|
||||
> several industries are already digging in. Here are some of the most visible and promising use cases.
|
||||
* [Are we doing enough to align our work with Zero Trust Architecture?](https://lists.w3.org/Archives/Public/public-did-wg/2021Jan/0000.html) Adrian Gropper on Public DID-WG mailing list
|
||||
> [https://www.nytimes.com/2021/01/02/us/politics/russian-hacking-government.html](https://www.nytimes.com/2021/01/02/us/politics/russian-hacking-government.html) 2021-01-02
|
||||
> What would be a good way for our SSI communities to advance zero trust architecture through more effective accountability and audit?
|
||||
@ -212,6 +148,7 @@ That’s why Domi locates all communication about a property in one place, makin
|
||||
> The most important message from the SolarWinds hack and much of the ransomware havoc is that our systems are not set up for individual accountability or independent audit.
|
||||
>
|
||||
> The VC and ZCAPs perspective is inadequate. As an SSI community we need to address the separation of concerns between authentication, authorization, and audit as equally important and needing a harmonized best-practice perspective. Standardized EDVs are table stakes but not terribly relevant to the protocols that link authentication, authorization, and audit. Confidential Storage should be adopting the protocols that connect authentication, authorization, and audit rather than introducing protocols narrowly scoped to the narrow and obvious role of encryption at rest.
|
||||
>
|
||||
> I've put together a few slides in an attempt to clarify the relationship between non-repudiable accountability and audits (and EDVs).
|
||||
> [https://docs.google.com/presentation/d/1ksKal62ZiApX09Nejm4RSqHzHJbgwpu_l2Ho64_ePKU/edit#slide=id.p](https://docs.google.com/presentation/d/1ksKal62ZiApX09Nejm4RSqHzHJbgwpu_l2Ho64_ePKU/edit#slide=id.p)
|
||||
|
||||
@ -222,185 +159,85 @@ That’s why Domi locates all communication about a property in one place, makin
|
||||
> 3. Requesting Party (RQ) and their user agent (mobile wallet)
|
||||
> 4. Requesting Client (RC), by definition has data in the clear
|
||||
|
||||
* [Digital Identity Isn’t Only For People](https://www.forbes.com/sites/davidbirch/2020/12/22/digital-identity-isnt-only-for-people/) David Birch, Forbes 2020-12-22
|
||||
* [Digital Identity Isn’t Only For People](https://www.forbes.com/sites/davidbirch/2020/12/22/digital-identity-isnt-only-for-people/) 2020-12-22 David Birch, Forbes
|
||||
> fintechs and regtechs looking for opportunities in the digital identity space should cast their ideas net pretty wide. Digital identities are not only for people and the future desperately needs digital identities for pretty much everything to underpin recognition, relationships and reputation (the 3Rs of the online economy).
|
||||
|
||||
|
||||
* [Why self-sovereign identity will get adopted (and it’s not the reason you probably want)](https://www.tuesdaynight.org/2018/06/15/why-self-sovereign-identity-will-get-adopted-and-its-not-the-reason-you-probably-want/) Tuesday Night 2018-06-15
|
||||
|
||||
In the payment card world, there are clear guidelines on personal liability. $50 if you use credit and up to $500 for debit depending on when you report the issue. Based on that, different people choose to use different “systems.”
|
||||
|
||||
However, no such guidelines exist for the use of identity information (e.g. attributes.)
|
||||
|
||||
|
||||
* [Why self-sovereign identity will get adopted (and it’s not the reason you probably want)](https://www.tuesdaynight.org/2018/06/15/why-self-sovereign-identity-will-get-adopted-and-its-not-the-reason-you-probably-want/) 2018-06-15 Tuesday Night
|
||||
> In the payment card world, there are clear guidelines on personal liability. $50 if you use credit and up to $500 for debit depending on when you report the issue. Based on that, different people choose to use different “systems.”
|
||||
>
|
||||
> However, no such guidelines exist for the use of identity information (e.g. attributes.)
|
||||
|
||||
* [ID Verification Threats On the Horizon](https://stateofidentity.libsyn.com/id-verification-threats-on-the-horizon) Liminal Podcasts
|
||||
> Cognito's CEO Alain Meier joins the State of Identity host Cameron D’Ambrosi to dive into why industries beyond financial services are now in the market for identity verification. They also unpack the impact of synthetic identity fraud across verticals, and how platforms find the balance when building their onboarding processes.
|
||||
|
||||
Cognito's CEO Alain Meier joins the State of Identity host Cameron D’Ambrosi to dive into why industries beyond financial services are now in the market for identity verification. They also unpack the impact of synthetic identity fraud across verticals, and how platforms find the balance when building their onboarding processes.
|
||||
|
||||
* [Hackers Gaining Power of Subpoena Via Fake “Emergency Data Requests”](https://krebsonsecurity.com/2022/03/hackers-gaining-power-of-subpoena-via-fake-emergency-data-requests/)
|
||||
|
||||
and people asking questions about whether SSI could slove this use case - Yes.
|
||||
|
||||
If there was a trust framework for police departments and a DID registry for them - the police departments could issue VCs to their officers.
|
||||
|
||||
If you want to se how hard this was/would have been to achieve in earlier technology stacks take a look at [conceptual outlines](https://trustmark.gtri.gatech.edu/concept/) from this NSTIC (National Strategies for Trusted Identities in Cyberspace) developing a trust framework for law enforcement federations done by the Georgia Technology Reserach Institute and the [results/learnings.](https://trustmark.gtri.gatech.edu/insights/)
|
||||
|
||||
|
||||
* [Hackers Gaining Power of Subpoena Via Fake “Emergency Data Requests”](https://krebsonsecurity.com/2022/03/hackers-gaining-power-of-subpoena-via-fake-emergency-data-requests/) 2022-03
|
||||
> If there was a trust framework for police departments and a DID registry for them - the police departments could issue VCs to their officers.
|
||||
>
|
||||
> If you want to se how hard this was/would have been to achieve in earlier technology stacks take a look at [conceptual outlines](https://trustmark.gtri.gatech.edu/concept/) from this NSTIC (National Strategies for Trusted Identities in Cyberspace) developing a trust framework for law enforcement federations done by the Georgia Technology Reserach Institute and the [results/learnings.](https://trustmark.gtri.gatech.edu/insights/)
|
||||
|
||||
* [Trusted Timestamping Part 1: Scenarios](https://medium.com/finema/trusted-timestamping-part-1-scenarios-9bf4a7cc2364) Nunnaphat Songmanee, Finema
|
||||
|
||||
Evidentiary value is an essential component of important transactions. When a transaction is recorded in a printed document, one way to impart evidentiary value is by including date and time
|
||||
|
||||
> Evidentiary value is an essential component of important transactions. When a transaction is recorded in a printed document, one way to impart evidentiary value is by including date and time
|
||||
|
||||
* [Survey: How Do You Use Your Identity at Work?](https://findbiometrics.com/survey-how-do-you-use-your-identity-at-work/) FindBiometrics
|
||||
|
||||
The COVID-19 pandemic rapidly shifted the way we work, coinciding with digital transformation trends that depend on strong identity assurance. Hybrid workplaces are more common, as is completely remote work
|
||||
|
||||
|
||||
|
||||
[Dignified Identities for Cash assistance project](https://hiplatform.org/digid). The first phase was implemented by KRCS to meet the needs of the vulnerable populations without official IDs
|
||||
|
||||
* [Coinfirm Adds Close To 1 Million Tokens To AML Platform, Offering Full Coverage](https://www.coinfirm.com/blog/1-million-tokens-aml-crypto/)
|
||||
|
||||
LONDON, United Kingdom – In the largest update of protocol coverage in Coinfirm’s history, the firm has added support for 840,361 new tokens to the AML Platform, offering total digital asset coverage of 17 blockchains. Now, the company’s industry-recognized blockchain agnostic AML Platform supports ~846 thousand cryptocurrencies and tokens.
|
||||
|
||||
|
||||
* [AERGO Labs: Funding The Future](https://medium.com/aergo/aergo-labs-funding-the-future-4d195c79858c)
|
||||
|
||||
AERGO is proud to announce the launch of the AERGO Venture Fund: a fund dedicated to dApp development! “Start Together, Scale Together” is a fundamental ethos of the AERGO hybrid blockchain ecosystem.
|
||||
|
||||
* [@Steve_Lockstep · Apr 23](https://twitter.com/Steve_Lockstep/status/1517861150129795072)
|
||||
|
||||
I had a stab at why Cardspace failed, in “[Identities Evolve: Why Federated Identity is Easier Said than Done](https://papers.ssrn.com/sol3/papers.cfm?abstract_id=2163241)
|
||||
|
||||
Why does digital identity turn out to be such a hard problem? People are social animals with deep seated intuitions and conventions around identity, but exercising our identities online has been hugely problematic.
|
||||
> The COVID-19 pandemic rapidly shifted the way we work, coinciding with digital transformation trends that depend on strong identity assurance. Hybrid workplaces are more common, as is completely remote work
|
||||
|
||||
* [Sandeep Shukla · Professor, Computer Science and Engineering at Indian Institute of Technology, Kanpur](https://www.linkedin.com/feed/update/urn:li:ugcPost:6924705964537389056/) Linkedin
|
||||
|
||||
IGNOU (Indira Gandhi National Open University) had their convocation today and they issued more than 60000 degrees and certificates as Self-Sovereign Identity document (Cryptographically verifiable Credential) on [National Blockchain Project](https://www.linkedin.com/company/national-blockchain-project/) and [CRUBN](https://www.linkedin.com/company/crubn/)'s SSI blockchain.
|
||||
> IGNOU (Indira Gandhi National Open University) had their convocation today and they issued more than 60000 degrees and certificates as Self-Sovereign Identity document (Cryptographically verifiable Credential) on [National Blockchain Project](https://www.linkedin.com/company/national-blockchain-project/) and [CRUBN](https://www.linkedin.com/company/crubn/)'s SSI blockchain.
|
||||
* [Self-Sovereign Identity as a Service: Architecture in Practice](https://arxiv.org/pdf/2205.08314.pdf) Yepeng Ding, Hiroyuki Sato, University of Tokyo
|
||||
|
||||
We propose a practical architecture by elaborating the service concept, SSI, and DLT to implement SSIaaS platforms and SSI services. Besides, we present an architecture for constructing and customizing SSI services with a set of architectural patterns and provide corresponding evaluations. Furthermore, we demonstrate the feasibility of our proposed architecture in practice with Selfid, an SSIaaS platform based on our proposed architecture.
|
||||
|
||||
Ontario (a province in Canada) just had an election last week and Darrell thinks: [Digital ID Can Increase Voter Participation](https://www.continuumloop.com/digital-id-can-increase-voter-participation/)
|
||||
|
||||
I’m not an expert on the election process, and this is just my opinion. I’ve been lazy in past elections, and I’d be lying if I said I’ve voted in every one. As a citizen, I believe ease and accessibility have a lot to do with it.
|
||||
|
||||
* [January Walker US Congress UT04](https://twitter.com/UtahPolitician)
|
||||
|
||||
Solution: Election Integrity & Expanded Voter Access w/ blockchain voting & Self Sovereign Identity [https://tiktok.com/t/ZTdvvX1uy/](https://tiktok.com/t/ZTdvvX1uy/)
|
||||
|
||||
* [Can SSI fit within the GDPR?: a Conceptual Data Protection Analysis (Part I)](https://www.law.kuleuven.be/citip/blog/can-self-sovereign-identity-ssi-fit-within-the-gdpr-part-i/)
|
||||
|
||||
while SSI principles incorporate similar notions to the provisions and principles in the GDPR, closer analysis shows that they might have different meanings.
|
||||
> We propose a practical architecture by elaborating the service concept, SSI, and DLT to implement SSIaaS platforms and SSI services. Besides, we present an architecture for constructing and customizing SSI services with a set of architectural patterns and provide corresponding evaluations. Furthermore, we demonstrate the feasibility of our proposed architecture in practice with Selfid, an SSIaaS platform based on our proposed architecture.
|
||||
|
||||
* [@tmarkovski Jun 10](https://twitter.com/tmarkovski/status/1535240038803464195)
|
||||
> 1/ Can [QUIC](https://www.akamai.com/blog/news/the-next-generation-of-http) use DIDComm as a Handshake protocol instead TLS1.3? The spec provides enough abstraction for the session handling, and most crypto operations are the same. The main difference is the trust architecture and model: certificate chain vs DID Documents.
|
||||
|
||||
1/ Can [QUIC](https://www.akamai.com/blog/news/the-next-generation-of-http) use DIDComm as a Handshake protocol instead TLS1.3? The spec provides enough abstraction for the session handling, and most crypto operations are the same. The main difference is the trust architecture and model: certificate chain vs DID Documents.
|
||||
|
||||
|
||||
* [SSI Essentials: 35 use cases of decentralized identities that will make your life easier](https://gataca.io/blog/ssi-essentials-35-use-cases-of-decentralized-identities-that-will-make-your-life-easier)
|
||||
* [SSI Essentials: 35 use cases of decentralized identities that will make your life easier](https://gataca.io/blog/ssi-essentials-35-use-cases-of-decentralized-identities-that-will-make-your-life-easier) Gataca
|
||||
|
||||
* [The Importance of Verifiable Credentials to Training Providers](https://uploads-ssl.webflow.com/6269810a06ae9fafd52556a3/629f94235eabc454ea48c117_The%20Importance%20of%20Verifiable%20Credentials%20for%20Training%20Providers.pdf?__hstc=100632769.d32f75d38c42eaa77409051b21d73653.1655033322879.1655033322879.1655033322879.1&__hssc=100632769.1.1655033322879&__hsfp=2803731784) Credivera
|
||||
|
||||
Great report!
|
||||
|
||||
Digital badges or PDF credentials lack proof of being authentic and current, and can be easily reproduced or falsified, impacting both the individual and the reputation of the training provider.
|
||||
> Digital badges or PDF credentials lack proof of being authentic and current, and can be easily reproduced or falsified, impacting both the individual and the reputation of the training provider.
|
||||
|
||||
* [Transferable Accounts Putting Passengers at Risk](https://www.windley.com/archives/2022/06/transferable_accounts_putting_passengers_at_risk.shtml) Phil Windley
|
||||
|
||||
The non-transferability of verifiable credential is one of their super powers. This post examines how that super power can be used to reduce fraud and increase safety in a hired car platform.
|
||||
|
||||
- [SSI and FIDO2: Different approaches for a passwordless world](https://blog.avast.com/ssi-fido2)
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
> The non-transferability of verifiable credential is one of their super powers. This post examines how that super power can be used to reduce fraud and increase safety in a hired car platform.
|
||||
|
||||
* [How Self-Sovereign Identity Helps Your Enterprise](https://zaisan.io/self-sovereign-identity-enterprise/) Zaisan
|
||||
|
||||
- Identity is the sum of a lot of individual parts that, when pieced together, paint a comprehensive and multi-layered picture of who someone truly is
|
||||
- Zaisan’s my.D platform leverages blockchain technology to provide a [comprehensive digital identity management solution](https://myd.online/)
|
||||
- My.D enables a cost-effective and efficient management solution for an individual’s digital credentials
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
* [Drone Pilot Credentialing for Air Safety](https://www.youtube.com/watch?v=GqMsaI3P51o) TOIP
|
||||
|
||||
Discussed the approach and the implementation challenges of drone pilot credentialing for air safety using verifiable credentials at the July 21, 2022 Ecosystem Foundry Working Group of the Trust Over IP Foundation.
|
||||
|
||||
> - Identity is the sum of a lot of individual parts that, when pieced together, paint a comprehensive and multi-layered picture of who someone truly is
|
||||
> - Zaisan’s my.D platform leverages blockchain technology to provide a [comprehensive digital identity management solution](https://myd.online/)
|
||||
> - My.D enables a cost-effective and efficient management solution for an individual’s digital credentials
|
||||
|
||||
* [How Blockchain Technology and Self-Sovereign Identity Enables the New Normal of Remote Learning, Training and Working](https://www.linkedin.com/pulse/how-blockchain-technology-self-sovereign-identity-enables-hossain-) Md Sabbir Hossain
|
||||
|
||||
* [An autonomous reputation system](https://reb00ted.org/tech/20220810-autonomous-reputation-system/) reb00ted
|
||||
|
||||
we need to figure out how to give more power to “better” actors within a given community or context, and disempower or keep out the detractors and direct opponents. All without putting a centralized authority in place.
|
||||
|
||||
|
||||
* [It’s time for digital self-sovereign identity](https://gcn.com/emerging-tech/2022/08/its-time-digital-self-sovereign-identity/375285/) GCN
|
||||
> the implementation of granular security measures to protect that data creates trusted networks between governments and the citizens they serve. Everyone wins.
|
||||
> we need to figure out how to give more power to “better” actors within a given community or context, and disempower or keep out the detractors and direct opponents. All without putting a centralized authority in place.
|
||||
|
||||
## Energy Systems
|
||||
|
||||
* [Digital identities – building block for an automated energy system](https://www.smart-energy.com/digitalisation/digital-identities-building-block-for-an-automated-energy-system/) Smart Energy
|
||||
|
||||
New features include credential revocation and expiration, full support for role-authorised issuance, credential issuance based on email verification and asset administration as well as better alignment with the W3C’s Verifiable Credential Standards.
|
||||
> New features include credential revocation and expiration, full support for role-authorised issuance, credential issuance based on email verification and asset administration as well as better alignment with the W3C’s Verifiable Credential Standards.
|
||||
|
||||
|
||||
* [War Against the Robots – Pick your Side with SelfKey & Metaproof Platform](https://selfkey.org/war-against-the-robots-pick-your-side-with-selfkey-metaproof-platform/) SelfKey Foundation
|
||||
|
||||
Trying to ban or sideline bots is not a solution. The solution is to distinguish bots from humans so that humans can do human stuff and bots can do bot stuff.
|
||||
> Trying to ban or sideline bots is not a solution. The solution is to distinguish bots from humans so that humans can do human stuff and bots can do bot stuff.
|
||||
|
||||
|
||||
* [OpenEarth partners with BCGov to develop a digital trust marketplace for climate accounting](https://www.openearth.org/blog/openearth-partners-with-the-government-of-british-columbia-to-develop-a-digital-trust-marketplace-for-climate-accounting) OpenEarth Foundation
|
||||
|
||||
OpenEarth Foundation partnered with the Mines Digital Trust initiative to allow BC companies to also share their greenhouse gas (GHG) emissions credentials to the [OpenClimate](https://www.openearth.org/projects/openclimate) platform so that they can be integrated into BC’s subnational climate inventory and showcased to interested purchasers and civic society
|
||||
> OpenEarth Foundation partnered with the Mines Digital Trust initiative to allow BC companies to also share their greenhouse gas (GHG) emissions credentials to the [OpenClimate](https://www.openearth.org/projects/openclimate) platform so that they can be integrated into BC’s subnational climate inventory and showcased to interested purchasers and civic society
|
||||
|
||||
|
||||
* [Event tickets as verifiable credentials](https://lissi-id.medium.com/event-tickets-as-verifiable-credentials-31f4a10b28cc) Lissi
|
||||
> This article explains how verifiable credentials can be used to benefit event organizers and visitors alike based on a practical usage of the Lissi team.
|
||||
|
||||
This article explains how verifiable credentials can be used to benefit event organizers and visitors alike based on a practical usage of the Lissi team.
|
||||
|
||||
* [Orie Steele @OR13b](https://twitter.com/OR13b/status/1573100718164164610) via Twitter
|
||||
|
||||
The [Content Authenticity Initiative](https://contentauthenticity.org/how-it-works) one of Orie’s favoriate Use-cases for VCS
|
||||
|
||||
Yes, verifiable authentic human content is important. I also think cryptography can provide better transparency for synthetic content. It's one of my favorite applications of W3C Verifiable Credentials.
|
||||
|
||||
* [Credivera @crediveratech](https://twitter.com/crediveratech) via Twitter
|
||||
|
||||
* [They are using Entra!](https://www.credivera.com/the-exchange/verifiable-credentials)
|
||||
|
||||
We Credivera are Having fun at the #NSCExpo
|
||||
* [Yes, verifiable authentic human content is important.](https://twitter.com/OR13b/status/1573100718164164610) Orie Steele
|
||||
*The [Content Authenticity Initiative](https://contentauthenticity.org/how-it-works) one of Orie’s favoriate Use-cases for VCS*
|
||||
> I also think cryptography can provide better transparency for synthetic content. It's one of my favorite applications of W3C Verifiable Credentials.
|
||||
|
||||
|
||||
* [Blockchains in HR: Prosoon and Talao go together on SSI and HR credentials](https://medium.com/@talao_io/blockchains-in-hr-prosoon-and-talao-go-together-on-ssi-and-hr-credentials-3b92968011fe) Talao
|
||||
> This partnership will enable the use of Blockchain and Self-Sovereign Identity technologies such as verifiable credentials to enable the support of diplomas and professional certifications in compliance with personal data in a decentralized environment (#web3).
|
||||
|
||||
This partnership will enable the use of Blockchain and Self-Sovereign Identity technologies such as verifiable credentials to enable the support of diplomas and professional certifications in compliance with personal data in a decentralized environment (#web3).
|
||||
* [Self sovereign online identity is going to be a CRITICAL tool for everyone on the internet.](https://twitter.com/ericxtang/status/1575645620659900417) EricTang.eth
|
||||
> Without it, we will lose trust of any content on the internet due to AI advancement in the next 12-24 months.
|
||||
>
|
||||
> This one of the most urgent issues in our society today.
|
||||
|
||||
* [HUMBL @HUMBLPay](https://twitter.com/HUMBLPay/status/1574454647384813568) via Twitter ([ANN](https://www.globenewswire.com/en/news-release/2022/04/13/2421969/0/en/HUMBL-Selected-To-Pilot-Digital-Wallet-Program-On-Behalf-of-The-County-of-Santa-Cruz-California.html) 2022-04-13
|
||||
|
||||
using verifiable credentials in their wallet.
|
||||
|
||||
#HUMBL x GF2GO - San Diego, CA - [Pilot Program](https://www.youtube.com/watch?v=H_HAFEzmkWU): New search engine, mobile wallet, verifiable credentials and delivery technologies.
|
||||
|
||||
|
||||
* [EricTang.eth](https://twitter.com/ericxtang/status/1575645620659900417) Twitter
|
||||
|
||||
Tweet of the week (emphasis ours)
|
||||
|
||||
Self sovereign online identity is going to be a CRITICAL tool for everyone on the internet. Without it, we will lose trust of any content on the internet due to AI advancement in the next 12-24 months.
|
||||
|
||||
This one of the most urgent issues in our society today.
|
||||
|
||||
* [Lost and Found: Digital identity Can Be The Difference Between Life And Death For Refugees](https://diacc.ca/2022/09/27/lost-and-found-digital-identity-can-be-the-difference-between-life-and-death-for-refugees/) DIACC 2022-09-27
|
||||
* [Lost and Found: Digital identity Can Be The Difference Between Life And Death For Refugees](https://diacc.ca/2022/09/27/lost-and-found-digital-identity-can-be-the-difference-between-life-and-death-for-refugees/) 2022-09-27 DIACC
|
||||
|
||||
Most Refugees and IDPs did not have the time to properly prepare by gathering all their important documents such as passports, identity cards, driver’s licenses, and land titles or rental agreements. Fleeing your home may save your life, but fleeing without identity documents can lead to a very long wait – sometimes a decade or more – before your life is stable again.
|
||||
|
||||
@ -410,6 +247,5 @@ Most Refugees and IDPs did not have the time to properly prepare by gathering al
|
||||
* [Creating trust in assertions, claims and the authenticity of the original content](https://liccium.com/) LICCIUM
|
||||
|
||||
* [Coming soon — a resume-validating blockchain network for job seeker](https://www.computerworld.com/article/3675547/coming-soon-a-resume-validating-blockchain-network-for-job-seekers.html#tk.rss_security) Computer World
|
||||
|
||||
“Verifying applicant career records can take days, weeks, if not months, to complete," said Dror Gurevich, founder and CEO of the Velocity Network Foundation. "Hiring methods are severely outdated to the point that one in three Americans have [admitted to lying on their resumes](https://t.yesware.com/tt/0db4de0058ee9613cdfcabd5fae96c6ca51e1b7f/275468cd0c53df0b2dfa60dbb913464b/c19e9bd03a563c32bab519acc1fa9f5b/www.resumebuilder.com/1-in-3-americans-admit-to-lying-on-resume/), which slows the hiring process immensely.
|
||||
> "Verifying applicant career records can take days, weeks, if not months, to complete," said Dror Gurevich, founder and CEO of the Velocity Network Foundation. "Hiring methods are severely outdated to the point that one in three Americans have [admitted to lying on their resumes](https://t.yesware.com/tt/0db4de0058ee9613cdfcabd5fae96c6ca51e1b7f/275468cd0c53df0b2dfa60dbb913464b/c19e9bd03a563c32bab519acc1fa9f5b/www.resumebuilder.com/1-in-3-americans-admit-to-lying-on-resume/), which slows the hiring process immensely.
|
||||
|
||||
|
||||
@ -76,9 +76,6 @@ Investors and consumers show growing enthusiasm for privacy-focused alternatives
|
||||
|
||||
Increased supply of user-friendly private tech and increased demand for privacy have converged, creating a moment of unprecedented opportunity for founders with a vision for privacy-first online experiences.
|
||||
|
||||
* [The vital role of LEI Issuers in facilitating wider adoption of globally recognized business identities across Africa with Alberta Abbey from London Stock Exchange Group](https://www.gleif.org/en/newsroom/blog/number-three-in-the-financial-inclusion-interview-series-the-vital-role-of-lei-issuers-in-facilitating-wider-adoption-of-globally-recognized-business-identities-across-africa-with-alberta-abbey-from-lseg-london-stock-exchange-group) GLEIF
|
||||
|
||||
We spoke with Alberta Abbey, LEI Analyst, Data & Analytics, LSEG to discuss how this initiative will support wider adoption of globally recognized business identities, in the form of Legal Entity Identifiers (LEIs), across Africa and how to encourage more entities across Africa to obtain LEIs.
|
||||
* [Google Sued for Misleading Users Over Location Data Privacy](https://anonyome.com/2022/03/google-sued-for-misleading-users-over-location-data-privacy/) Anonyme
|
||||
|
||||
“Google falsely led consumers to believe that changing their account and device settings would allow customers to protect their privacy and control what personal data the company could access. The truth is that contrary to Google’s representations it continues to systematically surveil customers and profit from customer data.”
|
||||
|
||||
@ -4,6 +4,22 @@ published: false
|
||||
|
||||
# User Experience
|
||||
|
||||
* [NO NEED FOR SUPERHUMANS!: A practical guide to ethics in socio-technical systems design](https://trustoverip.org/blog/2022/03/18/no-need-for-superhumans/) TOIP 2022-03-18
|
||||
> Of course we are not as Albert Camus once said, ‘wild beasts loosed upon this world’, all of us have a moral compass and a sense of what is right and wrong, no-one intends for their product or service to cause harm. Neither are we superhuman, able to always understand the perspectives of all stakeholders or foresee the consequences of every cool feature or elegant line of code, nor indeed can we forecast how our products and services will be used for good or ill. Lisa called on all of us to remember that “technology is not a product, but a system”, and gave us practical steps to help us tap into our innate moral compass and design for those systems with the human experience and human flourishing at its heart.
|
||||
- summary and video [on our Wiki](https://wiki.trustoverip.org/display/HOME/1.+Dear+Human%2C+The+Future+Needs+You.++Practical+Ethics+with+Digital+Sociologist%2C+Lisa+Talia-Moretti) or [YouTube](https://www.youtube.com/watch?v=Xmnnj82wpTM&t=20s
|
||||
- Lisa’s Ted Talk, [Technology is not a product, it’s system](https://www.ted.com/talks/lisa_talia_moretti_technology_is_not_a_product_it_s_a_system)
|
||||
- [HXWG Expert Series Summary](https://wiki.trustoverip.org/display/HOME/Expert+Series) including video of Lisa’s talk
|
||||
- [A SocioTechnical Process for Researchers, Designers and Creators](https://bit.ly/sociotechprocess)
|
||||
- The [responsible tech guide](https://atih.responsibletechguide.com/introduction) is full of useful links and insights
|
||||
- [Ethics for Designers also has practical tools](https://www.ethicsfordesigners.com/tools)
|
||||
* [FRIDA’S principles to guide data and technology](https://youngfeministfund.org/wp-content/uploads/2020/07/FRIDAS-TECH-AND-DATA-PRINCIPLES.pdf) Young Feminist Fund
|
||||
|
||||
The tech we use should be responsive to and responisble with the climate, environment crises of our time. Frida advocates for the use and creation of volence-free technologies putting first the care of our territories and bodies
|
||||
|
||||
* [FRIDA Happiness Manifesto](https://youngfeministfund.org/wp-content/uploads/2019/06/Happiness-Manifestx-web.pdf) Young Feminist Fund
|
||||
|
||||
* [We Should Embrace the Ethical Implementation of Digital Identity](https://www.continuumloop.com/embrace-the-ethical-implementation-of-digital-identity/) Continuum Loop
|
||||
> Maybe it’s because of the nature of my job in decentralized identity consulting, but lately, I’ve been seeing a lot of conspiracy theories on social media about Self-Sovereign Identity (SSI). People criticize the way it’s being implemented and warn about the negative consequences it will have. It’s almost as if people don’t realize that organizations are already monitoring and influencing us and that Google and social media algorithms have been instrumental in this.
|
||||
|
||||
* [Falsehoods Programmers Believe About Names - With Examples](https://shinesolutions.com/2018/01/08/falsehoods-programmers-believe-about-names-with-examples/) Shine Solutions Group 2018-01-08
|
||||
> In this post I’m going to list all 40 of Patrick’s original falsehoods, but give you an example (or two) drawn from my experiences working in this space. Ready? Let’s go!
|
||||
|
||||
Loading…
Reference in New Issue
Block a user